Specialty Protection of information where to work. Profession - information security specialist. Stages of information attack
Description
During training on this profile, students are taught:
- operate the components of the subsystems, to check their technical condition, repair and maintain maintenance;
- perform adaptation and installation of components of subsystems;
- organize activities related to labor protection and safety;
- apply software and hardware required to provide information security in automated systems;
- monitor the productivity of used hardware and software;
- ensure accounting, processing, transmission and storage of confidential information;
- use engineering equipment;
- solve private technical tasks that inevitably arise in the process of conducting control inspections, certification of premises, objects and technical means;
- apply legal regulatory acts, guidelines and documents;
- develop an organizational structure in a comprehensive information protection system;
- monitor the effectiveness of integrated systems used to provide information protection.
Whom to work
The main direction in professional growth is to ensure information protection in enterprises. These include large corporations and trading networks. In such services, various private detective agencies are also needed, in which the degree of data protection should be at the maximum level. Employment leaders are various state structures that regularly require the developers of security systems and the diagnostics of existing external threats. To promote the service, many graduates begin their professional activities in a team of developers in small enterprises. During this time, they receive invaluable experience, the presence of which will allow it to be hardened in large organizations on the best conditions.
The profession of information security specialist arose at the junction of two directions: information technology and security technologies.
Information security specialist is a person who is engaged in analyzing information risks of companies, as well as the development and implementation of measures to prevent them.
Features of the profession
With the growing number of cyber threats, the profession of information security is becoming more popular in the field of e-commerce, media, various online services.
Responsibilities:
- Collection and analysis of data for adopting information security measures
- Installation, configuration and maintenance of technical, as well as software protection;
- Take part in the development of new means of controlling systems for monitoring and protecting information;
- Find possible channel leakage channels;
- Develop a security policy that is most suitable for this organization;
- Develop proposals for improving and improving the existing security policies;
- Consultation company employees in the field of IB.
Basic skills:
- Administration and understanding of computer network architecture;
- Setup and support for various software;
- Knowledge of English to read high-specialized literature;
- Programming on C #, Java, PHP, Perl and TD.
Information Security Specialist Salary
It is clear that the highest salary of the IB specialist will be in Moscow. Depending on the qualifications and work experience, it ranges from 60,000 to 90,000 rubles.
In St. Petersburg, the remuneration of security specialist will be lower from 30,000 to 77,000 rubles.
In other regions of Russia, the salary of an information security officer is even lower: from 20,000 to 40,000 rubles.
Where to go to study at the IB specialist?
- National Research University Higher School of Economics
- Moscow Physico-Technical Institute (State University)
- Moscow State Technical University. AD Bauman (National Research University)
- Russian Academy of National Economy and Public Service under the President of the Russian Federation
- Financial University under the Government of the Russian Federation
- National Research Nuclear University "MEPHI"
The cost of learning ranges from 250,000 to 330,000 rubles per year. Do not forget that in every university there are budget places. Clarify about the list of documents and the passage Ballet in the schools themselves.
Who can work Spets IB?
After graduating from the university, not every applicant becomes a high-class information security specialist.
Installer networks
It can be said that this is the last hope to cling to work in the field of IT. As a rule, installer networks can take both an assistant without appropriate education. Therefore, people from the area of \u200b\u200binformation security make the installer quite simply.
I will say right away that the profession is not very profitable, so you need to strive for more.
Programmer
Many students who are studying at the Faculties of Information Technologies are read (writing programs). Some of this passion is so delayed that they can retrain the programmer who can tighten their knowledge and become a good specialist. As a rule, people are becoming specials when they code mainly in one programming language, but not enough for everything in a row. Here it is not necessary to explain that the higher the qualifications, the higher the salary.
System Administrator
Any information security specialist should know well and understand the work of the system administrator, and accordingly to perform it. That is, in the most difficult times, an IB employee will be quite simple to start the work of the system administrator.
Many believe that the sysadmin is a pretty simple and not dusty workman. If all the preliminary work on network setup and computers are correct, then consider you lucky. And if not, you will have to finish the shoals of the previous sysadmin. Here the amount of work will depend on the curve of the hands of the one who worked before you before.
