Cryptopro CSP 3.9 license. Step-by-step installation of the program without installation disk. Media with unchecked keys and protected messaging
To install the system without installation disk You must download and install all distributions of components from this instruction. Installation must be performed with local administrator rights.
Installation SCJC Cryptopro CSP
Download and install CSP cryptopro distribution according to the license acquired.
Open the CSP cryptopro program and enter serial number licenses. Depending on the computer, this can be done in different ways:
Installing the Rutoken driver
Download and install components to work with the Rutoken media. (If certificates are stored on Flash-carrier skip this step). When installing the components, disconnect the Rutoken from the computer.
Capicom installation
Install Certification Center Certificates
Download and install certificates of the Certification Center
Installing and configuring a browser
The system works in the following browsers: Internet Explorer. Versions not lower than 11, Mozilla Firefox., Google Chrome., Yandex.Browser, Opera.
For installation .
For the correct operation of Internet Explorer with the outline system. Experience, you must start the utility to adjust the browser.
Also, the browser setup can be performed manually. To do this, use this.
For the installation of other browsers, contact your system administrator.
Installing Adobe Reader.
Download and install Adobe Reader.. Use the link to the official website Adobe. For starting the installation, you must select the version of the operating system and language.
Setting a shortcut
For easy login, save the desktop. After the installation is completed, you must restart the computer. Before starting work in the reporting system, do not forget to establish a certificate of signature. Use the instructions for installing a personal certificate.
Installation completed
Cryptoprovider CSP cryptopro is designed for:- authorization and legal significance electronic documents When exchanging them between users, through the use of formation and verification procedures digital signature (EDS) in accordance with domestic standards GOST R 34.10-94, GOST R 34.11-94, GOST R 34.10-2001;
- confidentiality and monitoring the integrity of information through its encryption and imitobackers, in accordance with GOST 28147-89; ensuring authenticity, confidentiality and imitobackers of TLS connections;
- monitoring integrity, system and applied software for its protection against unauthorized changes or from violation of the correctness of functioning; Management of key elements of the system in accordance with the Rules of Defense Remedies.
Key carriers for CSP cryptopro
Cryptopro CSP. It can be used in conjunction with many key carriers, but most often the Windows, flash drives and tokens are used as key carriers.
The safest and most convenient key carriers that are used in conjunction with Cryptopro CSP.are tokens. They allow convenient and safe to keep your certificates electronic signature. The tokens are arranged in such a way that even in the case of theft, no one can use your certificate.
Supported CSP Cryptopro Key carriers:- roots 3.5 ";
- mPCOS-EMV processor cards and Russian intelligent cards (Oscar, Rick) using smart card readers supporting the PC / SC protocol (GEMPC TWIN, TOWITOKO, OBERTHUR OCR126, etc.);
- touch-Memory DS1993 - DS1996 tablets using ACCORD 4+ devices, electronic lock "Sable" or reading tablet Touch-Memory Dallas;
- electronic keys from uSB interface;
- replaceable media with USB interface;
- windows registry;
Digital signature certificate for CSP cryptopro
Cryptopro CSP. It works correctly with all certificates issued in accordance with the requirements of GOST, and therefore with most certificates issued by certifying centers in Russia.
In order to start using CSP cryptopro, you will definitely need a digital signature certificate. If you have not yet acquired a digital signature certificate, we recommend that you.
