Windows restoration using AVZ. Setting up AVZ firmware - restore system after viruses. Ways to restore encrypted files for free
Simple and convenient AVZ utility, which can not only will help but also knows how to restore the system. Why is it necessary?
The fact is that after the invasions of the viruses (it happens that Avz kills them thousands), some programs refuse to work, all the settings were somewhere smoked and Windows somehow works not entirely correctly.
Most often, in this case, users simply reinstall the system. But as practice shows, it is completely optional, because with the same AVZ utility, you can restore almost any damaged programs and data.
In order to give you a more visual picture, I give a complete list of what can restoreAVZ.
The material is taken from the directory byAVZ - http://www.z-oleg.com/secur/avz_doc/ (copy and paste into the browser address bar).
Currently, there are the following firmware in the database:
1. Installation of parameters start.exe, .com, .pif files
This firmware restores the system response to EXE, COM, PIF, SCR files.
Indications for use: After removing the virus, programs stop running.
2. Internet Explorer protocol prefix settings for standard
This firmware restores the settings of the protocol prefixes in Internet Explorer
Indications for use: When entering the address of type www.yandex.ru there is his substitution to something www.seque.com/abcd.php?url\u003dwww.yandex.ru
3. Installation of start-up internet pages Explorer
This firmware restores the start page in Internet Explorer
Indications for use: Substitution start page
4. Internet Explorer search settings for standard
This firmware restores the search settings in Internet Explorer
Indications for use: When you press the "Search" button in IE, there is an appeal to some extraneous site
5. Installation of desktop settings
This firmware restores the desktop settings.
Recovery implies removal of all active elements of ACTIVEDESCTOP, wallpaper, removing locks on the menu that is responsible for setting up the desktop.
Indications for use: The desktops settings disappeared in the "Properties: Screen" window, an extraneous inscriptions or pictures are displayed on the desktop.
6. The date of all POLICIES (restrictions) of the current user
Windows provides a mechanism for the restrictions of the user actions, called Policies. Many malicious programs use this technology, since the settings are stored in the registry and it is easy to create or modify them.
Indications for use: The function of the conductor or other functions of the system are blocked.
7. The date of the message output during WinLogon
Windows NT and subsequent systems in the NT (2000, XP) line allow you to install the message displayed during the autoload.
This is used by a number of malicious programs, and the destruction of a malicious program does not lead to the destruction of this message.
Indications for use: During the loading of the system, a foreign post is entered.
8. Restoration of the conductor settings
This firmware resets a number of the conductor settings to the standard (reset primarily settings varyable by malicious programs).
Indications for use: Changed the conductor settings
9. Research of debuggers system processes
Registration of the system process debugger will allow a hidden launch application that is used by a number of malicious programs.
Indications for use: AVZ detects unidentified system processes debuggers, problems arise with the start of the system component, in particular after the restarting disappears the desktop.
10. Installation of download settings in SafeMode
Some malicious programs, in particular Bagle worm, damage the system load settings in protected mode.
This firmware restores the download settings in protected mode. Indications for use: The computer is not loaded in secure mode (SAFEMODE). Apply this firmware follows only in case of downloading problems in protected mode .
11.Block Task Manager
Locking Task Manager is applied by malware to protect processes from detection and deletion. Accordingly, the execution of this firmware relieves blocking.
Indications for use: Locking task manager, when you try to call the task manager, the message "Task Manager is locked by the administrator".
12. Clearing HijackThis Utility Ignor
The HijackThis utility stores a number of its settings in the registry, in particular, the list of exceptions. Therefore, for disguise from HijackThis, a malicious program is enough to register your executable files in the exception list.
Currently, a number of malicious programs that use this vulnerability are known. AVZ firmware Clearing HijackThis utility exception list
Indications for use: Suspicions that the HijackThis utility displays not all information about the system.
13. Clearing Hosts File
Clearing Hosts file comes down to searching for the hosts file, removing all meaning rows from it and adding a standard line "127.0.0.1 Localhost".
Indications for use: Suspicions that the HOSTS file is changed by a malicious program. Typical Symptoms - Update Lock antivirus software.
Control the contents of the HOSTS file can be using the manager Hosts file.built into AVZ.
14. Automatic correction SPL / LSP settings
Performs analysis sPI settings And in case of error detection, it automatically correct the errors found.
This firmware can be launched a re-unlimited number of times. After performing this firmware, it is recommended to restart the computer. Note! This firmware cannot be launched from the terminal session.
Indications for use: After removing the malicious program, Internet access disappeared.
15. Reset SPI / LSP and TCP / IP settings (XP +)
This firmware works only in XP, Windows 2003 and Vista. Its principle of operation is based on the reset and re-creation of SPI / LSP and TCP / IP settings using the NETSH regular utility, which is part of Windows.
Note! Apply the reset of settings only if necessary if there are unreasonable problems with Internet access after removing malicious programs!
Indications for use: After removing the malicious program, Internet access and the firmware execution "14. Automatic fixing SPL / LSP settings »Does not result.
16. Restoring the Explorer start key
Restores the registry key keys responsible for starting the conductor.
Indications for use: During the system loading, the conductor does not start, but manually running Explorer.exe.
17. Unlock registry editor
Unlocks the registry editor by removing a policy that prohibits its launch.
Indications for use: Unable to start the registry editor, when you try, a message is displayed that its launch is blocked by the administrator.
18. Full recreation of SPI settings
SPI / LSP sets up back up, after which it destroys them and creates on the standard that is stored in the database.
Indications for use: Heavy damage to SPI settings, unreasonable scripts 14 and 15. Apply only if necessary!
19. Clean the MountPoints database
Cleaning the MountPoints and MountPoints2 base in the registry. This operation often helps in the case when after infection of the Flash virus in the conductor does not open discs.
To perform recovery, it is necessary to mark one or more items and click the "Run Activated Operations" button. Pressing the "OK" button closes the window.
On a note:
Recovery is useless if a Trojan program runs on the system that performs such reconfigurations - you must first delete malicious programand then restore system settings
On a note:
To eliminate traces of most Hijacker, you must perform three firmware - "Reset Internet Explorer search settings to standard", "Restoring the Internet Explorer start page", "Resetting Internet Explorer Plug Settings to Standard"
On a note:
Any of firmware can be performed several times in a row without prejudice to the system. Exceptions - "5.
Restoring the desktop settings "(the operation of this firmware will reset all the settings of the desktop and have to re-select the design of the desktop and wallpaper) and" 10.
Restoring download settings in SafeMode "(this firmware re-sends the registry keys responsible for loading in safe mode).
To start recovery, first download unpack and run utility. Then press the file - the restoration of the system. By the way, you can still perform
We celebrate the checkboxes that you need and click to run operations. All, expect to perform :-) In the following articles, we will consider more problems, solve that the AVZ firmware will help us restore the system. So good luck to you.
The launch of the AVZ utility may be required when contacting the technical support of Kaspersky Lab.
Using the AVZ utility you can:
- get a report on the results of the system research;
- run the script provided by the technical support technician "Kaspersky Lab"
To create quarantine and delete suspicious files.
The AVZ utility does not send statistics, does not processes information and does not transmit it to the Kaspersky Lab. The report is stored on a computer in the form of HTML and XML formats that are available for viewing without the use of special programs.
The AVZ utility can automatically create quarantine and put copies of suspicious files and their metadata.
Objects placed in quarantine are not processed, are not transmitted to Kaspersky Lab and stored on the computer. We do not recommend recovering quarantine files, they can harm the computer.
What data are contained in the AVZ utility report
AVZ utility report Contains:
- Information about the version and date of the output of the AVZ utility.
- Information about anti-virus bases AVZ utilities and its basic settings.
- Information about the operating system version, the date of its installation and the rights of the user with which the utility is running.
- Results of searching for rootkits and interceptor programs of the main functions of the operating system.
- Results of the search for suspicious processes and information about these processes.
- The results of the search for common malicious programs on their characteristic properties.
- Error information found when checking.
- Search results of keyboard events, mouse or windows interceptor.
- Search results for open TCP and UDP ports that are used by malicious programs.
- Information about suspicious keys of the system registry, file names on disk and system settings.
- The search results for potential vulnerabilities and safety problems of the operating system.
- Information about the damaged settings of the operating system.
How to execute a script using the AVZ utility
Use the AVZ utility only under the guidance of the Technical Support Specialist "KAPERSKY Laboratory" as part of its appeal. Independent actions can damage the operating system and data loss.
- Download AVZ utility executable file.
- Run Avz5.exe on your computer. If the Windows Defender's SmartScreen Filter prevented the launch of avz5.exe, click More details → Perform in any case in the window Windows system protected your computer.
- Go to section File→ Run script.
- Insert the script in the input field, which you received from the Technical Support Specialist "Kapersky Lab".
- Click Run.
- Wait until the utility is completed and further recommendations of the Technical Support Specialist "KAPERSKY Laboratory".
Modern antiviruses covered various additional features so much that some users have questions in the process of using them. In this lesson, we will tell you about all key features AVZ antivirus works.
Let's consider as much as possible in practical examples, which represents AVZ. The main attention of the regular user deserves the following functions.
Checking the system for viruses
Any antivirus should be able to identify malicious software on and deal with it (treat or delete). Naturally, this feature is present in AVZ. Let's look at the practice that it is a similar check.
- Run AVZ.
- A small ultype window will appear on the screen. In the area marked in the screenshot below, you will find three tabs. All of them belong to the process of searching for vulnerabilities on the computer and contain different options.
- On the first tab "Search area" You need to mark those folders and sections hard diskthat you want to scan. Slightly below you will see three lines that allow you to enable additional options. We put the marks opposite all positions. This will make a special heuristic analysis, scan additionally running processes and identify even potentially dangerous software.
- After that go to the tab "File Types". Here you can choose which data the utility should scan.
- If you make an ordinary check, then it is enough to celebrate the item "Potentially dangerous files". If the viruses have launched the roots deeply, then you should choose "All files".
- AVZ, in addition to ordinary documents, easily scans the archives than many other antiviruses do not boast. This tab includes or disconnected this check. We recommend to remove the tick in front of the lines of checking the archives of a large volume if you want to achieve the maximum result.
- In total, you have the second tab should look like this.
- Next, go on the last section "Search parameters".
- At the very top you will see a vertical slider. We shift it completely up. This will allow the utility to respond to all suspicious objects. In addition, we include checking the API and Rootkit interceptors, search for keyloker and check SPI / LSP settings. General form The last tab you must have approximately such.
- Now you need to configure the actions that AVZ will take in the detection of a threat. To do this, first need to mark the mark in front of the string "Perform treatment" In the right window of the window.
- Opposite each type of threats, we recommend putting a parameter "Delete". The exception is only the threats of the type "Hacktool". Here we advise you to leave the parameter "Treat". In addition, put the marks opposite the two lines that are located below the threat list.
- The second parameter will allow the utility to copy the unsafe document into a specially designated place. You can then view all the contents, then boldly remove. This is done so that you can eliminate those that are actually no (activators, key generators, passwords, and so on) from the list of infected data.
- When all the settings and search parameters are exhibited, you can start scanning. To do this, press the appropriate button "Start".
- The check process will begin. Its progress will be displayed in a special area. "Protocol".
- After some time, which depends on the amount of data being checked, the scan will end. The protocol will appear about the completion of the operation. There will immediately be the total time spent on the analysis of files, as well as statistics for checking and identified threats.
- By clicking on the button that is marked in the image below, you can see all suspicious and suspicious in a separate window. dangerous objectswhich were identified by AVZ during the inspection.
- There will be a path to a dangerous file, its description and type. If you put a mark next to the title of such software, you can move it to quarantine or removed from the computer. Upon completion of the operation, press the button Ok at the bottom.
- Cleaning a computer, you can close the program window.










