How to encrypt the entire hard disk using VeracryPt. Alternatives TrueCrypt. Programs for encryption of individual files or electrical disks encryption disks with
In the present days, we are constantly dealing with information. Thanks to the development information technologies, Now work, creativity, entertainment has largely turned into processes for processing or consuming information. And among this huge array of information, part of the data should not be publicly available. An example of such information may be files and data related to commercial activities; Private archives.
Some of these data is not intended for a wide range just for the reason that "they have no need to know about it"; And some information is vital.
This article is devoted to reliable protection precisely important informationAs well as any files that you want to protect from accessing other persons, even if your computer or carrier (flash drive, hard disk) fell into the hands of unauthorized persons, including technically advanced and access to powerful computing resources.
Why do not trust programs for encryption with a closed source code
In programs with closed source code "Bookmarks" may be implemented (and it is not necessary to hope that there are no them!) And the ability to open encrypted files using a master key. Those. You can use any, the most difficult password, but your encrypted file is still with ease, without password generation, it can be opened using the "bookmark" or master key owner. The size of the manufacturer of software for encryption and the name of the country in this issue is not played, as it is part of the state policy of many countries. After all, we all surround the terrorists and drug dealers (and what to do?).
Those. on really reliable encryption can be hoped correctly using a popular software Open source and resistant to hack encryption algorithm.
Is it worth moving with TrueCrypt on veracrypt
The reference program, which for many years allows you to very reliably encrypt files is TrueCrypt. This program still works great. Unfortunately, the program is currently terminated.
Her best heir was the VERACRYPT program.
Veracrypt is free disk encryption software, it is based on TrueCrypt 7.1a.
Veracrypt continues the best TrueCrypt traditions, but at the same time adds enhanced safety algorithms used to encrypt systems and partitions, which makes your encrypted files immune to new achievements in the attacks of full password enumeration attacks.
Veracrypt also corrected many vulnerabilities and security problems found in TrueCrypt. It can work with TrueCrypt volumes and offers the ability to convert TrueCrypt containers and non-system sections to VeraCrypt format.
This improved security adds some delay only to the opening of encrypted sections without any influence on performance in the use phase of the encrypted disk. For a legitimate user, this is a practically inconspicuous inconvenience, but for an attacker it becomes almost impossible to access encrypted data, despite the presence of any computing capacities.
This can be demonstrated by clearly the following benchmarks for hacking (mischief) passwords in Hashcat:
For TrueCrypt:
Hashtype: TrueCrypt PBKDF2-HMAC-RIPEMD160 + XTS 512 Bit Speed.dev. # 1.: 21957 H / S (96.78MS) Speed.dev. # 2.: 1175 H / S (99.79ms) Speed.Dev. # * .: 23131 H / S Hashtype: TrueCrypt PBKDF2-HMAC-SHA512 + XTS 512 Bit Speed.dev. # 1.: 9222 H / S (74.13ms) Speed.dev. # 2.: 4556 H / S (95.92ms) Speed.dev. # * .: 13778 H / S Hashtype: TrueCrypt PBKDF2-HMAC-Whirlpool + XTS 512 Bit Speed.dev. # 1.: 2429 H / S (95.69ms) Speed.dev. # 2nd: 891 H / S (98.61ms) Speed.dev. # *.: 3321 H / S Hashtype: TrueCrypt PBKDF2-HMAC-RIPEMD160 + XTS 512 Bit + Boot-Mode Speed.dev. # 1.: 43273 H / S (95.60ms) Speed.dev. # 2.: 2330 H / S (95.97MS) Speed.dev. # * .: 45603 H / S
For Veracrypt:
