Abstract lesson on the topic: "Computer viruses. Antivirus programs "- hypermarket knowledge. Antivirus Programs Antivirus Programs Lesson Abstract
Form of the plan-abstract lesson
____________________________ The beginning of the form ___________________________
Abstract of the lesson of informatics on the topic
"Computer viruses and antivirus programs"
FULL NAME (FULLY)
Kochiyev Isaura Tamazovna
Place of work
MBOU "SOSH №1 p. Cherman "
Position
teacher
Thing
computer science
Class
8th grade
Textbook
N.D. Ugrinovich
Objectives lesson:
summarize knowledge on "Computer viruses and antiviral programs";
form skills to work with antivirus program;
learn to check for viruses using Kaspersky Anti-Virus program;
develop information culture and computer literacy;
brief responsibility, careful attitudes towards computer technology and software.
Type of lesson: combined.
Educational and methodical support: PC, projector, computer science textbook and information technology. Tutorial for grade 8 / N.D. Ugrinovich. - 3rd ed. - M.: Binom. Laboratory of Knowledge, 2015; Distribution material, presentation to the lesson. Interactive board.
During the classes
1. Organizing time.
Check availability to the lesson.
View a positive video before starting work.
2. Front work.
After viewing questions:
What is this video?(about viruses)
How do they behave there?(multiply and copied)
How to deal with them?(fight medication and immune system)
3. Opening conversation.
Name a few common signs of a person and computer. Compare them on functionality?
The computer is an electronic analogue of a person. A person, like any biological organism, is exposed to various pathogenic viruses.
– Or can "get sick", "get infected" with a computer with a virus?
Today we find out: how does this happen, how to avoid this and how to "cure" a computer? How many computer viruses are, how do they behave, hitting the "computer" of the computer? Consequences of infection with a computer virus. What are they?
4. Studying a new material. (Slide 4)
So, really, the computer can get infected. And the cause of infection is really a virus, only computer. This name came from biology precisely on the basis of self-magazine ability.
Computer virus - This is a specially created small program intended for disorders of the computer. When recording the disk system regions or attributing to the files and produces various unwanted actions that often have catastrophic consequences.
The first "epidemic" of a computer virus occurred in1986 year, when the virus named Brain (eng. Brain) infected the floppy disks.
1988 year - Robert Morris in the US wrote a virus that struck 2,000 computers.
Currently, more than 50 thousand viruses infecting computers and distributing on computer networks are known. By the end of 1989, in a number of countries (USA, United Kingdom, Germany), laws providing for developers of computer viruses are under consideration. (In the USA up to 15 years).
Slide number 5. What is common between biological and computer viruses?
1. The ability to reproduce.
2. Harm harm and unwanted actions for a computer.
3. Security, because Viruses have an incubation period.
Slide number 6-7. Ways of penetration of computer viruses

"Let's think about how to get a malicious program on a PC?" (Through infected floppy disks, discs, flash cards, through the Internet or on a local network).
Usually the virus is introduced into any document or program, and at the beginning of work you may not notice anything unusual. However, after a while, the virus will show its destructive forces.
Slide number 8-9. Signs of computer viruses
Let's call the main signs of manifestation of computer viruses.

1. Over the work of the computer;
2. Inability to download
system or application programs, their improper functioning;
3. Changing the size of files, date and time of their creation, the appearance of new files (sometimes with incomprehensible names);
4. Reducing the amount of RAM to the user accessible;
5. Increasing the number of failures in the computer, including its spontaneous reboot;
6. And there are still possible spontaneous changes in the file structure of the disks, etc..
Slide 10. History of computer virology.
I asked to prepare a small message about the most significant points in the development of computer virology.

– The first viruses appeared many years ago, at the dawn of the EMM era, and not
always were malicious. For example, at the end of the 60s, a special program was created in the Xerox laboratory, which is a prototype of modern viruses, which traveled independently on the local computing network and checked the performance of devices included in it.
– However, later program-viruses began to be developed with evil
intent. There is information that some companies specially infected
computers of competitors in order to spy on them or
initiate their information systems.
Computer viruses bring great damage in all sectors.
At one time, many knowingly false reports about the threat of supposedly superpan viruses were distributed. And so, for example:
1) Once in the morning, many people around the world received emails with the heading "I love you", and the letters came from addresses of friends and colleagues. For love confession, a computer virus was hiding, which caused damage to the global economy in 10 billion euros. Virus "I Love You" (that is what it was called) was listed in the Guinness Book of Records as the most destructive computer virus in the world. He struck over 3 million computers on the planet, becoming also the most expensive in history.
2) the most famous lover of viruses in our country is a student
one of the universities of Voronezh. He created the site on the Internet, on which
posted for everyone a whole collection of computer viruses
(more than 4,000 pieces). This site was discovered by the FSB and the student was convicted.
for two years, it is conditional for distributing computer viruses on the Internet.
What is interesting, the student himself also wrote his virus, which is still
not detected by means of protection.
It is necessary to know that none of the viruses can disable components of the computer. The maximum that some viruses are capable of are to destroy the information on the hard disk, which will damage the OS and applications. Although even in this case, the situation can be fatal for you if the virus destroys important documents.
The person who "writes" viruses calls themselves by Vurramaker.
Slide number 11.

(See table "The leading twenty countries - malicious sources
Slide number 12. Classification of viruses

There are several different classifications of malicious programs.
Slide number 13-17. Types of habitat viruses:
Network
Can transmit your software code on computer networks and run it on computers connected to this network.
Infection of a network virus can occur when working with e-mail or with "travels" on the World Wide Web.
File
Implemented into the program and activate when they started.
They can infect other files until the computer is turned off.
Macrowurus
Infect document files, such as text documents.
The threat of infection is terminated only after closing the text document.
Boot
Implemented into the boot sector of the disk (boot sector) or to the sector containing the Master Boot Record (Master Boot Record).
Slide number 18. According to the degree of impact

Another existing classification of viruses - according to their exposure
Slide number 19.

Do not affect the work of the computer (except for reducing free memory on the disk as a result of its distribution).
Slide number 20.

The effect is limited to a decrease in free memory on disk and graphic, sound and other effects.
Slide number 21.

Can lead to serious disasters in the computer.
Slide number 22.

The impact of viruses can lead to loss of programs, data destruction, erasing information in the system areas of the disk.
Slide number 23. Protection Methods

To combat viruses
antivirus is being developed
programs.
Slide number 24. What do antivirus programs do?

Antivirus program (Antivirus) - program,
allowing to identify viruses, treat infected files and discs, detect and prevent suspicious actions.
Slide number 25. Antiviruses of the program
Antiviruses There are now there are more than a dozen antiviruses such as: Norton, Kaspersky, AVG, Dr Web, etc. They are subject to scanning the system find incomprehensible viruses or suspicious programs, and after the user's permission destroys them.

Slide number 26. Speech by the student on the topic: "Antivirus program. Kaspersky Anti-Virus

Short message of the student about Kaspersky.
Evgeny Kaspersky was born in Novorossiysk in 1965, was the only child in the family.
He began training in High School No. 3 named after Gastello in the city of Dolgoprudny near Moscow.
After the victory in the Mathematical Olympiad in 1980, he was enrolled in a physical and mathematical school, and 1982 graduated from the Physics and Mathematics School-boarding school No. 18 named after A. N. Kolmogorov at Moscow State University.
In 1987, Evgeny Kaspersky went to work at the Multidisciplinary Research Institute under the USSR Ministry of Defense. It was here that he began to study computer viruses - after in 1989 faced with the Cascade virus. After analyzing the virus code, Evgeny developed a special utility for his treatment and became interested in this topic.
In 1991, Evgeny Kaspersky began working at the Center for Information Technologies Kami, where he headed a small group of specialists engaged in the development of antivirus solutions.
In November 1992, the Group released its first full-fledged product - AVP 1.0. In 1994, he won the comparative testing conducted by the University of Hamburg test laboratory.
This provided the product international fame, and the developers began to license their technologies to foreign IT companies.
In 1997, Kaspersky and his colleagues decided to create their own company, performing as co-founders of Kaspersky Lab. Eugene did not want the name of the company to appear his surname, but he was convicted by Natalia Kasperskaya - the wife of Evgenia at that time, also included in the number of co-founders of the laboratory.
In November 2000, the AVP product was renamed Kaspersky Anti-Virus.
Kaspersky led antivirus research in the company since its foundation for 2007, when he took the post of Director General of the Kaspersky Lab.
Today Kaspersky is one of the world's leading specialists in the field of virus protection.
Slide number 27. Poll Among students (2008)

