Configuring VPN connections. Automatic creation of a VPN connection in the Windows script. What is a VPN connection and what it is needed
Greetings! And right away. What is the VPN server for? It is mainly used to change the IP address and its own country to get around the various blockages of sites at work and at home. In addition, the VPN connection helps encrypt traffic and thus ensures the security of the transmitted data.
For example, using public Wi-Fi, all data that is transmitted through the network can be "hijacked". Theoretically, it can be any files, but usually steal passwords from wallets, mail, skype and anything. In this article, we will configure your own VPN server, it is not difficult. Despite the volume of text, the main action takes the small part, and the rest - buns 🙂 in the article also have a video.
On the Internet there is a bunch and small, from free to very paid. Disadvantages of free VPN services:
- limited in speed
- instability (then everything is fine, then it slows down terribly)
- traffic restrictions (up to several gigabytes per month)
- restrictions of the period of free use
- periodically you need to look for other services
- it's not a fact that the transmitted data will be safe, you should not hope for anonymity at all, I would say.
Disadvantages of paid:
- not always there is a desired country or city
- connected IP addresses (used hundreds of customers), applies to free
- it just happens without refunding money, for example, traffic is not unlimited, some servers do not work or too slow
There are advantages of VPN services - it is simplicity of use, relative low cost.
Own VPN server on hosting VPS / VDS
So, if you need a specific country or city, or a lot of traffic is required, which do not give VPN services, security guarantee - then it makes sense to be confused by setting up a personal VPN server. As a rule, it requires deep knowledge of system administration of servers. But I tried to explain everything just to understand even the kettle)
The disadvantages of this method also have:
- only one IP address to which you can "transfer", but there are additional fees for a fee
- nontrivial setup for the first time
- paid
Read to the end, and I will show how to use your VPS server to bypass lockout without setting up on it VPN.
What is a VPS / VDS server?
Hosting providers on the Internet countless. All of them allow them to post their websites. The most popular service is a virtual hosting. More advanced is the selected virtual server - VPS (VDS is, consider, the same thing). On VPS you can place sites, lift the VPN server, mail server, game server - yes anything!
You need to know that the VPS server is a few species: OpenVZ, Xen and KVM. You need a VPN server to work KVM.. Server type is specified in hosting tariffs. OpenVz and Xen are also sometimes suited, but you need to write to the technical support of the hosting and asking if the "Tun" module is connected. Without going into details for what it is, just asking. If not, can they turn it on. It will not hurt to ask whether VPN will work as such (even at KVM), because Some companies cover this opportunity. Oh yes, Server Operating System - Debian, Ubuntu or CentOS (generally, Linux-like). Server power does not matter.
Configuring a VPN server
At my disposal there is a KVM VPS server. Here, everything works immediately, it is not necessary to write anywhere.
- When ordering services, you can choose the easiest tariff plan "Micro"
- All sites open even on servers in Russia
- There is a free trial period of 7 days
- Technical support helps
- For my visitors, when entering a promotion: itLike60 - you will get a real discount of 60% for the first payment.
HostName Introduce anyone or the name of your site (if you are in the future). «OS Template» Select "Ubuntu 14.04 64bit" or any of Ubuntu, Debian, CentOS:

The operating system can then be changed, if suddenly it does not work.
After payment, the mail arrives to enter the control panel and the root password to set up the server. As well as the IP address of the server, and it is it that will be your IP address when we raise the VPN and connect to it from the computer


Press the "Manage" button and fall into the administration window:

Here we do not need to touch anything. The only thing that may be needed is to reinstall the operating system - the "REINSTALL" button, which is later.
Now we need to connect to the server to send commands to him. For this we will use free program Putty.
Unpack the archive with the program and run the file putty.org.Ru \\ Putty Portable \\ Putty_Portable.exe
In the Host Name field, we insert the IP address of the server that came in the letter, you can also copy it from the control panel:

and click "Connect". If such a window jumped out, then click "yes":

We must appear the Black Console Window (command line). It is here that we will give teams. But first need to log in. To do this, in the "Login" field, we enter "ROOT"