Hashtype: Veracrypt PBKDF2-HMAC-RIPEMD160 + XTS 512 Bit Speed.dev. # 1.: 68 H / S (97.63ms) Speed.dev. # 2.: 3 H / S (100.62ms) Speed.Dev. # * .: 71 H / S Hashtype: Veracrypt PBKDF2-HMAC-SHA512 + XTS 512 Bit Speed.dev. # 1.: 26 H / S (87.81ms) Speed.dev. # 2.: 9 H / S (98.83ms) Speed.dev. # *.: 35 H / S Hashtype: Veracrypt PBKDF2-HMAC-Whirlpool + XTS 512 Bit Speed.dev. # 1.: 3 H / S (57.73ms) Speed.dev. # 2.: 2 H / S (94.90ms) Speed.dev. # *.: 5 H / S Hashtype: Veracrypt PBKDF2-HMAC-RIPEMD160 + XTS 512 Bit + Boot-Mode Speed.dev. # 1.: 154 H / S (93.62ms) Speed.dev. # 2: 7 H / S (96.56ms) Speed.dev. # *.: 161 H / S Hashtype: Veracrypt PBKDF2-HMAC-SHA256 + XTS 512 Bit Speed.dev. # 1: 118 H / s (94.25ms) Speed.dev. # 2.: 5 H / S (95.50ms) Speed.dev. # *.: 123 H / S Hashtype: Veracrypt PBKDF2-HMAC-SHA256 + XTS 512 Bit + Boot-Mode Speed.dev. # 1.: 306 H / S (94.26ms) Speed.dev. # 2.: 13 H / S (96.99ms) Speed.dev. # * .: 319 H / S
As you can see, hack encrypted VeraCrypt containers for several orders of magnitude more difficult than TrueCrypt containers (which are also not completely simple).
Full Benchmark and Iron Description I published in the article "".
The second important question is reliability. Nobody wants especially valuable and important files And the information was lost due to an error in the program. I know about VeraCrypt immediately after its appearance. I watched her development and constantly looked at it. Over the past year, I completely switched to TrueCrypt on VeraCrypt. During the year of daily work, Veracrypt never let me down.
Thus, in my opinion, now it is worth moving with TrueCrypt on VeraCrypt.
How Veracrypt works
Veracrypt creates a special file called a container. This container is encrypted and can only be connected when entering the correct password. After entering the password, the container is displayed as additional disc (as inserted flash drive). Any files placed on this disk (i.e. in the container) are encrypted. While the container is connected, you can easily copy, delete, record new files, open them. Once the container is disabled, all files on it become absolutely unavailable until its connection will be performed, i.e. until the password is entered.
Working with files in an encrypted container is no different from working with files on any other disk.
When you open a file or write it to the container, you do not need to wait for the decryption - everything happens very quickly, as if you really work with a regular disc.
How to install veracrypt in windows
With TrueCrypt there was a half-eyed story - sites were created to "download TrueCrypt", the binary file (well, naturally!) It was infected with the virus / trojan. Those who downloaded TrueCrypt from these unofficial sites have infected their computers, which allowed the attackers to steal personal information and promote the spread of malicious software.
Actually, all programs need to download only from official sites. And even more so it concerns programs that affect security issues.
Official placement places installation Files Veracrypt are:
Installing Veracrypt in Windows
There is a setup wizard, so the process of installing Veracrypt is similar to the similar process of other programs. Unless you can explain a few moments.
The VERACRYPT installer will offer two options:
- Install(Install Veracrypt to your system)
- Extract.(Extract. If you select this option, all files from this package will be extracted, but nothing will be installed in your system. Do not choose it if you intend to encrypt the system partition or system Disk. Selecting this option can be useful, for example, if you want to run Veracrypt in the so-called portable mode. Veracrypt does not require installation in the operating system in which it will run. After extracting all files, you can start the recovered file "veracrypt.exe" (VERACRYPT will open in portable mode))
If you select the marked option, i.e. Association with files .hc.This will add convenience. Because if you create a container with extension.hc, the VERACRYPT will be launched on the double click on this file. But minus is that unauthorized persons can know that.hc are encrypted VeraCrypt containers.

