The program for blocking Windows 7 folders. Encryption of files and folders in Windows. How did you use
Each user has some of its confidential data and it would not want this data to see other users. In fact, it does not matter what the files are, the main thing is that it is a personal information that should be inaccessible to the rest. In this difficult case, the user will help the program for encrypting and protecting files that we will tell below.
Some programs have integrated document protection tools using passwords, such as Microsoft Office and WinRAR. But minus their protection is that for these programs there are many utilities for hacking, with which it is quite realistic to hack this protection. And if you need to hide a photo, audio recording or video?!
So, what can be hidden and encrypt programs for encryption? Usually users hide individual files, folders, whole logical sections hard disk, Portable media (memory cards, flash drives, external hard drives), email and much more.
Note that the hide and encryption of files is not a complicated, but a fairly easy operation, which is comparable by complexity with the usual editing of the text file.
In conclusion, we turn your attention that programs for encryption and data protection can be dangerous due to the inattention of the users themselves. There may be such a situation that the user itself cannot access the encrypted data as a result of the loss or forgetting the password, any problems with operating system and other situations. To the use of this kind of software you need to approach seriously and carefully.
Unfortunately, Windows did not provide for the ability to protect the password folder. In many cases, the password folder would help save important data from viewing outsiders without any problems. How to implement it on a laptop or computer I will consider in this article. The instruction will suit the systems with Windows 7, 8 and 10
Speech will go demon paid programsah and their paid analogues, as well as about some other methods ( without third-party utilities ) With which you can protect folders and valuable data in them with password.
Free utilities and software to install a password to the folder
There are few such programs, but there are those that can easily help put a password to the folder. I will conduct a mini review of the most worthy, and you will choose what it will be more suitable for you. They should be compatible with popular versions of Windows. All links will be listed immediately in the article.
It is important to know what is unnecessary to set more than 1 programs for such purposes. They can conflict with each other.
Anvide Seal Folder.
Probably the most popular, free program that allows you to make a folder under password. There is a support of the Russian language. Download the archive and run it. Add to List 1 or several folders you want to close the password. Just drag them into the working window. Close access from the menu ( or press F5.). Make it for all the necessary files.
Settings allow not only to encrypt the password folder, but also data stored in it ( name, file size). All unsuccessful authorization attempts are remembered and shown in the right entry.

The rest of the opportunity you can easily check yourself. The author of the program always helps if any problems arise.
Winmend Folder Hidden.
A program with a very attractive interface allows you to access the password folders. There is Russian localization ( after installing and running). Download and use free.

Just a few control buttons. In addition to the color scheme and language there are no settings. Drag the folder to the window and it will automatically become hidden. Access to it can only be obtained from the program.

The disadvantages should include the lack of encryption without hiding folders.
SecretFolder.
No less simple program In English, but it has a very friendly interface in which even an inexperienceful user will figure out. Download it and install it. Enter the password at 1 launch. It will be required to enter the program where protected folders will be located.
This password is also required when removing ( for reliability, you can use the recovery via email address).

After hitting the working window, you will sufficiently drag into it the folder with the mouse or select it in the directory through the menu ( Add.). Pay attention to status. Lock - protected. Unlock - without protection. To re-access files, you will need to go to the program, and you will unlock the directory from here. Below in the window shows an instruction that is most likely not useful.

Such simple actions You can safely close access to a foreign folder with valuable files.
Dirlock.
The simplest in the use of the program that you can protect the folder immediately from the context menu windows Explorer (will appear new line Lock / unlock). There is nothing superfluous in it. Download it and block the folder entering the password 2 times. This must be done every time after viewing the protected files.

In the main window of the program, all protected folders are displayed. They can also be unlocked from here.

Convenient and safe solution.
Paid programs to protect the folder
If free options are not suitable, you can use paid. Of course, they are made better and have more functional, but they will have to pay for it. I will consider the most good in my opinion, and you yourself decide which best is suitable for you.
Folder Guard
This program has free trial period 30 days. There is Russian. Immediately after installation, you will be asked to enter a password for entering the program. To set the password to the folder, just drag it into the window. Each setting step is described in detail and there should be no difficulties. Download it and install it.

You can simply hide the folder as usual and network, but you can set the password. It is possible to limit access to different users. There is an emergency recovery function in case the password was forgotten.

There is even protection in safe mode. The program hides itself with the "hidden" attribute. The call is supported by hot key. Everything can be easily customized for your needs. Of the minuses, I would noted that the certificate in English.