Private security service
Here the spectrum of responsibilities will be somewhat already. It will be necessary to come to the object, install and configure equipment for tracking. Naturally, it will be possible to come, and check the condition of the equipment. For example, for unauthorized connections and other.
IT-teacher
You simply have no idea how much useful for your country you can do if you go to work as a computer science teacher.
Knowledge gained in educational institutions can warn future employees (students) from fatal errors. An important role is played by the supply of material. If you can interest the student at the lecture, then it can remember the information obtained for life.
Our country feels the deficit of highly qualified specialists in the field of information security. So, there is a place for business activities. For example, you can open private advanced training courses and learning new professionals. Dare, you will succeed.
Training duration:3 years 10 months - full-time (base 9).
Relevance of learning
In the age of information technology, information is becoming the main value. Accuracy and accessibility are important criteria. Therefore, it is so important to take care of its confidentiality and protection.
To date, automated systems (AC) play a key role in ensuring the effective implementation of business processes of both commercial and state-owned enterprises. At the same time, the ubiquitous use of the AC for storing, processing and transmitting information leads to an increase in the relevance of the problems associated with their protection. This is a confirmation of this that over the past few years, both in Russia and in leading foreign countries, there is a tendency to increase the number of information attacks.
Vulnerabilities - Achilles Fifth Automated Systems.
Almost any automated system can act as an object of information attack - a set of action of an attacker aimed at violating one of the three properties of information - privacy, integrity or accessibility.
Examples of automated systems vulnerabilities may be:
- incorrect configuration of network network services,
- availability of software without installed update modules,
- use unstecified to guessing passwords,
- lack of necessary means of protecting information, etc.
Personal qualities of a specialist in the protection of information
The creation and commissioning of information systems is always the work of several specialists: the company's head, analytics, system designers, programmers. Everyone needs to find an approach and be able to put a task understandable to them. And because communication and skill work in a team For such a specialist is extremely necessary.
Analytical mind warehouse and ability to plan their activities Let a specialist carry out the most complicated operations, develop computer programs, to work with computing equipment, quickly master the ever-developing technology market. Cooling and composure It will also be useful: in case of failure of the equipment, it must begin to eliminate the problems without exposing a panic. Will also be useful good memory, care and scrupulsiness.
Working with information is always responsible work. Therefore, from a specialist in the field of computer science and computing equipment is required efficiency, organization and stress resistance.
The main disciplines that are learning students specialty
- Basics of information security.
- Technical means of informatization.
- Organizational and legal support for information security.
- Networks and information transfer systems.
- Basics of algorithm and programming, programming languages.
- Electronics and circuitry.
- OS.
- Database.
- Economics of the organization.
- Management.
- Safety of vital activity.
- Operation of security subsystems of automated systems.
- Operation of computer networks.
- Software and hardware of information security.
- Cryptographic tools and methods of information protection.
- Application of engineering and technical means of providing information security.
Future professions
- ERP programmer.
- IT specialist.
- Database administrator.
- Specialist organizational and legal protection of information.
- Specialist software and hardware protection information.
- Technical Protection Specialist.
- Local computing network administrator.
- Information protection engineer.
- Programmer.
- Database developer.
- SAP specialist.

The area of \u200b\u200bprofessional activities of graduates with the specialty "Information Security of Automated Systems": Organization and work on ensuring the protection of automated systems in organizations of various structures and sectoral or organizations.
The objects of the professional activity of the graduate are Automated processing systems, storage and transmission of information of a certain level of confidentiality, methods and means of providing information security of automated systems.
Advantages of the specialty:
- The educational and production practices of students can be held in any organizations where technical means of processing, storing and transferring confidential information are used, namely: state authorities, power structures (Ministry of Internal Affairs, FSB, Traffic Policy, Ministry of Emergency Situations, Customs Service, Tax Authorities), medical institutions , banks and other financial institutions, media, enterprises of industry, energy, trade, communications and transport, as well as in research institutes, at the departments and in the laboratories of the universities themselves;
- The demand of specialists in the labor market;
- Dynamic growth in wages, the corresponding level of competence and responsibilities in a specific project involved.
Specialists in informational Safety takes direct participation in creating a system for the protection of information, its audit and monitoring, analyze information risks, develop and implement measures to prevent them.