Poll among students (2008)
Slide number 28. Speech by the student on the topic: "Antivirus program. Antivirus Avast »
Short message of the student about Avaste.
The history of the creation of the avast antivirus program begins in 1988, when two Czech scholars Edward Kucher and Pavel Baudis took up the development of an antivirus product, but was officially registered on April 21, 1991, as a joint partnership.
Despite the fact that the translation of the word avast from the English language ("Stop, stop") is quite suitable for the name of the antivirus, the originally name was invented as an abbreviation, without taking into account its English-speaking reading.
Avast is deciphered as Anti-Virus Advanced Set, oh there is a "advanced antivirus set". The value "Stop" was noticed later, and an exclamation mark was dwell to the title.
At the moment, the staff of the company consists of hundreds of specialists. From the first lineup, three works in the company still - this is its founders Edward Koucher and Pavel Baudis, as well as Vladimir Blynik - the first employee. Antivirus Avast! More than 150 million users are used throughout the world. If its products are available at the dawn of the company only in Czech language, then the products are localized and translated almost 40 languages. Products received various awards and deserve the recognition of users. Recently, the company noted his twentieth.
Avast. - Anti-virus program, designed to protect computers running on Windows operating systems, Mac OS, Linux, as well as for mobile devices that work on Andrid, Windows CE and Palm.
Slide number 29. Fizkulminutka

Practical work of students
(Check for viruses discs).
Run an antivirus program. Before running an anti-virus program for execution, we must decide which disk we want to check.
Today we will work out the skills of working with the Kaspersky Anti-Virus anti-virus program and check the presence of flexible discs for viruses, local disks.
How can we do it? (Open the folder my computer, select the disk, right-click on the disk and select the "Scan for Viruses" command).
You will have a console of the antivirus program Kaspersky Anti-Virus. On the right side of the console there are three "Start Check" buttons, "Suspend check", "Stop checking". The lower console window displays the presence of infected files.
If the disk or diskette has infected files, then we can delete them. How to do it? (Select the file, click the right mouse button, select the "Delete File" command).
Recall the rules of work on the computer (sit straight, at a distance of 50 cm from the screen of the monitor, the hands should be dry and clean, you can not touch the connecting wires and sockets with your hands and legs, do not touch the monitor screen).
Slide number 30. Testing "Who wants to become a millionaire?"

Questions to I. gre "Who wants to become a millionaire?"
1. Infection of computer viruses can occur in the process.
work with files
disk formatting
off computer
printer printing
2. What you need to have to check the hard disk virus?
protected program
boot program
file with antivirus program
antivirus program installed on a computer
3. What program is not antivirus?
AVP.
Defrag.
Norton.Antivirus.
Dr.Web.
4. The categories of computer viruses do not include
boot viruses
type-viruses
network viruses
file viruses
5. One of the popular antiviruses is:
kaspersky Anti-Virus
Norton.
Dr.Web.
AVP.
6. What year was the Kaspersky program for the first time?
1999
1893
1989
1993
7. What programs are antiviral?
AVP., DrWeb., Norton.Antivirus.
MS.Word., AVP.
MS Word, MS Excel
Norton Commander, MS Excel
8. Who developed an avast antivirus program?
Valery Igor
Alexander Klimov
Evgeny Kaspersky
Eduard Kuchet and Pavel Baudis
9. What does not apply to the main sources of computer infection?
hDD
flashki
the Internet
printer
10. What files infect macro viruses?
executive
graphic and sound
word Document Files and E-Tables Excel
hTML Documents
11. The computer program in which the virus is called:
infected
dangerous
spoiled or changed
formatted
12. Viruses can be classified by:
habitat
habitat
exposure
at the place of creation
13. Computer virus is ...
program for checking and treating disks
any program created in low-level languages
a program copied with a poorly formatted floppy disk
special created small program intended for computer disorders
15. The man who "writes" viruses calls themselves
virremaker
harest
programmer
engineer
Criteria for evaluation:
13-14 points - "5", with the value of the mastering coefficient of the material KU\u003e 0.9
11-12 points - "4", with the value of the mastering coefficient of material 0.9\u003e ku\u003e 0.8
9-10 points - "3", with the value of the mastering coefficient of material 0.8\u003e ku\u003e 0.7
Less than 8 points - "2", when the coefficient of absorption of the material<0.7
Slide number 31-32. Safety regulations when working at a computer.
I want to tell you that the legislation of the Russian Federation provides for punishment for crimes in the field of computer information.

Chapter 28.
"Crimes in the field of computer information"
Criminal Code
Russian Federation
Article 273.
Slide number 33. Security memo for domestic user
computer
I prepared you a security memo for a home computer user. Let's read it together.