Supported Windows operating systems
| CSP 3.6. | CSP 3.9. | CSP 4.0. | |
|---|---|---|---|
| Windows 10. | x86 / x64. | x86 / x64. | |
| Windows 2012 R2. | x64. | x64. | |
| Windows 8.1. | x86 / x64. | x86 / x64. | |
| Windows 2012. | x64. | x64. | x64. |
| Windows 8. | x86 / x64. | x86 / x64. | x86 / x64. |
| Windows 2008 R2. | x64 / Itanium | x64. | x64. |
| Windows 7. | x86 / x64. | x86 / x64. | x86 / x64. |
| Windows 2008. | x86 / x64 / itanium | x86 / x64. | x86 / x64. |
| Windows Vista. | x86 / x64. | x86 / x64. | x86 / x64. |
| Windows 2003 R2. | x86 / x64 / itanium | x86 / x64. | x86 / x64. |
| Windows XP. | x86 / x64. | ||
| Windows 2003. | x86 / x64 / itanium | x86 / x64. | x86 / x64. |
| Windows 2000. | x86. |
Supported UNIX-like operating systems
| CSP 3.6. | CSP 3.9. | CSP 4.0. | |
|---|---|---|---|
| iOS 11. | Arm7. | Arm7. | |
| iOS 10. | Arm7. | Arm7. | |
| iOS 9. | Arm7. | Arm7. | |
| iOS 8. | Arm7. | Arm7. | |
| iOS 6/7 | Arm7. | Arm7. | Arm7. |
| iOS 4.2 / 4.3 / 5 | Arm7. |
|
|
| Mac OS x 10.12 | x64. | x64. | |
| Mac OS x 10.11 | x64. | x64. | |
| Mac OS x 10.10 | x64. | x64. | |
| Mac OS x 10.9 | x64. | x64. | |
| Mac OS x 10.8 | x64. | x64. | x64. |
| Mac OS x 10.7 | x64. | x64. | x64. |
| Mac OS x 10.6 | x86 / x64. | x86 / x64. |
|
| Android 3.2+ / 4 | Arm7. | ||
| Solaris 10/11 | x86 / x64 / sparc | x86 / x64 / sparc | x86 / x64 / sparc |
| Solaris 9. | x86 / x64 / sparc | ||
| Solaris 8. | |||
| AIX 5/6/7 | PowerPc. | PowerPc. | PowerPc. |
| FreeBSD 10. | x86 / x64. | x86 / x64. | |
| FreeBSD 8/9 | x86 / x64. | x86 / x64. | x86 / x64. |
| FreeBSD 7. | x86 / x64. | ||
| FreeBSD 6. | x86. | ||
| FreeBSD 5. | |||
| LSB 4.0. | x86 / x64. | x86 / x64. | x86 / x64. |
| LSB 3.0 / LSB 3.1 | x86 / x64. | ||
| Rhel 7. | x64. | x64. | |
| RHEL 4/5/6 | x86 / x64. | x86 / x64. | x86 / x64. |
| Rhel 3.3 specials. assembly | x86. | x86. | x86. |
| RedHat 7/9 | |||
| CentOS 7. | x86 / x64. | x86 / x64. | |
| CentOS 5/6 | x86 / x64. | x86 / x64. | x86 / x64. |
| TD OSA AIS FSSP Russia (Goslinux) | x86 / x64. | x86 / x64. | x86 / x64. |
| CentOS 4. | x86 / x64. | ||
| Ubuntu 15.10 / 16.04 / 16.10 | x86 / x64. | x86 / x64. | |
| Ubuntu 14.04 | x86 / x64. | x86 / x64. | |
| Ubuntu 12.04 / 12.10 / 13.04 | x86 / x64. | x86 / x64. | |
| Ubuntu 10.10 / 11.04 / 11.10 | x86 / x64. | x86 / x64. | |
| Ubuntu 10.04 | x86 / x64. | x86 / x64. | x86 / x64. |
| Ubuntu 8.04 | x86 / x64. | ||
| Ubuntu 6.04. | x86 / x64. | ||
| Altlinux 7. | x86 / x64. | x86 / x64. | |
| Altlinux 6. | x86 / x64. | x86 / x64. | x86 / x64. |
| Altlinux 4/5 | x86 / x64. | ||
| Debian 9. | x86 / x64. | x86 / x64. | |
| Debian 8. | x86 / x64. | x86 / x64. | |
| Debian 7. | x86 / x64. | x86 / x64. | |
| Debian 6. | x86 / x64. | x86 / x64. | x86 / x64. |
| Debian 4/5 | x86 / x64. | ||
| Linpus Lite. 1.3 | x86 / x64. | x86 / x64. | x86 / x64. |
| Mandriva Server 5. Buisness Server 1. |
x86 / x64. | x86 / x64. | x86 / x64. |
| Oracle Enterprice Linux 5/6 | x86 / x64. | x86 / x64. | x86 / x64. |
| Open SUSE 12.2 / 12.3 | x86 / x64. | x86 / x64. | x86 / x64. |
| SUSE Linux Enterprice 11 | x86 / x64. | x86 / x64. | x86 / x64. |
| Linux Mint. 18 | x86 / x64. | x86 / x64. | |
| Linux Mint 13/14/15/15/17 | x86 / x64. | x86 / x64. |
Supported algorithms
| CSP 3.6. | CSP 3.9. | CSP 4.0. | |
|---|---|---|---|
| GOST R 34.10-2012 Creating a signature | 512/1024 Bit | ||
| GOST R 34.10-2012 Signature check | 512/1024 Bit | ||
| GOST R 34.10-2001 Creating a signature | 512 bits | 512 bits | 512 bits |
| GOST R 34.10-2001 Signature check | 512 bits | 512 bits | 512 bits |
| GOST R 34.10-94 Creating a signature | 1024 bits * | ||
| GOST R 34.10-94 Signature check | 1024 bits * | ||
| GOST R 34.11-2012 | 256/512 Bit | ||
| GOST R 34.11-94 | 256 bits | 256 bits | 256 bits |
| GOST 28147-89 | 256 bits | 256 bits | 256 bits |
* - To the CSP 3.6 R2 cryptopro version (assembly 3.6.6497 from 2010-08-13) inclusive.