Their competence also includes installation, configuration and support of technical information security tools.
Safety specialists teach and advise employees on information protection issues, develop regulatory and technical documentation.
This position arose at the junction of two directions of information technology and security technologies. No information security officers today can do neither commercial structures nor departmental organizations such as the FSB
Features of the profession
This profession arose at the junction of two directions: information technology and security technologies. Without information security officers today, neither commercial structures nor departmental organizations can do.
Specialists create protection systems for specific enterprises, protect local computer networks from virus attacks or hacking hackers. They prevent leakage of important information, the supply of data and incompetence (evil intent) of their own employees.
On a state scale, information security specialists create systems for the protection of strategic information on the country's defense capability, form secret databases, maintain the mystery of the nuclear suitcase.
Pros and cons profession
The pros of the profession can be attributed to:
- real estate in the labor market, as the selection of information security is rapidly developing, and therefore the demand for specialists in this area will constantly grow;
- high wage;
- the ability to master the most advanced information protection technologies;
- the ability to attend conferences and seminars;
- communication with a variety of experts, the ability to link useful links.
Cons Profession:
- high Responsibility, as you have to be responsible for the safety of all the company's information;
- frequent business trips are possible.
Place of work
In organizations of various forms of ownership that have their own computer networks and in need of maintaining corporate information and important commercial information.
Important qualities
Communicability and skill work in a team. Creation and commissioning of protection systems is a collective work of several specialists: the head of the company's protected company, analytics, system designers, programmers. Everyone needs to find an approach and be able to put a task understandable to them.
Salary
The level of remuneration of a specialist is determined by the welfare of the company, a list of job responsibilities, experience in the specialty, level of development of professional skills.
Stairs Career and Perspectives
By itself, this position is already one of the highest steps of career growth in the field of IT, above only the post of head of the department or information security department.
Start a career in this field can IT specialists with incomplete or completed higher education, the experience of administering information security and Windows or UNIX operating systems.
Employers' requirements for professional skills and skills of novice specialists are quite serious: even the applicants for a relatively low income should know the legislation of the Russian Federation for information security, the principles of operation of networks and means of cryptocrusts, modern software and hardware for information protection, as well as information security technologies. Salary on which young specialists can count on in the capital, from 40 thousand rubles.
The next level is a specialist with higher education in information technology or information protection, which has experience in providing information security for at least 2 years.
In addition, applicants must have experience in conducting an audit and assessment of the risks of the information security system, the development skills of the regulatory and technical documentation for information security, to know international standards for information protection and own English at the level sufficient to read technical literature. Experts that meet the above requirements earn in Moscow to 80 thousand rubles.
Source: https://www.profguide.ru/professions/specialist_in_information_security.html.
Information security of automated systems: What is the profession to work? :
Information security of automated systems is a profession (and specialty), which delivers graduates and applicants many problems and issues. Basically relative to further employment. And this is understandable - few can give some particular definition of this profession. It can be said vague.
And therefore many doubt whether to come here. But now we will try to understand who you can work after the end of the "Information Security of Automated Systems". Universities, as a rule, are promised to applicants "Golden Mountains", but to give a specific definition of the profession are not capable.
Therefore, you will have to carefully examine possible alternatives to work.
Engineering
The main task of a graduate of this profession is a comprehensive provision of information security of automated systems. But often such employees are arranged to work with the most ordinary engineers. And it suits them.
Often this career choose men. They are more suitable for the work of the engineer. Only here you can not see the golden mountains here. Of course, if we are talking about Russia.
To find a decent place of work will be very difficult. Only in some enterprises, engineers pay good wages.
Plus, this work is not distinguished by the stable working schedule and the absence of voltage.
If you think about the question: "Information security of automated systems - what is the profession and who to work after the end of the university?" You can really work as an engineer. Only for this immediately prepare yourself for what you have to work a lot in voltage. And in constant.
Means of communication
But it is not necessary to choose such a career. Many graduates who entered the direction of "information security of automated systems often go to work in different communication services. And very often employers are Internet providers.
To be honest, then you can meet the graduate specialists of our today's specialty at different jobs - from the usual consultant operator to the installer. And just the second profession is the most popular. Especially among men.