Output: avoiding infection with viruses is almost impossible, so regularpreventive actions :
Computer testing for viruses using antivirus programs.
Check diskettes and disks for viruses.
Protecting your diskettes from recording when working on other computers.
Creating archive copies of valuable information for you.
Regular renewal of antivirus programs
5. The results of the lesson.
Reflection
Tell me, please, do you consider the knowledge and skills important and necessary for work?
What of them will you enjoy in your practical activity?
What do you know about legal violations in the information sphere?
What are the laws in the field of information protection?
6. Homework. Read the description of some articles from the laws from the textbook. Think and bring add-ons to them. Answer justify.
Thank you for the lesson.
Theme lesson: "Antivirus".
Objectives:
didactic: Give an overview of antivirus software and tell about protection methods.
developing: Develop students' information thinking.
educational: Show that timely protection of a computer and data and competent work helps to avoid many troubles.
Lesson type (lesson type): Studying a new material.
Organizational forms of education: lecture.
Teaching methods: conversation.
View and forms of knowledge control: Frontal survey.
During the classes
I. Org. moment.
Greeting, checking present. Explanation of the course of the lesson.
II. Check and actualization of knowledge.
Computer viruses are programs that can propagate independently by adding your code for this to files or in the service area of \u200b\u200bthe disk. Thus, on the "sphere of interests", viruses are divided into software (which are capable of infecting
find files - COM and EXE-types and overlay), bootable (hiding its code in the boot-sector of a floppy disk or hard disk), recently text viruses (affecting documents in WINWORD format, replacing systemic macros), Trojan (creating programs with "interesting "Names, the launch of which leads to the infection of the computer - the calculation on the user's psychology, which for the sample will load it from where the appeared file type Game.exe) and combined (combining various means of infection - for example, and through the boot sector, and through programs). The main tactic of protection against viral infection is to use software from reliable sources (ideally - only licensed), in regular control over the state of the most important information in the computer (if possible, with the creation of backups on diskettes, ribbon or network disk) . A mandatory check of all newly reliable antivirus or their set on the disks is also needed. A set of high-quality antivirus programs is invariably replenished as the edge of the viral attack expands.
Popular antivirus packages are a set of JSC Dialognauka, Norton Antivirus and AntiViral Toolkit Pro. Panda Antivirus Titanium.
Dr. Web.
In the standard supply of the anti-virus kit, Dialognauka JSC includes four software products: weekly updated polyphag AidStest, ADINF drive auditor, the attending ADINF CURE MODULE unit and a DOCTOR WEB program, tracking and destroying complex and polymorphic viruses.
Auditor AdInf. Allows you to detect the appearance of any virus, including Stealth viruses, mutant viruses and viruses unknown to date. With the Adinf Cure Module program installed (the attending ADINF auditor unit), you can immediately remove up to 97% of them. Adinf takes control of all parts of the hard drive, where the virus penetration is possible. This method of checks completely eliminates the masking of stealth viruses and provides a very high speed of checking the disk.
DOCTOR WEB. Fights with a well-known program by polymorphic viruses. In addition, the Doctor Web can conduct heuristic analysis of files in order to identify unknown viruses, including complex and polymorphic viruses. The success of such an analysis is an average of 82%. The program can unpack and check the executable files processed by archivers LZEXE, PKLITE and DIET.
AVP.
Anti-virus set, which is an extended version of the famous antivirus kit "Dr. Kaspersky". The complex contains a FAG program, testing and restoring files and loading sectors of discs damaged by viruses. During the program, the program is tested for unknown viruses. The kit includes a resident program, tracking suspicious actions performed on the computer, and gives the ability to view a memory card. A special set of utilities helps to detect new viruses and understand them.
Norton Antivirus
Norton Antivirus anti-virus package belongs to the "installed and forgotten". All the necessary configuration parameters and scheduled activities (checking the disk, checking new and modified programs, launching the AUTO-PROTECT Windows utility, check the disk boot sector A: Before rebooting) are set by default. The disk scanning program exists for DOS and Windows. Among other Norton Antivirus detects and destroys even polymorphic viruses, and successfully reacts to virus-like activity and struggles with unknown viruses.
III. Fastening the material.
15 useful tips on how to protect against viruses from Panda Antivirus Titanium.
1. Use the best antivirus programs and update them regularly.
2. Make sure your antivirus program includes the following services: technical support, alert system of viruses, rapid response service.
3. Make sure your antivirus is constantly turned on.
4. Before opening messages received by email, check them for viruses.
5. Do not download anything from dubious sites.
6. Do not download the files offered to you in chat rooms or newsgroups.
7. Check each diskette used for viruses.
8. When the computer is turned off or when you reboot, remove the diskette from the drive.
9. Check the contents of archives.
10. Watch out for suspicious activity on your PC.
11. Use the built-in security features of frequently used programs to combat viruses.
12. Create backups regularly.
13. Follow the news.
14. Use only licensed software.
15. Require the developers of software, Internet providers and publishers of their accuracy in combating viruses.
The most reliable way to protect your PC from viruses is a good antivirus program.
Antivirus program - This is a computer program specifically designed to search and neutralizing viruses. Because She can detect a virus, she knows and appropriate means of dealing with it. Despite this, more than 20 new viruses come out every day, which antivirus programs are not able to detect. Therefore, regular updates of antivirus bases are the basis for successful search and destruction of these malicious codes.
I. II.. D / z
Know what archivers and their assignment are, to be able to pack and unpack files in archives. Additional task: learn how to create self-extracting archives.
I.V. Questions of students.
Answers to students' questions.
V. The result of the lesson.
Summing up lesson. Estimation.
At the lesson, we met the varieties of antivirus programs and their appointment.
The widespread dissemination of computer viruses has led to the development of antivirus programs that allow you to detect and destroy viruses, "treated" affected resources.
The basis of the work of most antivirus programs is the principle of searching for virus signature. Viral signaturethey call some unique characteristic of a viral program that issues the presence of a virus in a computer system. Most often, the anti-virus program includes a periodically updated virus signature database. The antivirus program studies and analyzes the computer system, and also compares, looking for compliance with signatures in the database. If the program finds a match, it tries to clean the discovered virus.
By the method of work, antivirus programs can be divided into filters, auditors, doctors, detectors, vaccines, etc.
Filter programs -this is a "guard", which are constantly in OP. They are resident and intercept all requests to the OS to perform suspicious actions, i.e. operations that use viruses for their reproduction and damage to information and software resources in the computer, including to reformat the hard disk. Among them, you can select attempts to change file attributes, correction of executable som or ex-files, records to the boot sectors of the disk.
Each time a request for such an action on the computer screen comes a message about which action is requested, and which program will perform it. In this case, the user must either allow or prohibit its execution. Permanent finding program "Watchmen" in OP significantly reduces its volume, which is the main disadvantage of these programs. In addition, the filters programs are not able to "treat" files or discs. This feature is performed by other antivirus programs, such as AVP, Norton AntiVirus for Windows, Thunder Byte Professional, McAfee Virus Scan.
Program-auditorsare a reliable means of protection against viruses. They remember the original state of the programs, catalogs and system regions of the disk, provided that the computer has not yet been infected with the virus. Subsequently, the program periodically compares the current state with the source. When inconsistencies are detected (through the length of the file, the modification date, the cyclic file control code) message appears on the computer screen. Among the audit programs, you can select the ADINF program and addition to it as ADINF CURE MODULE.
Doctor programit is capable not only to detect, but also to "treat" infected programs or discs. At the same time, it destroys infected virus body programs. Programs of this type can be divided into phages and polyphag. Phages -these are programs with which viruses of a certain species are found. Polyphagi.designed to detect and destroy a large number of varied viruses. In our country, polyphags such as MS AntiVirus, AidStest, Doctor Web are most common. They are continuously updated to combat emerging new viruses.
Detectors programscapable to detect files infected with one or more well-known program developers viruses.
Vaccine programsor immunizers,refer to the class of resident programs. They modify programs and discs so that this is not reflected in their work. However, the virus from which vaccination is produced, considers them already infected and is not introduced into them. At the moment, many antivirus programs have been developed that have received widespread recognition and constantly replenishing new means to combat viruses.
DOCTOR WEB POLIFAG program is used to combat polymorphic viruses that appeared relatively recently. In heuristic analysis mode, this program effectively defines files infected with new, unknown viruses. Using DOCTOR WEB.to control diskettes and received over the network files, you can almost certainly avoid infection of the system.
When using Windows NT, problems arise with virus protection created specifically for this environment. A new kind of infection has also appeared - macroviruses that are "implanted" into documents prepared by the Word text processor and Excel spreadsheets. The most common anti-virus programs include AntiViral Toolkit Pro (AVP32), Norton AntiVirus for Windows, Thunder Byte Professional, McAfee Virus Scan. These programs operate in scanner software mode and conduct anti-virus control of OP, folders and disks. In addition, they contain algorithms for recognizing new types of viruses and allow you to test files and discs in the check process.