CRYPTOPRO license conditions CSP
By buying CSP cryptopro, you get a serial number that you need to enter during the installation or program setting. The validity of the key depends on the chosen license. CSP cryptopro can be distributed in two versions: with an annual license or indefinite.
Buying permanent licenseYou will receive the CSP cryptopro key, whose validity will not be limited. If you buy, you will get a serial number Cryptopro CSP.which will act within a year after purchase.
- Key generation and coordination keys
- Formation and scan of electronic signature
- Import of software generated by EP's entered key keys - to enhance their secureness
- Updating the Cryptopro CSP Cryptopro Player Installation Base
Features
The main feature (earlier the product was called "Cryptopro Etoken CSP") is the use of technology of functional key carrier (FCN).
Functional key carrier (FCN) - Architecture of software and hardware products based on smart cards or USB tokens, implementing a fundamentally new approach to providing safe use Key on a smart card or USB-tokene.
Due to the presence of a protected communication channel between the token and cryptoprodroter, some of the cryptographic transformations, including storage of private keys and the EP keys in the unknowable form, is made on a smart card or USB-token.
In addition to the hardware generation of keys, their safe storage and formation of EP in a key carrier microprocessor, the FCN architecture allows you to effectively withstand attacks associated with the HASH value or signature submenus in the communication channel between the CSP software and hardware.
The CSP Cryptopro CSP version 3.9 is a specially designed token Jacarta Cryptopro, presented in smart card form factor and USB-tokens.
Part Ski "Cryptopro FCN CSP" version 3.9 The Jacarta Cryptopro's specially designed token is included with the possibility of calculating EP according to Crypto-Pro Technology and manufactured in USB-Tocken Form Factors (in Nano or XL Corps) or Smart Cards.
 |  |
Jacarta Cryptopro provides secure storage and use of EP enclosed keys, performs CSP and tokens mutual authentication, as well as strict two-factor authentication of the token user-owner.
Key Benefits Jacarta Cryptopro
- It is the fastest token among FCN devices (ahead of existing products operating with FCN, in the speed of formation of an electronic signature almost 3 times - on the basis of the protocol of measurements of the speed of the FCH devices "Crypto-Pro" dated December 12, 2014).
- Principle applied Secure By Design. - A protected microcontroller is used, designed as safe, for security purposes, has built-in protection both on hardware and software levels from cloning, hacking and all other attacks known to date.
- Generation of EP keys, matching keys, as well as the creation of EP occurs inside the Jacarta Cryptopro Tocken.
- Uses the protected data transfer channel with the CSP Cryptopro CSP software part.
Structure
"Cryptopro FCN CSP" version 3.9 Consists of two key components.
1. USB Tocken or Smart Card Jacarta Cryptopro:
- it is a functional key carrier (FCN), in which Russian cryptography has been implemented hardware;
- allows you to safely store and use closed keys EP;
- forms EP "under the mask" - k (h), which allows you to protect the exchange channel between the token (smart card) and software cryptoproder (CSP);
- performs CSP mutual authentication and tokens and strict user authentication - tokens owner.