In general, it is very convenient to use, in addition to installing a password, a lot of different options. In various situations, they can really be useful.
Iobit Protected Folder.
The simplest of all paid folder protection programs in the native language ( selects in the settings). 20 trial launches. Supports all topical windows version. In the picture below, you can see that it will not cause any difficulties in use.

There are several options additional parameters. I liked this program more than anyone else. Convenient, quickly, safe and there is nothing superfluous. Download it and try yourself.
My Lockbox
Another program from a Russian developer who will allow you to easily ensure the protection of important data. There are no frills in it. When you first start, you will need to enter a password. Access to all folders will open after its input. There is a recovery service via email ( not necessary). Download and test.

In the interface, only a few main buttons. It is possible to set a filter of trusted processes. Many topics. The functionality is similar to the rest of the programs.
- Install - adds protection to the folder.
- Clear - removes it.

It is possible to enjoy free only with 1 folder. In a paid version, this restriction is removed and user support is added.
Locking folder password inside archive

You can encrypt virtual hard Disk or flash drives. If you forget the password, it will be almost impossible to restore data. Reliable protection method windows tools without third-party programs.
Microsoft script to install a password to the folder
An unreliable way, the protection of which is very easily accounted for by simply inclusion of the display of hidden system files Windows. However, also takes place in this article as otherwise access to the folder is carried out using the password, which was installed in advance. Advantage this method It is not necessary to download any third-party applications.
What else can you do
In Windows, though it does not provide a built-in password installation function on folders, but you can do simple creation The second user and set the password to the account. In addition to this, limit the rights. Pretty simple and efficient data protection method. However, an experienced user can cope with this.
I would also advise and encrypt him. This can be done by the same bitlocker utility or her like. There is also your minus that the section can simply delete and the data will be lost.
Of all the most reliable ways to protect the folder is encryption. But then if you forget the password, then you ourselves lose access to the data. I add a folder to the archive and encrypt it. I think it is much more convenient and safer than everything else. It all depends on who is required to hide information. 100% protection against all does not happen.
I hope you have found a solution to the task. I will answer all questions in the comments.
How did you take advantage of?
Editor's Choice
Programs encryption files
Encrypt everything!
Every time the information about the scandal associated with the fact that important documents leaked somewhere were leaked, I ask myself why they were not encrypted? Document protection should be everywhere in the end.
Encryption algorithms

The encryption algorithm is similar to a black box. Dump document, images or other file that you download to it, you get back. But what you see seems to be nonsense.
You can turn this plate back to a normal document through a window with the same password that you entered when encrypted. Only so you get the original.
The US government recognized the advanced encryption standard (AES) as a standard, and all products that are assembled here, support AES encryption standard.
Even those who support other algorithms are usually recommended to use AES.
If you are an encryption expert, you may prefer another algorithm, blowfish, and perhaps even the algorithm of the Soviet government for GOST.
But it is already completely for lovers of extreme entertainment. For an ordinary user AES is just an excellent solution.
Open key cryptography and exchange
Passwords are important and you must keep them secret, right? Well, not when using open key infrastructure (PKI), which is used in cryptography.
If I want to send you a secret document, I just encrypt it using an open key. When you get it, you can use it to decipher the document. All simple!
Using this system in the opposite direction, you can create a digital signature that confirms that your document came from you and was not changed. How? Just encrypt it with your closed key.
The fact that your public key decrypts it is proof that you have the right to edit it.
PKI support is less common than support for traditional symmetric algorithms.
Many products allow the creation of self-seeping executable files.
You may also find that the recipient can use a free definite tool for decryption only.
What's better?
Now there is a huge selection of products available in the encryption area.
Everyone simply has to choose the solution that will be convenient for functionality, practical and stylish from the point of view of the primary program interface.

Digital CertainSafe Safe passes through a multistage security algorithm that identifies you on the site. You will have to pass several authentication.
Your files are encrypted if they are trying to hack, they crumple themselves, and no one can recreate them. In this case, there is a certain risk, but at the same time, the level of reliability is very worthy.
Then each piece of file is stored on another server. A hacker who was able to hack one of the servers will not be able to do anything useful.
Lock can encrypt files or just lock them so that no one can open them. It also offers encrypted lockers for safe storage personal confidential.
Among many others useful features It is possible to note the possibility of grinding, binding of free space, secure network backup and self-seeping files.
Veracrypt (Windows / OS X / Linux)