Then copy from the ROOT password and insert it in the "Password" field. To insert here from the clipboard, you just need to click once right-click on the console window. In this case, the password is not printed on the screen, such a feeling that nothing happened. Everything is fine, click "ENTER". Should slip lines with information about the system. If you wrote some error, then check all times. Also, the console will not wait a long time while you are looking for a root password. If an error pops up by that time, then run PUTTY again.
Installing and launching the main script
We are already on the finish line in configuring your own VPN server. There are many instructions on the Internet how to install the server, but they all require knowledge system administratorFor minor nuances are overlooked. To joy to all teapots, there is a universal script "OpenVPN Road Warrior", which will make all the work itself. We only need to give the command to download and run it.
So, copy this line and insert into the console window by right-click and click "Enter": wget https://git.io/vpn -o OpenVPN-install.sh && bash OpenVPN-install.sh

All sorts of lines and, if the script has been successfully downloaded and started, the dialog of the VPN server configuration wizard will begin with us:

The script finds the estimated value for each parameter and invites it to agree with it, i.e. Press "ENTER", or enter your value.
- The first parameter is «IP Address». The script must offer the same IIP VPS server. So it should be in 99.9% of cases, but if it is, for some reason, not so, then correct the correct address.
- Second - Protocol UDP or TCP.. We leave the default UDP.
- Go ahead, "Port: 1194" - We agree.
- "What DNS Do You Want To Use with the VPN?" - Choose "Google", i.e. Drive the digit "2" instead of a single, ENTER. If google is blocked, then we leave the default.
- "Client Name" - Username. You can create access for different users. By default, "Client" - agree.
- "Press Any Key ..." - Press "ENTER" and wait a few minutes until everything is installed and configured.
In general, the creation VPN Server This is over, it's time to reap the fruits. In the installation process, the script created a file with the setting for our computer. So that we can use the server, this file needs to download. To do this insert into command line: cat ~ / client.ovpn

The contents of the file "Client.OVPN" will be displayed. Now it must be accurately copied to the clipboard. Through the command to enter the command, we allocate the mouse all the lines, except the latest (for new commands), i.e. The last highlighted line will be " ". To copy the "Ctrl-V" selected to the clipboard.
Now on the computer in Windows 7/8/10, we open a notebook and insert the copied text into it. Save the file on the desktop under the name "client.ovpn".
If you plan to access the server to other people, it is better to create for them separate files, for example, vasya.ovpn. To do this, simply launch the script again and now chose the 1st point - creating a new user.
Client installation for Windows 7 / 8/10 / XP and Android
Congratulations, we are on the finish line! Now just left to install a free program that will connect to our VPN server. It is called "OpenVPN".
Download the version for Windows and install it, you do not need to run.

If all sorts of windows appear in the installation process, we agree with everything.
To connect to the server, click on the desktop on the file "client.ovpn" by right-click and select "Start OpenVPN On This Config File":

A black window will appear with the connection initialization process. If everything has passed successfully, the last line must be type:

A window can fall out with a type of type. new network, then choose the "public network".
You can check, go to the website 2IP.ru and see your IP, must match the IP of the VPS server:

The server console window is now safe you can close. And to close the NPN connection and return the old ip - you need to close the window from OpenVPN.
To connect the next time, it is easy enough to run the file "Client.OVPN" from the desktop, nothing more needs to do anything.
With phone It is still easier, you need to install OpenVPN application through the playmarket, download the client.ovpn file into memory, select it in the application and connect to our VPN server.
That if something went wrong
If you feel that because of your mistake now everything goes on a speed, then you can reinstall operating system on hosting. To do this, in the Reinstall Click Control Panel (see Panel Screenshot) and select a new operating system (or the same):

Let's give the "REINSTALL" button and wait for 10 minutes. Also will be issued a new root password, do not lose it!