What to do here? Monitor the performance of the equipment on the main server, eliminate failures and malfunctions on the line. Also connect Internet subscribers and configure it.
In general, if you studied well in the direction of "information security of automated systems", then there will be no problems with the duties here. The working schedule here, however, is not particularly pleasant - you can "call" from legitimate leave or tear off from the weekend.
But the salary of installers and operators in communication services is very good. Sometimes it is possible to accept such a schedule if it is adequately paid.
School
You graduated from the direction of "Information Security of Automated Systems". Who to work on the release, if the perspective of the installer or engineer you do not really like? In truth, such graduates can be found anywhere. But often they appear in ... schools.
Why? The thing is that our today's profession gives a lot of knowledge about computers and techniques. And therefore such an employee can easily fulfill the role of teacher computer science. This is a completely normal and usual phenomenon. Only now the prospect of working at school is the most ordinary teacher not very attractive young professionals.
And they can be understood - the responsibility is huge, the working schedule is intense, the full workload of the day (and not only the worker), and the salary is meager. Plus, there are few people want to learn 5-6 years in the university, then to get working for a penny. But at first you can be a teacher of computer science at school.
For example, if you really need work, or at least some experience is needed.
Plus, if you graduated from the "Information Security of Automated Systems" direction, you can always find an elite lyceum or an educational institution, where you like "computer science" will pay dignity.
There are such places, but very little. If you manage to get enough, then, most likely, it is no longer wanted to change the job.
After all, the main indicator in employment is nothing but the salary you will receive.
Sales Manager
Information security of automated systems is a specialty that allows you to work in many places. For example, students and graduates of this area are very often arranged as a sales manager. But this position can go to work without a diploma.
As a rule, "informationons" sell equipment and electronics. Especially computers and components. After all, such graduates know about the "hardware" PC quite a lot. Enough to convince the buyer to purchase one or another product.
But this is not the best career. After all, you do not see any growth. Maximum that "shines" is to become a senior manager. The difference is small here. Therefore, you can work as a seller until you find a more suitable vacancy. Especially if you just released, but there are no other vacancies to ensure our own life.
Security system
Information security of automated systems - what kind of profession is this? With it, you can be an ordinary manager or engineer! But there is another very interesting place that is often chosen by graduates. This is security services. In other words, the work of the guard.
But not at all, as in the supermarket or store. It is about working in special services that set and connect security equipment. Just with this you will have to do.
Plus, sometimes just follow the order through the cameras sitting in the office. In case of violations - or call the usual security guard and call it, or take some actions yourself.
The first version of the development of events is usually selected.
As a rule, the work schedule is rather loyal here, and the income is very good.
Therefore, many are trying to conduct no information security of automated systems, but simply monitor the safety of a particular enterprise.
This is considered a prestigious profession to which, as a rule, many seek. But the competition is very big here. Therefore, it will have to be pretty to try to arrange a "warm" place on such.
Operator
But the female half of graduates, as a rule, is experiencing more problems with employment. After all, those who have chosen the direction "Information Security of Automated Systems" will have to pretty try to find a job. Everywhere or have employees, or need men.
Therefore, many are arranged to work with the most ordinary operators. Depending on the activities of the company will have to or provide advice, or sell goods and services. Plus, many operators are required to call customers (including potential) to alerts them on the shares and bonuses.
In fact, this is quite normal place of work for a young girl. But not for a man. After all, the earnings here are medium, and the working schedule is quite tense. But there is no fully physical activity. So graduate specialists can meet here in such, not even the most prestigious places of work.
Own business
Information security of automated systems - What is this profession in which it is so difficult to find an answer to the question of employment? In order not to break your head, many just open their job. And this is a pretty popular way to build a career.
To be honest, it can engage in an individual graduate of our direction can anything. But only there are the most popular directions. For example, the opening of its own computer aid service or a specialized store of machinery and components. Competition is quite high here, but there are many techniques that can make you a worthy businessman.
In general, individual entrepreneurs are found in graduates of different directions. The main thing is to come up with a decent idea and realize it. Your income, of course, will depend only on their own success. Therefore, if you want to work on the result, this direction will be perfect for you.
Scripture
To be honest, then often people who cannot find a job for a long time are arranged to work by writers. That is, they just begin to write texts and books based on the knowledge gained. And the information security of automated systems here is considered a very popular topics.
