What is the rate of hashing. What is hash and what is it needed for? What is the mining process based on
What is hash?Hash function is called mathematical transformation of information in a short, certain length string.
Why do you need it?Analysis using hash functions is often used to monitor integrity. important files operating system, important programs, important data. Control can be done both as needed and on a regular basis.
How it's done?At first, determine which the integrity of which files must be monitored. For each file, it is calculated to calculate the value of its hash over a special algorithm while maintaining the result. After the required time, a similar calculation is made and the results are compared. If the values \u200b\u200bdiffer, it means the information contained in the file has been changed.
What characteristics should have a hash function?
- must be able to perform transformations of data of arbitrary length to fixed;
- must have an open algorithm so that its cryptoscope can be explored;
- must be one-sided, that is, there should be no mathematical capabilities by determining the source data;
- must "resist" conflicts, that is, it should not give out the same values \u200b\u200bwith different input data;
- should not require large computing resources;
- with the slightest change in the input data, the result must change significantly.
What are the popular hashing algorithms?The following hash functions are currently used:
- CRC - cyclic excess code or checksum. The algorithm is very simple, has a large number of variations depending on the required output length. Not cryptographic!
- MD 5 is a very popular algorithm. Like Him previous version MD 4 is a cryptographic function. Hesha size 128 bits.
- SHA -1 is also very popular cryptographic confunction. Hesha size 160 bits.
- GOST R 34.11-94 - Russian cryptographic standard for calculating hash functions. Hesha size 256 bits.
When can these algorithms use a system administrator?Often when downloading any content, such as programs from the manufacturer, music, films, or other information, there is a value of the checksum calculated by a specific algorithm. For safety reasons, after downloading, it is necessary to conduct an independent calculation of the hash function and compare the value with what is indicated on the website or in the application to the file. Did you ever do it?
What is more convenient to count hash?Now there are a large number of similar utilities of both paid and free to use. I personally liked Hashtab. First, the utility during installation is embedded in the form of a tab to the properties of the files, secondly, allows you to choose a large number of hashing algorithms, and thirdly is free for private non-commercial use.
What is Russian?As mentioned above in Russia, there is a standard of hashing GOST R 34.11-94, which is used everywhere in many manufacturers of information security tools. One of these funds is the program of fixation and control source state Software complex "Fix". This program is a means of controlling the effectiveness of the application of SZI.

Fix (version 2.0.1) for Windows 9x / NT / 2000 / XP
- Calculate the checks of the specified files by one of the 5 implemented algorithms.
- Fixation and subsequent control of the original state of the software package.
- Comparison of the versions of the software package.
- Fixation and control of catalogs.
- Monitoring changes in specified files (directories).
- Formation of reports in TXT, HTML, SV formats.
- The product has certificate FSTEC on the NDV 3 № 913 until June 1, 2013
And how about the EDS?The result of the calculation of the function together with the secret key of the user enters the input of the cryptographic algorithm, where the electronically digital signature is calculated. Strictly speaking, the hash function is not part of the EDS algorithm, but often this is done specifically, in order to exclude the attack using the public key.
Currently, many e-commerce applications allow you to store the user's secret key in the closed token area (Rutoken, Etoken) without the technical ability to extract it from there. The token itself has a very limited area of \u200b\u200bmemory, measured in kilobytes. To sign the document there is no possibility to transfer the document to the token itself, but to transfer the hash of the document to the token and at the exit to get the EDS is very simple.
Many of the Miminat, or Minnieli, or are going to start the Maja, selecting themselves the equipment to the maximum of some gigaches there. What are these hashies?
As you know, cryptocurrency (take Bitcoin) is mined as a result of solving mathematical problems. But why is Bitcoin generated by this way? To do this, you need to understand the value of such a process as cryptographic hash or hashing. So, hashing is a change in incoming data various size In the source data of a clearly specified size, using a special algorithm (rules).
Let's figure it out why it is necessary. Suppose we own a computer network or a closed database into which you can only get using the login and password. People are registered with thousands of us, introducing this data. And now imagine what will happen if someone possesses access to your computer network. They will get personal data huge number other people. It is for this that this does not happen, and a cryptographic hash was invented.

This is how it works: the process of hashing receives data, such as a password, and processes these input through a special algorithm that creates a large number called "hash". Hash has two key distinctive properties.
- First, one and the same input data always corresponds to the same number. That is, if you will enter the same password every time, the hash will generate the same number at the exit, which corresponds to it.
- Secondly, hashing is a unidirectional process. It is almost impossible to take the meaning of the hash and with the help of reverse development to disclose what was at the entrance. So it is impossible to go from the opposite, and entering the hash value, that is, the most large number, Determine the password. It is thanks to these two hash items and is used as an independent data processing method. If the process was reversible, it would be called not hashing, but an old good encryption / decryption that in the modern world is ineffective.
Now how it works for even more simple example. You register on the site, enter your password. The system processes it and generates a hash that matches your password. At the same time, the password itself is not saved. And now, when you come to this site and enter this password, the system will generate a hash, compare it with a stored value, and approve access with coincidence. And hackers, hacking the system, will receive only a set of haze, absolutely useless to get a password.

