Protection against telephone flood. Flood or how to beat off from the phone number attack protection against floods on the phone
Offers effective protection from telephone flood!
- Have you ordered competitors?
- You are called hidden numbers, but when you take the phone right away?
- Many calls and customers can not get through to you?
- Do you lose customers and because of what is reduced profit?
Then you need to us!
What is "telephone dos" or "telephone flood"?
There are hundreds of calls on the phone. You can call and reset or lose the specified entry when you raise the phone, and so dozens, hundreds and thousands of times. The result (and purpose) of such an attack is interruptions or a complete refusal to receive incoming calls. Such an attack is able to destroy not only nervous cells, but also a business.
We work around the world with mobile, stationary, multichannel phones, as well as with TalkFree prefixes (8-800, 8-804)
How to deal with telephone flood?- This is the first question that people fall under his impact.
Unfortunately, it is not necessary to do with standard methods of fencing yourself from unwanted calls. * For this reason, there is our project with which you can protect against DOS attacks on the phone. We will help you get rid of the phone flood as quickly as possible, in fact immediately after contacting us.
*
How does the counter-telephone flud service work?
*
All calls entering your number take filtering on our IP PBX servers in manual and automatic modes, unwanted connections are read in real time, as a result of which only those calls are received on your phone as in normal mode.
We will provide you with remote access through your personal account to statistical information about calls.
For our service are characteristic:
- Countering attacks with power up to a thousand threads on the number.
- high level of protection.
- round-the-clock support.
- Constantly updated base of numbers involved in attacks.
We present to your attention our service for the sale of rooms 8-800 ... !!!
The number with a code 8-800 is a telephone number that can be made free from any stationary or mobile phone from anywhere in Russia. The numbers are an integral part of any successful business built at work with customers: partners or buyers.
They are used online shopping, customer service services, sales departments, reference services, hot lines, delivery services or technical support for most modern companies.
Such a vital element of business, as a communication channel with customers, often may become the goal of attacks of unfriendliers. With the help of automatic dialing programs, you can literally "bombard" any phone number, causing an overload of office PBX equipment and reducing the quality of communication, occupying all lines and not allowing customers to get through, forcing the company to pay "empty" calls, etc.
Why need 8-800:
You often call customers from mobile phones.
- You want to increase the number of new customers.
- You work with buyers or partners throughout Russia.
- You need a single room for branches in different cities.
- You want to impress the successful and prosperous company.
The resulting effect:
Increasing the number of calls from new customers by eliminating the "paid call barrier".
- Improving the satisfaction of existing customers through the provision of a more accessible method of communication.
- Improving the positive image of the company in the eyes of customers by delivering them from spending calls.
- Call processing occurs on a dedicated cluster from a plurality of servers, therefore, with an increase in the load on the line, additional power is automatically connected, while maintaining high quality and reliability of communication.
- Specially designed tools for automated protection and dedicated employees constantly monitor the communication status to identify and prevent possible malicious actions to our customers.
- Detailed reports on calls and consumption of funds are available to you in real time in your personal account, so you can quickly identify unwanted numbers and immediately put them in the "black" list.
Connect number 8-800:
Select a room. (A huge selection of rooms in code 8-800 is available, including "beautiful."
- Pay for an order in Webmoney or in other way. (Details at the operator.)
- Configure call reception scheme.
- Go to your account and configure incoming calls.
- The number is activated immediately after payment. You can immediately receive calls.
For consultation, contact managers.
The support service works 24 hours, 7 days a week, so it will be able to instantly respond to any appeal and take any necessary measures.
Contacts:
What is a phlood phone?
How are such attacks?
What are the attackers grow?
If the victim uses a regular wired telephone connection and introduces the phone number to the blacklist, the calls will still occupy a wired line. The phone or PBX will be filtered, but during the arrival of the call and filtration, the line will still be occupied and quickly becomes overloaded. The phone of the victim becomes constantly busy and customer calls cease to enter the company.
Classic Scenario Attack
An attacker creates a flow of phone calls with different AON. Each call takes the line resource until the tube is raised. As soon as the tube rises, there is an expectation of 2-5 seconds and reset the connection. Call flow can go around the clock.
If the victim changes the phone number, it will become known to the attacker, and calls will become the second, if necessary on the third or tenth phone number.