Thus, you can start writing to order information texts of this direction. Or specialized literature and methods. True, the writing is rather a vocation, not a profession. And therefore, while you are not popular, it is better to combine this direction with some more familiar job. And the writing activity to tie with part-time.
System Administrator
This is a multifaceted career to build our information security of automated systems. Colleges, by the way,, like many universities, help such graduates become the most real system administrators. To be honest, many applicants and students love this profession.
You will have to connect the equipment, follow it and configure. Plus to all, on your shoulders will be responsible for the performance of computers.
And even a schoolboy can cope with this task. The system administrator salary ranges from the middle level to high, and the work schedule is very loyal. Often free.
This allows you to work somewhere else.
The main thing is to find a worthy place of work. Sometimes, of course, it will have to stay in the office for a long time and work behind computers. But in general, such a workload is extremely rare.
Alternatives
Fortunately, in the graduates of information security of automated systems there are still a lot of alternative approaches to building a career. Only think about this during admission to the university or college. After all, you will have to develop any additional skills.
What is it talking about? For example, you can easily make a programming bias and become a programmer. Or seriously do modeling - will become 3D-designer. In the end, learn how to handle multimedia files and become the creator of the games.
In general, everything that is only connected with computers may be your profession. The main thing is to find your own vocation.
Now you know what information security of automated systems, who to work on the release, as well as possible difficulties with which you may encounter in case of employment.
Source: https://www.syl.ru/article/205037/undefined.
Profession - Information Security Specialist
- Who to become?
- Where to study?
- How to grow?
- What to try?
Concept "Information Security" It became relevant with the development of the Internet.
The virtual world has become very similar to the real one: already now people communicate on the Internet, read books, watch movies, buy goods and even commit crimes. And if there are cybercriminals, it means there must be specialists who are engaged in the security of objects on the network.
These are specialists in information security.
Why should I pay attention to the protection of information?
Imagine that the hacker knows all credit card data. With this information, he will be able to steal money from the card without leaving his home computer. Now imagine that the hacker managed to hack the security system of a whole bank. In this case, the forage size grows hundreds of times. Cybercriminals for the sake of financial benefits can detain social networks, Internet services, automated systems in commercial and government structures. Users will not be able to visit the site, and the site owner will bear financial and reputational losses until the site earns again. Hackers can steal valuable information: personal photos of a famous person, classified military documents, drawings from unique inventions. It becomes clear that no organization or separate person is protected from theft important information for them, so IT companies and large organizations pay great attention to its protection.
Information or Computer Safety Specialist - This is an employee of a company that ensures the confidentiality of the company's data and individual users, is engaged in strengthening the security of information systems, prevents information leakage.
How does an information security specialist doing at work? ✎ Adjusts a multi-level information protection system (logins and passwords, identification by phone numbers, on the fingerprint, on the retina, etc.) ✎ examines the components of the system (site, service, automated system in the company) for vulnerabilities ✎ eliminates the identified breakdowns and Vulnerabilities ✎ eliminates the effects of hacking if they have occurred ✎ develops and implements new information protection regulations ✎ Conducts work with users of the system to explain the importance and types of protective measures ✎ conducts documentation ✎ Prepares reports on the state of IT systems ✎ interacts with partners and suppliers Safety equipment equipment
Computer Security Specialist Works in the team of programmers, system administrators, testers and other IT specialists. According to the security officers themselves, they guard the rear and cover the backs of other departments that are engaged in the development of IT infrastructure.
What universal competencies need a security officer in work?
✔ Analytian mind
✔ skill to see and solve the problem
✔ Patience
✔ Stress resistance
✔ ability to work under pressure
✔ Methodology
✔ curiosity
✔ Permanent self-development
✔ learning
✔ skill work in a team
✔ ability to make decisions
✔ Care for details
Position information security specialist Spends high risks and constant stress. They carry the main responsibility in case of violation of the security system.
Due to the fact that the technologies of hacking and methods of work of attackers are constantly changing, an information security specialist has to be engaged in constant self-education, follow the news in their field and for new items in software and hardware protection, read technical literature in English.