The program recalls Donate:

If you are not constrained in the means, of course, be sure to help the author of this program (he one) would not like to lose it, as we lost the author TrueCrypt ...
VERACRYPT instruction for beginners
VERACRYPT has many different features and advanced features. But the most popular function is the encryption of files. Next step by step is shown how to encrypt one or more files.
Let's start with switching to Russian. Russian is already built into VeraCrypt. It only needs to be turned on. To do this in the menu Settingschoose Language ...:

Select the Russian language there, after that the program language will immediately change.
As already mentioned, the files are stored in encrypted containers (they are also called "volumes"). Those. You need to start with creating such a container, for this in the main program interface, click on the button " Create volume».

The VERACRYPT volume creation wizard appears:

We are interested in exactly the first option (" Create an Encrypted File Container"), So we, without changing, press Further,

Veracrypt has very interesting function - Ability to create a hidden volume. The bottom line is that there is no one and two containers. The fact that there is an encrypted section know everything, including possible unfavorers. And if you force you by force to give the password, it is difficult to refer to what the "encrypted disk is not". When creating a hidden partition, two encrypted containers are created that are posted in one file, but are opened with different passwords. Those. You can place files that look "sensitive" in one of the containers. And in the second container - really important files. For your needs, you enter a password to open an important partition. If it is impossible to refuse, you disclose a password from a not very important disk. No opportunity to prove that there is a second disk, no.
For many cases (concealing not very critical files from prying eye) It will be enough to create a normal volume, so I just click Further.
Select the location of the file:

Tom Veracrypt can be in the file (in the VERACRYPT container) on the hard disk, USB flash drive, etc. Flash Drive The VERACRYPT container is no different from any other regular file (for example, it can be moved or deleted as other files). Click the "File" button to specify the name and path to the generated container file to store a new volume.
ATTENTION: If you choose an existing file, Veracrypt does not encrypt it; This file will be deleted and replaced by the newly created VeraCrypt container. You can encrypt the available files (subsequently), moving them to the Veracrypt container created now.
You can select any file extension, it does not affect the work of the encrypted volume. If you select Extension .hc., And also if you set the VERACRYPT association with this extension, then VERACRYPT will be launched with a double click on this file.
History recently open files Allows you to quickly access these files. Nevertheless, entries in history like "H: \\ My offshore bills renovated on Okhuladr dollars.doc" can have unauthorized persons to tax doubts about your decency. So that the files open from the encrypted disk did not fall into history, check the box in front of " Do not save history».
Selection of encryption and hashing algorithms. If you are not sure to choose, then leave the default values:

Enter the volume size and select Units of Measurement (kilobytes, megabytes, gigabytes, terabytes):

Very important stage, set the password for your encrypted disk:

Good password - it is very important. Avoid passwords from one or more words that can be found in the dictionary (or combinations of 2, 3 or 4 such words). The password should not contain names or dates. It must be difficult for guessing. A good password is a random combination of uppercase and lowercase letters, numbers and special characters (@ ^ \u003d $ * +, etc.).
Now russian letters can be used as passwords.
Help the program to collect random data:

Please note that here you can put a tick to create. dynamic Disc. Those. It will expand as it fills it with information.
As a result, I was created on the desktop. Test.hc file:

If you have created a file with extension.hc, then you can click on it twice, the main program window will open, and the path to the container will already be inserted:

In any case, you can open veracrypt and select the path to the file manually (for this click the "File" button).

If the password is entered correctly, then you will appear in the system new Disc:

You can copy / move any files to it. You can also create folders there, copy files from there, delete, etc.
To close the container from strangers, click Unmount:

To get access to your secret files again, reinstate the encrypted disk.
Setting up VeraCrypt.
Veracrypt has a lot of settings that you can change for your convenience. I strongly recommend putting a tick on " Automatically unmount volumes when inactivity during»:

And also set hot key for " Immediately unmount everything, clean the cache and go out»:

It can be very ... very useful ...
Portable version of VeraCrypt in Windows
Starting from version 1.22 (which at the time of this writing is a beta) a portable option was added for Windows. If you have read the installation section, you must remember that the program is so portable and allows you to simply extract your files. However, a separate portable package has its own features: To start the installer you need administrator rights (even if you want to simply unpack the archive), and the portable version can be unpacked without administrator rights - the difference only in this.
Official beta versions are available only. The VERACRYPT NIGHTLY BUILDS folder with a portable version is VERACRYPT Portable 1.22-beta4.exe.
The file with the container can be placed on the flash drive. On the same flash drive can be copied portable version Veracrypt is allowing you to open an encrypted partition on any computer, including without VeraCrypt installed. But remember the danger of interception of keystrokes - probably the screen keyboard can help in this situation.
How to use software for encryption
Several tips that will help you better save your secrets:
- Try to prevent unauthorized persons to your computer, including do not give laptops to luggage at airports; If possible, give computers to repair without a systemic hard disk, etc.
- Use a complex password. Do not use the same password you use for mail, etc.
- Do not forget the password! Otherwise, the data will not be possible to restore.
- Download all programs only from official sites.
- Use free programs or bought (do not use a hacked software). And also do not download and do not launch dubious files, since all such programs, among other malicious elements, may have kiloggers (keystroke interceptors), which will allow an attacker to find out the password from your encrypted container.
- Sometimes as a means of intercepting keystrokes, it is recommended to use screen keyboard - It seems that it makes sense.
Hard disk - popular modern devicewhich allows you to extend the computer's memory without autopsy system Block. Modern external hard drives can be placed in any handbag, and therefore large amounts of information can always be kept at hand. If you store confidential information on your hard disk, then the best way It is protected - it is to install a password.
Password - a universal means to protect information that is a key that can consist of any number of letters, numbers and symbols. If the user will incorrectly specify the password, then, respectively, access to the data stored on an external hard disk can not be obtained.
How to set a password to an external hard drive?
Before our site has already been covered. Moreover, the question of the right thing was considered. The following will be discussed how the password is overlayed for this device.
Installing the password with built-in Windows tools
Setting the password in this case is used successfully both for conventional USB drives and external hard diskswhich are distinguished by large volumes disk space. The main advantage of this method is that you will not need to download and install third-party programs.
Connect outdoor hard Disk to a computer, and then open Windows Explorer. Specifically, we are interested in the "This computer" section, which displays all connected discs to the computer. Click on the external hard disk with the right mouse button and in the displayed context menu, go to the item "Enable BitLocker" .

The start of the utility will start on the screen. After a moment, a window will be displayed on the screen in which you will need to mention the checkbox "Use a password to remove blocking from the disk" and lines below twice specify new password. Click on the button "Further" .

You will be asked to choose the option of saving a special regenerating key. Three options are available to you: Save to your account microsoft recording, Save to a file to a computer or immediately print the key on the printer. In our opinion, the most preferable is the second option because this file You can unload, for example, in a cloud, and at any time, if the password from the external hard disk will be forgotten, open it.

The following configuration item is invited to configure data encryption. You can note how to mark the encryption of only busy space on the disk and encryption of the entire disk.

We draw your attention to the fact that if you have chosen the encryption of the entire disk, you need to be prepared for the fact that the encryption process can delay long hours. Therefore, if you do not have any large number time, as well as open hDD Supposed on modern computersWe recommend choosing the first encryption option.
The final setup step you should select encryption mode from two available: new regime Encryption and compatibility mode. Given that we work with an external hard disk, check the parameter "Compatibility Mode" And then go further.

Actually, the BitLocker configuration process is completed. To start the password overlay process, you just stay right "Start Encryption" And wait for the end of the process.

If, after the encryption is completed, open Windows Explorer in the "This Computer" section, then our external hard drive will be in the icon with a lock. An open icon with a lock indicates that data access is obtained, and closed, as shown in the screenshot below, says that the password is required.

Opening a twice disk, a miniature window appears on the screen, in which the user will be asked to specify the password from the connected external hard disk.