Veracrypt supports encryption on TrueCrypt, which has ceased to develop last year.
The developer team argues that they have already considered the issue raised during the initial TrueCrypt audit, and believe that it can still be used as an accessible version for, OS X and.
If you are looking for a file encryption tool that really works, then it is it. Veracrypt supports AES (most frequently used algorithm).
It also supports TWOFISH and Serpent Encryption Ciphers, supports both hidden encrypted volumes.
The program code is open, most of the code base consists of TrueCrypt.
The program is also constantly developing, regular security updates and independent audit at the planning stage (according to developers).
Those of you who have already tried it, praised it for the fact that the encryption tool works perfectly on the fly, and in your files are decrypted only when they are needed. So the rest of the time they are stored in an encrypted form.
Especially users note that the program is a powerful tool that is easy to use and always to the place. Yes, he lacks a pretty interface or tons of bells.
AXCRYPT (Windows)

AxCrypt is a free program, open source code GNU licenses.
The GPL-licensed encryption tool for Windows, which is proud to be simple, efficient and reliable to use.
It is perfectly integrated with windows shellSo you can right-click on the file that you want to encrypt and give the command.
Or you can simply configure the executable code, so the file will be blocked if it is not used for a certain period of time. It can be decrypted later, or when the recipient will notify about receipt.
Files with AxCrypt can be decrypted on request or keep them decrypted while they are used, and then automatically they will be encrypted.
It supports 128-bit AES encryption, provides protection against hacking attempts. It is very light (less than 1 MB.)
Everyone himself decides which program to use, but if your data is at least worth something for you, be sure to think about what you need a program for encryption.
Encryption of files and folders in Windows
Programs for encryption files: what better to choose?
Put a password to the folder and using special programs, paid and free. As part of this article, we will consider several free programs to protect the password folders.
Remember, before reinstalling Windows You must open access to all folders!
The WinMend Folder Hidden installation process is similar to other programs, so we will not stop in more detail. We only note that when installing, select English (english), because In addition to it, only Greek is available. Later, in the program itself, it can be changed into Russian.
When you first start the program, you need to come up with, enter and confirm the password for an input, consisting of 6 to 15 characters.
Each time, running a program, you will need to enter your password.
The running program has the following form.
To protect the password folder - drag it into the program window, or specify the path to it using the right button to the Hide Folder.
Using the "Show" and "Hide" buttons, you can show and hide files. Thus, you protect the selected objects. For example, to display hidden from them, you need to run the program and enter your password. You can also "change the password" to enter the program and "Delete" from it selected objects. The selection of the program language is located in the lower right corner. This program for protecting folder folders is simple and understandable, everyone can figure it out.
Now you know how to put a password to a folder or a separate file.

Run the password installation program to the folder. When you first start, it will offer to read the license. Click the button "accept a license agreement". In subsequent launches, it will start immediately bypassing this window.


That's actually installed without any problems, which can not but rejoice. Now you need to select the folder on which we want to set the password and hide from prying eye. Click on a big plus game that refers to adding a folder

In the review of the folders, I choose the same in the first way the folder "Documents" and click "OK"

Now after selecting the folder to install the "Documents" password, click on the "Castle" button


There is still a special option "Reminders", in order if you suddenly forget set password. The button is in the lower right corner. Just click her and write a hint


So, installed the hint, click the "Close Access" button

Now access to the folder is closed. And by the way, this folder is nowhere to find anywhere on the computer (at least a truly user).

Now. To work with the folder, you need to open the program again and click two times on it. The password input field appears on the folder. Enter it and the folder again appears on the place where it was. Those, open the "my computer" or another file manager and go to the place where it was previously.

Folder without a password tinted light blue.

Now you know how to set a password to the folder. I hope this article will help you maintain confidential information safely and preservation.
Another disadvantage of the above-mentioned program is the lack of creating several user profiles. That is, only one user can enjoy the function of hiding the information: the second copy of the application (wherever it is installed) will still cause the same storage as the first: (however, if you need to hide something, only you personally, then Folder Hidden.it will be the perfect option!
Winmend Folder Hidden Installation
To set the program, we need to start the standard installer. At the same time, the Russian-speaking instruction is not provided, therefore, at first it will have to choose English:

After pressing the "FINISH" button in the last dialog box, the program will start the program itself.