And although security officers are, first of all, high-class technical specialists, they need the development of communicative skills. They have to work a lot with other employees of the Organization to raise corporate culture in data protection.
average salary
The position of information security specialist is paid relatively high due to the high level of responsibility:
✔ 50 000 - 150,000 per month
Where to study
To become an information security specialist, it is necessary to deal with both the Hard and Soft, that is, be able to work with components and with programs. Therefore, it is necessary to start your education in school, training to collect and disassemble a computer, install new programs and work the soldering iron.
Getting an education in the direction of "Information Security" (10.00.00) You can both in colleges and in universities. Colleges are preparing security specialists for security systems. And in universities - more qualified engineers, system architects, information security analysts
Universities:
Academy of Federal Security Service of the Russian Federation (AFS) National Research University Higher School of Economics (NSU HSE) Moscow Aviation Institute (MAI) Moscow State Linguistic University (MGLU) Moscow City Pedagogical University Moscow State Technical University. AD Bauman (MGTU) Moscow State Technical University of Civil Aviation (MGTU GA) Moscow State University of Geodesy and Cartography (Miigaik) Moscow State University of Communications (MIIT) National Research Nuclear University "MEFI" (MEPI) National Research University MIET (MIET) Moscow University of the Ministry of Internal Affairs of the Russian Federation named after V. Ya. Kikotya (Moscow Moss of the Ministry of Internal Affairs) Moscow Polytechnic University (Moscow State Engineering University "Mami") Moscow State University of Information Technologies, Radio Engineering and Electronics (Mirea) Moscow Technical University of Communications and Informatics (MMTUCI) Moscow Physico- Technical Institute (University) (IFTI) Moscow Energy Institute (Technical University) (MEI) Russian State Humanitarian University (RSU) Russian Economic University named after G. V. Plekhanova (REU) University of Technology Financial University under governments f of the Russian Federation
Colleges:
Western Complete Education Complex (former PC No. 42) College of Automation and Information Technologies No. 20 (Cait No. 20) College of Urban Planning, Transport and Technology No. 41 (KGTT No. 41) College of Decorative and Applied Arts named after Karl Faberge (KDPI. Karl Faberge) College of Space Engineering and Technologies TU (KKMT TU) College of International University of Nature, Society and Man "Dubna" (College Muina Dubna) College of Entrepreneurship No. 11 (CP No. 11) College of Communication No. 54 (COP No. 54) College of Modern Technologies Hero named after the Hero of the Soviet Union M. F. Panova (former construction technical school No. 30) Moscow State Educational Complex (former MGTTP) Educational Complex Service (OCS) Polytechnic College No. 8 Name Twice Hero Soviet Union I. F. Pavlova (PC No. 8) Polytechnic Technical School No. 2 (Fri No. 2)
Where to work
Information security specialist in demand:
✔ in major organizations
✔ Banks
✔ IT-companies, for example, Kaspersky Lab, Central Bank of the Russian Federation, Crook, FSB of the Russian Federation Sometimes to work in the field of information security requires a special form of admission to state secrets, which imposes certain restrictions on the employee, including non-market abroad.
Establishment
The demand for information security professionals in the labor market today is extremely high. This is due to the fact that almost every company faces the problem of computer threats.
Olga Bikkulova, Specialist TSR "Humanitarian Technologies"
If you want to receive fresh articles about professions, subscribe to our newsletter.
Return to the list of articles
Subscribe to the news digest
We guarantee confidentiality
Privacy Policy The company CRT "Humanitarian Technologies" respects your right and complies with confidentiality when filling out, transferring and storing your confidential information. Accommodation on the website of the company TTR "Humanitarian Technologies" means your consent to data processing. Under personal data, information belonging to the subject of personal data, in particular the surname, name and patronymic, date of birth, address, telephone, email address, family, property situation and other data attributable to Federal Law No. 152-FZ dated July 27, 2006 The year "On Personal Data" (hereinafter - "Law") to the category of personal data.
The purpose of processing personal data is the provision of services for the CTR "Humanitarian Technologies" company.
Source: https://proforientator.ru/publications/articles/detail.php?id\u003d9747.
Information Security
The specialty "Information Security" appeared in Russian universities about 15 years ago - its significance and popularity is constantly increasing due to the development of digital and telecommunication technologies.
