How to connect to Wi-Fi not knowing the password. Why connect to Wi-Fi neighbor is a bad idea. Basic Hacking Wi-Fi Methods
Many people turned out to be in a situation, Wi-Fi and a smartphone or a laptop catches many networks with a good signal, but there is a password on each network. Of course, we can say that connecting to someone else's network against the will owner is ugly. But what if connecting to the Internet is a matter of life and death? For such cases, there are several working options to circumvent protection:
- brutfors;
- change MAC address;
- programs for hacking;
- android application;
- interception of traffic.
Brutfors is a banal selection of all possible combinations of characters from which a password can consist. This is perhaps the easiest way that can only come up with, since it does not need special knowledge or complex software. But, on the other hand, the complexity of the method is that it is quite a mutually and the process can take a lot of time if the owner has established a rather complicated password.


Automatic selection of combinations
It is not necessary to carry out this operation manually. There are quite a lot of programs that automatically sequentially select combinations. It is much faster and easier for the user. But it is worth it in mind that the search for a suitable combination may take enough for a long timeEven if you use special software. A simple password like QWERTYUI can be hacked in less than a minute, but on the decoding / # 7 & //. 'Will take a lot of time.

WiFi Crack
One of the programs for automatic selection of passwords is WiFi Crack. It is very easy to use it.
- Download the program from any site that distributes such a software.
- Run the file and see a simple interface.

- At the top in the "Refresh" string, select the network that you want to hack and activate the program by pressing the "Scan for Access Points" button.

- Waiting for the completion of the scanning process of networks, click on the active button, in our case "Wi-Fi WPA", with the list of networks found.

- In the Select Target Access Point section, click on the desired network.

- At the bottom of the window, click on the "Browse" button to select the file with the vocabulary of possible passwords.


The note! Most likely, the program will need to connect a dictionary to which it will use to select passwords. Usually, dictionaries are included with the program.
- Configuring the parameters, press the "Wi-Fi Attack" button and wait for the completion of the process.

- The final result of the program will be an inscription with a password under the "finished" line at the bottom of the window.

- We return to the program interface and click on the Key Database button.

- In the open window, you will see connected information, including Wi-Fi password.

The note! On average, the password hacking the program occurs in 30-90 minutes. Since users rarely install really complex passwords, most can be hacked for half an hour. But there are such passwords, on the hacking of which it can take not one year. So not every network gets to hack.
Change MAC address
Not always, passwords are used as protection for Wi-Fi. Frequently, users use a filter by MAC addresses. From the device, this network will be detected as an open and not requiring password. But the connection to it will not work, since our MAC address does not pass filtering. So, the only output is to change the MAC address of the device to suitable. But how to do that?
If you have completed these three steps, connecting to your network without a password becomes impossible. More precisely, you can connect it, but it will take so much time and energy that any hacker will quickly understand that the game is not worth the candle.
There are quite a lot of ways to hack someone else's Wi-Fi. But all of them are focused on users who did not take care of the security of the connection.
Video - How to hack Wi-Fi Password of the neighbor in 5 minutes
This instruction is intended to familiarize the owners of wireless networks with effective techniques Hacking Wi-Fi to ensure the protection and safety of the personal home network. It is not recommended to apply the instructions below to use the Wi-Fi strangers, although they allow it to do "incognito".
That is, the real IP of the hacker to identify ordinary users of Wi-Fi-networks is not possible, and therefore the identity of the hacker remains unknown. Real Ai-Pi "Halavier" can only find out a person who has a legislative power using which it can access information from the provider). Thus, use or not the following manual: "How to hack WiFi?", - For mercenary purposes, lies entirely to the conscience of the user itself.
Basic Hacking Wi-Fi Methods
Development in the field of protection information networks Promoted by "seven-world steps", but hacking technology is always a couple of steps ahead of them.
Given the widespread distribution of wireless networks, today the question is especially relevant among portable PC owners and mobile gadgets: "How to hack someone else's Wai Fi?" Fortunately, the methodology for its solution is many, so each person has the opportunity to choose the most preferred.
There will be minimal efforts to master them and then with the person of such a user will not be a dishonal smile, because he is always (where there is Wi-Fi) can stay for free in touch and download from the Internet to free everything that he wants.
Particular students are especially interested in such skills. After all, saved money, it is more expedient to please the growing organism with a couple of milk cocktails than to give a scholarship for the service provider.
If a person has a computer with a wifi module, then free access to the network can be provided without spending a lot of time.
The easiest way to connect is the detection of an unprotected network:
- Through the "Control Panel" enter the tab "Network and Internet";
- Go to "Network Connection Center";
- Next, open the "Connection to Network" tab;
- A list of networks will appear, from which you should choose not password protected and connect to it.
If there are difficulties with the discovery of an unparalleled network, it is recommended to install the FREE ZONE program. It will make the connection itself. In addition, the utility is automatically able to quickly find and connect to unprotected Wi-Fayam, it contains a rather big base with saved passwords to wireless networkswho regularly replenish the users of the application. Thus, the more people use it, the more likely to connect with one of the wireless networks within the radius of the cracker.
If such a simple method turned out to be powerless, then you can use the selection method.
 Often, the owners of routers put simple to memorize access codes, for example, consisting of seven-eight identical numbers or characters, or simply introduce "12345678" or "QWERTY", for example, most popular WiFi passwords in Russia and the world. Obviously, such passwords can be easily chosen even manually, and specials. Applications cope with them in a matter of minutes.
Often, the owners of routers put simple to memorize access codes, for example, consisting of seven-eight identical numbers or characters, or simply introduce "12345678" or "QWERTY", for example, most popular WiFi passwords in Russia and the world. Obviously, such passwords can be easily chosen even manually, and specials. Applications cope with them in a matter of minutes.
Also, many users loved the method - "phishing". The method is based on the manipulation of a hacker, forcing the owner of the WiFay network to give the name and password.
Hackers are widely used by the "Interception" method, which is sent to connect to a connection with a router from a smartphone or a laptop. The router with a mobile gadget hacker exchanges data (Handichek process), which contain an encrypted password.
Special applications or services are used to decrypt the received code.
Brutfors-programs for automatic password selection
Brute Force. - this is the technology of selection of access codes by the program in automatic mode.
Experienced users write such applications themselves. They targeted the target network, mailer, resource, etc. Also, many hackers apply ready-made utilities. For example, "Proxy Grabber" automatically outputs information about connecting to servers.
The hacker receives a file with all data, which is then applied in the Brutfors application. A library with combinations of names and passwords is embedded in the application (libraries are common in hacker forums and are constantly complemented). The utility in automatic mode changes proxy, so the Web server cannot identify the attack, which means the hacker.
Brute Force analyzes about one or two hundred threads. The higher this number, the faster it will be taken by hacking Wi Fi. However, the amount is limited to PC. At low-power computers, you have to run at the same time no more than 100 combinations checks, respectively, with such values, the procedure can delay for a long time (sometimes it takes several days).