System functions
In addition to the standard check for malware, AVZ can perform a lot of other functions. Let's consider those that may be useful to the ordinary user. In the main menu of the program at the very top click on the string "File". As a result, a context menu appears in which all available auxiliary functions are located. 
The first three lines are responsible for starting, stopping and pause scanning. This is analogues of the appropriate buttons in the AVZ main menu. 
System Study
This feature will allow the utility to collect all the information about your system. It seems not the technical part, but hardware. Such information includes a list of processes, various modules, system files and protocols. Once you click on the string "System Study", A separate window will appear. In it you can specify what information AVZ should collect. After installing all the required flags, you should click the button. "Start" at the bottom. 
After that, the save window opens. In it you can choose the location of the document with detailed information, as well as specify the name of the file itself. Please note that all information will be saved as an HTML file. It opens with any web browser. When specifying the path and name for the saved file, you need to click "Save".
As a result, the system scanning and information collection will be launched. At the very end, the utility will display a window in which you will be prompted to immediately view all the information collected. 
System Restore
With this set of functions, you can return the elements of the operating system in their initial look and reset various settings. Most often, malicious software is trying to block access to the registry editor, task controls and register its values \u200b\u200bin the HOSTS system document. Unlock similar items you can use the option "System Restore". To do this, it is enough to click on the name of the option itself, after which it is ticked by those actions that need to be made. 
After that you need to click "Perform marked operations" In the bottom area of \u200b\u200bthe window.
A window will appear on the screen in which the actions should be confirmed. 
After some time, you will see a message about the completion of all tasks. Just close this window by clicking the button. Ok.
Scripts
In the list of parameters there are two lines related to work with scripts in AVZ - "Standard Scripts" and "Run the script".
By clicking on the line "Standard Scripts"You will open the window with a list of ready-made scripts. You will need only to mark those of them that you want to run. After that, press the button below the window "Run".
In the second case, you run the script editor. Here you can write it on your own or download it from the computer. Do not forget to write after writing or downloading "Run" In the same window. 
Update base
This item is important from the entire list. By clicking on the appropriate string, you will open the AVZ database update window. 
We do not recommend settings in this window. Leave everything as it is and press the button "Start".
After some time, a message appears on the screen that the database update is completed. You can only close this window. 
View the contents of quarantine folders and infected
By clicking on the lines in the list of options, you can view all potentially dangerous files that detected AVZ during your system scanning. 
In the open windows, you can finally delete similar files or restore them if they do not really represent threats. 
Please note that suspicious files are placed in the folder data, you must install the appropriate checkboxes in the system scan settings. 
This is the last option from this list that may need an ordinary user. How can I understand from the name, these parameters allow you to save to the computer pre-configuration of the antivirus (search method, scanning mode, and so on), as well as download it back. 
When saving, you will need only to specify the name of the file, as well as the folder to which you want to save it. When loading the configuration, it is enough to highlight the desired file. with settings and click the button "Open".
Output
It would seem that this is obvious and the well-known button. But it is worth mentioning that in some situations - when a particularly dangerous software is detected, AVZ blocks all the ways of its own closure, except for this button. In other words, you will not be able to close the program combination of keys "Alt + F4" Either when you click on a banal cross in the corner. This is done so that viruses cannot prevent the correct operation of AVZ. But clicking this buttonYou can close the antivirus if necessary, for sure. 
In addition to the described options, there are also others in the list, but they will most likely not need to be ordinary users. Therefore, to focus on them we did not. If you still need help on the use of not described functions, write about it in the comments. And we are moving further.
List of services
In order to see the full list of services that AVZ offers, you need to click on the string "Service" At the very top of the program. 
As in the past section, we are running only by those of them that can be useful to the usual yowser.
Process Manager
By clicking on the first line from the list, you will open the window. "Process Manager". It can see a list of all executable files that are running on a computer or laptop in this moment time. In the same window, you can read the description of the process, find out its manufacturer and the full path to the executable file itself. 
You can also complete this or that process. To do this, it is enough to select the desired process from the list, and then click on the corresponding button in the form of a black cross on the right side of the window. 
This service is an excellent replacement for the standard task dispatcher. Special value service purchases in situations when "Task Manager" blocked by a virus.
Service Manager and Drivers
This is the second service in the overall list. By clicking on the string with the same name, you will open the Office Management window and drivers. You can switch between them using a special switch. 
In the same window, a description of the service itself is attached to each item, and the location of the executable file is attached. 
You can select the desired item, after which you will be available on, disconnecting or fully deleting the service / driver. These buttons are located at the top of the workspace. 
Manager autorun
This service will allow you to fully configure autorun parameters. Moreover, in contrast to standard managers, this list includes system modules. By pressing the string with the same name, you will see the following. 
In order to disable the selected item, you just need to remove the tick next to its name. In addition, it is possible to remove the necessary record at all. To do this, simply select the desired string and click at the top of the window on the button in the form of a black cross. 
Please note that the remote value cannot be returned. Therefore, be extremely attentive, in order not to erase vital system records of autoload.
Hosts file manager
We mentioned a little higher about the fact that the virus sometimes prescribes its own values \u200b\u200bin the system file HOSTS. And in some cases, malicious software also blocks access to it so that you cannot correct the changes made. This service will help you in such situations. 
By clicking on the list shown in the image above, you will open the Manager window. You can not add your own values \u200b\u200bhere, but you can delete existing ones. To do this, select the desired string with the left mouse button, after which we press the removal button, which is located in the upper area of \u200b\u200bthe working area. 
After that, a small window will appear in which you need to confirm the action. To do this, press the button "Yes".
When the selected line is removed, you only need to close this window.
Be careful and do not delete those strings whose assignment you do not know. To file. HOSTS There are not only viruses, but also other programs can prescribe their values.
System utilities
Using AVZ, you can also start the most popular system utilities. You can see their list provided if you drive a mouse pointer to a string with the appropriate name. 
By clicking on the name of this or that utility, you run it. After that, you can make changes to the registry (REGEDIT), configure the system (msconfig) or check system files (SFC).
These are all services that we wanted to mention. Novice users are unlikely to need protocol manager, expansion and other additional services. Such functions will be more advanced more advanced users.
Avzguard
This function was designed to combat the most cunning viruses that are not deleted in standard ways. She simply makes malicious programs into the list of incorrect software, which is forbidden to perform his operations. To enable this feature you need to click on the string "Avzguard" In the upper area AVZ. In the drop-down window, click on the item "Enable Avzguard".
Be sure to close everything third-party applications Before turning on this function, since otherwise they will also be in the list of incredulous software. In the future, the work of such applications may be violated.
All programs that will be marked as trusted will be protected from removal or modification. And the work of untrusted software will be suspended. This will allow you to calmly delete dangerous files using standard scanning. After that, you should turn off AvzGuard back. To do this, click on the similar line at the top of the program window, after which we press the function to disable the function. 
Avzpm.
The technology specified in the title will monitor all launched, stopped and modified processes / drivers. To use it, you must first enable the appropriate service.
Click at the top of the window on the Avzpm string.
In the drop-down menu, click on the line "Install the Extended Monitoring Driver".
Within a few seconds, the necessary modules will be installed. Now when you detect changes to any processes, you will receive the appropriate notification. If you no longer need a similar monitoring, you will need to simply click on the string marked in the image below. This will allow you to unload all AVZ processes and delete the previously installed drivers. 
Please note that the AVZGUARD and AVZPM buttons can be gray and inactive. This means that you have the X64 operating system installed. On the OS with this discharge, the mentioned utilities unfortunately do not work.
This article approached its logical conclusion. We tried to tell you how to use the most popular functions in AVZ. If you have questions left after reading this lesson, you can ask them in the comments to this entry. We are pleased to pay attention to every question and try to give the most detailed answer.
Excellent program to remove viruses and restore system - AVZ (Zaitsev Anti-Virus). You can download AVZ by clicking on the Orange Button after generating links.And if the virus blocks the download, then try to download the entire anti-virus set!The main features of AVZ are the detection and removal of viruses.
AVZ anti-virus utility is designed to detect and delete:
- Spyware and Adware Modules are the main purpose of the utility
- DIALER (Trojan.dialer)
- Trojan programs
- Backdoor modules
- Network and postal worms
- Trojanspy, TrojandownLoader, Trojandropper
The utility is a direct analogue of Trojanhunter and Lavasoft Ad-Aware 6 programs. The primary task of the program is to remove Spyware and Trojan programs.
The features of the AVZ utility (in addition to the typical signature scanner) is:
- The microprogram of the heuristic check of the system. Firmware is searching for well-known Spyware and viruses by indirect features - based on the registry analysis, files on the disk and in memory.
- Updated base of safe files. It includes digital signatures of tens of thousands of system files and files of well-known secure processes. The base is connected to all AVZ systems and works on the "own / alien" principle - the secure files are not entered into quarantine, the deletion and output and output are locked for them, the base is used by anti-tat, the file search system, various analyzers. In particular, the built-in processes manager highlights secure processes and services in color, searching for disk files can be excluded from the search for well-known files (which is very useful when searching for the Disk Trojan programs);
- Built-in RootKit detection system. RootKit is searching without the use of signatures based on the study of basic system libraries for intercepting their functions. AVZ can not only detect Rootkit, but also to correctly lock the operation of the Usermode Rootkit for its process and Kernelmode Rootkit at the system level. RootKit contractions applies to all AVZ service functions, as a result, the AVZ scanner can detect disguised processes, the search system in the registry "sees" the masked keys, etc. Anti-troops is equipped with an analyzer that detects the processes and services disguised by Rootkit. One of the main features of the rootkit counteraction system is its performance in Win9x (the common opinion on Rootkit's absence, working on the Win9x platform is deeply erroneous - hundreds of Trojan programs, intercepting APIs for masking their presence, for distortion aPI works functions or tracking their use). Another feature is a universal detection and blocking system Kernelmode Rootkit, workable under Windows NT, Windows 2000 Pro / Server, XP, XP SP1, XP SP2, Windows 2003 Server, Windows 2003 Server SP1
- Detector keyboard spies (Keylogger) and Trojan DLL. The search for Keylogger and Trojan DLL is conducted on the basis of the system analysis without the use of the signature base, which allows you to confidently detect the unknown Trojan DLL and KEYLOGGER.
- Neuroanalyzer. The AVZ signature analyzer comes with a neuroemologist, which allows you to study suspicious files with a neural network. Currently, neurallet is used in the keylogger detector.