Connect errors
Most of the problems occur during the connection to the server in the OpenVPN program, especially in Windows 8/10. In the black window there may be errors, for example:
- Flushipnettable Failed On Interface
- All Tap-Win32 Adapters On This System Are Currently in Use
- Createfile Failed on Tap Device
- DNS FAILED ..
At the same time, the first thing to do is to give a program of administrator rights and, accordingly, to enter the system with administrator rights. We go B. "C: \\ Program Files \\ OpenVPN \\ BIN \\"Clicking the right button on the OpenVPN.exe file -\u003e properties. On the Compatibility tab, we set the "execute this program on behalf of the administrator." Now everything should work.
More treatment options:
- remove the program and reinstall on behalf of the admin
- turn off the "Routing and remote access"(" Routing and Remote Access ") through "Control Panel -\u003e Administration -\u003e Services"
- try to reinstall from or from here
- delete all VPNO programs and pribluds from other paid and free services
It is possible to understand exactly the problem in a computer or laptop, you can, if you install an OpenVPN application via the playmarket on your phone or tablet, download the Client.OVPN file and connect to our VPN server. If it does not work, then you need to look for the cause on the server, write to the support service.
If everything worked, the sites are stupid and open with interruptions
Pay attention to messages in the black window, there are no repeated lines "Read From Tun / Tap ... (code \u003d 234)"

and also on the message somewhere in the middle of "Warning: 'Tun-MTU" IS Used Inconsistently, Local ... ":
In this case, open the client.ovpn file in notepad and in the new first line write:
tun-MTU 'server value'
server value - This is the number specified at the end of the line in the text "Remote \u003d 'Tun-MTU 1500". We substitute your value! As a result, it should work like this:

This is done because for some reason the MTU value on the computer and on the VPS server differ. File.OVPN for smartphone is left untouched!
Let traffic via proxy at all without settings
You can use our VPS / VDS server as Proxy Server. To do this, we do everything as before before pressing the "Connect" button in the PUTTY program. No need to open the console and run the script. We go to the "SSH-\u003e TUNNEL" tab, we prescribe Source Port: 3128

Oops, the article adds later, here I have putty in English, but the essence of the same.
If you write an error "You Need to Specify A Destination Address in the Form Host.name:port", then switch to "Dynamic" instead of "Local".
On the Connection tab in the "Seconds Between Keepalives ..." field, we put 100 seconds, it is necessary that the connection does not break due to downtime. Now connect - click "Open", enter a login / password. Next, we go to network settings in the browser and prescribe a proxy server there. In chrome it "Settings-\u003e Search for settings-\u003e Write 'Proxy' -\u003e Proxy Server Settings."We do everything as in the screenshot:

Now all sites will work through our server, but only in the browser and some programs. Other programs will not see the proxy, will work directly. It is necessary in each program in the connection settings, if they are provided, to register the address, port and proxy type: SOCKS4 / 5. Or install OpenVPN and do not use proxy.
How to start through proxy only individual sites
Install the extension for Google Chrome. or Mozilla Firefox., called. In the settings you need to add our proxy server:


On the "URL PATTERNS" tab, add the site masks to be opened through our server. Site mask is his name with the stars on the sides.

Everything, now the added site will go through Proxy, and all others directly. If you click on the extension icon, you can choose to let all sites through it or any at all.
Label for automatic connection
Connect the Putty to the proxy can be with one click. To do this, you need to register login server before connecting in the Connection-\u003e DATA section, the one is usual root


Now you need to create a shortcut on the desktop that specifies such parameters:

"C: \\ Program Files \\ Putty \\ Putty.exe" -Load MyVPN -PW password_K_Servera
where myVPN. - This is the name of the saved session. Everything, one item remained - remove the Putty window from the taskbar in the system tray. You need to download the modification of the utility and replace the EXE file. Now in the settings on the tab Behaviour. A corresponding check mark appears, but this can not be done.
The article discusses the setting client computer under windows control 7, from which the connection to the remote worker must be set. windows table. Here, the configurations of the server and the computer, to which the connection will be installed.
Creating a new VPN connection
1. Open the "Network Management Center and common access"To do this, click on the connection icon in the system tray by right-click and select the menu item" Network and Shared Access ". "Network and Shared Access Center" can also be opened through the control panel.
3. Select "Connect to Workstation. Configuring a telephone or VPN connection to workplace "and click" Next ".

4. Select "Use My Internet Connection (VPN)".

5. Enter the "Internet address" and destination name and click "Next".

6. Fill in the "User" and "Password" fields and click Connect.

7. After connecting to click "Close".

So that the connected network is not basic need to perform the following steps
8. Open the "Network and Common Access Control Center".
9. Click on the "Change Adapter Settings" link (left).