The most popular applications for Bruta:
- Appnimi Password Unlocker.
I break up the password using a PIN device code
To solve the password to Wi-Fi network protected WPA / WPA2, you will need:
- PC with Wi-Fi-adapter (almost all laptops and netbooks already have built-in modules);
- YUSB flash drive is not less than 2 GB;
- Utility "" under Windows.
Basic operations are recommended to be performed in the Linux environment, although it is available to perform a planned one through Windows, but everything is fulfilled in Linux much easier. It is necessary to format the USB flash drive and save the WiFi Slax package on it.
Wi-Fi-Slot starts directly from the outer medium, it is enough to deploy the contents of the Boot directory and clasp by "Wifislax Boot Installer". Next, specify the parameter S and click "Enter". Then run the PC from the created flash drive and execute the following sequential steps:
- Specify the download with the SMP and Wifislax C KDE with adjustments;
- Wait;
- After the download is complete, it is recommended to change the mass laptop by following in the "IFCONFIG WLAN0 DOWN" console;
- Now open the Macchanger application;
- Clazzo "Change Mas";
- Exit the utility and in the console to execute "IFCONFIG WLAN0 UP;
- Open the MINIDWEP-GTK utility;
- Clasp "scan";
- Wait;
- If the found points are with the support of WPS technology, they are easier to hack and faster.
- Newcomers hackers, it is recommended to crack points with active WPS and only after purchasing experience to move towards complex tasks. Highlighting the point to clap "reader";
- Click OK;
- Wait;
- The utility will show a password;
- If the attack was unsuccessful due to the blocking of WPS, then in the package recorded on the USB carrier there are means for bypass;
- If the points with the WPS is not detected, it is very easy to solve the password when at least one PC or a mobile gadget is already connected to the network. Waiting when someone (sacrifice) is connected to Wi Fay. It should be chosen and clap "Attack";
- The wireless module embedded in the laptop will generate interference and will turn off the "victim" from Wi-Faya;
- Of course, the victim will predict to fulfill the attempt to connect again, and at the same time will happen "Handichek" to the victim with a router with a data exchange, which are easily intercepted. Captured information is stored as files;
- Next, you should write down the files in the memory of the laptop and restart;
- Launch windows in the laptop;
- In the copied files there is an encrypted access code for Wi Fai. To see it, you will need to install the utility "ElcomSoft Wireless Security Auditor";
- Clause Data Import - TCPDUMP;
- After that, by one finger to clas down "Ctrl" and not releasing it click on the button with the English letter "I";
- Specify copied files;
- Clasp "run ...";
- Wait;
- Ready.
Note: WPS is a vulnerability of encryption technology. The connection is carried out using the PIN code. For example, IDUs may contain eight characters, that is, overdid by about one hundred million PIN variants, the hacking of the wifi network will be successfully completed. The lack of technology is that it is allowed to divide PIN into a pair of parts. As a result, it is required to analyze parts with a maximum of four characters, and this is several orders of magnitude reduces the number of options (up to 10 thousand).