When you first start, you will need to come up with a password (from 6 to 15 characters) to access the hidden repository and enter it twice in the form. After confirming the password and click the button Okwe will see the work window itself Folder Hidden.:

Winmend Folder Hidden interface
The default English interface is English, however, the Russian localization is also present. To activate it, it is enough to click the button "English"in the lower right corner of the working window, and in the dialog that opens, select the item "RUSSIAN", then press the button Ok. Changing the language will occur without restarting the program itself, so we can immediately begin work:

Working with the program
First you need to press one of the two top buttons: for example, to hide the whole directory (as in our case) - "Hide folder". In the opening window that opens, it is now enough to allocate the desired folder and press Ok.
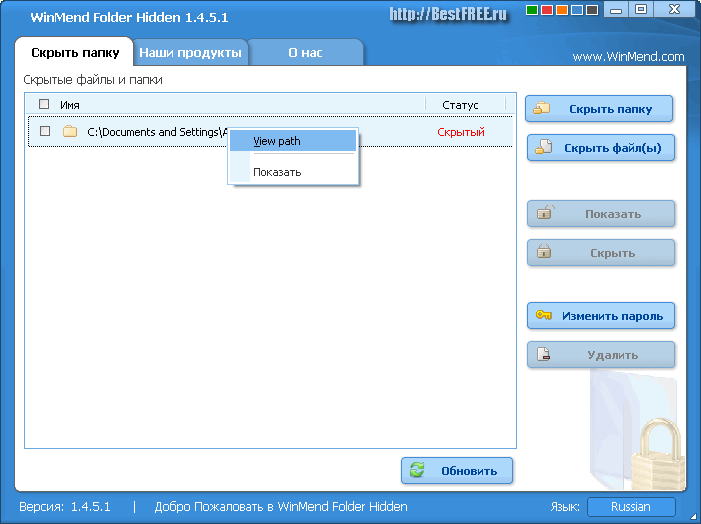
The folder specified by us will disappear, but will appear in the list. Folder Hidden.as new recording. To the right of the recording you will see its current status. Now, if you even close the program, all entries with the status "hidden" will remain invisible until you return to Folder Hidden.and do not activate their visibility!
Now about how to return our folders to your previous place. The program has two ways change appearancehidden files and folders:
- Use the buttons on the sidebar (right). To the button "Show"it became active, the desired record should be previously marked with a check mark (left). Such a way of display hidden folders It will be especially convenient if you want to open a few or even all hidden folders.
- To display a single entry in the list Folder Hidden.just call its context menu and select item "Show"(or "Hide"). Here (in the menu) there is another item ( VIEW PATH), which allows you to quickly go to the directory in which there is a hidden file or folder.
If desired, being in the main window Folder Hidden., You can change the login password. To do this, click the button. "Change Password"and in the window that opens, double-to enter a new access code to our hidden files and folders.

- AES-encryption, key length 256 bits.
- Hiding files and folders.
- Encryption of files (by creating virtual disks - safes) "on the fly".
- Backup online.
- Creating secure USB / CD / DVDs.
- Encryption attachments email.
- Creating encrypted "wallets" storing information about credit cards, accounts, etc.
It would seem that the possibilities of the program is quite enough, especially for personal use. Now let's look at the program in work. When you first start, the program asks to install a master password that is used to authenticate the user in the program (Fig. 1). Imagine this situation: you hid files, and someone else launched the program, viewed which files are hidden and access to them. Agree, not very good. But if the program requests a password, then this "someone" does not exit anything already - in any case, until he picks up or does not recognize your password.

Fig. 1. Setting the master password when you first start
First of all, let's see how the program hides the files. Go to section Lock Files., then either drag files (Fig. 2) and folders to the main program area or use the button Add.. As shown in Fig. 3, the program allows you to hide files, folders and discs.

Fig. 2. Drag the file, highlight it and click Lock

Fig. 3. Button Add.
Let's see what happens when we press the button. Lock. I tried to hide the file C: \\ Users \\ Denis \\ Desktop \\ Cs.zip. The file disappeared from the conductor, Total Commander and the rest file managersEven if the display of hidden files is enabled. The file hiding button is called Lock, and section Lock Files.. However, it would be necessary for these elements of the UI to name Hide and Hide Files, respectively. Because in fact, the program does not block access to the file, but simply "hides" it. Look in Fig. 4. I, knowing the exact name of the file, copied it to the CS2.Zip file. The file was calmly copied, there were no access errors, the file was not encrypted - he unpacked, as usual.

Fig. 4. Copying a hidden file
By itself, the function of the concealment is stupid and useless. However, if you use it with the file encryption function - to conceal the safes created by the program - then the efficiency of its use will increase.
In chapter Encrypt Files. You can create safes (Lockers). Safe is an encrypted container, which, after mounting, can be used as a regular disk - encryption is not easy, but transparent. The same technique is used by many other encryption programs, including TrueCrypt, Cybersafe Top Secret, etc.