Installing a password using archiving
Many users do not trust the data encryption process, since in this way you cannot access the disk as a whole. Therefore, this method we will go somewhat different ways - place information stored on an external hard disk in the archive without compression, i.e. An external hard disk, if necessary, can be used without a password, but to access the information saved in it, the security key will need.
To set a password using information archiving, you will need almost any program archiver. In our case, a popular tool will be used WinRar , You can download which you can link at the end of the article.
As soon as the archiver program is installed on your computer, open the contents of an external hard disk, highlight it with a simple keyboard shortcut Ctrl + A or highlight certain folders and files in the event that you need to hide under password not all information on an external hard disk. After that, click on the right mouse button and select the item in the displayed context menu. "Add to archive" .

A window will appear on the screen in which you will need in the block. "Compression Method" Select a parameter "Without compression" and then click on the button "Set password" .

In the displayed window, you will need to specify a password of any duration twice. Below, if necessary, you can activate the encryption of the data contained in the archive (without activating this item named folders and files will be visible, but access to them will be limited).

When the archive creation is completed, in the root folder of the hard disk, in addition to the files, the archive created you will be contained. Now files on the disk, except for the archive, can be deleted.

When you try to open the archive on the screen, a window will be displayed with the request to enter a password. While the password from the archive will not be received, access to information will be limited.

That in the end
Most effective method Confidential Information Storage - Use standard tool BitLocker. This is a wonderful utility, which, perhaps, cannot find analogues superior in quality. The second method implying the use of the archiver can be considered most preferable because it does not limit access to an external hard disk, and only to the information you wish to pass.
Of course, if a mass of information-encrypters of information, but we did not focus on them, since the two methods described in the article are the most optimal for most users.
Enchant hard drive or one of its sections without programs and special efforts
Today we consider the question of how you can encrypt hard disk or it separate sectionswithout applying complex programs and special efforts.
Well, the question of why encrypt the hard disk (Winchester) is rhetorical.
The goals for encryption can be a little different from users, but, in general, everyone strive to ban access to the partition or to the entire Winchestera, foreign people.
It is understandable in our time raised cyber crime, and indeed small computer packs, you can lose important personal files.
So, let's consider the most simple way to encrypt a hard disk or one of its sections.
The way we use:
BitLocker Encryption (embedded in Windows 7 Maximum and Corporate)
And so, proceed. This method The "coding" of the Winchester is embedded in Windows and is called BitLocker. Pros of this method:
- No third-party programs need, all we need already have in operating system (OS)
- If the hard drive was kidnapped, then connecting it to another computer, the password will still be required
Also, at the end stage, when saving the access key, one of the ways is to record it on the USB flash drive, so that it is worth it in advance with it.
This method itself was included in Windows Vista.. In the "seven" it has an improved version.
Many could observe when installing Windows OS, a small section of 100 megabytes is created before local disk "C", now you know what he needs.
Yes, just for encryption BitLocker (in Vista it was 1.5 gigabyte size).
To enable it are heading to the "Control Panel" - "System and Security" - "BitLocker disk encryption".

We are determined with the disk for encryption and choose - "Enable BitLocker".
If a message appears, as in the image below, you need to make minor changes in the system settings:

To do this, in the "Start" in the search bar, we prescribe "policies", search options appear.
Choosing a "Group Policy Change":

We fall into the editor in which we need to proceed by: Computer configuration - administrative templates Windows components - BitLocker disk encryption - operating system discs. On the right twice click on - "Mandatory Additional Authentication":