We use phishing
Many users loved the method - "phishing". The method is based on the manipulation of a hacker, forcing the owner of the WiFay network to give the name and password.
Basically, the "hook" is thrown through the message e-mail or social network, but in the case of Wi-Fatch "Sacrifice" will begin to suspect a nonlade. Therefore, the hacker builds a trick in different, for example, organizes a duplicate network with identical name (the name of the Wai-Faya victim and the created hacker coincide). As a result, while connecting the unlucky user with fake Wi-Fi, it indicates the password. The owner of the lime network without difficulty reads the entered access code and turns off it. Next, in the usual mode, it is connected to Wi-Fay, because the password is already known to him.
The technique is easy for implementation, however, hackers are distinguished by lazyness and even more facilitated hacking, developing special application "WiFiphisher."
You must perform the following steps:
- Put the program "WiFayfisher" in the PC (it is freely available on the Internet);
- To disable users from Wi-Faya;
- Wait until the program translates the victim router to the access point mode and will make a net sheet with the same name;
- Next, the utility to implement some additional auto-tunches;
- Then the application will bring to the PC or the Device of the victim a lime window, which will ask for updating the software;
- The victim to update the password will indicate;
- Since the owner of the lime menu is a hacker, the password entered by the victim will appear on the monitor of its PC;
- It is done.
 Created a lot convenient programs, with extensive login databases and passwords of Wi-Fi-networks around the world. These utilities collect Wi-Fi access codes entered users and constantly update them.
Created a lot convenient programs, with extensive login databases and passwords of Wi-Fi-networks around the world. These utilities collect Wi-Fi access codes entered users and constantly update them.
The utilities are simple and equipped with an intuitive menu. Often, only the user is required to activate Wi-Fi search and select the available network.
The following programs are most popular:
Not very popular, but no less effective, the Wi-Fi Map and SWIFT WiFi programs include. They clearly show the user of the Wi-Fi point on the map and automatically connect to the nearest point.
Some users entrust high hopes for ensuring the safety of their network filtering by the MAC address, however, in practice, even a beginner hacker, bypassing such protection faster than the owner of the router is included in the instrument's web configurator with administrator rights.
The procedure for changing the Wireless adapter in Linux takes only a few seconds, for example, the IFConfig Wlan0 Down command. Also, the Macchanger utility allows you to assign random mas in automatic mode, as a result, even the technically advanced network owner will be confused. And if the victim uses the white list, the application "Airodump-ng" helps to determine the loyal address. The utility displays the allowed MAC in the "Station" column.