Fig. 5. Section Encrypt Files
Press the button Create Locker, In the window that appears, enter the name and select the location of the safe (Fig. 6). Next, you need to enter a password to access the safe (Fig. 7). The next step is to select the file system and the size of the safe (Fig. 8). Safe size - dynamic, but you can set the maximum limit. This saves disk space if you do not use the Safety Deposit Browse. If you wish, you can create a fixed-size safe, which will be shown in the "Performance" section of this article.

Fig. 6. Title and location of the safe

Fig. 7. Password to access the safe

Fig. 8. File system and safes
After that, you will see the UAC window (if it is turned on), in which it will be necessary to click Yes, then a window will be displayed with information about the created safe. It is necessary to press the FINISH button, after which the conductor window will be opened, which displays a supported container (carrier), see Fig. nine.

Fig. 9. Virtual disk created by the program
Return to section Encrypt Files. And select the desired safe (Fig. 10). Button Open Locker Allows you to open a closed safe, Close Locker - close open, button Edit Options. Calls a menu in which you are deleting / copying / renamed / change the safe password. Button Backup Online Allows you to retrieve the safe, and not somewhere, but in the cloud (Fig. 11). But first you have to create an account Secure Backup Account., after which you get up to 2 TB disk spaceAnd your safes will be automatically synchronized with the online storage, which is especially useful if you need to work with the same safe on different computers.

Fig. 10. Safety operations

Fig. 11. Creating Secure Backup Account
Nothing is just like that. Rates for storing your safes can be found at Secure.NewsoftwareS.Net/signup?id\u003den. For 2 TB will have to put $ 400 per month. 500 GB will cost $ 100. To be honest, it is very expensive. For $ 50-60, you can rent a whole VPS from 500 GB "Onboard", which you can use as a repository for your safes and even create your own website on it.
Please note: the program knows how to create encrypted sections, but unlike the PGP Desktop program, it does not know how to encrypt all the disks. In chapter Protect USB / CD You can protect your USB / CD / DVDs, as well as email attachments (Fig. 12). However, this protection is carried out not by encrypting the carrier itself, but by recording to the appropriate carrier of the self-sewn safe. In other words, a trimmed portable version of the program will be recorded on the selected medium, which is allowed to "open" safe. As such support for postal customers, this program is also not. You can encrypt the attachment and attach it (already encrypted) to the letter. But the attachment is encrypted by the usual password, and not PKI. I think about reliability there is no point.

Fig. 12. Section Protect USB / CD
Section Make Wallets. Allows you to create wallets containing information about your credit cards, bank accounts, etc. (Fig. 13). All information, of course, is stored in encrypted form. I can say with all responsibility that this section is useless, since the function of exporting information from the wallet is not provided. Imagine that you have many bank accounts and you made information about each of them to the program - the account number, the name of the bank, the account owner, SWIFT code, etc. Then you need to provide information about the account of the third person to transfer you money. You will have to manually copy each field, insert it into a document or email. The presence of export functions would greatly facilitate this task. As for me, it is much easier to store all this information in one general document to be placed on the Virtual Disc - safe created by the program.

Fig. 13. Wallers
Advantages of the Folder Lock Program:
- An attractive and understandable interface that will enjoy novice users who speak English.
- Transparent encryption "on the fly", the creation of virtual encrypted discs with which you can work with as with conventional discs.
- Ability to back up online copying and synchronization of encrypted containers (safes).
- The ability to create self-seeping containers on USB / CD / DVDs.
Disadvantages of the program:
- There is no support for the Russian language, which will complicate work with the program of users who are not familiar with English.
- The dubious functions of the Lock Files (which simply hides, and not "locks" files) and make wallets (ineffective without exporting information). Honestly, I thought that the Lock Files feature would provide transparent encryption folder / file on a disk, as did Cybersafe Top Secret or file system.
- Lack of file signing, digital signature checks.
- When opening a safe, it does not allow you to select the drive letter, which will be assigned to a virtual disk that corresponds to the safe. In the program settings, you can only select the order in which the program will assign a drive letter - ascending (from A to Z) or descending (from Z to A).
- There is no integration with postal customers, there is only the ability to encrypt the attachment.
- High cost cloud reserve copy.
PGP Desktop.
The PGP Desktop program from Symantec is a set of encryption programs that provides flexible multi-level encryption. The program differs from Cybersafe Topsecret and Folder Lock close integration into the system shell. The program is embedded in the shell (conductor), and access to its functions is carried out through the context menu of the conductor (Fig. 14). As you can see, in the context menu there are encryption functions, file signatures, etc. Quite interesting is the function of creating a self-seeping archive - according to the principle of self-extracting archive, only instead of unpacking the archive also deciphered. However, the Folder Lock and Cybersafe programs also have a similar function.
Fig. 14. Context Menu PGP Desktop
Also, access to the functions of the program can be obtained through the system tray (Fig. 15). Team Open PGP Desktop. Opens the main program window (Fig. 16).