2. Cryptoprovider (CSP):
- is a high-level software interface (MS CAPI) for external applications and provides them with a set of cryptographic functions;
- from the signature "under the mask" obtained from the hardware tokeny (smart card) - K (H), "removes the" Mask K (S) and forms a "normal" signature, understandable to external applications
Architecture "Cryptopro FCN CSP" version 3.9

TECKEN SPECIFICATIONS JACARTA CRYPTOPRO
| Microcontroller characteristics | Manufacturer | Inside Secure. |
| Model | AT90SC25672RCT. | |
| EEPROM MEMORYS. | 72 KB | |
| Characteristics of the operating system | Operating system | Athena Smartcard Solutions OS755 |
| International Certificates | CC Eal4 +. | |
| Supported cryptoalgorithms | GOST R 34.10-2001, GOST 28147-89, GOST R 34.11-94 | |
| Supported interfaces | USB | Yes |
| Contact interface (ISO7816-3) | T \u003d 1. | |
| Security certificates | FSB of Russia | Certificate of conformity of the FSB of Russia No. SF / 114-2734 Certificate of conformity of the FSB of Russia No. SF / 114-2735 |
| Supported OS | Microsoft. Windows Server 2003 | (32/64-bit platforms) |
| Microsoft Windows Vista. | (32/64-bit platforms) | |
| Microsoft Windows 7. | (32/64-bit platforms) | |
| Microsoft Windows Server 2008 | (32/64-bit platforms) | |
| Microsoft Windows Server 2008 R2 | (32/64-bit platforms) | |
| CentOS 5/6. | (32/64-bit platforms) | |
| Linpus Lite 1.3. | (32/64-bit platforms) | |
| Mandriva Server 5. | (32/64-bit platforms) | |
| Oracle Enterprise Linux 5/6 | (32/64-bit platforms) | |
| Open SUSE 12. | (32/64-bit platforms) | |
| RED HAT ENTERPRISE LINUX 5/6 | (32/64-bit platforms) | |
| SUSE Linux Enterprise 11 | (32/64-bit platforms) | |
| Ubuntu 8.04 / 10.04 / 11.04 / 11.10 / 12.04 | (32/64-bit platforms) | |
| Alt Linux 5/6. | (32/64-bit platforms) | |
| Debian 6. | (32/64-bit platforms) | |
| FreeBSD 7/8/9 | (32/64-bit platforms) | |
| Cryptographic operations | Key Import | 3.2 Op / s (USB TECKEN), 2.4 OP / S (Smart Map) |
| Creating a signature | 5.8 Op / S (USB-Token), 3.9 Op / s (Smart Map) | |
| Available key carriers | Smart Map. | Jacarta Cryptopro. |
| USB Tocken | Jacarta Cryptopro. |
Security certificates
confirming that the means of cryptographic protection of information (SCJO) "Cryptopro FCN CSP" version 3.9 (execution 1) complies with the requirements of GOST 28147-89, GOST R 34.11-94, GOST R 34.10-2001, requirements of the FSB of Russia to encryption (cryptographic) COP1, electronic signature requirements approved by the Order of the FSB of Russia dated December 27, 2011 No. 796 established for the COP class, and can be used for cryptographic protection (creation and management of key information, the encryption of the data contained in the area random access memory, calculating the value of the hash function for the data contained in the RAM area, the protection of TLS connections, the implementation of the electronic signature functions in accordance with Federal law On April 6, 2011 No. 63-FZ "On Electronic Signature": Creating an electronic signature, checking the electronic signature, creating a key of an electronic signature, creating an electronic signature key) information that does not contain information constituting the state secret.
confirming that the means of cryptographic protection of information (SCJO) "Cryptopro FCN CSP" version 3.9 (execution 2) complies with the requirements of GOST 28147-89, GOST R 34.11-94, GOST R 34.10-2001, requirements of the FSB of Russia to encrypted (cryptographic) X2, electronic signature funds approved by the order of the FSB of Russia dated December 27, 2011 No. 796 established for the CC2 class, and can be used for cryptographic protection (creating and manage key information, encryption of data contained in the RAM area, calculate the value Hash functions for the data contained in the field of RAM, the protection of TLS connections, the implementation of the electronic signature functions in accordance with the Federal Law of April 6, 2011 No. 63-FZ "On Electronic Signature": creating an electronic signature, an electronic signature check, Creating an electronic signature key, creating an electronic signature key) information that does not contain information constituting State secret.
 Error appearance during program launch
Error appearance during program launch FRIGATE plugin for Firefox
FRIGATE plugin for Firefox How to show hidden folders and files in Windows
How to show hidden folders and files in Windows Ways how to make a screen on a laptop brighter or darker
Ways how to make a screen on a laptop brighter or darker How to format a flash drive, disk protection
How to format a flash drive, disk protection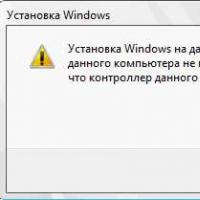 If installing Windows to this disc is not possible
If installing Windows to this disc is not possible During installation of Windows "Make sure that the controller of this disc is included in the computer's BIOS menu.
During installation of Windows "Make sure that the controller of this disc is included in the computer's BIOS menu.