Note: You can also identify the Valid Mas with Brutfors, which has already been told at the beginning of this article.
Select the MDK3 application and the Brutfors model. The main advantage of the utility is the possibility of detecting mas even in the absence of connected wireless router devices. For example, you can apply the command: MDK3 WLAN0 F -T 20: 25: 64: 16: 58: 8c -m 00:12:34.
We protect your WiFi network from hacking
The more protection steps you pride, the longer it will be more difficult to break the hacking of your network, and the newcomer hacker may even refuse the venture at all. Therefore, it is recommended to use all the following recommendations, without missing any.
We put a password to enter the web configurator of the router
- In the router web interface, open the System Tools tab.
- Next, enter the subsection "Password" and set a reliable access code. Be sure to set to "save" at shutdown.
- Install the access code to the wifi network.
- Enter the Wireless tab and then go to Wireless Security subsection. Set the type of encryption "WPA / WPA2" and showing the fantasy to set a difficult password.
- Save the entered parameters and restart the router.
- Hide the name of Wi-Faya
- Open the "Wireless" tab. Remove the mark from the "Enable Ssid Broadcast" graph.
- Clazzo "Save".
Determine the mass devices that will be allowed to connect to Wi-Fame (for example, see the smartphone address in the "phone" settings section). Next, open the "Wireless Mac Filtering" subsection in the Wireless tab. 
- Clazzo "Enable" and activate the "ALLOW THE STATIONS SPECIFIED by A Enabled Entries in the List to Access".
- Next, Clazzo "Add New ...".
- Specify wt with permitted status.
- Click "Save".
- Turn off QSS (WPS).
- Open the WPS bookmark (in some router models interfaces, it is called "QSS"). Clazzo "Disable WPS".
- Restart the router.
 The easiest way is to install the FREE KALI Linux application from the application store on a smartphone or tablet and run it.
The easiest way is to install the FREE KALI Linux application from the application store on a smartphone or tablet and run it.
The use of the program does not cause problems, since most processes are automated in it. In case of the impossibility of installing the above utility, it is recommended to find and install "Linux Deploy" in the market, the menu of which is also not distinguished by difficulties.
Despite the ease of installation of these funds, they are the advanced tools of the hacker, with which even a hacker-newcomer will understand.
Advanced users often use "WIFINSPECT" for hacking. It allows you to bring detailed information On the mode of operation of the detected networks. The program also extends freely, but it requires root to work for some of its functions.
If there is a root authority, you can use a powerful WiFi Analyzer tool. It successfully copes not only with Wi-Fi networks at a frequency of 2.4 GHz, but also 5 GHz.
The owners of the phones from "EPL" successfully crack the neighbor's Wi-Fi installing "Airslax" or "AirCrack-NG".
What is dangerous to use the neighbor WiFi?
Some open neighboring networks that are not encrypted and have no interception protection, dangerous for use.
Since each attacker connected to such Wi-Fay is able to intercept and scan the traffic of any customers.
If the network is encrypted and protected, the danger decreases, but such a wi-fi to use, it will have to hack, and this is punishable by articles 272 and 273 UG of the Russian Federation.
Obviously, to punish a hacker, it will be necessary to find it, for example, to reveal his IP. It should be noted that for this sacrifice it will be necessary to make a corresponding request to the provider. Communication companies providing communication services to access the Internet may issue information only by IMB employees or people from state buildings with even greater power. It is not possible to obtain data from ordinary faces.
After identifying the personality of the hacker, he will be brought to justice under Art. 272 ("Unauthorized access to computer information") only with the proven fact of deletion, encryption, changes or copying the victim data.
Punishment for hacking networks
The penalty of 273-her will follow in the case of writing applications that are intended to erase (encrypt-block, change, copy) information either when using and distributing such utilities.
If the exit to the global network, the hacker used a long time and the victim suffered the damage more than 250000 rubles. When paying the traffic cracker, the attacker will be punished by Art. 165 (causing property damage to the owner ...).
A lot of utilities have been developed for hacking Wi-Fi-networks. The use of some of them will seem too simple, but it does not reduce their effectiveness. Applications are issued for all existing platforms, then consider the most popular of them.
Under Windows.
For the most popular platform in the world, released the greatest number Applications crackers.
WiFiCrack - It works almost entirely automatically. The selection technique is used.
Steps:
- Run "wiFicrack.exe";
- Mark network;
- Click "Next";
- Activate the database with passwords and clap "Start";
- Wait;
- Now the application directory contains the "good.txt" file, which displays the password and login.
Kali Linux — Steps:
- Install Kali Linux in virtual Machine Vmware;
- Run the program and select "Live";
- Wait;
- Enter "iwconfig";
- The displayed name of the interface is written on a sheet of paper;
- Run "Airmon-NG START WLAN0";
- Then "AirODUMP-NG MON0";
- Click "Ctrl + C";
- Enter "Wash -i Mon0 -C";
- Specify Wi-Fi with WPS;
- Enter "REAVER -I MON0 -B (name that previously wrote on a piece of paper) -A -VV";
- Wait;
- A login and code will appear on the monitor.
Under Android
It is not entirely convenient to use for hacking a laptop. Significantly more accurate use of a compact android gadget.
WPS Connect. — Steps:
- By installing running the program and tap on the collapsed red icon on the screenshot below;
- Tap on the victim's network;
- Tap "Show password", the access code will appear.
WIFI WPS WPA TESTER — Steps:
- Tap "update";
- The list of networks will appear (next to which the green lock is depicted, you can hack);
- Connect with the selected Wi-FAT;
- The display will appear on the display.
 Wifikill. - If there are too many devices connected to wi-fi and exhausted limit for the connection, then this application will help free the vacant place. Steps:
Wifikill. - If there are too many devices connected to wi-fi and exhausted limit for the connection, then this application will help free the vacant place. Steps:
- Tap "update";
- Clasp "GRANT";
- Wait;
- There will be a list of clients connected to Wi-FAT;
- To highlight the client and tap "GRAB";
- Next, Koll's Kill;
- Now you can safely work on the network.
Under the iPhone.
Device owners from "EPL" are often used by Aircrack-NG, intercepting information and quickly hacking codes.
The owners of the iPhones often use "IWep Lite", which you just need to enable and then specify your wi-fi. The utility will analyze in automatic mode and will show the access code.
Today, almost every second uses the Internet. It can be like home networkAnd unprotected or protected wireless. Often users are interested in a completely legitarious question about how to connect to WiFi, not knowing the password? Many can say with confidence that it is impossible, but the thing is that everything is not so simple. In fact, there is nothing impossible, so we will tell you how to do it.
A bit of general information
As practice shows, not everyone sets the password to its Internet. In this case, you do not need to invent anything, and you can freely use it, not experiencing that they will learn about it and turn the connection. Please note that, for example, in large companies almost never put protection, it is clear why, it is not very convenient, and the time is engaged in entering data. But we have another situation: an evil neighbor put a password, and we want to go online. First of all, make sure whether the password is worth it. To do this, it is enough to enter any combination if the connection is interrupted, then we will need a sniffer. Just about this we will talk.
How to connect to wifi, not knowing password