In business, economics, politics, armed forces and society, computer and information security is a critical area of \u200b\u200bknowledge.
The development of the Internet and the concomitant technologies and its penetration in almost every aspect of society, business and government management opens up great opportunities for cybercriminals in their desire to break the usual lifestyle.
The task of educational programs for information security is to prepare modern Specialists in the field of IT, security to cyberspace operations for various sectors of the economy and management.
In 2103, all costs in the world of information security exceeded $ 25 billion, and every year this figure grows by 7%.
Today you can allocate three main areas in the specialties block "Information Security":
1) recognition and access control (solutions to identify users in the system and control of their access to system resources), 2) Content protection and management of threats (development of products against viruses, spyware, spam, hackers and unauthorized access or use of confidential information),
3) protection of systems sensitive to external factors (a complex set of solutions that allow companies to determine, interpret and develop risk strategy).
The need to develop, implement and manage information security decisions will grow from year to year. You can add a skill to work with monitoring technologies (for example, tracking hacker programs), content classification, content filters and data loss prevention tools.
All these prerequisites are due to rapid changes in the work of companies - an increase in mobility, a reference to the consumer, the development of cloud and social types of communications. All this closes clients, employees, suppliers, partners and other parties, which negatively affects the vulnerability of companies to cyberatics.
Theory
Regardless of which specialization is chosen within the direction of "Information Security", on the undergraduate program, students are given general courses on computer science and methods and methods of information protection. Further, depending on the university and curriculum, students receive more specialized knowledge. In the magistracy there is an opportunity to choose the directions of specialization.
On a typical undergraduate program for information or computer security, students receive multidisciplinary training in their field, which also includes cryptography, safety of hardware, software protection. Sometimes the same courses are included in the program of magistracy. By the way, information security magistracy is one of the most sought-after.
Learning in undergraduate in the direction of "Information Security" lasts 4 years and includes a whole range of scientific and practical knowledge of computer, automated, information and telecommunication systems. Students study the basics of providing information security systems or system objects.
Sometimes such programs have some additional bias in accordance with the specifics of the university. For example, in the Moscow State Linguistic University, give excellent language training, which is then very useful for work in a large international company. In the Moscow State Industrial University, the program is built with an emphasis on the automotive industry.
The program "Economic Safety" in Ra them. G.V. Plekhanov also practically perfectly combines these two in demand areas of knowledge. The program is also interesting at the Faculty of National Security of Ranjigs.
Students also teach programming in several languages, such as C, Java, PHP, et al., Legal aspects of information protection and a lot.
Work
Talk about the practical orientation of information security specialists is overcome. Such specialists will not be left without work, perhaps never. Undergraduate graduates of information security provide information protection, telecommunications, satellites, etc.
Arrival
The profile exam upon admission to the specialty "Information Security" is mathematics. In addition to the exam on this subject and in the Russian language, universities usually require another exam - physics or computer science and ICT.
Universities and directions
Russian universities offer two main undergraduate programs - Actually "Information Security" (MTCU, MGLU, RGSU, MGIU, MGU, MGUI, MII, RGGU, MGUG, FINALLY UNIVERSITY, MHPU, MESI, MIET, MEI, MFU), as well as "Computer Safety "(NiU" Higher School of Economics ", Unit MIEM, MSTU them. AD.
Bauman, Academy of Federal Security Service, MFU).
There are also narrower specialization, for example, "Safety of Information Technologies in Law Enforcement" (RSU, MAI, MGUPI, MEPI, IFU), "Information Security of Telecommunication Systems" (MTCUCI, MGUPI, Academy of Federal Security Service), "Information Security of Automated Systems "(MSTU named after N.E.
Bauman, MGIU, MGUPI) and "Information and Analytical Security Systems" (MGUPI, MEPI, Academy of the Federal Security Service), "Economic Safety" (RSU, MIII, REU them. G. Plekhanov, Ranhigs (Faculty of National Security), Mami, MFU). In almost all of these universities, the second highest "information security" can also be obtained.
Communicate with representatives of universities personally
It is much easier and faster to determine the choice by visiting the free exhibition "Master and Additional Education" in Moscow or St. Petersburg. Our other exhibitions can be found in the "Events" section.