Fig. 15. The program in the system tray

Fig. 16. PGP Desktop window
Program sections:
- PGP Keys. - Key management (both own and imported with Keyserver.pgp.com).
- PGP Messaging - Management of messaging services. When installing the program automatically detects your accounts And automatically encrypts the AOL Instant Messenger communication.
- PGP Zip. - Management of encrypted archives. The program supports transparent and opaque encryption. This section is just implementing opaque encryption. You can create an encrypted zip archive (PGP Zip) or a self-seeping archive (Fig. 17).
- PGP DISK. - This is the implementation of a transparent encryption function. The program can, how to encrypt the entire partition of the hard disk (or even the entire disk) or create a new virtual disk (container). Here there is a SHRED FREE SPACE function that allows you to lose free space on the disk.
- PGP Viewer. - Here you can decipher PGP messages and attachments.
- PGP Netshare. - The "Sharing" tool for folders, and the "balls" are encrypted using PGP, and you have the opportunity to add / delete users (users are identified on the basis of certificates) that have access to the "ball".

Fig. 17. Self-resistant archive
As for the virtual disks, I especially liked the possibility of creating a virtual dynamic size disk (Fig. 18), as well as the choice of an algorithm other than AES. The program allows you to select the drive letter to which the virtual disk will be configured, and also allows you to automatically mount the disk when the system starts and unmounting with a simple (by default after 15 minutes of inaction).

Fig. 18. Creating a virtual disk
The program tries to encrypt everything and everything. It monitors POP / SMTP connections and offers them to protect them (Fig. 19). The same applies to customers for exchanging instant messages (Fig. 20). It is also possible to protect IMAP connections, but it is necessary to separately include in the program settings.

Fig. 19. SSL / TLS connection detected

Fig. 20. PGP Im in action
It is a pity that PGP Desktop does not support popular modern programs Like Skype and Viber. Who is now using AOL im? I think there are some such.
Also, when using PGP Desktop, it is difficult to configure email encryption that only works in intercept mode. And what if the encrypted mail was already received, and PGP Desktop was launched after receiving an encrypted message. How to decipher it? You can, of course, but you have to do this manually. In addition, the already deciphered letters in the client are no longer protected. And if you configure the client to certificates, as is done in the Cybersafe Top Secret program, then the letters will always be encrypted.
Interception mode is also not very good, as mail protection message appears each time each new mail server, and gmail is a lot of them. Mail protection window very quickly you get tired.
The program stability is also no different (Fig. 21).

Fig. 21. PGP Desktop hung ...
Also after its installation, the system worked slower (subjectively) ...
Advantages of the PGP Desktop program:
- A full-fledged program used to encrypt files, signing files and checks electronic signature, transparent encryption (virtual disks and encryption of the entire partition), email encryption.
- Keyserver.pgp.com keys server support.
- The ability to encrypt the system hard disk.
- PGP Netshare feature.
- The ability to rub free space.
- Close integration with conductor.
Disadvantages of the program:
- Lack of Russian support, which will complicate work with the program to users who do not know English.
- Unstable program work.
- Low program performance.
- There is support for AOL IM, but no Skype and Viber support.
- Already deciphered letters remain unprotected on the client.
- Mail protection only works in the intercept mode, which is quickly tired, because the mail protection window will appear every time for each new server.
Cybersafe Top Secret.
As in , detailed description Cybersafe Top Secret will not be, because in our blog and so much has been written about it (Fig. 22).
Fig. 22. Cybersafe Top Secret
However, we still pay attention to some moments - the most important. The program contains key management tools and certificates, and the presence in the Cybersafe your own key server allows the user to publish its public key on it, and also get open keys other employees of the company (Fig. 23).

Fig. 23. Key management
The program can be used for encryption. individual filesWhat was shown in the article. As for encryption algorithms, the Cybersafe Top Secret program supports the GOST algorithms and a certified cryptopropro cryptopro, which allows it to be used in government agencies and banks.
Also, the program can be used for transparent folder encryption (Fig. 24), which allows it to be used as a replacement for EFS. And, given that the Cybersafe program turned out to be more reliable and faster (in some scenarios) than EFS, it is not only possible to use it, but also needed.