10. Find the created connection, click on it with the right mouse button and select the "Properties" menu item.

11. On the Network tab, select "Internet Protocol version 4 (TCP / IPv4)" and click "Properties".

12. In the "Properties window that opens. Internet Protocol version 4 (TCP / IPv4) »Click on the" Advanced "button.

13. In the window that opens " Extra options TCP / IP »Remove the daw" Use the main gateway in the remote network ".

14. Close all windows by pressing the "OK" buttons. This will show a warning that a number of changes will take effect after a re-connection.

15. To change the changes to take effect, in the window open at step 10, find your connection, right-click and select the menu item "Disable".

16. After shutdown, right-click on your connection and select "Connect". When requesting a password, fill in the "User" and "Password" fields and click "Connect".

Connect to a remote desktop
17. Install the VPN connection as described in step 16.
18. Run the "Connection to the Remote Desktop" program. Usually the shortcut is located in the Start -\u003e All Programs menu -\u003e Standard -\u003e Connect to the remote desktop. " And you can start writing the text "Connect to a remote desktop" and the program will be found.
19. In the "Connection to Remote Desktop" window that appears, enter the IP address or computer name and click "Connect".

20. In the window that appears " Windows security"Enter the username and password and click OK. If you have already entered the remote desktop, the system will prompt the username, see the drawing.

21. In the window that appears, the system will warn you that it cannot confirm the authenticity of the computer, see the drawing. If you are sure that you connect to the desired computerYou can set the checkbox "no longer display a request for connections to this computer" and click "Yes."