To do this, you need to download a special software. As noted above, we will use a sniffer - a program, the main purpose of which is to catch information packages. Today in free access on the Internet there is a whole bunch of similar utilities, for example, Shark. To deal with this software will not be difficult. When you follow the first launch, you will understand that you can intercept enough useful information. Here you can find the IP address of the recipient of the data and, in fact, the sender. Based on this, you can configure your computer to a successful connection. In principle, in the near future we will work with IP addresses. But this is not as easy as it may seem at first glance. Firstly, wireless Internetwhich we gathered to hack, should work. Secondly, it will be good if it is actively used, it is due to the fact that at this time it is simply transmitted a huge amount of information packages, and we just need it.
WiFi Router: Password is not a problem

So let's try to change the network address of our computer. This is done in order to make it "native" for the router. There is a lot depends on what operating system you use. Although the principle is the same. It is that the network address of the computer or laptop is exactly the same as the router. However, the last digit needs to be left unchanged, because we are talking about the unique address of the network. The subnet mask can not be changed and left for the same. As a visual example, we give the following information. With the help of a sniffer, you received the following address 192.168.5.2, in addition to this you have and subnet mask 255.255. 255.0. You make your address exactly the same, but the last figure remains unchanged, and the mask leave the same, although it usually coincides. In principle, we have already practically managed to connect to WiFi. Without a password it is impossible to do it, so it must be hacked.
Final Protection Stage