To the rest of the specialties \u003e\u003e
Specialists in informational Safety takes direct participation in creating a system for the protection of information, its audit and monitoring, analyze information risks, develop and implement measures to prevent them. The profession is suitable for those who are interested in computer science (see the choice of a profession for interest in school subjects).
Their competence also includes installation, configuration and support of technical information security tools. Safety specialists teach and advise employees on information protection issues, develop regulatory and technical documentation. This position arose at the junction of two directions of information technology and security technologies. Without information security officers today, neither commercial structures nor departmental organizations such as the FSB cannot do.
Features of the profession
This profession arose at the junction of two directions: information technology and security technologies. Without information security officers today, neither commercial structures nor departmental organizations can do. They prevent leakage of important information, the supply of data and incompetence (evil intent) of their own employees. On a state scale, information security specialists create systems for the protection of strategic information on the country's defense capability, form secret databases, maintain the mystery of the nuclear suitcase.
Pros and cons profession
Pros:
- real estate in the labor market, as the selection of information security is rapidly developing, and therefore the demand for specialists in this area will constantly grow;
- high wage;
- the ability to master the most advanced information protection technologies;
- the ability to attend conferences and seminars;
- communication with a variety of experts, the ability to link useful links.
Minuses:
- high Responsibility, as you have to be responsible for the safety of all the company's information;
- frequent business trips are possible.
Place of work
In organizations of various forms of ownership that have their own computer networks and in need of maintaining corporate information and important commercial information.
Important qualities
Communicability and skill work in a team. Creation and commissioning of protection systems is a collective work of several specialists: the head of the company's protected company, analytics, system designers, programmers. Everyone needs to find an approach and be able to put a task understandable to them.
Training at information security specialist
Higher education:
Universities
We invite you to familiarize yourself with our list of universities of information technologies (IT).
Information security specialist should know all Web environment technologies, as well as understand the ways of hacking access and damage to networks and projects.
Salary
Salary on 12/10/2019
Russia 25000-80500 ₽
Moscow 40000-200000 ₽
The level of remuneration of a specialist is determined by the welfare of the company, a list of job responsibilities, experience in the specialty, level of development of professional skills.
Stairs Career and Perspectives
By itself, this position is already one of the highest steps of career growth in the field of IT, above only the post of head of the department or information security department. Start a career in this field can IT specialists with incomplete or completed higher education, the experience of administering information security and Windows or UNIX operating systems. Employers' requirements for professional skills and skills of novice specialists are quite serious: even the applicants for a relatively low income should know the legislation of the Russian Federation for information security, the principles of operation of networks and means of cryptocrusts, modern software and hardware for information protection, as well as information security technologies. Salary on which young specialists can count on in the capital, from 40 thousand rubles.
The next level is a specialist with higher education in information technology or information protection, which has experience in providing information security for at least 2 years. In addition, applicants must have experience in conducting an audit and assessment of the risks of the information security system, the development skills of the regulatory and technical documentation for information security, to know international standards for information protection and own English at the level sufficient to read technical literature. Experts that meet the above requirements earn in Moscow to 80 thousand rubles.
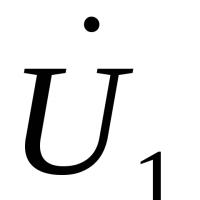 Magnetometry in the simplest version The ferrozond consists of a ferromagnetic core and two coils on it
Magnetometry in the simplest version The ferrozond consists of a ferromagnetic core and two coils on it Effective job search course search
Effective job search course search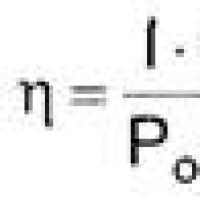 The main characteristics and parameters of the photodiode
The main characteristics and parameters of the photodiode How to edit PDF (five applications to change PDF files) How to delete individual pages from PDF
How to edit PDF (five applications to change PDF files) How to delete individual pages from PDF Why the fired program window is long unfolded?
Why the fired program window is long unfolded? DXF2TXT - export and translation of the text from AutoCAD to display a dwg traffic point in TXT
DXF2TXT - export and translation of the text from AutoCAD to display a dwg traffic point in TXT What to do if the mouse cursor disappears
What to do if the mouse cursor disappears