22. After working with a remote computer, you can simply close the window. Then the session will be saved and, with the next connection, you will see all the windows you open in constant condition. If the session is required to close (usually you need to do on servers), then you need to exit the system on the remote computer.
- When choosing a connection protocol, think about how to use VPN. It is known that the PPTP protocol works quickly wireless networkBut less secure than L2TP and IPSec. Therefore, if you take care of security, use L2TP or IPSec. If you connect to VPN at work, your employer will most likely inform you which protocol to choose. If you use your own VPN, select a protocol that is supported by your Internet provider.
- Choosing a VPN provider, think about security. If you want to use VPN to send documents and emails, or want to protect yourself when working on the network, select a VPN provider that offers SSL (TLS) or IPsec encryption. SSL encryption protocol is the most popular. Encryption is a method to hide data from outsiders. In addition, select the VPN provider, which uses OpenVPN to encrypt, and not PPTP. In recent years, several vulnerabilities have been found in PPTP; In this case, OpenVPN is usually considered more safe method encryption.
- Choosing a VPN provider, think about privacy. Some providers are followed by the activity of their customers and can inform the authorities if any suspicions arise. If you want your activity on the Internet to be confidential, select a VPN provider that does not lead user logs.
- Choosing a VPN provider, think about the bandwidth VPN. It determines how much data can be transmitted. Keep in mind that high-quality videos and music files have a larger size and, therefore, require greater bandwidth than text files and images. If you are going to use VPN for viewing and transferring confidential documents, any VPN provider will provide sufficient bandwidth. But if you, for example, want to watch Netflix or play online games, select a VPN provider that will allow you to use unlimited bandwidth.
- Choosing a VPN provider, consider whether you want to view content, which is available only in other countries. When you are viewing web pages, they get your IP address that defines your location. If you try to get access to content in another country, you may not succeed because of the IP address, because there is no copyright agreement between the countries. Therefore, look for a provider with output servers - in this case you will have the IP address of the country you need. So you will get access to content in another country using foreign servers. Select a VPN provider that has servers in the country with the content you need.
- Choosing a VPN provider, think about whether you will connect to a VPN on a computer or mobile device. If you travel a lot or often use a mobile device (smartphone or tablet), select a VPN provider that provides a VPN connection for mobile devices or even provides applications compatible with your mobile devices.
- Choosing a VPN provider, think about what support you need. Read the reviews and find information on customer support with a particular VPN provider. Some providers provide support only by phone, and with others can also be contacted by chat or by e-mail. Find a provider that offers a convenient customer support method. Also look for reviews (through search engine, such as Yandex or Google) about the provider to assess the quality of customer support.
- Choosing a VPN provider, think about what amount you are willing to spend. Some VPN providers offer free services (for example, Open VPN), but, as a rule, in this case services (functions, bandwidthSupport and so on) will be trimmed. Since there are many VPN providers, compare prices of some of them. Surely you will find a provider who will provide you with the services you need at an affordable price.
Today I will tell you how to configure a VPN connection between two computers. Most recently discovered this opportunity. It turns out to create VPN connections Do not need to configure the VPN server.
Why do I need it? For connecting B. unified Network, two remote to a large distance of computers. Distance between them, about 50 km. According to B. physical network It will not be possible to connect. How to do it, and what is needed for this, read further.
It has long appeared the idea to connect these computers, but everyone did not reach hands. Ask for what? For throwing photos between them and personal documents, for games over the network.
To implement the conceived, you need one of the computers (which will be created by the VPN connection) had a dedicated IP address. Nothing more needs.
Create a network
And so bend. For the machine on which the VPN connection will be created. I will use my homework.
Open the "Network Management Center ..." from the "Control Panel", in this window, click on the "Changing parameters"
In the window that opens " Network connections"Press ALT to display the menu buttons and select the" File "menu -" New Incoming Connection "
 Now you should choose a user who will have the right to connect to the VPN network. I did not choose an existing user, and created a new name " vPN.”
Now you should choose a user who will have the right to connect to the VPN network. I did not choose an existing user, and created a new name " vPN.”
 In the next window, we leave a tick and press "Next"
In the next window, we leave a tick and press "Next"
 We leave the default protocols and click "Allow access"
We leave the default protocols and click "Allow access"
 Ready! Press "Close"
Ready! Press "Close"
 Now you have a new network incoming connection.
Now you have a new network incoming connection.
 Connect to the network
Connect to the network
To connect to the created network, open on remote computer "Network Management Center" and click on "Setting up a new connection ..."
 In the next window, select "Connect to Workstation"
In the next window, select "Connect to Workstation"
 Now select "Use My Connection" item.
Now select "Use My Connection" item.
 In the next window, enter the address of the machine on which the VPN is configured (be sure to dedicated IP if the machine is connected via the router, on the router to configure the port of port and specify the IP address with the port "Address: Port")
In the next window, enter the address of the machine on which the VPN is configured (be sure to dedicated IP if the machine is connected via the router, on the router to configure the port of port and specify the IP address with the port "Address: Port")
 Now it remains to enter a login (the one that was created for the VPN connection) and the password, then click "Connect".
Now it remains to enter a login (the one that was created for the VPN connection) and the password, then click "Connect".
After connection, computers will see each other on the net as if they were found in one local network.
There is much more private virtual network settings than just registration and its activation. Our guide will help you extract the maximum benefit from this means Privacy and security.
Everyone should use a private virtual network (VPN) regardless of the Internet connection method: whether it is a computer or smartphone. Perhaps it sounds paranoid, but the real threats really exist, and they become only worse. Malefactors may try to intercept your personal information through Wi-Fi network. And every time you go online, your Internet provider (ISP) has access to everything you send, as well as Congress gave good to sell your anonymous information to advertisers. On the wide Internet spaces, advertisers and spies can track your sites and your location by browsing your IP address. And it sounds frightening.
The fact is that the Internet was not designed to protect your privacy. It was created to facilitate the exchange of information, and not for user anonymity, confidentiality or encrypted communication. Although the HTTPS connection does a lot to protect your information, it does not protect against the attack on Internet providers or on local networksWhat in turn is a serious problem if you have ever used your connection, for example, at the hotel or cafe.
And while the new, more confidential Internet has not appeared (perhaps he will never appear), the use of VPN is the most easy way To be sure that you share personal information as little as possible. Do not doubt: you need a private virtual network.
That VPN may not
As with other security tools, it is important to understand the boundaries of the possibilities of VPN. In the end, you will not hope that the body armor will save you when falling out of the aircraft or that parachute will stop the bullet.
When you turn on the VPN, your traffic is sent through an encrypted tunnel to a server managed by a VPN company. This means that neither your Internet provider nor anyone (or anything) still connected to your router will not see your Internet traffic. Your traffic goes online via a VPN server. If you go to the site that does not use the HTTPS connection, your traffic will no longer encrypted.
And since your traffic comes from the VPN server, your this IP address safely hidden. This is important because IP addresses are distributed geographically and can be used to determine your location. And if someone tries to know your IP address, it will see the IP address of the VPN server. And it can be useful if you want to replace your location. Connecting to the VPN server in London, you can make it look like you are going to the Internet from the UK.
But the fact that VPN cannot provide: make your traffic completely anonymous. For this purpose, you better use such services as Tor. To this excellent anonymization tool, you can easily access the special version Firefox. browser. Instead of transmitting your data through one intermediary (via a VPN server), Tor redirects your information through several different TOR network computers. This makes the process of tracking your activity and your stay on the network much more difficult.
In addition to everything, websites can track your movement through cookies, collecting personal information in the browser, online trackers and other zazny devices. The use of advertising blocker, such as Privacy Badger, helps to suppress these observation pests, and also complicates advertisers tracking your move on the network.
Finally, the presence of a private virtual network does not mean that you can forget about the basic safety rules. Despite the fact that some VPN services say that they can block viruses, we recommend a separate anti-virus software for your computer, as it was designed specifically to protect your computer from malicious programs.
You also better use password manager, because the reusable use of the same password is often the main cause of hacking or infection. Another caution is to use ordinary intuition when opening links or applications in emails. Phishing attacks - attacks when the cracker uses a fictitious website that is copied from the present to fool and make you introduce your personal data - so common that they have become practically commonplace, so be alert.
How to choose VPN.
When you select VPN there are several key points that you should pay attention to. For example, the VPN service must provide you with a connection of five devices at the same time, at a minimum. We also pay attention to whether the VPN service allows you to use BitTorrent traffic on your servers. Some allow, and some are not, so pay attention to it, because you do not want to be disappointed in the company in which you make a fee monthly.
Speaking of payment, the average value of VPN is $ 10.53 per month. If the VPN service charges a monthly fee of this, then this does not mean that they rob you, but they must offer something significant. For example, best interface or a large number of Server locations to sweeten a deal slightly. Usually you are offered a discount if you make up a long-term contract, but we do not advise you to do it until you completely make sure that you are happy with this service.
Before buying a VPN carefully read the service conditions. This document will allocate what information the VPN service keeps and what it does with this information. Many companies argue that they do not lead traffic logs, which is excellent. Others go further and argue that they do not follow the activity of the user at all. And this is important, since VPN has access to all the information you are trying to protect from others. In the best service conditions, all of the above moments are transparently traced, and in the worst on the contrary - everything is foggy, with large quantity Links to the details and the law. If you feel that I am deciphering Petkin to a diploma, if reading one of these documents, be sure that you need to contact another service. TunnelBear, for example, clearly and transparently explains its services in a light and accessible language.
Also, it will not be superfluous to see where the VPN company is located. Remember that this is not always the physical location of the company, but a legal aspect that the company works under whose jurisdiction. For example, NordVPN is located in Panama, and ProtonVPN - in Switzerland. This means that these companies do not apply to the data storage law on which security services can access the information stored on them. Another example, Hide My Ass VPN is located in the UK, where such laws are more cruel.
The most important thing when choosing a VPN is trust. So if the location, the price or condition of service does not inspire you confidence, then try another service.
The best VPN services in 2020:
Paid or free VPN
We recently conducted a survey of 1000 people on the topic using VPN.. According to our results, 62.9% of respondents say they do not want to pay more than $ 5, and 42.1% argue that they want to use free VPN.
Unfortunately, most VPN services are far from gratuitous provision of their services. Or at least less $ 5. But you do not need to rob the bank in order to be protected. After trial use Service For 1-2 months, you can issue a long-term contract, thereby reducing its costs. PRIVATE INTERNET ACCESS VPN - excellent and available servicewhich costs only 6.65 $ a month for the services provided (without excesses).