AntiViral Toolkit Pro (AVP32) is a 32-bit application running in Windows NT. It has a convenient user interface, a help system, a flexible system of settings selected by the user, recognizes more than 7 thousand different viruses. This program determines (detects) and removes polymorphic viruses, mutant viruses and invisible viruses, as well as macroviruses that infect Word document and Excel tables, Access objects - Trojan horses.
An important feature of this program is the ability to control all file operations in the background and virus detection until the system is realized, as well as the detection of viruses within the archives of the ZIP format, ARJ, ZHA, RAR.
Allmicro AntiVirus interface is simple. It does not require an additional knowledge of the product. When working with this program, press the Start button (SCAN), after which the check or scanning of the OP, boot and system sectors of the hard disk will begin, and then all files, including archival and packaged.
The VSCAN 95 program When you start loading, checks the computer memory, the boot sectors of the system disk and all files in the root directory. Two other package programs (McAfee VSHIELD, VSCAN) are Windows applications. The first after Windows boot is used to track the newly connected disks, control of executable programs and copied files, and the second is to further check the memory, disks and files. McAfee VirusScan package is able to find macarrow in MS Word files.
During the development of local computer networks, e-mail and Internet and implementing the Windows NT network OS, anti-virus software developers are prepared and shipped programs such as Mail Checker, which allows you to check the incoming and outgoing email, and AntiViral Toolkit Pro for Novell NetWare (AVPN ) used to detect, treat, delete and move to a special directory of the files affected by the virus. The AVPN program is used as an antivirus scanner and a filter that constantly monitors the files stored on the server. It is able to delete, move and "treated" affected objects; check packaged and archive files; determine unknown viruses using the heuristic mechanism; Check in the scanner mode remote servers; Disable an infected station from the network. The AVPN program is easily configured to scan files of various types and has a convenient process of replenishing the anti-virus base.
| |
Abstract for the lesson of informatics "Computer viruses. Antivirus programs"
1. Actualization of knowledge
At the past lessons, we reviewed the main types of software. Let's remember what software is? (Software - the whole set of programs used on the computer).
- Why does the computer need a computer? (Software allows the computer to perform a specific job).
- What groups share all by? (System software, applied software, programming system).
- What applies to system programs? (Programs required for computer operation).
- Give examples of system programs (operating systems, drivers, utilities).
- What is applied software? (Programs designed to perform specific user tasks).
- Examples of applied software? (Text, Graphics Processors, Games)
- What is programming systems? (These are programs for creating new programs in programming languages).
- What group of programs include antivirus programs? (System software). Why? (They are necessary for the correct operation of the entire computer system).
The subject of the lesson: "Computer viruses and antivirus programs". The purpose of our work is to get acquainted with the basics of computer virology, learn to detect viruses and fight them.
We told me that the computer could be compared to something with a person. A person, as a biological organism, is subject to various exposure to the external environment, including various diseases, the causes of which, often, are viruses and bacteria that penetrate the human body from outside.
Try to describe the stages and the consequences of human infection by any virus. Features:
- the penetration of the virus into the human body comes from outside;
- virus ability to self-insulating;
- activation of some viruses is not immediately after penetration into the body, and after a while.
Can a computer get infected with a virus? What should be this virus on your presentation?
2. Studying a new material
Computer virus
- slow computer work;
- the inability to load the OS;
- changing file sizes;
5) rumors and delusion
7) Virus Classification
viruses on their habitat
- File viruses
- macrowirus
- Network viruses
- Habitat boot viruses
Another existing one.
- Harmless viruses
- Non-hazardous viruses
- Dangerous viruses
- Very dangerous viruses
- Resident viruses
- Non-resident viruses
Distinguish:
- The simplest viruses
- Satellite Viruses (Companions)
- Stealth Virus (invisible)
- Polymorphic viruses (mutants)
- Macrowuri
- Trojan program
- Worms
9) antivirus programs
- Polyphagi.
- Auditors
- Blockers
3. Additional Information
In the early 1970s, in the prototype of the modern Internet, the APRAnet military computer network - the Creeper virus was discovered. This program was able to independently enter the network via the modem and transfer its copy to the remote system. On infected systems, the virus found himself with the message: "I" Mo Creeper: Catch Me If You Can. "It was an annoying, but overall a harmless virus.
1981 appeared Elk Cloner virus. He was recorded in the loading sectors of the diskette, to which the appeal went. In those days it seemed incredible and caused in ordinary users a steady connection between viruses and extraterrestrial civilizations trying to conquer the world. The impression of the virus was intensified by its manifestations: ELK Cloner turned the image on the screen, forced the text to flash, displayed a variety of messages.
In 1983, Len Eididerman uses the term "virus" for the first time in the application to self-magazing computer programs. In the same year, Fred Cohen, the investigator of modern computer virology, at a computer security seminar demonstrates a virus-like program that can be introduced into other objects, and a year later gives a scientific definition of the term "computer virus".
In 1986, the first global virus epidemic was registered. BRAIN virus, infecting boot sectors diskette, has spread almost all over the world for several months. Following the discovery of Brain, scientific fiction novels dedicated to viruses began to appear.
In December 1987 there was a first well-known Clastic Network Virus Epidemic "Christmas Tree". For four days (December 9-13), the virus paralyzed the IBM VNet network - it was clogged with its copies. When you start the virus, the image of the Christmas tree image and sent its copies to all network users whose addresses were present in system files.
1988 - Global epidemic. The Jerusalem virus found himself: on Friday, the 13th, he destroyed all files running on an infected computer. November 1988: Pedal epidemic of the present network virus, called the Morris worm. The virus infected more than 6,000 computer systems in the United States (including the NASA Research Center). At this time, the first anti-virus software developers began to appear.
December 1989: A certain attacker sent 20,000 disks containing "Trojan" at different addresses. After 90 operating system downloads on an infected PC, the program made invisible all files and left on the disk only one readable file - an account that should have been paid and sent at the specified address. In 1989, Evgeny Kaspersky began her career of the anti-virus expert, later founding the company "Kaspersky Laboratory".
In the 90s, the number of viruses grows in geometric progression. In July 1990, there was a serious incident with the English PC Today computer magazine. A floppy disk was made to each magazine number for free, as it was subsequently infected by the Diskkiller virus. More than 50,000 copies of the magazine were sold. Sleeve comments.
July 1992: The appearance of the first designers of viruses. They allowed people to create their own viruses of various types and modifications.
At the end of the XX - early XXI century, email and the Internet strengthened their positions as the most dangerous sources of malicious programs.
In January, the global epidemic of the Internet worm of Happy99 broke out. Next - Global Virus Epidemic "Melissa". Immediately after the system infection, he reads the address book of the postal program and immediately sent his copies from the first 50.
On Thursday, on May 4, 2000, a new dangerous virus was discovered, pretending to be recognized in love! - "Worm" Loveletter, which extends e-mail under the "ILOVEYOU" heading. Iloveyou inflicts significant damage to the data contained on the disk of an infected computer. "Of course, this is so interesting. Having received a message in which it is said that you are loved, you will certainly hurry to open it and see what inside. "
2001 - a new Zoher virus - an automated letter of happiness "zoher" extends e-mail in the form of nested files. Thus, when attempting to read the letter, the virus is activated independently if a special patch has been installed on the computer for a postal program.
The body of the letter contains a very long text in Italian.
Its translation is approximately following:
"With this letter you will come happiness! Not just happiness, but happiness with a capital letter with! Even more - happiness with large letters with and b! We do not spend time on trifles! From today, luck will come to you, but only if you send this letter to everyone who you know. If you do it, then:
a) Your male force will be like King Kong to the end of your life
b) the traffic light in front of you will always be green, or, at least, yellow
c) you will catch all the pokemones
d) (for men) when you go fishing, then no simple fish, and siren, by mistake born not with a tail, but with beautiful female legs
e) (for women) you will be born siren with female legs, and you will catch your dream man
If you do not send this letter to all your familiar for 40 seconds, you are waiting for trouble! You will get into a lot of tragicomic situations, your life will become one big joke, which only you will not seem funny ..., etc. "
1) The concept of "Computer Virus"
So, really, the computer can get infected. And the cause of infection is really a virus, only computer. This name came from biology precisely on the basis of self-magazine ability. Viruses are small malicious programs that run on the computer without the knowledge of its host and perform various unwanted actions. In this case, viruses can be both almost harmless and very unpleasant.
Computer virus - This is a program that can create your copies and implement them into files, boot sectors of the disks, network. At the same time, the copies retain the possibility of further distribution. Often viruses have a destructive effect.
2) ways of distribution of computer viruses
Let's think about how to spread viruses. (Viruses can get to PC as well as any other program). In contrast to ordinary bacillos, computer viruses are not transmitted by air: since only various computer equipment serves as viruses - only various computer equipment serves their habitat medium.
How can a malicious program get on a PC? (Through infected floppy disks, discs, flash cards, through the Internet or on a local network). Usually the virus is introduced into any document or program, and at the beginning of work you may not notice anything unusual. However, after a while, the virus will show its destructive power.
3) signs of the appearance of computer viruses
Let's call the main signs of manifestation of computer viruses.
- incorrect work of normally working programs;
- slow computer work;
- the inability to load the OS;
- disappearance of files and directories;
- changing file sizes;