In the menu that appears, select "Enable", plus you need to put a bird to "Allow the use of BitLocker without compatible TPM" - confirm our settings - OK.
You also need to decide on encryption. We need to put the most complex method.
To do this, we go along the same path as in the previous paragraph, just stop on the "BitLocker disk encryption" folder on the right you see the file - "select a disk encryption method and cipher durability".
The most reliable here is AES with a 256-bit encryption, choose it, find it - "apply" and "ok".
All now you can easily use encryption.
As at the beginning of the article, go to the "Control Panel" - "System and Security" - "BitLocker disk encryption". Click "Enable".
We will be available to the only way in which the key is required. It will be on the flash drive.
The resulting key is recorded in the usual text file. Then it will be proposed to include the check, mark the check mark and "continue."
We make a reboot. If everything has passed successfully, then the next time you turn on, the process of encryption of the hard disk partition will begin.
By time, the process will last depending on the system power - usually from a few minutes to several hours (if there are several hundred gigabytes section).
Upon completion, we receive a message - encryption is completed. Do not forget about the access keys, check them.
We looked at a very simple way to encrypt a hard disk without any third-party programs and deep knowledge in the field of cryptography.
This method is very effective and convenient, you can also encrypt a flash drive using it, consider this question in the next article.
IN lately Laptops received great popularity thanks to affordable price and high performance. And users often use them outside the protected premises or leave unattended. This means that it becomes an extremely pressing issue of ensuring inaccessibility for extraneous personal information on systems running Windows. Simple installation The password on the entrance to the system will not help here. And encryption individual files And folders (read about something) - too routine lesson. Therefore, the most convenient and reliable means is encryption hard disk. In this case, you can make only one of the sections encrypted, and keep private files and programs on it. Moreover, such a section can be made hidden without appropriating a disk letter. Such a partition will look like an unformatted, and thereby not attracting attackers to themselves, which is especially effective, since the best way to protect the secret information is to hide the fact of its presence.
How does the hard disk encryption
The general principle of this: the encryption program makes the image file System And places all this information into the container, the contents of which are encrypted. Such a container can be both a simple file and section on disk device. Using an encrypted container file is convenient because such a file can be copied at any convenient place and continue working with it. This approach is convenient when storing a small amount of information. But if the size of the container is several dozen gigabytes, then its mobility becomes very doubtful, and, moreover, such a huge file size gives the fact that the content in it is some kind useful information. Therefore, the more universal approach is the encryption of a whole section on the cruel disk.
There are many different programs For these purposes. But the most famous and reliable is considered TrueCrypt.. Since this program has open source codes, this means that there are no bookmarks from manufacturers to access the encrypted data through an undocumented "black move". Unfortunately, it is assumed that the creators of the TrueCrypt program were forced to abandon further development and transfer the relay with proprigatory counterparts. Nevertheless, the last reliable version 7.1a remains well-workable on all versions of Windows, and most users use this particular version.
Attention!!! Last actual version - 7.1A ( download link). Do not use the "trimmed" version 7.2 (the project was closed, and on the official website of the program propose to transition from TrueCrypt to BitLocker and is available just version 7.2).
Create an encrypted disk
Consider a standard approach when encrypting sections. To do this, we will need an unused partition on the hard disk or flash drive. For this purpose, you can free one of logical disks. In fact, if there is no free partition, it will be possible in the process of creating an encrypted disk to select disk encryption without formatting, and save the available data. But this is longer in time and there is a small risk to lose the data in the process of encryption, if you permiss the computer hangs.
If the required partition on the disk device is prepared, now you can run the TrueCRYPT program and select the menu item "Create a new Tom".
Since we are interested in storing data not in a container file, but in the disc section, then select the "Encrypt Unisendable Section / Disk" item and the usual type of volume encryption.





At this stage, the mentioned choice may appear - encrypt the data available in the section or format it without saving information.

After that, the program asks what algorithms to make encryption. For household needs, there is no big difference here - you can choose any of the algorithms or bundles of them.

Only this is worth considering that when applying a bundle of several algorithms requires more computational resources When working with an encrypted disk - and, accordingly, the speed of reading and writing drops. If the computer is not powerful enough, it makes sense to press the test button to select the optimal algorithm for your computer.
The next step is the process of formatting the encrypted volume.






Now it remains to wait until the program finishes the encryption of the hard disk.