So, with addresses figured out. As you could see, there is nothing difficult. We still have to do quite a bit, and then you can join. First, it is necessary to find a decent password cracker. Since connecting to WiFi, not knowing the password and not hacking it, it is unlikely to come out. There are a lot of such programs. Most of them are aimed specifically to open the wireless Internet protection, and passwords accounts in games, social networks etc. But it is better for us to use such a software as COMM VIEV for Wi-Fi. The utility is completely free and extremely easy to use. Intuitive understandable interface It will help you quickly figure out. But the thing is that all the necessary data we already have. This is the network address and information package of the router. Next for you will do everything. For password WiFi. Invent different combinations of letters and numbers come up, but the degree of protection depends on the selected encryption method.
Conclusion
As already noted above, much depends on the degree of protection, that is, the selected encryption variant. There are three of them three. If something like WPA or WPA-2 is used, then you are unlikely to do something, at least because you can not see the network, even if you know exactly what it is. In this case, you will not help dancing with a tambourine, here you need to participate a professional hacker, and such services are decent, therefore it makes sense to think about the feasibility of such an activity. If we are not talking about intensive devouring traffic, it is likely that it is easier to ask the owner's password. The probability is that no problems will arise, especially if you need access to work or studies, rather than downloading films by 20 gigabytes per day. Well, that's all that can be said about how to connect to WiFi, not knowing the password. There is nothing complicated here, but sometimes it does not make sense, and modern routers are protected rather reliably, therefore they are very difficult to "open". But if you really need, you can try.
Free Wi-Fi is a pleasant find for everyone. Hidden Wi-Fi network In stores, cafes and other public places sometimes do not give rest. Some people want to hack the password from Wi-Fi.
Rarely meet a kind person who will not limit access to his own Internet. Clear, cafes and hotels attract visitors to free distribution of traffic. However, Wi-Fi is found with open access not only in such places, and the neighbor is at the entrance. Whether this is too kind person, whether he is very forgetful by nature.
What to do if the Internet urgently needs, but there is no money to pay your own? What tricks came up with wise hackers? For free use The nearest Wai-fi will have a serious hacking procedure. Other paths that could help bypass authorization are not yet known to the public.
Hacking methods
What is only in global Network Do not find, even descriptions of fraudulent actions for extraction free Wi-Fi. If knowledge in the field of Internet technologies is not significant, it is better to ask to help a familiar hacker. Who can cope on their own, here are some popular ways:
- guess password;
- use a special program so that it picks up the "key";
- to receive a PIN device;
- "Phishing";
- catch up password.
How to guess the password
In each method, it is originally worth choosing Wi-Fi with best level Signal. By choosing the first method, you will have to reflect a little. It is unlikely that the neighboring wi-fi is seriously encrypted. If he is far from information technology, an ordinary inexperienced user, it is unlikely that he has long thought over the complexity of the combination. Most likely, he used his date of birth, spouse or child, and maybe at all.
When the very simple options Personal information did not pass, it is worth paying attention to other popular "Passvorda". Most often, users use the following combinations of numbers - "1234", "1111", "123123" and similar to them, also passwords from the letters - "QWERTY", "Password" and others. Of common combinations to protect Wi-Fi, there are many, on the network on this topic is full of information, and specific combinations are presented.
Plus, the method is significant - simplicity, but minuses are also present - the duration of the process. Especially much time will spend a restriction on input attempts. If there is such a thing on someone else's Wi-Fi, then after three unsuccessful attempts, the password will have to be administered only every other day.
Password solve software
How to hack a difficult password from Wi-Fi? The principle of such programs is simple, they act by analogy with a person. Only a computer at times faster and intelligent. Programs have whole dictionaries with popular combinations. Sometimes the car picks up passwords in minutes, it happens, the process is delayed for several days. First, the simple versions are followed, then complex. Recognition time depends on the degree of password complexity. This technology They also call "Brutfors", which means searching for a password.
To familiarize examples of programs - Aircrack-NG, Wi-Fi Sidejacking, Wi-Fi Unlocker Airslax and others. On the Internet there are many of them, it is only a small part. Downloading such software, a fraudster himself risks to be deceived. Troyans and other troubles will be placed on a computer.
The idea to connect the technique to search for a password genial. True, this method also has its own minuses. The main one is a negative outcome. The selection may pass to no avail. This means that too complex combination of characters, letters and numbers, which is not yet familiar to this program, is conceived.
Where to get a PIN foreign device
Finding PIN is an easy task. What is worth going to visit and rewrite it from the case of the device for wi-Fi distributions. PIN fully consists of numbers. Not always the device will be located in a convenient place, but in case there is a failure there is a way out.
Another method to get PIN - take advantage of special programs. You can use, for example - CommView or Blacktrack. Such an option of hacking of perekalny Wi-Fi is not easy. The Wi-Fi device is constantly exchanged by the information packages between other devices, which are included in the area of \u200b\u200bits action. The goal is to intercept the data.
It is necessary to act through a computer or a laptop with a powerful hardware, having a Wi-Fi map with the MONITOR MODE function. Create boot disk or a flash drive with a software distribution kit to intercept the package, install the shell on the PC. Select a network, and after waiting for the interception process of about 10,000 packages. First, the program will give PIN, and after and password.
Video material for hacking network using third-party:
Tip: Remember PIN. When the owner changes the password, it will be much easier to solve it, knowing PIN.
Change MAC address
How else to paw wai-fi? In the presented method, the question in principle is inappropriate, sometimes users leave the network open, but put a filter by MAC addresses. This is a special identifier for each device. Learn the allowed MAC addresses can be applied by a special program. For example, Airdump-NG.
Video:
Upon learning of the white list of "Identifiers", change your own. For what you want to open the "Control Panel", click "Network Management Center and Shared Access", after selecting "Change parameters network adapter" Choose need network connection, go to "Properties". Network setting - Enter the MAC address of 12 characters. Further, restart, and "voila", everything turned out.
Phishing
Phishing is one of the methods of network fraud. It allows you to deceive the login and password. So, by visiting the site, you can visit the phishing page and enter your data that the cracker will post.
Information with secret data on Wi-Fi will be recognized using WiFiphisher.
What scheme works on:
- Configure HTTP and HTTPS;
- Search for wireless networks WLAN0 and WLAN1 until it is connected to one of them;
- Tracking the DHCP service and output IP addresses;
- Select one of the available Wi-Fi points;
- A copy of the access point is created, it is defined by the same name. The speed of the real point is reduced, so that the user starts to reconnect and falls on the copy.
- The browser requests the password entry, the user fills the count and the Passvord gets into his hands a fraudster through WiFiphisher.
Video instruction:
Now the scammer has the opportunity to set up a foreign router. It can change WPS PIN, view data for authorization on any resources. With such privileges, it is possible to send banking services to other sites, having fallen "your".
Tip: In order not to get caught on the "phishing" trick, you need to always thoroughly recheck visited sites.
Protection of own network
As it turned out, there are a lot of espionage options for the data from Wi-Fi. Everyone who has at home or in the office router should complicate the access of third parties. Otherwise, each risk is cruelly deceived. It is recommended to take advantage of the following tips:
- Come up with a complex combination for a password - at least 10-12 characters, where to take into account the keyboard layout, register, signs and numbers.
- Disable WPS, this feature remembers authorized users and connects them again in automatic mode.
- Periodic change of PIN used device, as well as the removal of the factory inscription from the case.
- Limit access to PIN information, do not enter it on dubious sites.