Fig. 24. Transparent folder encryption C: \\ CS-Crypted
Cybersafe Top Secret features Reminds the PGP Desktop functionality - if you notice, the program can also be used to encrypt email messages, as well as for electronic signatures of files and checking this signature (section El. digital signatureSee fig. 25).

Fig. 25. Section El. digital signature
Like the PGP Desktop program, Cybersafe Top Secret is able to create virtual encrypted discs and encrypt completely. It should be noted that the Cybersafe Top Secret program can create virtual disks of fixed size only, as opposed to Folder Lock and PGP Desktop programs. However, this lack is neutralized by the possibility of transparent encryption of the folder, and the size of the folder is limited only by the size of the free space on the hard disk.
Unlike PGP Desktop, Cybersafe Top Secret does not know how to encrypt systemic hDDIt is limited only to the encryption of external and internal non-system drives.
But Cybersafe Top Secret has the possibility of a cloud backup, and, unlike the Folder Lock, this feature is absolutely free, you can more accurately, the cloud backup function can be configured to any service - both paid and free. You can read more about this feature in the article.
It also needs to be noted two important features of the program: two-factor authorization and system of trusted applications. In the program settings, you can or set the password authentication or two-factor authentication (Fig. 26).

Fig. 26. Programs settings
On the tab Allowed. Applications You can define trusted applications that are allowed to work with encrypted files. By default, all applications are trusted. But for greater security, you can specify applications that are allowed to work with encrypted files (Fig. 27).

Fig. 27. Trusted applications
Advantages of Cybersafe Top Secret:
- Support for algorithms for encryption of GOST and certified cryptoproder cryptopro, which allows the program not only to individuals and commercial organizations, but also to government agencies.
- Support for transparent folder encryption, which allows you to use the program as an EFS replacement. Given that the program provides, such a replacement is more than justified.
- The ability to sign the email files digital signature and the ability to check the file signature.
- Built-in keys server that allows you to publish keys and access other keys that have been published by other employees of the company.
- The ability to create a virtual encrypted disk and the possibility of encrypting the entire partition.
- The ability to create self-sewn archives.
- The possibility of free cloud backup, which works with any service - both paid and free.
- Two-factor user authentication.
- The system of trusted applications allowing you to allow access to encrypted files to specific applications.
- The Cybersafe application supports the AES-NI instruction set, which has a positive effect on the program performance (this fact will be demonstrated below).
- The Cybersafe program driver allows you to work on the network, which makes it possible to organize.
- Russian-language program interface. For English-speaking users there is a possibility of switching into English.
Now about the shortcomings of the program. There are no special flaws from the program, but since the task was to be honestly compare programs, then the shortcomings will still have to find. If you carefully find fault, sometimes in the program (very, very rarely) "slip" unlocked messages like "Password is weak". Also while the program does not know how to encrypt system DiskBut such encryption is not always and not necessary. But all these are little things compared to the hanging PGP Desktop and its value (but you still do not know about it).
Performance
When working with PGP Desktop, I got an impression (already immediately after installing the program) that the computer began to work slower. If it were not for this "sixth sense", then this section was not in this article. It was decided to measure the performance of the CrystalDiskmark program. All tests are held on real Machine - No virtual. Laptop Configuration Next - Intel 1000m (1.8 GHz) / 4 GB RAM / WD WD5000LPVT (500 GB, SATA-300, 5400 RPM, Buffer 8 MB / Windows 7 64-Bit). The car is not very powerful, but what is it.The test will be made as follows. Run one of the programs and create a virtual container. Container parameters are as follows:
- Virtual disk size - 2048 MB.
- File System - NTFS
- Disc letter Z:
- SEQ is a sequential recording / sequential read test (block size \u003d 1024KB);
- 512K - Test of the random recording / random reading (block size \u003d 512kb);
- 4k - the same as 512k, but block size 4 kb;
- 4K QD32 - Test of the random recording / reading (block size \u003d 4kb, the depth of the queue \u003d 32) for NCQ & AHCI.
Let's start with a conventional hard disk to make it with what to compare. Disk performance C: (and this is the only partition on my computer) will be considered a reference. So, I got the following results (Fig. 28).

Fig. 28. Hard disk performance
Now proceed to testing the first program. Let it be Folder Lock. In fig. 29 shows the parameters of the created container. Note: I use a fixed size. The results of the program are shown in Fig. 30. As you can see, there is a significant reduction in performance compared to the benchmark. But this is a normal phenomenon - after all, the data is encrypted and decrypted on the fly. Performance should be lower, the question is as far as.