Most VPN services offer trial periodwhich is usually limited in time. Others like TunnelBear and Anchorfree Hotspot Shield Elite offer completely free versions Your products, but with some restrictions that do not act on paid users. For example, TunnelBear keeps accounting data to his free users. But the free HotSpot Shield version works on advertising. ProtonvPN - the creators of the protected mail Service Protonmail - there is also a limited trial period.
Opera browser has a built-in free VPN and does not charge anything for its use. Also Opera offers excellent VPN applications separately for iOS and Android free, providing you with protection wherever you go.
Start
Once you install the service, the first thing you have to do is download the company's application. Usually there are special boot pages for this on the VPN service website. So forward, download the application and your mobile devices; The more devices protect, the better for you. In most cases, you pay once for subscribing to a certain amount of Licenses (usually five), and then you can use the service on any device for which there is a special application.
We found that when the VPN is released for Mac, the version of applications in Mac App. Store can sometimes differ from versions available on the VPN service website. Apparently, this happens due to restrictions apple companies. By trial and errors, of course, you can find out what version will work with you, but we made it for you in our reviews.
After you installed the application, you will be prompted to enter input information. In most cases, this is the username and password that you specified during registration. Some companies, such as Private Internet Access, assign you a username different from your payment data to ensure greater user privacy.
After you entered, your VPN application connects to the nearest VPN server. This is done to ensure better speed Through VPN, as the delays and a reduction in speed grow as the distance between your actual location and the VPN server location increases. That's all: now your information is directed through a safe tunnel to the VPN server.
Keep in mind that you do not need to install a VPN application. Instead, you can configure network settings of your device to directly connect to the VPN service. If you are concerned about the possible surveillance "under the hood" of the application, then this option is well suited. Most VPN services have instructions for setting up your device.
Select Server
Sometimes you may not want to connect to the server that recommends the VPN application. You may want to fake your location, use BitTorrent via VPN or a desire to take advantage of some configured servers that your VPN company provides you.
Many VPN companies include an interactive map in their applications. For example, in NordVPN you can click on the country to connect to its servers. it available way To understand where your information is sent, and most likely there will be a list of servers from which you can choose.