- Built-in WINSOCK SPI / LSP Settings Analyzer. Allows you to analyze the settings, diagnose possible mistakes In the setting and produce automatic treatment. The ability to automatically diagnose and treatment is useful for novice users (in utilities of type LSPFIX there is no automatic treatment). To study SPI / LSP manually in the program there is a special LSP / SPI settings manager. The WinSOCK SPI / LSP analyzer is applied to the action of antiooker;
- Built-in processes, services and driver dispatcher. Designed to explore running processes And downloaded libraries, running services and drivers. The operation of the processes of processes is subject to the action of anti-troops (as a result - he "sees" processes masked by rootkit). Process Manager is associated with the secure AVZ database, identified safe and system files are highlighted by color;
- Built-in utility for searching for files on the disk. Allows you to search for a file on various criteria, the search system features exceed the system search capabilities. The operation of the search system is subject to the action of anti-troops (as a result - the search "sees" files masked by roottite and can delete them), the filter allows you to exclude from the search results files identified by AVZ as secure. The search results are available as a text protocol and in the form of a table in which you can mark the group of files for subsequent removal or quarantine removal or room.
- Built-in utility for data search in the registry. Allows you to search for keys and parameters for a specified sample, the search results are available as a text protocol and in the form of a table in which you can mark multiple keys to export or delete them. The search for the search system extends the action of anti-troops (as a result - the search for "sees" the registry keys masked by rootkit and can delete them)
- Built-in TCP / UDP open port analyzer. It disseminates the action of anti-troops, in Windows XP, the process is displayed for each port. The analyzer relies on the renewed database of ports of famous Trojan / Backdoor programs and well-known system services. Search ports of Trojan programs is included in the main system check algorithm - when suspicious ports are detected in the protocol, warnings are displayed indicating what Trojan programs are peculiar to the use of this port
- Built-in common resource analyzer, network sessions and opened files. Works in Win9x and NT / W2K / XP.
- Built-in Analyzer Downloaded Program Files (DPF) - Displays DPF items, connected to all AVZ Sustems.
- System recovery firmware. Firmware carry out recovery internet Settings Explorer, program start settings and other system parameters damaged by malicious programs. Recovery starts manually, the parameters restored are specified by the user.
- Heuristic deletion of files. Its essence is that if the malicious files were removed during treatment and this option is enabled, the system is automatic, covering classes, BHO, IE and Explorer extensions, all available AVZ types of autorun, WinLogon, SPI / LSP, etc. . All found links to the remote file are automatically cleaned with information in the protocol of information that specifically and where it was cleaned. For this cleaning, the microprogram engine of the treatment of the system is actively used;
- Check archives. Starting from version 3.60 AVZ supports checking archives and composite files. At the moment, the archives of the format of ZIP, RAR, CAB, GZIP, TAR are checked; email letters and MHT files; CHM archives
- Check and treatment of NTFS streams. NTFS Checking Flows In Avz Starting from version 3.75
- Control scripts. Allow the administrator to write a script that performs a set of specified operations on the user's PC. Scripts allow you to apply AVZ in the corporate network, including its launch during the system loading.
- Process Analyzer. The analyzer uses neural networks and analysis firmware, it turns on when the extended analysis is turned on at the maximum level of heuristics and is designed to search for suspicious processes in memory.
- Avzguard system. It is intended to combat difficult malicious programs, besides AVZ, protect the applications specified by the user, for example, other anti-spyware and antivirus programs.
- System direct access to the disk to work with blocked files. Works on FAT16 / FAT32 / NTFS, supported on all NT ruler operating systems, allows a scanner to analyze blocked files and placing them into quarantine.
- Driver monitoring processes and AVZPM drivers. Designed to track start and stopping processes and download / unload drivers to search for masking drivers and detecting distortions in describing processes and drivers structures created by DKOM rootkitams.
- Driver Boot Cleaner. Designed to clean the system (delete files, drivers and services, registry keys) from Kernelmode. Cleaning operation can be performed both in the process of rebooting the computer and during treatment.
Restore system parameters.
- Restore parameters start.exe .com .pif
- Reset IE settings
- Restoring desktop settings
- Delete all user restrictions
- Deleting a message in WinLogon
- Restoring conductor settings
- Removing the debuggers of system processes
- Restore Safe Mode Download Settings
- Unlock task dispatcher
- Clearing the Host file
- Fixing SPI / LSP Settings
- Reset SPI / LSP and TCP / IP settings
- Unlocking the registry editor
- Clearing MountPoints Keys
- Replacing DNS servers
- Deleting Proxy Setup for IE / Edge Server
- Deleting Google restrictions
Program Tools:
- Process Manager
- Service Manager and Drivers
- Modules of nuclear space
- Manager internal DLL
- Search in the registry
- Search files
- Search by Coocie.
- Manager autoload
- Browser expansion manager
- Manager of Apgestions Control Panel (CPL)
- Expansion Manager Expansion
- Print Extensions Manager
- Task Planner Manager
- Protocol manager and handlers
- DPF Manager
- Manager Active Setup.
- WinSock SPI Manager
- Hosts file manager
- TCP / UDP port manager
- General Network Resources Manager and Network Connections
- Set of system utilities
- Checking the secure file database file
- Checking Microsoft Safety Catalog File
- Calculation of MD5 files of files
Here is such a rather big set to save your computer from various infection!
16.08.2019
Dedicated AVZ.I want to share with you a number of knowledge for the possibilities of this wonderful utility.
Today it will be about the means of restoring the system, which often can save your computer after infection with viruses and other horrors of life, as well as solve a number of systemic problems arising in a consequence of certain errors.
Useful will be any.
Enterprise
Before proceeding, traditionally, I want to offer you two material formats, namely: video format or text. Video here:
Well, the text below. See what option to you closer.
General description of the functionality of the program
What is it for the means of recovery? This is a set of firmware and scripts that help to return to the operating status of certain functions of the system. Which for example? Well, let's say, return or registry editor, clear the HOSTS file or reset the IE settings. In general, I give it entirely with the description (in order not to reinvent the bike):
- 1. Restore the parameters of startup.exe, .com, .pif files
Indications for use: After removing the virus, the programs stop running. - 2. Reset Internet Explorer Protocols for Standard
Indications for use: when entering the address of type www.yandex.ru there is his substitution to something www.seque.com/abcd.php?url\u003dwww.yandex.ru - 3. Restoring the Start page Internet Explorer
Indications for use: Substitution of the start page - 4. Reset Internet Explorer search settings for standard
Indications for use: When you press the "Search" button in IE, there is an appeal to some extraneous site. - 5. Restore desktop settings
This firmware restores the desktop settings. Recovery implies removal of all active elements of ACTIVEDESCTOP, wallpaper, removing locks on the menu that is responsible for setting up the desktop.
Indications for use: Disappeared desktop configuration bookmarks in the Properties: Screen window, outsiders are displayed on the desktop. - 6. Removing all policies (restrictions) The current user.
Indications for use: The function of the conductor or other functions of the system is blocked. - 7. Deleting a message displayed during WinLogon
Windows NT and subsequent systems in the NT (2000, XP) line allow you to install the message displayed during the autoload. This is used by a number of malicious programs, and the destruction of a malicious program does not lead to the destruction of this message.
Indications for use: During the loading of the system, an extraneous message is entered. - 8. Restoring conductor settings
Indications for use: Changed Conduct Settings - 9. Removing system processes debuggers
Indications for use: AVZ detects unidentified system processes debuggers, problems arise with the start of the system component, in particular, after a restart, the desktop disappears. - 10. Restore download settings in SafeMode
Some malicious programs, in particular Bagle worm, damage the system load settings in protected mode. This firmware restores the download settings in protected mode.
Indications for use: The computer is not loaded in the secure mode (SAFEMODE). Apply this firmware follows only in case of problems with the load in protected mode. - 11. Unlock task dispatcher
Indications for use: Locking task manager, when you try to call the task manager, the message "Task Manager is blocked by the administrator". - 12. Clearing the HijackThis Utility Ignore List
The HijackThis utility stores a number of its settings in the registry, in particular, the list of exceptions. Therefore, for disguise from HijackThis, a malicious program is enough to register your executable files in the exception list. Currently, a number of malicious programs that use this vulnerability are known. AVZ firmware Clearing HijackThis utility exception list
Indications for use: suspicion that the HijackThis utility displays not all information about the system. - 13. Clearing Hosts File
Clearing Hosts file comes down to searching for Hosts file, removing all significant rows from it and add a standard line "127.0.0.1 localhost".
Indications for use: Suspicions that the HOSTS file is changed by a malicious program. Typical symptoms - blocking the update of antivirus programs. You can monitor the contents of the HOSTS file using the Hosts Manager of the file built into AVZ.
Performs an analysis of SPI settings and in case of error detection, it automatically fix the errors found. This firmware can be launched a re-unlimited number of times. After performing this firmware, it is recommended to restart the computer. Note! This firmware cannot be launched from the terminal session.
Indications for use: After removing the malicious program, Internet access disappeared.
This firmware works only in XP, Windows 2003 and Vista. Its principle of operation is based on the reset and re-creation of SPI / LSP and TCP / IP settings using the NETSH regular utility, which is part of Windows. Details about resetting settings can be found in the Microsoft Knowledge Base - pay attention! Apply the reset of settings only if necessary if there are unreasonable problems with Internet access after removing malicious programs!
Indications for use: After removing the malicious program, Internet access and firmware execution "14. Automatic fixing of the SPL / LSP settings" does not give results ".
Indications for use: In the course of loading the system, the conductor does not start, but manually running Explorer.exe is possible.
Indications for use: Unable to start the registry editor, when trying, a message is displayed that its launch is blocked by the administrator.
Indications for use: Heavy Damage to SPI settings, Focipal scripts 14 and 15. Apply only if necessary!
Cleaning the MountPoints and MountPoints2 base in the registry.
Indications for use: This operation often helps in the case when after infection of the Flash virus in the conductor does not open discs- On a note:
On a note:
To eliminate traces of most Hijacker, you must perform three firmware - "Reset Internet Explorer search settings for standard", "Restore the Start page of Internet Explorer", "Reset Internet Explorer Protocol Plug Settings for Standard"
On a note:
Any of firmware can be performed several times in a row without prejudice to the system. Exceptions - "5. Restore the desktop settings" (the operation of this firmware will reset all desktop settings and will have to re-select the desktop coloring and wallpaper) and "10. Restore the download settings in SafeMode" (this firmware re-sends the registry keys responsible for downloading safe mode).
Useful, is it not true?
Now about how to use.
Download Running, Use
Actually everything is simple.
- Kacham from here (or from somewhere else) antivirus utility AVZ..
- Unpack the archive with her somewhere convenient
- Follow in the folder where we unpacked the program and launch there avz.exe..
- In the program window, choose "File" - "System Restore".
- I celebrate the checkboxes the necessary items and davim in the button " Perform marked operations".
- We are waiting and enjoying the result.
Here are such things.
Afterword
It must be said that it works with a bang and eliminates a number of extra televitations. So to speak, everything is at hand, quickly, simple and effectively.
Thanks for attention;)
Thank you for your help in preparing the material of computer masters service Center Run.rf. These guys you can order repair of laptops and netbooks in Moscow.
Malicious programs are introduced into the personal computer system, they cause significant damage to the entire data volume. At the moment, the pest programs are created with different purposes, so their actions are directed to the adjustment different structures Personal computer system.
The common and consequences obvious to the user are problems in working with the Internet, violations in the work of devices attached to the PC.
Even if the pest was detected and destroyed - this does not exclude the loss of information and other problems that arise in subsequent work. Listed options can be infinitely, most often the user detects a complete or partial blocking of access to the World Wide Network, refusal to work external devices (mouse, flash card), an empty desktop and so on.