- an unexpected increase in the number of files on the disk;
- reducing the size of free RAM;
- output to the screen of unexpected messages and images;
- feeding unforeseen sound signals;
- frequent freezes and malfunctions in the computer.
4) History of Computer Virology
The first viruses appeared long ago, at the dawn of the EMM era, and were not always malicious. For example, at the end of the 60s, a special program was created in the Xerox laboratory, which is a prototype of modern viruses, which traveled independently on the local computing network and checked the performance of devices included in it.
However, later the viruses program began to be developed with malicious intent. There is information that some companies specially infected the computers of competitors in order to thus spy on them or disable their information systems.
5) rumors and delusion
Sometimes the fear of viruses causes more trouble than the viruses themselves. At one time, many knowingly false reports about the threat of supposedly superpan viruses were distributed.
It is necessary to know that none of the viruses can disable components of the computer. The maximum that some viruses are capable of are to destroy the information on the hard disk, which will damage the OS and applications. Although even in this case, the situation can be fatal for you if the virus destroys important documents.
6) Creators of Computer Viruses
The person who "writes" viruses calls themselves by Vurramaker. Who is engaged in creating malicious programs? Nowadays, enthusiasts are usually engaged in the creation of viruses. They can be professional programmers, and researchers and ordinary students beginners to study programming. And currently there are dozens of programs for automatic generation of viruses - designers.
What is an incentive for such activities - to say difficult. It can be both a sense of revenge and the desire to assert. The first viral designer who got widespread was VCL (Virus Creation Laboratory), created in 1992.
7) Virus Classification
There are several different classifications of malicious programs.
The most common of them dividesviruses on their habitat. According to it, computer viruses are file, network, boot and macro.
- File viruses - These are programs that affect the executable files of the operating system and user applications. Most often, they are introduced into files with COM, EXE, BAT, SYS, DLL extensions. Such viruses will detect and neutralize the easiest. It also glances that they can show their malicious activity only after launching an infected program.
- Often, a separate subtype called the file viruses, which is calledmacrowirus . They also live in files, but not programs, but user documents and templates (DOC, DOT, XLS, MDB, etc.). To create them use the language of the macros. Therefore, in order to protect yourself from macrors, you need to turn off the autorun macros when opening documents.
- Network viruses As a habitat, global or local computer networks use. They do not save their code on the hard drive of the computer, and penetrate directly into the PC RAM. Viruses of this type for the ability to calculate the network addresses of other machines, while in the computer's memory, and independently send their copies on these addresses are called network worms. Such a virus can be simultaneously in the memory of several computers. Network viruses detect more difficult than file. Network viruses are distributed at high speed and can highly slow down the computer network hardware.
- Habitat boot viruses - Special areas of rigid and flexible disks that serve to load the operating system. To infect viruses use the main boot record of the hard drive. The boot virus replaces the original entry and intercepts the management of the system. Such viruses detect and remove the most difficult because they start their work before loading antivirus applications. They also represent the greatest danger.
Another existing oneclassification of viruses - by their destructive capabilities.
- Harmless viruses - Have a slight impact on the work of the PC, occupying some of the system resources. Often, users do not even suspect their presence.
- Non-hazardous viruses - Also occupy a part of the computer resources, but the user knows about their presence. Usually they are manifested in the form of visual and sound effects and do not harm the user data.
- Dangerous viruses - Programs that violate the normal operation of user applications or the entire system.
- Very dangerous viruses - Programs whose task is to destroy files, output from standing programs and OS or declassify confidential data.
All computer viruses are two types - resident and non-resident.
- Resident viruses There are programs present in RAM or maintaining their active part there, which constantly infects certain objects of the operating system.
- Non-resident viruses Loading only during the opening of an infected file or work with an infected application.
It is easy to guess, resident viruses represent the greatest danger, since the time of their active work is limited only to a shutdown or reboot of the entire system, and not a separate application.
According to the features of the work algorithm distinguish:
- The simplest viruses - Viruses that, when distributing their copies, necessarily change the contents of the disk sectors or files, so it is easy enough to detect.
- Satellite Viruses (Companions) - A virus that is not implemented in the executable file itself, and creates its infected copy with another extension.
- Stealth Virus (invisible) - Viruses that hide their presence in infected facilities, substituting instead of unreleased areas.
- Polymorphic viruses (mutants) - Viruses modifying their code in such a way that copies of the same virus did not coincide.
- Macrowuri - Viruses that infect documents of office applications.
- Trojan program - A program that is masked for useful applications (utilities or even antivirus programs), but it produces various spy steps. It is not embedded in other files and does not have the ability to self-insulating.
- Worms - These are pesting computer programs that are capable of self-insulating, but, unlike viruses, other files are infected. Wormy received its name because they use computer networks and email to distribute.
Today, the so-called network worms are most common, as well as macroviruses.
8) Prevention of computer viruses
One of the main methods of combating viruses is, as in medicine, timely prevention. Think what means help prevent PC infection?
- Backup the most valuable data;
- creating a distribution and system disk;
- storage of all registration and password data is not on PC;
- checking all the information incoming from the information on viruses, both on diskettes, CD-ROM and over the network;
- the use of "fresh" antivirus programs, a regular test of a computer for viruses.
9) antivirus programs
So, a special place in this list is occupied by software protection software - antivirus programs. What kind of type do they relate? (System software).
Antivirus Program (Antivirus)- A program that allows you to identify viruses, treat infected files and discs, detect and prevent suspicious actions.
There are several types of antivirus programs that differ in the functions performed.
- Polyphagi. . View the contents of the files located on the disk of the computer, as well as the contents of the computer's RAM in order to search for viruses.
- Auditors . In pre-scanning mode, creates a database with checksums and other information that allows you to control the integrity of the files (control over the changes that occur in the PC file system).
- Blockers . Check for viruses of launched files, interception of "virus-hazardous" situations.
No type of antivirus software separately gives full protection against viruses. Therefore, modern anti-virus programs typically include components that implement all these functions.
1. The concept of "computer virus" and its properties
Computer virus is a malicious self-propagating software code in the information environment. It can be embedded in executable and command files of programs, distributed through the boot sectors of floppy disks and hard drives, documents of office applications, via email, Web sites, according to other electronic channels. Penetrating into the computer system, the virus may limit into harmless visual or sound effects, but may also cause loss or distorting data, leakage of personal and confidential information. In the worst case, the computer system affected by the virus will be under the complete control of the attacker.
(Virus - with lat.) - Type of programs characterized by the ability of self-magazin hidden from the user to defeat other programs, computers or networks.
Students and schoolchildren who have just studied the assembler language, want to try their strength, are created by the majority of viruses. A significant part of these viruses is often not covered by their authors.
The second group also also make up young people (more often - students), which have not yet fully mastered the art of programming, but have already decided to devote themselves to writing and spreading viruses. As a rule, they create numerous modifications of "classic" viruses, or viruses are extremely primitive and with a large number of errors. The exit of virus designers, with which you can create new viruses, even with minimal knowledge about the operating system and the assembler greatly facilitated their work.
Becoming older and more experienced, many of these virus writers fall into the third, most dangerous group, which creates and launches "professional" viruses into the world. These are carefully thought out and debugged programs. Such viruses often use fairly original algorithms, undocumented and few people who are known ways of penetration into system data areas.
The fourth group of viruses authors is "researchers." This group consists of talented programmers who are engaged in the invention of fundamentally new methods of infection, hide, counteract antivirus, etc. They also come up with ways to introduce into new operating systems, virus constructors and polymorphic generators. These programmers write viruses not for the sake of viruses itself, but rather for the "study" of the potentials of "computer virology".
When infecting a computer, the virus is important to detect it, for this you should know the main signs of its manifestation:
Termination of work or incorrect work of previously successfully functioning programs;
Slow computer work;
The inability to load the operating system;
Disappearance of files and directories or distorting their contents;
Changing the date and time of file modification;
Changing file size;
An unexpected significant increase in the number of files on the disk;
A significant reduction in the size of free RAM;
Output to the screen of unforeseen messages or images;
Feeding unforeseen sound signals;
Frequent freezes and malfunctions in the computer.
It should be noted that the above phenomena are not necessarily caused by the presence of a virus, and may be a consequence of other reasons. Therefore, the correct diagnosis of the computer status is always difficult. It is possible to infected with a computer virus only in a very limited number of cases. It:
Connecting to the system of the infected driver;
Opening a document infected by Macrowarus;
Installation on a computer infected operating system.
The computer cannot be infected if:
Text and graphic files were rewriting on it (with the exception of files involving the execution of the macrocomand);