These steps will help to qualitatively protect their network. Now it can break it only a hacker with a capital letter. Be sure if the hacking was successful, he is somewhere near. Only the close arrangement of an attacker can lead it to a prosperous outcome.
Applications with famous data of millions Wi-Fi
Or maybe to hack protected Wi-Fi? Users all over the world have created a kind of database with passwords and Wi-Fi points. To access it it is worth downloading the ready program and select the desired network. Information is obtained in the following applications:

- Wi-Fi Map - universal app For any phone platform, it will show the coming Wi-Fi point and passwords, if someone has previously connected to the selected network;
- SHIFT WIFI - Popular Users Application android systemsAlso, as well as the previous program shows all previously saved passwords to Wi-Fi.
Wi-Fi Map Application Overview:
The list of such applications is gradually replenished. There is a risk to get a low-quality product. Always safer to download software from official and proven sources.
Hacking wi-fi with phone
Today, it is possible to carry out a network of Wi-Fi to a mobile gadget. It is even more convenient than with PC. The phone is easier to bring closer to the device you want to hack. There is a lot of paid and free applications. Some of them - deception. Paid among themselves may differ in the actualization of the bases.

To date, known:
- Wi-Fi Prank;
- Wihask Mobile;
- IWep Lite.
Wi-Fi Prank - Brutfors app. It requires an additional database download. Next it automatically picks up password. Suitable for Android.
Wihask Mobile - valid on a specific algorithm, does not require additional bases. Works until the latent password is detected. Based on the same technology "Brutfors". Distributed for the Android system.
IWep Lite - Search Password on iPhone gadgets. The application requires an activation procedure. It is necessary to find a network and choose statistics. After begins automatic search To a satisfactory response with the code.
Responsibility for hacking
Not in vain say that free cheese Only in a mousetrap. These words can be attributed to the Internet. Free use is legally only in public places, where the thought does not occur - is it possible to hack the available Wi-Fi, as he is in open access. Here everyone can use the network plenty.
A business is a hacking of someone else's apparatus. In other words, this is a fraud. And such actions are not legal. All criminal violations in our country are limited to laws. At all the "cleverings" there is an article in the Criminal Code of the Russian Federation. Do not risk, plug or pay your own Internet.
Wi-Fi is a wireless network that provides transmission and receiving information between clients, as well as access points. Communication between several points and at least one client is ensured. Using the Wi-Fi connection, a person can go to the Internet, as well as share information. It is now difficult to submit modern life Without Internet use. It is used at home, studying and at work for their own purposes. With it, you can communicate in real time with friends who are on the other end of the planet. Here you can learn almost any information. A long time ago, the Internet was a true satellite of a person's life, without which it cannot be called comfortable and modern. From year to year wi-Fi technology Gets more and more distribution.
To enter the network, mobile device Or laptop must be configured. Wi-Fi adapters should work.
So we figured out what Wi-Fi is, now let's talk about how to connect to wiFi neighbor And when it is necessary to do.
The reasons:
- sharing one access point;
- you have problems with the Internet on the side of the provider - there are planned technical works;
- ended the paid period and you forgot or did not have time to pay the Internet;
- You are in relatives or friends who have no Internet;
- why do I pay for the Internet, if there is free access.
Connection methods:
- connect to a deposit WiFi with an unprotected access point (without password);
- agree on the sharing of the Internet with payment 50/50;
- you can find out the password from someone else or once to ask to connect to the other, and then use constantly.
Connect to unprotected networks
The easiest way is to connect to unprotected networks. Fortunately, not all users set the password to their network and this can be used. First you need to enable a laptop or other device and wait for it to fully download.
If necessary, the WiFi module and the operating system will independently determine all available networks.

Most often, the system detects a device that distributes wi-fi, but you can connect to each network. Below, on the right side there is an icon in the form of vertical strips. After clicking on it, a list of possible connections to wireless networks will open. It needs to choose that network that is not protected.