There is only one disadvantage in this system - if you forget the password, it cannot be restored. The system does not store your passwords, therefore it cannot send them. However, in extreme cases, the password can be reset, you will send a temporary password, going through which you can set your own again. This disadvantage, in my opinion, is not critical, especially against the background of the safety of hashing.
And now back to the topic of Bitcoin and to the fact that this is for computer tasks, the solution of which awards you with cherished bitcoins. So, earlier we said that with the help of a hash you can not determine your password. However, the way to learn this value is still there. It is called "the method of coarse power" or in other words - the combinations are brutexing until the moment until guess and the value did not coincide with the hash.
Imagine that the Bitcoin Protocol issued the task - to guess the number 5, and the total numbers are a million. Your chances to solve this problem amount to 1 to a million. If the network wants to simplify the task, it sets the range of numbers, let's say from 1 to 100, and your chances are already 100 to a million. If you need to complicate the task, expand the range, and now you need to guess one figure not from a million, but from a billion values. It is in this that the mathematical task is - it is necessary that the number that corresponds to a certain hash.
Hash is updated every 10 minutes, and the first computer, solving the task, receives a reward. But today the range of numbers from which the right thing needs to be found is huge. All bitcoin-miners of the world together process for a minute about 50,000,000,000,000,000 input values \u200b\u200bper second in an attempt to pick up the key to the specified hash.
Bitcoin Network regularly tracks the speed of solving the problem, and if it has been solved much faster than 10 minutes, make the following harder. If not invested in 10 minutes, the next will be easier. As soon as the first computer decided the task, it shows its solution to all participants who check this decision, and when confirming the coincidence of the Heshem, he receives a reward, and the new cycle begins next.

The above is the chart of growth in difficulty, so choosing mining equipment is better inserted with a good power supply and the speed of calculations.
Often when downloading torrents or directly the files themselves in the description, there is something like "AD33E486D0578A892B8VBD8B19E28754" (for example, in Ex.ua), often with the asscription "MD5". This is a hash code - the result that gives a hash function after processing incoming data. Translated from the English hash indicates confusion, marijuana, herb or a dish of finely chopped meat and vegetables. Very and very difficult, we can say that it is almost impossible. Then the question arises: "Why do you need all these, they give out the incomprehensible abrakadabra, which is also not amenable to decipher?" This will be discussed in this article.
What is a hash function and how does it work?
This function is designed to convert the incoming data as much as large in the result of a fixed length. The process of such a transformation itself is called hashing, and the result is a hash or hash code. Sometimes still use the words "imprint" or "digest of the message", but in practice they are much less common. There are a lot of different algorithms for how you can turn any data array into a certain sequence of symbols of a certain length. The highest distribution received an algorithm called MD5, which was developed back in 1991. Despite the fact that today MD5 is somewhat outdated and not recommended for use, it is still still in the go and often instead of the word "hash code", on sites simply write MD5 and indicate the code itself.
Why do you need a hash function?

Knowing the result, it is almost impossible to determine the source data, but the same incoming data give the same result. Therefore, hash function (it is also called a convolution function) is often used for storage important information, such as password, login, certificate number and other personal information. Instead of comparing the information entered by the user, with those that are stored in the database, there is a comparison of their haze. This gives a guarantee that, with a random leakage of information, no one can take advantage of important data for its purposes. By comparing the hash code, it is also convenient to check the correctness of downloading files from the Internet, especially if the connection interruptions took place during the download.
Hash functions: what they got.

Depending on its purpose, the hash function can be one of three types:
1. Function to check the integrity of information
When it occurs over the network, the hash package occurs, and this result is also transmitted with the file. When receiving, the hash code is calculated and compared with the value obtained over the network. If the code does not match, it says about errors, and the spoiled package will again be transferred. Such a function has a quick rate of calculation, but a small amount of hash values \u200b\u200band poor stability. An example of this type: CRC32, in which only 232 differences between themselves.
2. Cryptographic function
Used to protect from (ND). They allow you to check if the data distortion occurred as a result of ND during the transfer of files over the network. True hash in this case is publicly available, and the hash of the file received can be calculated using the set different programs. In such functions, a long and stable period of work, and the search for collisions (possible matches of the result from different source data) is very complicated. Such functions are used for storage in database passwords (SH1, SH2, MD5) and other valuable information.
3. A function intended for creating an effective data structure
Its goal is a compact and fairly ordered organization of information in a special structure that is called the hash table. Such a table allows you to add new informationDelete information and search for the desired data at a very high speed.
Let's try to understand what the complexity of the network, which is frightened by all new miners and what kind of holstery network is.
Now there are so many chat chats cryptocurrency and trading. Every question of the newcomer "What ASIC to buy or what farm to assemble" is accompanied by an answer ... "Yes, you see how the complexity of the network is growing and do not even think about this matter!"