It was copied from a single floppy disk to another, provided that no file with a floppy disk was launched;
The computer does the processing of text and graphic files, data files and information files (with the exception of files involving the execution of the macrocomand);
Rewriting to the computer infected with the virus of the file does not mean infection with its virus. To infect the infection, you need to either run the infected program, or connect the infected driver, or open the infected document (or, of course, to boot with the infected floppy disk). In other words, it is possible to infect your computer only if you run unverified programs and (or) software products, install untested drivers and (or) operating systems, boot from the unverified system floppy disk or open unverified documents subject to macrovirus.
2. Classification of computer viruses
Tens of thousands of different viruses are known today. Despite such abundance, the number of types of viruses, differing from each other with the dissemination mechanism and the principle of action, is very limited. There are combined viruses that can be attributed simultaneously to several types. Thus, viruses can be classified according to the following features:
Habitat;
A method of infection with habitat;
Degree of impact;
Features of the algorithm.
1. Depending onhabitat environment Viruses are divided into:
1) Network - apply to various computer networks;
2) File - affect files with extension.com,.. Lee, less frequently .Sys or overlay modules. Files. These viruses add their body to the beginning, middle or end of the file and change it in such a way as first to get control. Having received control, the virus can infect other programs, embed into the computer's operational memory, etc. Some of these viruses do not care about the preservation of the infected file, as a result of which it turns out to be inoperable and not subject to recovery;
3) Boot - receive control at the computer initialization stage, even before the OS boot starts. When infected with a floppy disk or hard disk, the boot virus replaces the BR boot record or the MBR main boot record. When the BIOS computer is booting, reads the boot record from the disk or floppy disk, as a result of which the virus is managed before loading the OS. Then it copies itself to the end of RAM and intercepts several BIOS functions. At the end of the procedure for infection, the virus loads the present boot sector into the computer's memory and transmits it to control. Further, everything happens, as usual, but the virus is already in memory and can control the operation of all programs and drivers;
4) File-loading - combined viruses that combine the properties of file and boot. As an example, the ONEHALF file-boot virus is widely widespread. Penetrating into the computer with MS-DOS OS, this virus infects the main boot record. During loading, the virus gradually encrypts the hard disk sectors starting from the most recent sectors. Onehalf virus uses various disguise mechanisms.
2. P. habitatviruses are divided into:
1) Resident - when infected (infection), the computer leaves its residence in the RAM, which then intercepts the access of the operating system to the infection objects (files, boot sectors, etc.) and is introduced into them. Resident viruses are in memory and are active up to shutdown or restarting the computer;
2) Non-resident viruses do not infect computer memory and are active limited time.
3. in degree of impactviruses can be divided into:
1) non-hazardous, non-interfering operation of the computer, but reduce the amount of free RAM and memory on disks, the actions of such viruses are manifested in any graphic or sound effects;
2) hazardous viruses that can lead to various violations in the computer;
3) Particularly dangerous, the impact of which can lead to loss of programs, the destruction of data, erasing information in the system areas of the disk.
4. P. features algorithm:
A wide variety of viruses causes difficulties in their classification on this basis.
2) Invisible viruses (stealth viruses) - try to hide their presence in the computer. They have a resident module that is constantly in the computer's RAM. This module intercepts access to the computer's disk subsystem. If OS or another program read the file of the infected program, the virus substitutes a real, unprofitable, program file. To do this, the resident module can temporarily delete the virus from an infected file. After the end of working with the file, it is infected again. Booting stealth viruses act according to the same scheme. When any program reads data from the boot sector, the real boot sector is substituted instead of infected.
3) Macrocomand viruses. Microsoft Office documents may contain small programs for processing these documents drawn up in Visual Basic for Applications. This also applies to Access databases, as well as POWER POINT presentation files. Such programs are created using MacroComand, so viruses living in office documents are called macrosand. Macro command viruses are distributed with document files. To infect the computer with such a virus, just open the document file in the appropriate application. The prevalence of this type of viruses to a large extent contributes to the popularity of Microsoft Office. They can change infected documents, remaining unnoticed for a long time.
In addition to viruses, it is customary to allocate at least three types of malicious programs. These are Trojan programs, logic bombs and wormship programs. There is no clear separation between them: Trojan programs may contain viruses, logic bombs and others can be built into viruses.
4) Trojan programs - in basic purposes of Trojan programs are completely harmless or even useful. But when the user enters the program to his computer and starts it, it can imperceptibly perform malicious functions. Most often, Trojan programs are used for the initial distribution of viruses, to obtain remote access to the computer via the Internet, theft of data or their destruction;
5) Logic bombs - a program or its individual modules, which under certain conditions perform malicious actions. A logic bomb may, for example, work upon reaching a specific date or when recording will appear in the database or disappear, etc. Such a bomb can be built into viruses, Trojans and even in conventional programs;
6) Wormware programs are aimed at performing a specific function, for example, to penetrate the system and modifying data. You can, let's say, create a worm program that spies in the password to access the banking system and the changing database. The well-known worm program was written by a student of the Cornell University Robert Morris. The worm of Morris was launched on the Internet on November 2, 1988 and in 5 hours was able to penetrate more than 6,000 computers. Some worm viruses (for example, Code Red) exist not within the files, but in the form of processes in the memory of an infected computer. This eliminates their detection of antiviruses scanning files and dismounting the operational memory of the computer;
7) Viruses in document management systems - Documents stored in databases of document management systems such as Lotus Notes and Microsoft Exchange, also may also contain viruses, more precisely, malicious macros. They can be activated when performing any actions on the document (for example, when the user clicks the mouse button). Since such viruses are not located in files, but in database records, specialized antivirus programs are required to protect against them;
8) new and exotic viruses. As computer technologies are developing, computer viruses are improved, adapting to new habitats for themselves. So, the new W32 / Perrun virus, the message about which is available on the website of Network Associates, is able to distribute ... through the image files of JPEG format. Immediately after starting W32 / Perrun, it looks for files with extension.jpg and adds your code to them. It must be said that this virus is not dangerous and requires a separate program for its distribution. Among other "achievements" of the creators of malicious programs, the Palm.PHage virus deserves attention. He infects the application of "Palmpilot" computers, overwrite these applications files with their code. The appearance of viruses such as W32 / Perrun and Palm.phage indicates that a computer virus, a Trojan program or a worm of a new, unknown earlier type, or a known type, but aimed at a new computer equipment can be born at any time. New viruses can use unknown or previously existing distribution channels, as well as new technologies for introducing into computer systems.
3. Antivirus programs
Antivirus is a program designed to scan and recognize on a computer program or scripts (script - a text file containing sections, sections parameters, and sections parameter values \u200b\u200bthat describe the actions that you need to perform an interpreter of the script), macros (macro is a set of commands, which can be applied by clicking just one key). Using the macro, you can automate any action that is performed in the application used, which can cause damage to the user or significantly slow down the computer.
Antivirus programs can be divided into several types:
Detectors . Their appointment is only to detect the virus. Virus detectors can compare the boot sectors of the diskette with known boot sectors generated by operating systems of various versions, and thus detect bootable viruses or scan files on magnetic disks in order to detect signatures of known viruses. Such programs in pure form are currently rare.
The doctors (Phages. Fag) is a program that is capable not only to detect, but also destroy the virus, i.e. Delete its code from infected programs and restore their performance (if possible). The Fagom's famous in Russia is AidStest, created by D.Nozinsky. One of the latest versions detects more than 8,000 viruses. AidStest for its normal functioning requires that there are no residency antiviruses that block the record in program files, so they should be unloaded, or by specifying the unloading option of the resident program itself, or use the corresponding utility.
Auditors . The revizor program controls the possible ways to disseminate viruses and infection of computers. The audit programs belong to the most reliable means of protection against viruses and should be included in the arsenal of each user. The auditors are the only means that make it possible to monitor the integrity and changes in files and system regions of magnetic disks. The most famous ADINF auditor program developed by D. Mostovyov is most famous.
Vaccines . So called antivirus programs, leading themselves like viruses, but not harm. Vaccines protect files from changes and are capable not only to detect the fact of infection, but in some cases "cure" files affected by viruses. Currently, antiviral vaccine programs are not widely used, since in past years some incorrectly working vaccines caused damage to many users.
To find DR Web viruses uses the processor emulation program, i.e. It simulates the execution of other files using the I-8086 microprocessor software model and thereby creates a medium for the manifestation of viruses and their reproduction. Thus, the Dr Web program can fight not only with polymorphic viruses, but also viruses that can only appear in perspective.
The main functional features of DR Web are:
· Protection from worms, viruses, trojans, polymorphic viruses, macro-versions, spyware, dosers, adware, hacker utilities and malicious scripts;
· Updating anti-virus databases up to several times per hour, the size of each update to 15 kb;
· Checking the computer's system memory that allows you to detect viruses that do not exist as files (for example, CodeRed or Slammer);
· Heuristic analyzer that allows you to neutralize unknown threats before the relevant updates of viral databases.
Any modern anti-virus product is not only a set of individual detection technologies, but also a complex protection system built on its own understanding of the antivirus company of how to ensure safety from malicious programs.
Kaspersky Antivirus Personal is designed for anti-virus protection of personal computers running Windows 98 / Me, 2000 / NT / XP operating systems, from all known types of viruses, including potentially dangerous software. The program performs constant control of all sources of virus penetration - email, Internet, floppy disks, CDs, etc. The unique system of heuristic data analysis effectively neutralizes unknown viruses. You can select the following variants of the program (they can be used both separately and in the aggregate):
· Permanent protection of the computer - check all the starts open and stored on the computer to the presence of viruses.
· Verification of a computer on demand - checking and treating both the entire computer as a whole and individual disks, files or directories. You can run such a check on your own or configure its regular automatic launch.
The program creates a reliable barrier on the path of penetration of viruses through email. Kaspersky Antivirus Personal automatically checks and treatment with the entire incoming and outgoing mail correspondence on POP3 and SMTP protocols and effectively detects viruses in the postal bases. The program supports a more seed formats of archived and compressed files and provides automatic anti-virus scan of their contents, as well as removing malicious code from archive files of ZIP, Cab, RAR, ARJ, LHA and ICE. The Kaspersky Anti-Virus includes a special component that protects the file system of the computer from infection - the file antivirus. It starts at the start of the operating system, constantly in the memory of the computer and checks all files that are stored and the files that are stored or programs.
Computer viruses. Antivirus programs
Computer viruses- Programs that create programmers specifically for damage to PC users. Their creation and distribution is a crime.
Viruses can multiply and hidden to embed their copies into files, boot sectors of discs and documents. The activation of the virus can cause the destruction of programs and data .. The first epidemic occurred in 1986 (the Brain virus - the brain in English) The World Epidemic Infection of the Postal Virus began on May 5, 2000, when computers on the Internet received messages "I love you" with nested The file that contains the virus.
Distinctive features of computer virusesare: 1) a small volume; 2) independent launch; 3) multiple code copying; 4) Creating interference to work correctly
On the scale of harmful effectscomputer viruses are divided into:
* Harmless - Do not affect the work of the PC, only reduce the amount of free memory on the disk, as a result of its reproduction
* Non-hazardous - the influence of which is limited to a decrease in memory on disk, graphic, sound and other external effects;
* Dangerous - lead to failures and freezes when working on a PC;
* Very dangerous - lead to loss of programs and data (change, removal), formatting of the hard drive and so on.
On the habitatcomputer viruses are:
* File viruses are able to implement in the programs and activate when they started
From OP viruses infect other software files (COM, EXE, SYS) by changing their code until the PC is turned off. Transmitted with illegal copies of popular programs, especially computer games. But they cannot infect data files (images, sound)
* Boot viruses Transmitted through the infected boot sectors when loading OS and is embedded in the OP, infecting other files. Protection rules: 1) It is not recommended to run the files of the dubious source (for example, before loading from the disk A - check antivirus programs); 2) Install in the BIOS PC (SETUP) protection of the boot sector from changes
* Macrowurus - infect Word and Excel documents. These viruses are actually macros and embedded in the document, infecting the standard document template. The threat of infection stops after closing the application. When opening a document in Word and Excel applications, the presence of macros is reported and it is proposed to prohibit their download. The choice of a ban on macros will prevent the load from infected, but also turn off the possibility of using beneficial macros in the document
* Network viruses - apply to a computer network.
When you open the postal message, pay attention to the nested files!
Antivirus program - a program designed to combat computer viruses.
In its work, these programs use various principles for finding and treating infected files.
For normal operation on the PC, each user must follow the update of antiviruses.
If the antivirus program detects the virus in the file, then it removes the virus software code from it. If treatment is not possible, the infected file is removed entirely.
There are various types of anti-virus programs - polyphag, auditors, blockers, guard, vaccines, etc.
Types of anti-virus programs:
Antivirus scanners - After starting, you check files and RAM and provide neutralization of the virus found
Antivirus Storam (monitors)- constantly being in the OP and provide checking files in the process of downloading them in op
Polyphagi. - the most universal and efficient antivirus programs. Check files, loading sectors of disks and OP to search for new and unknown viruses. Occupy a lot of space, work not fast
Auditors - Check changing the length of the file. Cannot detect the virus in new files (on floppy disk, when unpacking), because There are no information about these files in the database.
Blockers - Can detect and stop the virus at the earliest stage of its development (when writing to the boot sectors of the disks). Anti-virus blockers can enter BIOS Setup
Computer viruses and antivirus programs
Computer virus - a specially created computer program that is able to spontaneously join other programs, create your copies, implement them into files in order to violate other programs, damage files and directories.
Signs of virus manifestation:
- incorrect work of programs;
- slow computer work;
- the inability to load the operating system;
- disappearance of files and directories;
- changing file sizes;
- an unexpected increase in the number of files on the disk;
- reduction of the size of free operating memory;
- output to the screen of unexpected messages and images;
- feeding unforeseen sound signals;
- frequent "freezes" and malfunctions in the computer.
Viruses can spread through:
- executable programs;
- word, Excel documents;
- computer software;
- web pages;
- files from the Internet;
- letters e-mail;
- dies and CDs.
Classification of viruses on the scale of harmful effects
Classification of habitat viruses
Prevention of computer viruses:
- have a special boot disk;
- systematically check the computer for viruses;
- have the latest versions of antivirus;
- check all incoming data for viruses;
- do not use unlicensed software;
- select a ban on downloading macros when opening Word and Excel documents;
- select a high level of security in the "Observer Properties";
- do archive copies of files;
- add to autoloader file Antivirus watchman program;
- do not open an email attachment if the sender is unknown.
Antivirus programs - programs that prevent the infection with a computer virus and eliminate the effects of infection.
There are several types of antivirus programs that differ in the functions performed.
Polyphagi.
The most popular and efficient antiviral programs are antiviral polyphag programs (for example, Kaspersky Anti-Virus, Dr.Web).
To search for famous viruses are used so-calledmasks.
The mask of the virus is some permanent sequence of the program code specific for this particular virus.
If the antivirus program detects such a sequence in any file, the file is considered an infected virus and is treated.
To search for new viruses, the "Heuristic scanning" algorithms are used, that is, an analysis of the command sequence in the verifiable object. If the "suspicious" command sequence is found, the polyphag gives a message about a possible infection of the object.
Polyphases can provide files in the process of downloading them to RAM. Such programs are calledantivirus monitors.
TO polyphag advantages Refers their versatility. TOdisadvantages The large dimensions of the anti-virus databases you can include, which should contain information on the maximum possible amount of viruses, which, in turn, leads to a relatively small speed of the search for viruses.
Auditors
The principle of operation of the auditors (for example, ADINF) is based on counting checksums for files present on the disk. These checksums are then stored in antivirus database, as well as other information: file lengths, date of their last modification, etc.
With the subsequent startup, the auditors are checked by the data contained in the database, with actually calculated values. If the file information recorded in the database does not match the real values, then the auditors sign that the file has been changed or infected with the virus.
Lack of auditors It is that they cannot detect the virus in new files (on diskettes when unpacking files from the archive, in e-mail), since there are no information about these files in their databases.
Blockers
Anti-virus blockers are programs that are intercepting "virus-hazardous" situations and reporting this to this.These situations include, for example, writing to the boot sector of the disk. This entry occurs when installed on the computer of a new operating system or when infected with a bootable virus.
Anti-virus blockers in the computer BIOS received the greatest distribution. With the help of the BIOS Setup program, you can configure the BIOS in such a way that it will be prohibited (blocked) any entry into the boot sector of the disk and the computer will be protected from infection with loading viruses.
To the advantages of blockers The ability to detect and stop the virus at the earliest stage of its reproduction.
Development of lesson
by computer science
for grade 8
"Antivirus programs"
The purpose of the lesson: To acquaint students with the concept of "computer virus", classification of computer viruses and some types of antivirus programs and their purpose.
Tasks :
Educational:
D. an idea of \u200b\u200bthe types of existing viruses, paths of their distribution, precautions when working with other files,learn to check for viruses using the Kaspersky Anti-Virus program To check and save the file structure of the computer.
Developing:
Develop mental operations, theoretical, critical, creative thinking.
Educational:
To form students with the right attitude to the security of a personal computer.
Type of lesson: combined
Equipment: PC, projector, presentation to the lesson.
During the classes
I. Organizational moment.
Greeting, checking the appearance of students and their readiness for the lesson.
II. Message Topics lesson ( gaying crossword ).
One or more files are combined and compressed to reduce the information volume.