Fig. 29. FOLDER LOCK container settings

Fig. 30. Folder Lock Results
The following program is PGP Desktop. In fig. 31 - parameters of the created container, and in Fig. 32 - Results. My feelings were confirmed - the program really works more slowly, which confirmed the test. But only a virtual disk, and even the whole system, which was not observed when working with other programs was not only when the program was "braked."

Fig. 31. PGP Desktop Container Parameters

Fig. 32. PGP Desktop Program Results
It remains to test the Cybersafe Top Secret program. As usual, first - the parameters of the container (Fig. 33), and then the results of the program (Fig. 34).

Fig. 33. Cybersafe Top Secret Container Parameters

Fig. 34. Cybersafe Top Secret
I think comments will be superfluous. By productivity, it was distributed as follows:
- Cybersafe Top Secret.
- Folder Lock.
- PGP Desktop.
Price and conclusions
Since we tested proprietary software, It is necessary to consider another important factor - the price. The Folder Lock application will cost $ 39.95 per unit and $ 259.70 for 10 installations. On the one hand, the price is not very high, but the functionality of the program, frankly, is small. As already noted, there are few sense of files and wallets. The Secure Backup feature requires an additional fee, therefore, to give almost $ 40 (if you put yourself in place of the usual user, not the company) only for the possibility of encrypting files and create self-seated safes - expensive.The PGP Desktop program will cost 97 dollars. And notice - this is just the initial price. The full version with the set of all modules will cost approximately $ 180-250 and this is only a license for 12 months. In other words, every year for using the program will have to lay out $ 250. As for me, this is a bust.
Cybersafe Top Secret is the Golden Middle, both in terms of functionality and price. For a regular user, the program will cost only $ 50 (special anti-crisis price for Russia, for the rest of the countries full version cost $ 90). Please note, so much is the most complete version of the Ultimate program.
Table 1 contains a comparative table of functions of all three products that can help you choose exactly your product.
Table 1. Programs and functions
| Function | Folder Lock. | PGP Desktop. | Cybersafe Top Secret. |
| Virtual encrypted discs | Yes | Yes | Yes |
| Encryption of the entire section | Not | Yes | Yes |
| System disk encryption | Not | Yes | Not |
| Convenient integration with postal customers | Not | Not | Yes |
| Email Email Encryption | Yes (limited) | Yes | Yes |
| File encryption | Not | Yes | Yes |
| EDS signing | Not | Yes | Yes |
| EDS, check | Not | Yes | Yes |
| Transparent folder encryption | Not | Not | Yes |
| Self-resistant archives | Yes | Yes | Yes |
| Cloud backup | Yes (charge) | Not | Yes (broist) |
| System of trusted applications | Not | Not | Yes |
| Support certified cryptoprovidera | Not | Not | Yes |
| Support Tokenov | Not | No (support is discontinued) | Yes (when installing cryptopro) |
| Own server keys | Not | Yes | Yes |
| Two-factor authentication | Not | Not | Yes |
| Hiding individual files | Yes | Not | Not |
| Concealment hard sections disk | Yes | Not | Yes |
| Payment information storage wallets | Yes | Not | Not |
| Support for guest encryption | Not | Not | Yes |
| Russian interface | Not | Not | Yes |
| Sequential read / write (diskmark), MB / s | 47/42 | 35/27 | 62/58 |
| Cost | 40$ | 180-250$ | 50$ |
Considering all the factors set out in this article (functionality, performance and price), winner this comparison Is Cybersafe Top Secret. If you have any questions, we will gladly answer them in the comments.
Tags:
- data encryption
- protection of information
 Error appearance during program launch
Error appearance during program launch FRIGATE plugin for Firefox
FRIGATE plugin for Firefox How to show hidden folders and files in Windows
How to show hidden folders and files in Windows Ways how to make a screen on a laptop brighter or darker
Ways how to make a screen on a laptop brighter or darker How to format a flash drive, disk protection
How to format a flash drive, disk protection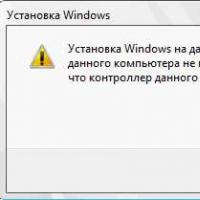 If installing Windows to this disc is not possible
If installing Windows to this disc is not possible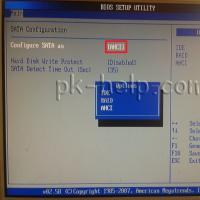 During installation of Windows "Make sure that the controller of this disc is included in the computer's BIOS menu.
During installation of Windows "Make sure that the controller of this disc is included in the computer's BIOS menu.