The selection of the server is completely dependent on what you want to do. For safety and speed you better choose a server near yourself. To access the content, depending on the region, you should select a server in the relevant region. For example, if you want to see BBC, you'd better connect to the tunnel in the UK. Some VPN companies, KEEPSOLID VPN Unlimited And NordVPN, for example, there are special servers for streaming video.
Such special servers are useful because such stream services like NetFlix are blocking VPN. We are talking About licensed content, which is protected by the studios and Netflix itself. For example, Netflix has rights to provide Star Trek: Discovery outside the United States, but being in the US themselves you need to pay for CBS's All Access service.
It would also be nice to check whether your VPN service BitTorrent traffic on all servers or only on special. NORDVPN Also, like many other services, clearly makes it clear that they do not allow the use of torrents. But Torguard, for example, nothing has nothing against it and allows you to use torrents on all servers of the company.
Services such as NORDVPN and PROTONVPN have advanced security settings, such as access to the TOR network or multi-interval VPN. As noted earlier, Tor is a tool to ensure a higher level of privacy. It allows you to access hidden websites on the expanses, the so-called Dark Web. The multi-interval VPN works in a similar way: instead of redirect your traffic through one VPN server, a multi-interval connection will transfer you first to one server, and then to another. Both suggestions work for privacy, but to the detriment of speed.
If you decide to ignore third-party applications and configure network settings manually, then you may have to enter information for each VPN server separately.
Advanced settings
The set of functions in each private virtual network differs from the service to the service, so that we can only summarize and assume that you can see before your eyes when you open the settings panel. But we recommend that you read the documentation and try to dink the buttons. Most the best way Learn to use something - try it in the end.
Most VPN services include the Kill-Switch feature. After switching on, this option prohibits the computer to receive or transmit information via the Internet while the VPN is turned off. This feature is useful when your computer is disconnected from VPN and can transmit (or obtain) information bits for unencrypted compound.