You can learn according to the appropriate icons, for example, it can be yellow warning icons, as in pictures above or other designations. The protected network may vice versa denoted by the lock. At least you can go to the name of the network and see the security type, which should have the status "not protected". It is to this network that can be connected. If the network is protected by password, then enter, not knowing it, it will not work. Here it will be necessary to enter the security key to access.

Found the available network, now you need to click on the "Connection" button. We read a warning that states that "information through this network can be visible to other users."

I went to the connection process.

We look at the WiFi icon if the icon appears that there is an internet connection, then you can safely surf.
After that, you can open the browser and dial any address.
How else can you connect to neighbor Wi-Fi?
A neighbor can ask the network to use the network. For this, of course, you need to be not just neighbors. You can also offer monetary compensation. Consider a second option that is more acceptable.
This miracle happened, and the neighbor turned out to be quite pleasant and not a greedy man, providing a password from his Wi-Fi network. This will solve all the problems and relieve the need to make unlawful actions. The connection procedure is quite simple and does not take much time.
Connection occurs in a similar way, which is described above. The only difference is that you already know the name of the network and received a password.
Briefly the process of connecting to a WiFi neighbor will be as follows:
- Turn on Wi-Fi;
- Click on the icon in the lower right corner of the "Available Network" screen;
- In the spool window, choose a network of neighbor;
- Press "Connection";
- A password is prescribed, which so kindly provided a neighbor.
This will already be a standard connection. As a rule, the connection occurs after entering the password.
Depending on the manufacturer of the laptop, it must be installed in the OS necessary program (Driver), which helps find and connect to the access point. Samoa frame problem During connecting to WiFi Networks From the computer it turns out an inactive module (in this case it is not possible to detect the network, as well as the presence of devices that allow it to be).
In such a situation, it is necessary to see if the module is activated on the laptop.
To do this, you need to find on the right side of the screen. wiFi iconIf the cross is worth it, then it is turned off.

Enable the module in different ways:
- Combination of the Fn + F2, FN + F3, FN-F10 keys and so on (depends on the laptop model).
- Enable via "Device Manager".
If you do not manage to connect using the key combination, then this can be corrected as follows:

Right-click on the "My Computer" icon and select "Management".

Go to "Device Manager" and open "Network Adapters".

On the Wi-Fi adapter you need to click on the right button and choose "Enable".
Usually, the neighbor network is connected to save money, paying for the Internet in half, or to not pay at all, using them absolutely free.
Is it worth it to connect to unprotected Wi-Fi networks?
Networks that are unprotected by password are always pleased with the human eye. Many laugh at the owner of such a network, which just distributes the Internet to everyone in the district. But it is worth connecting to networks to which everyone has access.
In the event that the network is not password protected, but the encryption of transmitted data is used, it is undoubtedly plus. Even if user data is intercepted, they will be decrypt enough. Therefore, the first criterion is the presence of encryption of those data that are transmitted.
In the event that people are connected to unprotected network passwords, especially if they do not have encryption, then the network needs to minimize all actions related to authorization. Such networks are best suited for simple surfing on news sites or to search for other information, where the user does not need to introduce their personal data. It is even better to use the browser in incognito mode or use not the main web browser. The ideal solution to the problem will be using special programs. Such utilities are designed to encrypt all data that are transmitted by users.
Of course, the fact of which network and where the connection occurs is of great importance. If this is the main access point of any organization, then, most likely, there are ways to encrypt these customer data. But those networks that are in incomprehensible place and have an incomprehensible name, it is best to go around the party.
What can the connection be given to?
Connecting to such a network that has no encryption, a rather risky step. All transmitted data may be in the hands of intruders. Passwords and other information will be intercepted and used for various purposes. Therefore, it is better to think a hundred times before risking.
 Lighting devices based on alternating current LEDs find their niche and may come out beyond its limits.
Lighting devices based on alternating current LEDs find their niche and may come out beyond its limits. Requirements and rates for cable laying in Earth Scope of application, Definitions
Requirements and rates for cable laying in Earth Scope of application, Definitions Automobile stroboscope from laser pointer
Automobile stroboscope from laser pointer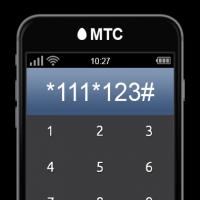 Order 20 UAH to the account. How to Borrow on MTS. Additional information on the service
Order 20 UAH to the account. How to Borrow on MTS. Additional information on the service How to check the account replenishment
How to check the account replenishment How to get a loan on tele2?
How to get a loan on tele2? Responsiveness SSD on a miniature board What SSD Drive Buy
Responsiveness SSD on a miniature board What SSD Drive Buy