In addition, when changing the phone number, all the efforts of the victim to advertise the old phone number are becoming in vain.
The main problem is that the usual number is limited by bandwidth and after 3-5 parallel calls the number becomes occupied and the goal of the flooders is achieved.
Forewarned is forearmed
How to prepare for the attack
Your task is to prevent serious losses. Framed with flood is difficult, but you can. Most of the flooders count the attack on the usual phone number and the usual PBX, which have a lot of restrictions.
But it's not like that if IP telephony is used. SiPnet has no restriction on the number of lines, and the behavior of your server accepting a call may be unpredictable complex.
But, if your side does not have your own VoIP server, but only SIP phones are used, then there are no reasons for optimism. Ordinary SIP phones do not have sufficient arsenal of opportunities to protect.
What will Asterisk help us?
When you receive a call to the server, the first package reports what number to you calls. This is enough to make a decision what to do with a call.
If the server decides to repel the challenge, it will immediately (for the split second) will send a message and resources will be released.
For the flood attack on the Asterisk server, an attacker must send not 5-10 simultaneous calls, and several hundreds of simultaneous calls. This call stream will invalid the network of the telecom operator through which an attacker works. The involuntary operator of the attacker himself interrupt the attack, saving his network and service for other customers.
What challenges should be taken?
Most often, the company has a list of customer telephone numbers and counterparties. Usually, they are stored in the CRM system. If a person calls you, whose number is known to you, then such a call can be immediately sent by the manager. This is called straight (intelligent) call routing. To implement such a scenario, CRM and VoIP PBX integration is necessary.
The majority of modern CRM have such an opportunity. For example, AMOCRM has integration widget. You just need to connect it and configure it. Contact your CRM to support your CRM support, they will certainly have a ready-to-integrate instruction with Asterisk. If you do not have a CRM, then you can analyze the call history that is stored in the FreePBX database.
What challenges can be disconnected?
If the call does not apply to the zone of potential customers of your business, then it can be rejected immediately. For example, you do not deliver Pitsy to Tyumen, why do you need to receive a call from Tyumen? This can be done using incoming routes (INBOUND ROUTES). Reduce the possibility of choosing AON for an attacker attacker.
How to find a list of telephone numbers of the region of the Russian Federation?
There is a database of distributed numbering of the Russian Federation. With the help of this information, you can find all stationary (ABC) and mobile (DEF), ranges of numbers of any region of the Russian Federation.
Blacklist Setup (BlackList)
If the call is accepted and removed less than 10 seconds, then most likely it is the call of an attacker. If such behavior is repeated several times, then the caller number must be blacklisted and no longer respond to calls from such a number within a few hours. This is the most complex part of the logic to beat the flood attack. Automate adding numbers to the blacklist, is dangerous. Real clients may suffer. Analyze the statistical report, it can be difficult with a large amount of calls. You can configure FREEPBX notifications about unique challenges for 3 months and analyze only numbers from notifications.
With the development of technical capabilities, new methods of fraud and struggle in a competitive environment appear. One of these methods is to create a flood in or in the telephone network.
Under the concept of "flood" (the word Flood - in translating from English means "Flood", "flood") usually understand the overflow of the communication line with unnecessary information that scores the channel. The following floods are possible:
- continuous calls;
- DDOS attack.
The most common is the flood in the form of telephone calls. With such a flood, calls come to the phone, and after raising the tube, the following options are possible:
- tensile connection;
- audio recording;
- waiting and hold call.
Then the cycle is repeated.
Legislation
Cybercrime is devoted to chapter 28 of the Criminal Code of the Russian Federation. The use of floods can be attributed to Art. 273, in which punishments for creating, use and dissemination of malicious programs.
Under art. 273 of the Criminal Code for the above, acts may be appointed in the form of imprisonment up to 4 years, as well as a fine of up to 200 thousand rubles. In the presence of aggravating circumstances (a crime committed by a group of persons, or due to indispension), the term of conclusion can reach 5 years with a fine of up to 200 thousand rubles. And the subsequent deprivation of the right to work in some posts for up to 3 years.
With the appearance as a result of these acts, severe consequences, the detention period can reach 7 years.