Listed consequences are observed due to the changes that the program has made - the pest to the system files of the personal computer. Such changes are not eliminated with the elimination of the virus, they must be corrected independently, or resort to the help of specialists. In fact, the work of this kind does not require special training, and any advanced user can perform it, having studied the relevant instructions.
In practice, work on the organization of restoring the operating system is distinguished by several approaches depending on the reasons that led to a failure. Consider each of the options in detail. A simple way accessible to each user is a rollback OS to a recovery point, when the work of a personal computer complied with the requirements of the user. But very often this decision is unsatisfactory, or it is impossible to implement it for objective reasons.
How to restore the OS, if the entry into the PC system is impossible?
Running system recovery occurs as follows. Start menu \\ Control panel \\ system restores. At this address, choose the recovery point you need and start the process. After a while, the work will be completed and the computer is ready for normal functioning. Reception is quite applicable to eliminate certain types of viruses, since changes occur at the registry level. This option to restore the operating system is considered the simplest and enters the set of standard Windows tools. Step-by-step instructions and a certificate with detailed comments of the process will help you master the recovery of the workburn and computer even if the user does not quite confidently feel as an administrator of the PC.
Another common option to restore the OS is the start of the procedure from the external medium. This option is complicated by some moments, for example, it is necessary to have an image of the system on a flash map or disk and take care of the presence of such a copy in advance. In addition, it is often necessary to have certain skills in working with the BIOS system. The image of the operating system on the outer carrier is the optimal option if the recovery is not possible, since the virus has blocked the input to the computer system. There are other options.
Using the standard Windows tools to restore the OS is not possible, if such an input is not possible, or there are other reasons for preventing the execution of the operation in standard mode. Situation is solvable using the ERD Commander tool (ERDC).
How does the program functions, we will examine the situation consistently. The first step is to load the program. The second step is to launch the SYST EM Restore Wizard tool, it is with its help that the OS rollback is performed at the specified recovery position.
As a rule, each tool has several checkpoints in stock, and in eighty percent of cases, the operations of the personal computer will be completely reanimated.
AVZ utility tools
The following tool in operation does not require any special skills and user skills. Software Developed by Oleg Zaitsev and is designed to search and destroy all types of viruses and malicious programs. But besides the main function, the utility restores most of the system settings that have been attacked or a change in pest viruses to it.
What problems can the presented program can solve? The main thing is to restore system files and settings that have been attacked viruses. The utility copes with damaged drivers of programs that refuse to start after recovery. When problems arise in browsers or in case of blocking access to the Internet and many other troubles.
Activate the recovery operation at the file \\ system restores and select the operation that is necessary. The figure shows the microprogram interface that operates the utility, we will give the characteristic of each of them.
As you can see, the operation set is represented by 21 points, and the name of each of them explains its appointment. Note that the possibilities of the program are quite diverse and it can be considered universal tools in resuscitation not only the system itself, but also to eliminate the effects of viruses with system data.
The first parameter is used if the consequences of the attack of viruses and the OS recovery procedures refuse to work the user-needed program. As a rule, it happens if the pest penetrates files and program driver and made any changes to the information recorded there.
The second parameter is necessary when viruses have been submented domains when entering them to the browser search system. Such a substitution is the first level of adjusting the interaction of system operating system system files and the Internet. This function of the program is usually without a trace eliminates the changes made without trying to detect them, but simply exposing the total formatting of the entire amount of prefix data and protocols by replacing them with the standard settings.
The third parameter resumes the configuration of the online browser start page. As in the previous case, the default program corrects the problems internet browser Explorer.
The fourth parameter adjusts the work search engine and installs standard mode Work. Again, the procedure concerns the default browser.
During the problem of the functioning of the desktop (the appearance of banners, drawings, foreign entries on it) activate the fifth item of the program. Such consequences of malware have been very popular for a couple more years ago and delivered a lot of problems to users, but also the penetration into the operating system of PC such pacishers is not excluded.
The sixth item is required if the program-harmful spruce has limited the user's actions when performing a number of commands. These restrictions can be different in nature, and since the access settings are stored in the registry, the malicious programs most often use this information to adjust the user's work with its PC.
If a third-party message appears when booting OS, it means that the program-harm is able to escape to the Windows NT launch parameters. The restoration of the OS, which destroyed the virus does not remove this message. In order to remove it, you must activate the seventh menu parameter AVZ utility.
The eighth menu parameter, according to the title, restores the conductory settings.
Sometimes the problem is manifested in the form of interruptions in the operation of system components, for example, during the launch of the Personal computer, the desktop disappears. The AVZ utility conducts the diagnosis of these structures and makes the necessary adjustments using the tool menu item.
OS boot problems in safe mode are eliminated by paragraph ten. Detect the need to activate this point of multiprogram under consideration here the utility simply. They manifest themselves with any attempts to work in safety mode.
If task manager is blocked, you must activate the Eleven menu item. Viruses on behalf of the administrator make changes to the activation of this section of the operating system, and instead of the working window a message appears that the task manager is blocked.
The HijackThis utility as one of the main features uses storage in the list of exception list. For the virus, it is enough to penetrate the database of the utility and register files in the registry list. After that, he can independently restore an unlimited number of times. Cleaning the registry utility occurs due to activation of the twelfth item of the AVZ settings menu.
The next, thirteenth point, allows you to clear the HOSTS file, this file modified by the virus can cause difficulties when working with the network, block some resources, interfere with updating the databases of antivirus programs. Working with this file will be dismantled in more detail below. Unfortunately, almost all viral programs are striving to edit this file, which is due, firstly, with ease of making such changes, and the consequences may be more than significant and after removing viruses, information recorded in the file may be direct gate for penetration into OS new pests and spies.
If Internet access is blocked, this usually means errors in the SPI settings. Their correction will occur if you activate the Fourteen menu item. It is important that this setup item cannot be used from the terminal session.
Similar functions are laid in the fifteenth menu item, but its activation is possible only with work in such as XP, Windows 2003, Vista. You can use this multiprogram if attempts to correct the situation with the network input using the previous setting did not bring the desired result.
The capabilities of the sixteenth point menu are aimed at restoring the registry key keys that are responsible for launching the Internet browser.
The next step in working to restore OS parameters after the virus attack is unlocking the registry editor. As a rule, external manifestation - it is impossible to upload a program to the network.
The following four items are recommended to be applied only if the damage to the operating system is so catastrophic that by and large there is no difference in whether they will be eliminated using such methods or as a result it will be necessary to reinstall the system entirely.
So, the eighteenth item recreates initial settings SPI. The nineteenth item clears the Mount Points / 2 registry.
The twentieth point removes all static routes. Finally, the last, twenty-first item erases all DNS connections.
As can be seen, the premises of the utility covers almost all areas in which the program can penetrate the program and leave their active trace, to detect which is not so simple.
Since anti-virus applications do not guarantee one hundred percent protection of your PC operating system, we recommend that you have such a program in the arsenal of control tools computer viruses All kinds and shapes.
As a result of the treatment of a personal computer, the devices connected to it are not operating.
One of the popular ways to mask spyware is to establish your viral driver in addition to real software. In this situation, the real driver is most often the mouse file or keyboard. Accordingly, after the virus is destroyed, its track remains in the registry, for this reason the device to which the pest was able to join stops working.
A similar situation is observed with incorrect work in the process of removing Kaspersky Anti-Virus. It is also associated with the specifics of the program installation, when its installation on the PC uses the Klmouflt auxiliary driver. In the Caspership situation, this driver must be found and completely removed from the system of a personal computer in accordance with all the rules.
If the keyboard and mouse refuse to function in the right mode, first of all you need to restore the registry keys.
Keyboard :
HKEY_LOCAL_MACHI NE \\ SYSTEM \\ CURREN TCONTROLSET \\ CONT ROL \\ CLASS \\ (4D36E 96B-E325-11CE-BF C1-08002BE10318)
UpperFilters \u003d KBD ClassMouse :
HKEY_LOCAL_MACHI NE \\ SYSTEM \\ CURREN TCONTROLSET \\ CONT ROL \\ CLASS \\ (4D36E 96F-E325-11CE-BF C1-08002BE10318)
UpperFilters \u003d Mou Class
The problem of inaccessible sites
The effects of malware attacks may be the inaccessibility of some resources on the Internet. And these consequences are the result of changes that have managed to make viruses into the system. The problem is detected immediately or after some time, but if as a result of the actions of the pest programs, it manifested after some time, eliminate it will not be difficult.
There are two blocking options and the most common is the adjustment of the Hosts file. Second option to create false static routes. Even if the virus is destroyed, the changes made by them into these tools will not be eliminated.
The document under consideration is located in the system folder on the disk of S. Its address and location can be found here: C: \\ Windows \\ System 32 \\ Drivers \\ etc \\ hosts. To quickly search, usually use the command string from the Start menu.
If, using the specified procedure, the file is not possible to find, it may mean that:
The viral program has changed his location in the registry;
The file document has the "hidden" parameter.
In the latter case, change the search characteristics. At the address: folder parameters / View Find the string "Show hidden files" and install the label, expanding the search range.
The hosts file contains the information of the conversion of the letter name of the site domain to its IP address, so the program-harmful airs prescribe in it adjustments that can redirect the user to other resources. If this happened, then when entering the address of the desired site, it opens completely different. In order for these changes to return to the initial state and fix it, you need to find this file and analyze its contents. Even an inexperienced user will be seen that the virus has been corrected, but if it causes certain difficulties, you can restore standard settings, thereby removing all changes made to the file.
As for the correction of routes, the principle of action is the same. However, in the process of interaction between the PC operating system and the Internet, the priority always remains behind the HOSTS file, so its recovery is enough to work in standard mode.
The complexity occurs if the required file cannot be found, since the virus changes its location in system folders. Then you need to correct the registry key.
HKEY_LOCAL_MACHI NE \\ SYSTEM \\ CURREN TCONTROLSET \\ SERV ICES \\ TCPIP \\ Param Eters \\ Databasepa Th
Viruses that are included in the Win32 / Vundo group in inchorage conversion of Hosts files, exceed most of their malicious fellows. It changes the name of the file itself, washing the Latin letter O and replacing a sign on a Cyrillic letter. Such a file is no longer engaged in converting the domain name of sites to the IP addresses, and even if the user will restore this file, the result of the work will remain the same. How to find a genuine file? If doubts arise in the fact that the object you need the object we need, carry out the following procedure. The first step is to activate the display mode of hidden files. We explore the catalog, it looks like, as it is presented in the figure.