Information output device designed to output textual, numerical and graphic information on paper.
The command sequence that the computer performs during data processing.
Symbolic information entry device.
The graphic information entry device into the computer's RAM.
Today, the lesson will be studied:
What are computer viruses.
Types of computer viruses.
Signs of computer viruses.
Programs of combating computer viruses.
Methods of protection against computer viruses
Treatment and removal of viruses.
II. Actualization of the previously studied material.
Testing knowledge on the topic "Computer Software".
1. Computer is:
a) device for working with texts;
b) electronic computing device for treating numbers;
c) a device for storing information of any kind;
d) a multifunctional electronic device for working with information;
e) device for processing analog signals.
2. During execution, the application program is stored:
a) in video memory;
b) in the processor;
c) in RAM ;
d) on the hard disk; e)
e) in ROM.
3. The personal computer will not function if you turn off:
a) drive;
b) RAM ;
c) mouse;
d) printer;
e) scanner.
4. For long-term storage of information serves:
a) RAM;
b) processor;
c) external carrier ;
d) drive;
e) power supply.
5. File is:
a) a named set of single-type data elements called records;
b) the object characterized by the name, value and type;
c) a set of indexed variables;
d) a combination of facts and rules;
e) term.
6. Expansion of the file name, as a rule, characterizes:
a) the time of creating a file;
b) the size of the file;
c) the location occupied by the disk file;
d) the type of information contained in the file;
e) Place of file creation.
7. Text editor is a software product, which is part of:
a) system software;
b) programming systems;
c) applied software;
d) unique software;
d) operating system.
8. Operating systems are software products that are part of:
a) applied software;
b) system software;
c) database management systems;
d) programming systems;
e) unique software.
9. The operating system is:
a) the combination of the main devices of the computer;
b) Low-level programming system;
c) a set of programs that ensures all computer hardware devices and user access to them;
d) a set of programs used for operations with documents;
e) program to destroy computer viruses.
10. Computer device service programs are called:
a) loaders;
b) drivers;
c) translators;
d) interpreters;
e) compilers.
III. Studying a new material.
1. Opening conversation.
– Name a few common signs of a person and computer. Compare them by functionality.
The computer is an electronic analogue of a person. A person, like any biological organism, is exposed to various pathogenic viruses.
– Or can "get sick", "get infected" with a computer with a virus?
Today we find out: how does this happen, how to avoid this and how to "cure" a computer? How many computer viruses are, how do they behave, hitting the "computer" of the computer? Consequences of infection with a computer virus. What are they?
2. Explanation of the new material.
BUT) Computer virus – this is a specially created small program designed for computer disorders.. When recording the disk system regions or attributing to the files and produces various unwanted actions that often have catastrophic consequences.
1959 year - the IBM 650 computer discovered the virus that "eaten" part of the words.
The first "epidemic" of a computer virus occurred in1986 year, when the virus named Brain (eng. Brain) infected the floppy disks.
1988 year - Robert Morris in the US wrote a virus that struck 2,000 computers.
Currently, more than 50 thousand viruses infecting computers and distributing on computer networks are known. By the end of 1989, in a number of countries (USA, United Kingdom, Germany), laws providing for developers of computer viruses are under consideration. (In the USA up to 15 years).
A person, as a biological organism, is subject to various exposure to the external environment, including various diseases, the causes of which, sometimes, are viruses and bacteria that penetrate the human body out.
– Try to describe the stages and the consequences of the person's contamination by any virus (focus on the following moments):
the penetration of the virus into the human body occurs from the outside;
virus ability to self-insulating;
the activation of some viruses is not immediately after penetration into the body, butover time.
Activation may step:
The onset of a certain date or day of the week.
Running program.
Opening a document, etc.
B) viruses classification
Types of habitat viruses:
Network
Can transmit your software code on computer networks and run it on computers connected to this network.
Infection of a network virus can occur when working with e-mail or with "travels" on the World Wide Web.
On May 5, 2005, the World epidemic of infection with a postal virus began, when tens of millions connected to the Internet received postal report: I Love You, with the result that an avalanche-like virus infection occurred.
File
Implemented into the program and activate when they started.
They can infect other files until the computer is turned off.
Macrowurus
Infect document files, such as text documents.
The threat of infection is terminated only after closing the text document.
According to the degree of impact:
Harmless viruses - Have a slight impact on the work of the PC, occupying some of the system resources. Often, users do not even suspect their presence.
Non-hazardous viruses - Also occupy a part of the computer resources, but the user knows about their presence. Usually they are manifested in the form of visual and sound effects and do not harm the user data.
Dangerous viruses - Programs that violate the normal operation of user applications or the entire system.
Very dangerous viruses - Programs whose task is to destroy files, output from standing programs and OS or decaying confidential data
According to the features of the work algorithm distinguish:
The simplest viruses - Viruses that, when distributing their copies, necessarily change the contents of the disk sectors or files, so it is easy enough to detect.
Satellite Viruses (Companions) - A virus that is not implemented in the executable file itself, and creates its infected copy with another extension.
Stealth Virus (invisible) - Viruses that hide their presence in infected facilities, substituting instead of unreleased areas.
Polymorphic viruses (mutants) - Viruses modifying their code in such a way that copies of the same virus did not coincide.
Macrowuri - Viruses that infect documents of office applications.
Trojan program - A program that is masked for useful applications (utilities or even antivirus programs), but it produces various spy steps. It is not embedded in other files and does not have the ability to self-insulating.
Worms - These are pesting computer programs that are capable of self-insulating, but, unlike viruses, other files are infected. Wormy received its name because they use computer networks and email to distribute.
Today, the so-called network worms are most common, as well as macroviruses.
IN)Signs of computer viruses
Let's call the main signs of manifestation of computer viruses.
incorrect work of normally working programs;
slow computer work;
the inability to load the OS;
disappearance of files and directories;
changing file sizes;
an unexpected increase in the number of files on the disk;
reducing the size of free RAM;
output to the screen of unexpected messages and images;
feeding unforeseen sound signals;
frequent freezes and malfunctions in the computer.
D) Prevention of computer viruses.
Avoiding infection with viruses is almost impossible, so regularpreventive actions :
Computer testing for viruses using antivirus programs.
Check diskettes and disks for viruses.
Protecting your diskettes from recording when working on other computers.
Creating archive copies of valuable information for you.
Regular updating antivirus programs.
E) antivirus programs
So, a special place in this list is occupied by software protection software - antivirus programs. What kind of type do they relate? (System software).
Antivirus Program (Antivirus) - A program that allows you to identify viruses, treat infected files and discs, detect and prevent suspicious actions.
There are several types of antivirus programs that differ in the functions performed.
Polyphagi. . View the contents of the files located on the disk of the computer, as well as the contents of the computer's RAM in order to search for viruses.
Auditors . In pre-scanning mode, creates a database with checksums and other information that allows you to control the integrity of the files (control over the changes that occur in the PC file system).
Blockers . Check for viruses of launched files, interception of "virus-hazardous" situations.
No type of antivirus software separately gives full protection against viruses. Therefore, modern anti-virus programs typically include components that implement all these functions.
Dance Fizkultminutka
3. Laboratory workshop
Practical work number 1
Purpose: Learn to detect and remove viruses on removable media.
The task:
Install flash media inUSB The system unit connector.
Open the Kaspersky Anti-Virus program.
Perform the search for viruses to flash media.
The workshop is summarized, called aspen errors when working with the program.
Practical work number 2.
The task: With the help of the World Global Internet, find out the most popular antivirus programs currently:
in Russia
in the European Union
in USA
Discussion of outcomes of practical work with students.
In conclusion, we give two simple rules, observing which you can easily prevent the loss of valuable information in case of failure or infection of the machinevirus:
Rule №1. Having created any new file (containing, for example, text, program orfigure), be sure to immediately copy it to a floppy disk.
Rule №2. Any media who visited someone else's machine, be sure to check antivirus programs with updated antivirus bases.
IV. Summarizing.
What consequences can be infected with computer
viruses?
What are the signs of a computer infection with a virus?
What needs to be done first in case of infection
computer virus?
Estimation. Students explain their "+" and "-" when working in a lesson, basic mistakes when working for PCs.
V. Homework. Workshop 8 - 9. Topic 1.9 (theory)
Vi. Reflection.
Questions students:
How are the information studied at today's lesson, will you apply in further practical activities?
How useful to you, how to users of PC, are the skills of working with antivirus programs?
 Magnetometry in the simplest version The ferrozond consists of a ferromagnetic core and two coils on it
Magnetometry in the simplest version The ferrozond consists of a ferromagnetic core and two coils on it Effective job search course search
Effective job search course search The main characteristics and parameters of the photodiode
The main characteristics and parameters of the photodiode How to edit PDF (five applications to change PDF files) How to delete individual pages from PDF
How to edit PDF (five applications to change PDF files) How to delete individual pages from PDF Why the fired program window is long unfolded?
Why the fired program window is long unfolded? DXF2TXT - export and translation of the text from AutoCAD to display a dwg traffic point in TXT
DXF2TXT - export and translation of the text from AutoCAD to display a dwg traffic point in TXT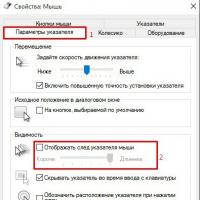 What to do if the mouse cursor disappears
What to do if the mouse cursor disappears