The above-mentioned malicious program SkypePhone Killer, with which the information distribution channels are blocked, presented on the Internet for free distribution. According to the letter of the law for such activities, the site author may well be brought to justice under Art. 273. This is confirmed in the "Methodological recommendations for the Prosecutor's supervision of the execution of laws" from 9.04. 2018, where it says that punishable under Art. 273 of the Criminal Code Dissemination of Malicious Programs can be carried out in any way, including for free and software.
Where to contact?
In the Russian Federation, the management of the "K" of the Ministry of Internal Affairs of the Russian Federation is engaged in the fight against crime in the field of computer technology.
In accordance with the practice, the crime statements associated with violations on the Internet or lines of communication are submitted directly to the duty parts of the Ministry of Internal Affairs.
Submitted statements must accept and send to the district office "K". The form of the statement is shown on the website of the Ministry of Internal Affairs of the Russian Federation.
For the implementation of its goals for blackmail, extortion and unfair competition, criminals carry out flood attacks on the phones of their victims. These floods are attacking the communication channel by unnecessary information, which leads to the impossibility of using this link. To combat flood, it is necessary to use both technical methods and the appeal to law enforcement agencies (the management "K" of the Ministry of Internal Affairs of the Russian Federation). According to Art. 273 of the branch of the offense associated with in terms of the use and dissemination of malicious programs, entail a sentence for up to 4 years in prison, and in severe consequences, the conclusion can reach 7 years.
(No ratings no)
Hello dear friends!
Www.phonegs.com offers efficient protection from telephone flood!
Have you ordered competitors?
- You are called hidden numbers, but when you take the phone right away?
- Many calls and customers can not get through to you?
- Do you lose customers and because of what is reduced profit?
Then you need to us!
What is "telephone dos" or "telephone flood"?
There are hundreds of calls on the phone. You can call and reset or lose the specified entry when you raise the phone, and so dozens, hundreds and thousands of times. The result (and purpose) of such an attack is interruptions or a complete refusal to receive incoming calls. Such an attack is able to destroy not only nervous cells, but also a business.
We work around the world with mobile, stationary, multichannel phones, as well as with TalkFree prefixes (8-800, 8-804)
How to deal with telephone flood? - This is the first question that people fall under his impact.
Unfortunately, there is no standard methods for fencing yourself from unwanted calls. For this reason, there is our project with which you can protect against DOS attacks on your phone. We will help you get rid of the phone flood as quickly as possible, in fact immediately after contacting us.
How does the counter-telephone flud service work?
All calls entering your number take filtering on our IP PBX servers in manual and automatic modes, unwanted connections are read in real time, as a result of which only those calls are received on your phone as in normal mode.
We will provide you with remote access through your personal account to statistical information about calls.
For our service are characteristic:
Countering attacks with power up to a thousand threads on the number;
- high level of protection;
- round-the-clock support;
- constantly updated base of numbers involved in attacks;
We present to your attention our service for the sale of rooms 8-800 ... !!!
The number with a code 8-800 is a telephone number that can be made free from any stationary or mobile phone from anywhere in Russia. The numbers are an integral part of any successful business built at work with customers: partners or buyers.
They are used online shopping, customer service services, sales departments, reference services, hot lines, delivery services or technical support for most modern companies.
Such a vital element of business, as a communication channel with customers, often may become the goal of attacks of unfriendliers. With the help of automatic dialing programs, you can literally "bombard" any phone number, causing an overload of office PBX equipment and reducing the quality of communication, occupying all lines and not allowing customers to get through, forcing the company to pay "empty" calls, etc.
Why need 8-800:
-Is often call customers from mobile phones.
-You want to increase the number of new customers.
-You have been working with buyers or partners throughout Russia.
-Is need a single room for branches in different cities.
-You want to make the impression of a successful and prosperous company.
The resulting effect:
Increasing the number of calls from new customers by eliminating the "paid call barrier".
Improving the satisfaction of existing customers through the provision of a more accessible communication method for them.
Improving the positive image of the company in the eyes of customers by delivering them from spending calls.
Call processing occurs on a dedicated cluster from a plurality of servers, so additional power is automatically connected when loading on the line, while maintaining high quality and reliability of communication.
Specially designed tools for automated protection and dedicated staff constantly monitor the state of communication to identify and prevent possible malicious actions to our customers.