Here are two identical fileBut since the OS does not allow the use of identical items, it is obvious that we are dealing with a false document. Determine which one is correct, and which is not, simply. The virus creates a bulk file and numerous adjustments, so the result of its depression in the figure is represented by a hidden file with a volume of 173 KB.
If you open a file document, the information in it will contain such lines:
31.214.145.172 vk.com - a string that can replace the IP address of the site
127.0.0.1 avast.com - the line of the file registered with the virus in order to prohibit access to the site of the antivirus program
Above, we have already noted that you can block individual resources using the creation of incorrect routes in the routing table. How can the situation be resolved, consider sequence of actions.
If the HOSTS file does not have malicious adjustments, and the work with the resource is not possible, the problem lies in the route table. A few words about the essence of the interaction of data tools. If the HOSTS file is registered the correct adaptive address of the domain, then it is redirected at this address to an existing resource. As a rule, the IP address does not belong to the range of local subnet addresses, because redirection occurs by the router gateway, which is determined by the Internet connection settings.
If you adjust the route entry for a specific IP address, then automatic connection will occur based on this record. Provided that there is no such route, or the gateway does not work, the connection will not occur, and the resource will remain inaccessible. Thus, the virus can delete the entry in the route table and block absolutely any site.
Routes created for specific sites remain in the HKLM registry database. Upgrading the route occurs when the Route Add or manual data adjustment is activated. When statically, the routes are missing, the table section is empty. You can view the Routing Data List by applying the Route Print command. Add it as follows:

Active routes:

The table presented above is standard for a PC with a single network card, and the network connection setting parameters:
IP address 192.168.0.0
mask 255.255.255.0.
default gateway 192.168.0.1
The entry presented above includes the IP address of the network with an encoding of 192.168.0.0 and an ending the coding mask 255.255.255.0. If you decrypt this data, then the information is as follows. The mask includes the entire volume of nodes with an equivalent older address. According to the metric system, the first three bytes of the subnet mask are equal to 1 in all PC operating systems (an exception is a decimally, where the value is 255 and hexadecimally, where the value is 0 * FF). The youngest part of the address of the accepted nodes is in the range of 1-254.
In accordance with the information presented above, the younger address has an encoding - 192.168.0.0, this code is the network address. Senior address with encoding 192.168.0.255 is characterized as broadcast address. And if the first code eliminates its use for data exchange, the second code is just designed to perform these functions. Its nodes are exchanged data packets using routes.
Imagine the following configuration:
IP address - 192.168.0.0
Mask Network - 255.255.255.0
Gateway - 192.168.0.3
Interface - 192.168.0.3
Metric - 1.
Information is logically decrypted: in the address range from 192.168.0.0 - 192.168.0.255 to exchange information as a gateway and interface, use the network card code (192.168.0.3). All this means that the information goes to the addressee itself directly.
When the end address condition does not correspond to the specified range 192.168.0.0-192. 168.0.255, it will not work directly directly. The server protocol sends data to the router that transmits it to another network. If static routes are not prescribed, the default router address remains the same as the gateway address. Information is sent to this address, then to the network, and on routes prescribed in the table, until the addressee receives the package. In general terms, the data transfer process looks like this. Imagine an illustration of the standard router table entries. In the example there are only a few records, but their number can reach tens and hundreds of strings.
 Stripping from the data of the example, we describe the redirection process to the addresses of the Internet resource in. During contact with the addresses of the Internet resource in the specified range from 74.55.40.0 to 74.55.40.255, the router code is equal to the network number 192.168.0.0, and, accordingly, cannot be applied in the information data exchange process. IP proTocol diagnoses address (74.55.40.226), which is not included in the individual local network address package and appeals to the static routes.
Stripping from the data of the example, we describe the redirection process to the addresses of the Internet resource in. During contact with the addresses of the Internet resource in the specified range from 74.55.40.0 to 74.55.40.255, the router code is equal to the network number 192.168.0.0, and, accordingly, cannot be applied in the information data exchange process. IP proTocol diagnoses address (74.55.40.226), which is not included in the individual local network address package and appeals to the static routes.
Situation When this route is not registered, the information package is sent by the identification of the gateway address set in the default example.
Since the route presented in the example is characterized by a high priority, so it needs a certain gateway, and not a standard suitable for all. Since the gateway satisfying the query in the table is not, the server with a network address 74.55.40.226 will remain outside the access zone. And with the subnet mask code prescribed in the example, all addresses of the range of 74.55.40.0 - 74.55.40.255 will be blocked. It is this range that includes a network path to the anti-virus software site installed on a personal computer that will not receive the necessary updates of viral databases and will not properly function.
The more such data in the route table, the greater the amount of resources is blocked. In the practice of specialists, viral programs created up to four hundred lines of such a species, thereby blocking the work of about thousands of network resources. And the owners of viruses are not particularly interesting that seeking to ban some kind of separate resource, they exclude from possible access of dozens of other sites. This lies the main error of unclean programmers, since the amount of inaccessible resources detects the probability of blocking data itself. For example, if the most popular social networks entered the exclusion circle, and the user can not enter the website of VKontakte or classmates, then there is a suspicion about the proper work of the PC with the network.
It is not difficult to correct the situation, the Route command and the DELETE key are used for this purpose. We find in the table false records and uninstall. A small remark, the entire operation is carried out only if the user has administrator rights, but also changes to the virus route can make only if the network has been introduced into the network account Administrative computer. We give examples of such tasks.
rOUTE DELETE 74.55.40.0 - Recording that removes the first option of the route line;
rOUTE DELETE 74.55.74.0 - Recording that deletes the second option of the route string.
The number of such strings should be the total number of false routes.
If you approach the procedure easier, then you must apply an output redirection operation. This is done by entering the ROUTE PRINT\u003e C: \\ Routes.txt. The activation of the command creates a situation when a file document is created on the system disk called routes.txt, it contains a table with route data.
The list of tables contains DOS codes. These characters are unreadable, and they do not matter to work. By adding Route Delete at the beginning of each route, delete each false record. It looks like this:
rOUTE DELETE 84.50.0.0.
rOUTE DELETE 84.52.233.0.
rOUTE DELETE 84.53.70.0.
rOUTE DELETE 84.53.201.0.
rOUTE DELETE 84.54.46.0.
Next, you need to change the file extension, the options for replacing this extension are CMD or BAT. The new file is started using the double click of the right mouse button. You can simplify the task with the help of a popular file manager, which works as follows. The editor whose call is carried out by the F 4 function key, highlights the right part of the route recording with a special label. Using the CTRL + F key combination, the automatic permutation of all spaces per character with an empty value is performed, and the space in turn is installed in the starting position of the line. The new combination of the specified keys, sets the Route Delete task to the place you need.
When false routes in the data table, it is written very much and adjust them manually seems to be a long and tedious process, it is recommended to apply the ROUTE task together with the key f.
This key removes all non-prompt routes, as well as completely uninstalling routes with the end point and broadcast by the M address. The first and last have a digital code 255.255.255.255; Second 127.0.0.0. In other words, all false information prescribed in the table will be uninstalled. But at the same time, the records of static routes discharged by the user's entire main gateway will be destroyed, so they will need to be restored, since the network will remain inaccessible. Or track the process of cleaning the data table and stop it with intention to delete the record you need.
AVZ anti-virus program can also be used to adjust the router settings. A specific multiprogram of this process is the twentieth TCP setup item.
The last option to block the user access to IP addresses of sites that are used by viral programs is to use the DNS server address substitution. In this embodiment, the connection to the network occurs through a malicious server. But such situations are rather rare.
After the behavior of all works, you need to restart the personal computer.
Thank you again for the help of the preparation of the material of the Masters of the Computer Service Center. Running. RF - http: //trcupisci.rf/information/territoria/ Kolomenskaya/, who can order laptop repair and netbooks in Moscow.
Restoring encrypted files - This is a problem with which a large number of users of personal computers faced the victim of a variety of encryption viruses. The number of malicious programs in this group is very much and it increases with each day. Only Recently, we ran into dozens of encryption versions: Cryptolocker, Crypt0L0CKER, Alpha Crypt, Teslacrypt, CoinVault, Bit Crypt, CTB-Locker, TorrentLocker, Hydracrypt, Better_call_Saul, Crittt, etc.
Of course, you can restore encrypted files by simply by following the instructions that the creators of the virus are left on the contaminated computer. But most often the price of the decryption is very significant, you also need to know that part of encryption virusers so encrypt files that it is simply impossible to decrypt them. And of course, it's just unpleasant to pay for the restoration of your own files.
Ways to restore encrypted files for free
There are several ways to restore encrypted files using absolutely free and proven programs, such as ShadowExplorer and Photorec. Before and during recovery, try to use an infected computer as small as possible, so you increase your chances for successful recovery of files.
The instruction described below needs to perform step by step, if anything does not work, stop, request by writing a comment on this article or creating new topic on our.
1. Remove virus encryption
Kaspersky Virus. Removal Tool. And Malwarebytes Anti-Malware can detect different types Active encrypter viruses and easily delete them from a computer, but they cannot restore encrypted files.
1.1. Remove virus encrypter using Kaspersky Virus Removal Tool