Many services offer the option of selecting a VPN protocol. It looks frightening, since the protocols are strange incomprehensible names, and companies rarely provide information on what will happen if the protocol is changed. In general, this is the thing you can leave alone.
But if it is still interested, then OpenVPN is a protocol that we recommend. He is in open accessSo it looked at a lot of eyes for possible vulnerabilities. IKEV2 is a good, secure replacement if OpenVPN is not available. Keep in mind that on some platforms, like MacOS and iPhone, OpenVPN is not always available due to additional restrictions imposed on the developers.
When it is necessary to use VPN
To provide highest level You must use private security virtual networks So often, as far as possible, and ideally - all the time. But it is ideally, which is not always achievable. At a minimum, you should use VPN if you use a network that do not control, and in particular, if this is a public Wi-Fi network. But most often we recommend users to customize their VPN applications so that they worked as long as possible. You can always disconnect if it starts to deliver inconvenience.
VPN for Android and other mobile devices are a bit more complicated, in particular, when you often enter and leave the access zone mobile network. Every time you lose and cross the connection data, VPN also reconnects, which adds tedious expectation. Also the least probably your mobile traffic It can be intercepted, but we have seen research proving that it is possible. Considering the fact that law enforcement and intelligence bodies have almost unhindered access to telecommunications data, here's a good advice: use the VPN even during use cellular communication. In addition, most mobile devices can be connected automatically to familiar Wi-Fi networks. At a minimum, you must use VPN while connecting via Wi-Fi, because it is elementary just to fake Wi-Fi network.
Many VPN services provide configuration of the parameters of how and under what circumstances they should be reconnened in the case when the connection was broken. We honestly cannot come up with a reason why you would not want your VPN service to try to reconnect, and therefore we all recommend that you make sure that the settings are exhibited correctly.
If you are concerned that VPN brakes your connections or blocks an important traffic, then you need to look at the split tunneling option. And again, we will repeat that different companies give this option to different name, but its essence is that you will allow you to configure applications that will use the VPN connection for your traffic, and applications that will work in normal mode. For example, TunnelBear includes an option not to tunneling apple applicationsSo that they can function on Mac. Streamers and gamers who need VPN will probably become interested in this option.
How to use VPN for streaming via Chromecast or Airplay
Chromecast and AirPlay allow you to broadcast music and video from your computer or mobile device On columns, TVs and other stream devices. But for all of them you need Wi-Fi, which can be problematic if you use VPN.
With VPN enabled, your traffic is moving along an encrypted tunnel, which does not allow devices connected to one Wi-Fi network, detect each other. It should work as much as you do not want someone, just being in the area of \u200b\u200byour network, learned what you do. It is sad to recognize, but it also means that Chromecast and AirPlay will not work until you use VPN.

The easiest solution is to turn off the VPN, but it is not the only one. You can use split tunneling, as noted earlier to direct only the traffic that you want to protect through the VPN. You can also turn on the VPN-Browser plugin, it encrypts only browser traffic and nothing more.
Alternative Solution: You can install a VPN on your router. After that, all devices connected to your router (from your phone to smart juicer) will use encrypted traffic. This is an excellent solution for well-equipped smart homes.
Private virtual networks are not nuclear physics
At first glance, VPN may seem like some kind of security, but many companies are working hard to make them understandable and convenient to use. Most of them now do not represent difficulties. So it should be. And although it is always reluctant to defense against possible threats, VPN is one of the best and easy ways to protect your network traffic from ... and from everything.
 Cellular - what it is on the iPad and what's the difference
Cellular - what it is on the iPad and what's the difference Go to digital television: What to do and how to prepare?
Go to digital television: What to do and how to prepare? Social polls work on the Internet
Social polls work on the Internet Savin recorded a video message to the Tyuments
Savin recorded a video message to the Tyuments Menu of Soviet tables What was the name of Thursday in Soviet canteens
Menu of Soviet tables What was the name of Thursday in Soviet canteens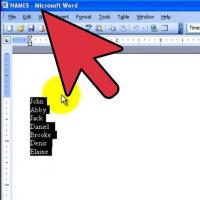 How to make in the "Word" list alphabetically: useful tips
How to make in the "Word" list alphabetically: useful tips How to see classmates who retired from friends?
How to see classmates who retired from friends?