Detailed call reports and consumption of funds are available to you in real time in your personal account, so you can quickly identify unwanted numbers and immediately put them in the "black" list.
Often there is a call in Internet communication not to flood. What does it mean and how to determine if your messages do not belong to flood? On the Internet there are own rules that have been developing for years, and just like in real life, there are our hooligans and just impatient people. To know exactly why the site moderators or the forum appeared claims to the behavior of users, it is worth understanding the terminology.
What is flood?
If you appeal to the history of the term of the term, then it is a slightly simplified and improper pronunciation of the English word Flood, which is translated as "stream". This is a very accurate definition, because in initially Flood called the flow of meaningless messages, designed to tightly score the space anything, right up to emoticons or symbol sets. Sometimes the flow picks up other users, copying the first few messages, and are accepted. The meaning of the word over time has changed somewhat and expanded. In the Russian-speaking Internet segment, the concept of "flood" has absorbed such a phenomenon as "flame".

What is the flood different from the flame?
If Flood was initially a meaningless flow, Flame is incorporated with defined targets. The word is translated as "flame" and refers to a number of nuances of communication. Flame is a conversation not on the topic of conversation, but solely for the sake of burning emotions. Literally this is a quarrel for the quarrel itself, the instigators are not interested in truth or confirmation of their rightness. Any types of spoken aggression are used, from direct insults to thin trolling.
For the past few years, in the case of Flame, you can hear the request "stop flooding" - what does this mean? The merger and absorption of concepts occurred, as it often happens in Russian. Now Flood is called almost any communication, which is different from the startpost specified in the start, even if it is initially conducted in a non-aggressive key.
Flud - what does it mean?
For example, several Internet users gathered on the forum to discuss the new feature film. After several posts, a discussion may flash, only distant with the relationship to the original topics of the conversation. If a film about dogs, and in the comments, there is a dispute about whether it is possible to wear a short skirt, and this is not a relation to the film, nor to the dogs or director, then users began to flood. The meaning of the word really went out, and the permissibility of such a dispute remains exclusively on the conscience of the users themselves, the project moderators and concerns the rules that need to be observed.

FLOD Fight Methods
There are two main ways to organize communication on any Internet resource. The first is a thorough moderation of messages that are made by people who have access to resource management. The moderator can either in words call for user order, or take punitive measures: make warnings or block users generally, depriving the right to leave comments.
The second method is passive. For lovers, a special topic is simply created, in which you can communicate with each other on any topics, from recipes to political disputes. Over time, in many resources, the meaning of the word has changed to quite harmless. You wanted to flood, what does this mean? Most likely, it's just a desire to talk with pleasant interlocutors, and for this it is really better to go into a special topic or subforum, which is often called "Flood" or "Fludalka".
If you have come up with the topic of someone in a personal network diary, the function of the moderator performs the owner of the resource, and in most cases it is enough to apologize for the flood. Many people do not see anything special in the desire to talk, even if the interlocutors left the original topic, and allow them to communicate, while they themselves support the conversation. Thus, it turns out a virtual imitation of a regular conversation, when the themes cling to each other, and the result is a relaxed and pleasant pastime.
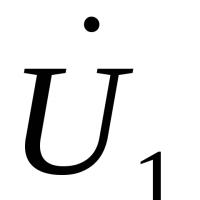 Magnetometry in the simplest version The ferrozond consists of a ferromagnetic core and two coils on it
Magnetometry in the simplest version The ferrozond consists of a ferromagnetic core and two coils on it Effective job search course search
Effective job search course search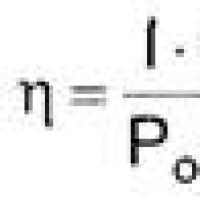 The main characteristics and parameters of the photodiode
The main characteristics and parameters of the photodiode How to edit PDF (five applications to change PDF files) How to delete individual pages from PDF
How to edit PDF (five applications to change PDF files) How to delete individual pages from PDF Why the fired program window is long unfolded?
Why the fired program window is long unfolded? DXF2TXT - export and translation of the text from AutoCAD to display a dwg traffic point in TXT
DXF2TXT - export and translation of the text from AutoCAD to display a dwg traffic point in TXT What to do if the mouse cursor disappears
What to do if the mouse cursor disappears