It is worth noting that at the stage of the password task, you can set the key file as an additional protection. In this case, access to encrypted information will be possible only with this key file. Accordingly, if this file is stored on another computer in local network, if the laptop is lost with the encrypted disk or flash drive, no one can access the secret data, even if it picked up the password - after all, there is no key file on the laptop itself on the flash drive.
Hiding the encrypted section
As already mentioned, the advantage of the encrypted partition is that in the operating system it is positioned as unused and unformatted. And there is no indication that there is encrypted information. The only way to find out is to use special programs According to cryptanalysis, able to make a high degree of chaotic bit sequences to make a conclusion that there are encrypted data in the section. But if you are not a potential target for the special services, then such a threat of compromising you are hardly threatened.
But for additional protection against ordinary people, it makes sense to hide the encrypted partition from the list of available disks available. Moreover, any equal to the disk access directly by its letter will not give anything and is required only if the encryption is removed by formatting. To disseminate the volume from the letter used, you follow in the "Control Panel" to enter the "Computer / Disk Management" section and calling the context menu for necessary section Select the item "Change the letter of the disk or the path to the disk ...", where it will be able to remove the binding.



After these manipulations, the encrypted section will not be seen in windows Explorer and others file managers. And the presence of several varied system sections One unnamed and "unformatted" is unlikely to cause interest among outsiders.
Using an encrypted disk
To use an encrypted device as a regular disk, you need to connect it. To do this, in the main window of the program, you right-click on one of the available drive letters and select the menu item "Select a device and mount ..."

After that, you need to mark the previously encrypted device and specify the password.


As a result, a new disk with the selected letter should appear in the Windows browser (in our case it is a x disc).

And now with this disk it will work out as with any ordinary logical disk. The main thing after the end of the work does not forget or turn off the computer, or close the TrueCrypt program, or disable the encrypted partition - because while the disk is connected, any user can access the data located on it. Disable the section by clicking the "Unmount" button.

RESULTS
Using TrueCrypt program will allow you to encrypt the hard disk and thereby hide your private files from strangers, if someone suddenly get access to your flash drive or hard disk. And the location of the encrypted information on an unused and hidden section creates an additional level of protection, since the uninimal circle may not guess that one of the sections is stored secret information. This method of protection of private data is suitable in the overwhelming majority. And only if you are performed targeted surveillance with the threat of violence to get a password, you may need more sophisticated protection methods, such as steganography and hidden TrueCrypt volumes (with two passwords).
Open source has been popular for 10 years due to its independence from the main vendors. The creators of the program are publicly unknown. Among the most famous users of the program you can allocate Edward Snowden and Bruce Schnayer Security Expert. The utility allows you to turn the flash drive or hard disk into a protected encrypted storage, in which confidential information is hidden from prying eyes.
The mysterious developers of the utility announced the closure of the project on Wednesday on May 28, explaining that the use of TrueCrypt is unsafe. "Attention: use TrueCrypt is unsafe, because The program may contain unreasonable vulnerabilities "- such a message can be seen on the product page on the SourceForge portal. Next, another appeal follows: "You must postpone all the data encrypted in TrueCrypt on encrypted discs or images virtual disksSupported on your platform.
An independent Safety Expert Graham Clemi Commented Logically Commented on the current situation: "It's time to find an alternative solution for encrypting files and hard drives".
It's not a joke!
Originally appeared assumptions that the site of the program was hacked by cybercriminals, but now it becomes clear that it is not a hoax. SourceForge website now offers the updated version of TrueCrypt (which has digital signature Developers) during the installation of which it is proposed to go to BitLocker or another alternative tool.
Professor in the field of cryptography of the University of John Hopkinas Matthew Green said: "It is very unlikely that an unknown hacker identified the TrueCrypt developers, stole them with a digital signature and hacked their website."
What to use now?
The site and pop-up alert in the program itself contains instructions for transferring files encrypted TrueCrypt to the BitLocker service from Microsoft, which comes with Microsoft Vista Ultimate / Enterprise, Windows 7 Ultimate / Enterprise and Windows 8 Pro / Enterprise. TrueCrypt 7.2 allows you to decrypt files, but does not allow you to create new encrypted sections.
The most obvious alternative program is BitLocker, but there are other options. Schnayer shared that it was returning to the use of PGPDisk from Symantec. ($ 110 per user license) uses a well-known and proven PGP encryption method.