Click on the button Scan To start checking your computer for the encrypter virus.

Wait until the end of this process and remove the foundation found.
1.2. Remove virus encrypter using Malwarebytes Anti-Malware
Download the program. After the download is completed, run the downloaded file.


Automatically start the program update procedure. When it is up to click Run check. MalwareBytes Anti-Malware will start checking your computer.

Immediately after the completion of the computer check, the MalwareBytes Anti-Malware program will open a list of the components of the encrypter virus found.

Click on the button Delete selected To clean your computer. While removing malicious programs, Malwarebytes Anti-Malware may require restart the computer to continue the process. Confirm this by selecting Yes.
After the computer starts again, Malwarebytes Anti-Malware will automatically continue the treatment process.
2. Restore encrypted files using ShadowExplorer
ShadowExplorer is a small utility that allows you to restore shadow copies of files that are created automatically by the Windows operating system (7-10). This will allow you to restore the source status of encrypted files.
Download the program. The program is in the zip archive. So click on the downloaded file right key And select Extract All. Then open the ShadowExplorerportable folder.

Run ShadowExplorer. Select the desired disk and the date of creation of shadow copies, respectively, the figure 1 and 2 in the figure below.

Right-click on the directory or file, which you want to recover. In the menu that appears, select Export.

And last, select the folder to which the recovered file will be copied.
3. Restore encrypted files using PHOTOREC
PhotoRec is a free program created to restore remote and lost files. Using it, you can restore the source files that encrypter viruses are removed after creating their encrypted copies.
Download the program. The program is in the archive. Therefore, click on the downloaded file with the right key and select Extract All. Then open the TestDisk folder.
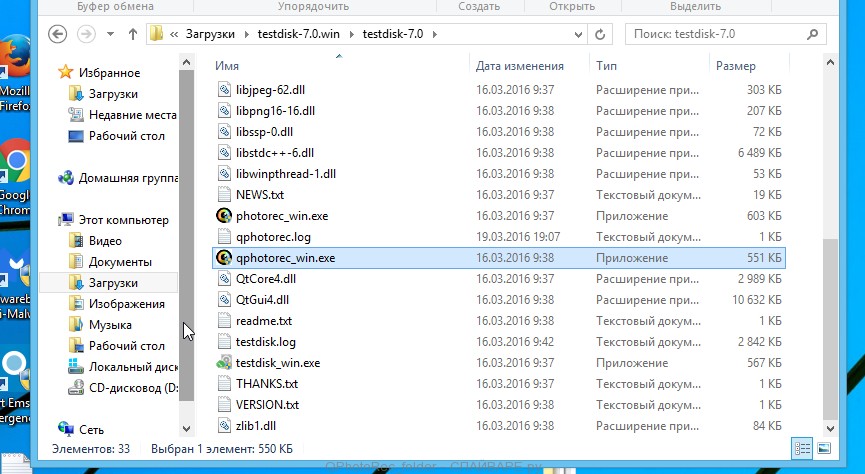
In the list of files, find the qphotorec_win and run it. A program window will open in which all sections of the available disks will be displayed.

In the section list, select the one on which the encrypted files are located. Then click on the File Formats button.

By default, the program is configured to restore all types of files, but to speed up the work it is recommended to leave only the types of files that you need to restore. After completing the selection, click OK.
At the bottom of the QPhotorec program window, locate the Browse button and click it. You need to select a directory in which recovered files will be saved. It is advisable to use a disc on which you are not encrypted files requiring recovery (you can use a USB flash drive or an external disk).
To start the search procedure and restore source copies of encrypted files, click the Search button. This process lasts for quite a long time, so take patience.

When the search is over, click the QUIT button. Now open the folder you selected to save the recovered files.

The folder will contain directories with the names recup_dir.1, recup_dir.2, recup_dir.3 and so on. The more files find the program, the more directory will be. To search for the files you need, check all the directories. To facilitate the search for the file you need, among large number Recovered, use the built-in Windows Search System (by file content), as well as forget about the file sorting function in directories. As a sort parameter, you can select a file change date, since the QPhotorec when recovering the file tries to restore this property.
A Virus Is a Type of Malicious Software That Penetrates System Memory Areas, Code of Oter Programs, and boot sectors. IT IS Capable of Deleting Important Data From A Hard Drive, USB Drive Or Memory Card.
Most Users Do Not Know How to Recover Files After A Virus Attack. In this article, We Want to Tell You How to Do It In A Quick and Easy Way. We Hope That This Information Will Be Useful to You. There Are Two Main Methods You Can Use to Easily Remove The Virus and Recover Deleted Data After A Virus Attack.
DELETE THE VIRUS USING THE COMMAND PROMPT
1) Click The "Start" Button. ENTER CMD IN THE SEARCH BAR. You Will See the "Command Prompt" at the top of the pop-up window. Press Enter.
2) RUN THE COMMAND PROMPT AND TYPE IN: "ATTRIB -H -R -S / S / D DRIVER_NAME \\ *. *"

After This Step, Windows Will Start Recovering The Virus-Infected Hard Drive, Memory Card or USB. IT Will Take Some Time for the Process to Be Completed.
To Start Windows Recovery, Click The "Start" Button. Type Restore in The Search Bar. IN THE NEXT WINDOW CLICK "START SYSTEM RESTORE" → "NEXT" AND SELECT THE DESIRES RESTORE POINT.