There are others free alternatives For Windows, for example diskcryptor. Researcher in computer security, known as The Grugq last year amounted to a whole, which is relevant to this day.
Johannes Ulrich, Scientific Head of the SANS Institute of Technology, Mac OS X users recommend paying attention to FileVault 2, which is embedded in OS X 10.7 (Lion) and later OS of this family. FileVault uses 128-bit XTS-AES encryption, which is used in US National Security Agency (NSA). According to Ulrich, Linux users must stick to the built-in Linux Unified Key Setup (LUKS) system tool. If you are using Ubuntu, the installer of this OS already allows you to enable full disk encryption from the start.
However, users will need other applications for encrypting portable media that are used on computers with different OS. Ulrich said that in this case comes to mind.
German company Steganos offers to use old version its SAFE SEGANOS SAFE encryption utility (current version on this moment - 15, and it is proposed to use the 14 version) that applies for free.

Unknown vulnerabilities
The fact that TrueCrypt may have security vulnerabilities cause serious concerns, especially considering that the audit of the program did not reveal similar problems. Users have accumulated $ 70,000 to audit after rumors that the US National Security Agency can decode significant amounts of encrypted data. The first stage of the study, in which the TrueCrypt loader was analyzed last month. The audit did not reveal either backdors or intentional vulnerabilities. The next phase of the study in which the cryptography methods were used to be checked was scheduled for this summer.
Green was one of the experts participating in the audit. He told that he had no preliminary information The fact that developers plan to close the project. Green told: "The last thing I heard from the TrueCrypt developers:" We look forward to the results of the 2 phases of the test. Thanks for your efforts! " It should be noted that the audit will continue as planned, despite the TrueCrypt project.
Perhaps the creators of the program decided to suspend the development, because the utility is obsolete. Development ceased on May 5, 2014, i.e. after official termination of support windows systems XP. SoundForge is mentioned: "Windows 8/7 / Vista and later systems have built-in tools for encryption disks and virtual disk images." Thus, data encryption is built into many OS, and the developers could consider the program no longer needed.
To add oil to the fire, we note that on May 19, TrueCrypt was removed from the protected Tails system (Snowden's favorite system). The reason is not clear to the end, but the program clearly should not be used - the clubs noted.
CLULES also wrote: "Be it deception, hacking or logical end of the TrueCrypt life cycle, it becomes clear that conscious users will not feel comfortable, trusting their data from the program after the Fiasco."
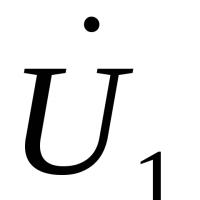 Magnetometry in the simplest version The ferrozond consists of a ferromagnetic core and two coils on it
Magnetometry in the simplest version The ferrozond consists of a ferromagnetic core and two coils on it Effective job search course search
Effective job search course search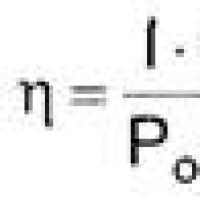 The main characteristics and parameters of the photodiode
The main characteristics and parameters of the photodiode How to edit PDF (five applications to change PDF files) How to delete individual pages from PDF
How to edit PDF (five applications to change PDF files) How to delete individual pages from PDF Why the fired program window is long unfolded?
Why the fired program window is long unfolded? DXF2TXT - export and translation of the text from AutoCAD to display a dwg traffic point in TXT
DXF2TXT - export and translation of the text from AutoCAD to display a dwg traffic point in TXT What to do if the mouse cursor disappears
What to do if the mouse cursor disappears