Another Variant of the Path IS " Control Panel."→" System "→" System Protection ". A Recovery Preparation Window Will Appear. The Computer Will Reboot and A Message Will Appear Saying "System Restore Completed SuccessFully." If IT Did Not Solve Your Problem, Then Try Rolling Back to Another Restore Point. That's All to Be Said About the Second Method.
Magic Partition Recovery: Restoring Missing Files and Folders After A Virus Attack
For Reliable Recovery of Files Deleted by Viruses, USE Magic Partition Recovery.. The Program IS Based on Direct Low-Level Access to the Disk. Theraefore, IT Will Bypass The Virus Blocking and Read All Your Files.
Download and Install The ProGram, Then Analyze The Disk, Flash Drive or Memory Card. After the Analysis, The Program Displays The List of Folders on the Selected Disk. Having Selected The Necessary Folder on The Left, You Can View IT in the Right Section.

Thus, The Program Provides The Ability to View The Contents of the Disk in The Same Way As with the Standard Windows Explorer. INDITION TO EXISTING FILES, DELETED FILES AND FOLDERS WILL BE DISPLAYED. They Will Be Marked With A Special Red Cross, Making It Much Easier to Recover Deleted Files.
If You Have Lost Your Files After Virus Attack, Magic Partition Recovery Will Help You Restore Everything Without Much Effort.
Simple and convenient AVZ utility, which can not only help, but also knows how to restore the system. Why is it necessary?
The fact is that after the invasions of the viruses (it happens that Avz kills them thousands), some programs refuse to work, all the settings were somewhere smoked and Windows somehow works not entirely correctly.
Most often, in this case, users simply reinstall the system. But as practice shows, it is quite optional, because with the same AVZ utility, you can restore almost any damaged programs and data.
In order to give you a more visual picture, I give a complete list of what is able to restore AVZ.
The material is taken from the directory by AVZ - http://www.z-oleg.com/secur/avz_doc/ (copy and paste into the browser address bar).
Currently, there are the following firmware in the database:
1. Installation of parameters start.exe, .com, .pif files
This firmware restores the system response to EXE, COM, PIF, SCR files.
Indications for use: After removing the virus, programs stop running.
2. Internet Explorer protocol prefix settings for standard
This firmware restores the settings of the protocol prefixes in Internet Explorer
Indications for use: When entering the address of type www.yandex.ru there is his substitution to something www.seque.com/abcd.php?url\u003dwww.yandex.ru
3. Installation of the Start page Internet Explorer
This firmware restores the start page in Internet Explorer
Indications for use: Substitution of the start page
4. Internet Explorer search settings for standard
This firmware restores the search settings in Internet Explorer
Indications for use: When you press the "Search" button in IE, there is an appeal to some extraneous site
5. Installation of desktop settings
This firmware restores the desktop settings.
Recovery implies removal of all active elements of ACTIVEDESCTOP, wallpaper, removing locks on the menu that is responsible for setting up the desktop.
Indications for use: The desktops settings disappeared in the "Properties: Screen" window, an extraneous inscriptions or pictures are displayed on the desktop.
6. The date of all POLICIES (restrictions) of the current user
Windows provides a mechanism for the restrictions of the user actions, called Policies. Many malicious programs use this technology, since the settings are stored in the registry and it is easy to create or modify them.
Indications for use: The function of the conductor or other functions of the system are blocked.
7. The date of the message output during WinLogon
Windows NT and subsequent systems in the NT (2000, XP) line allow you to install the message displayed during the autoload.
This is used by a number of malicious programs, and the destruction of a malicious program does not lead to the destruction of this message.
Indications for use: During the loading of the system, a foreign post is entered.
8. Restoration of the conductor settings
This firmware resets a number of the conductor settings to the standard (reset primarily settings varyable by malicious programs).
Indications for use: Changed the conductor settings
9. Research of debuggers system processes
Registration of the system process debugger will allow a hidden launch application that is used by a number of malicious programs.
Indications for use: AVZ detects unidentified system processes debuggers, problems arise with the start of the system component, in particular after the restarting disappears the desktop.
10. Installation of download settings in SafeMode
Some malicious programs, in particular Bagle worm, damage the system load settings in protected mode.
This firmware restores the download settings in protected mode. Indications for use: The computer is not loaded in secure mode (SAFEMODE). Apply this firmware follows only in case of downloading problems in protected mode .
11.Block Task Manager
Locking Task Manager is applied by malware to protect processes from detection and deletion. Accordingly, the execution of this firmware relieves blocking.
Indications for use: Locking task manager, when you try to call the task manager, the message "Task Manager is locked by the administrator".
12. Clearing HijackThis Utility Ignor
The HijackThis utility stores a number of its settings in the registry, in particular, the list of exceptions. Therefore, for disguise from HijackThis, a malicious program is enough to register your executable files in the exception list.
Currently, a number of malicious programs that use this vulnerability are known. AVZ firmware Clearing HijackThis utility exception list
Indications for use: Suspicions that the HijackThis utility displays not all information about the system.
13. Clearing Hosts File
Clearing Hosts file comes down to searching for the hosts file, removing all meaning rows from it and adding a standard line "127.0.0.1 Localhost".
Indications for use: Suspicions that the HOSTS file is changed by a malicious program. Typical symptoms - blocking the update of antivirus programs.
You can monitor the contents of the HOSTS file using the Hosts Manager of the file built into AVZ.
14. Automatic fixing SPL / LSP settings
Performs an analysis of SPI settings and in case of error detection, it automatically fix the errors found.
This firmware can be launched a re-unlimited number of times. After performing this firmware, it is recommended to restart the computer. Note! This firmware cannot be launched from the terminal session.
Indications for use: After removing the malicious program, Internet access disappeared.
15. Reset SPI / LSP and TCP / IP settings (XP +)
This firmware works only in XP, Windows 2003 and Vista. Its principle of operation is based on the reset and re-creation of SPI / LSP and TCP / IP settings using the NETSH regular utility, which is part of Windows.
Note! Apply the reset of settings only if necessary if there are unreasonable problems with Internet access after removing malicious programs!
Indications for use: After removing the malicious program, Internet access and the firmware execution "14. Automatic fixing SPL / LSP settings »Does not result.
16. Restoring the Explorer start key
Restores the registry key keys responsible for starting the conductor.
Indications for use: During the system loading, the conductor does not start, but manually running Explorer.exe.
17. Unlock registry editor
Unlocks the registry editor by removing a policy that prohibits its launch.
Indications for use: Unable to start the registry editor, when you try, a message is displayed that its launch is blocked by the administrator.
18. Full recreation of SPI settings
SPI / LSP sets up back up, after which it destroys them and creates on the standard that is stored in the database.
Indications for use: Heavy damage to SPI settings, unreasonable scripts 14 and 15. Apply only if necessary!
19. Clean the MountPoints database
Cleaning the MountPoints and MountPoints2 base in the registry. This operation often helps in the case when after infection of the Flash virus in the conductor does not open discs.
To perform recovery, it is necessary to mark one or more items and click the "Run Activated Operations" button. Pressing the "OK" button closes the window.
On a note:
Recovery is useless if a Trojan program runs on the system that performs such reconfigurations - you must first delete a malicious program, and then restore the system settings
On a note:
To eliminate traces of most Hijacker, you must perform three firmware - "Reset Internet Explorer search settings to standard", "Restoring the Internet Explorer start page", "Resetting Internet Explorer Plug Settings to Standard"
On a note:
Any of firmware can be performed several times in a row without prejudice to the system. Exceptions - "5.
Restoring the desktop settings "(the operation of this firmware will reset all the settings of the desktop and have to re-select the design of the desktop and wallpaper) and" 10.
Restoring download settings in SafeMode "(this firmware re-sends the registry keys responsible for loading in safe mode).
To start recovery, first download unpack and run utility. Then press the file - the restoration of the system. By the way, you can still perform 
We celebrate the checkboxes that you need and click to run operations. All, expect to perform :-)
In the following articles, we will consider more problems, solve that the AVZ firmware will help us restore the system. So good luck to you.

 Magnetometry in the simplest version The ferrozond consists of a ferromagnetic core and two coils on it
Magnetometry in the simplest version The ferrozond consists of a ferromagnetic core and two coils on it Effective job search course search
Effective job search course search The main characteristics and parameters of the photodiode
The main characteristics and parameters of the photodiode How to edit PDF (five applications to change PDF files) How to delete individual pages from PDF
How to edit PDF (five applications to change PDF files) How to delete individual pages from PDF Why the fired program window is long unfolded?
Why the fired program window is long unfolded? DXF2TXT - export and translation of the text from AutoCAD to display a dwg traffic point in TXT
DXF2TXT - export and translation of the text from AutoCAD to display a dwg traffic point in TXT What to do if the mouse cursor disappears
What to do if the mouse cursor disappears