For simplicity, we will consider the complexity and housing of the network on the example of a coin (analogue of Etherium, on a similar algorithm). The numbers are less and hopeful to me it will be easier for you to explain the essence.
The network of each cryptocurrency has such a parameter as "block creation time". In the case of Musicoin it is 15 seconds. Every 15 seconds one of the miners should find a solution to create a block.
How to keep this parameter in 15 seconds, regardless of the number of miners that are connected to the network? After all, if there are many miners, they will find blocks too often (here is an example of an empty block in the UBIQ network http://www.ubiqu.cc/block/212214), and if miners are small, then the blocks will be rarely and network transactions will go a very long time.
For finding 1 block in the Musicoin network Mainer or Pool (many miners together) get 309 Musicoin \u003d $ 13 coins at today's course.
Retreat. In the network, Etherumer for finding one block is paid 5 Eth \u003d $ 1900, in the network Etherium Classic 5 etc \u003d $ 75. But, unfortunately, the complexity and hashiret networks in these coins are many times more.
If the miners will produce empty blocks and receive money for it - the coin will be depreciated, and if the blocks find slowly - transactions will stand up ... Again, the coin will be depreciated.
The complexity begins to work here. If on your fingers, then it is just the complexity of the task that the Mainers needs to be solved to create a block, and it can change. The complexity depends on the netheraid of the network (the number of miners connected to the network of this coin). If miners are not enough - the complexity falls if the miners are much - the complexity begins to grow and one concrete Mainer the block is more difficult to find the block ...

Remuneration Miners get in the coins of the network itself, but all miners love good cars, food and rags. Therefore, it is important for them how much is in US dollars, because if the price of the coin has grown on the stock exchange, then the value of the remuneration for finding the block has become more in the notorious US dollars.
The other day, August 27 (see the chart above) the price of Musicoin coins has grown at times, miners who were engaged in Minning Zcash coins, Ethyurium, Monero ... Achnuli in anticipation more profits and switched their farms on the Musicoin coin. At the same time, the Musicoin network itself, of course, responded with a sharp increase in complexity.
The complexity is measured in the hash (usually the terrarahchs th), in use to the mining, this unit of completed work. The network power (the number of miners) is measured in hashas per second (TH / S). The network itself adjusts the complexity so that the complexity / power of the network \u003d time until the next block (in the case of Musicoin 15 seconds).
August 27 to takeoff Price complexity of the network was: 7.5 TH on average, and the Heschery of the network: 500 GH / S (approximately 16,000 video cards), then after takeoff, the price of the network has grown to: 1.12 Th / S (1120 GH / S) (approximately 35000 Video cards), and the complexity at the same time took off to 16.728 TH.
As a result, the profit of the farm, which mined the coin before the price takeoff and the price has not changed after takeoff. The farm began to produce less coins, but for the larger price (the farm does not matter or a whole pool of farms).
This is a key point that many people do not understand. Yes, you can pull up a couple of bucks in these jumps, but, as a rule, everything is stirred in a couple of hours and not fundamentally what currency you will be produced on the same algorithm. The exhaust will be the same. Of course, if you are waiting for one or another currency, dig it.
It is necessary to make another digression, there are people who closely follow the complexity and hashier ... all networks are a round day and at moments when Hesrayite will fall or the complexity sends, buying power on Nicehash and send them to a network of recognized coins. And we catch a lot of blocks.

Actually, the conclusion: Let's imagine that there is only one currency Etieth. Hesreite Network Etherumer is constantly growing, more and more new miners come. If the course of Etherium is falling, and the number of miners will be unchanged (or will grow even worse), the mining will come to the level of the outlet (how much did the $ spread, so much paid for electricity $). In this situation, the farm will begin to turn off and sell, the complexity will begin to fall, and incomes to grow again.
Survives the strongest and one who has money sometimes wait for the Major on the outlet.
 Cellular - what it is on the iPad and what's the difference
Cellular - what it is on the iPad and what's the difference Go to digital television: What to do and how to prepare?
Go to digital television: What to do and how to prepare? Social polls work on the Internet
Social polls work on the Internet Savin recorded a video message to the Tyuments
Savin recorded a video message to the Tyuments Menu of Soviet tables What was the name of Thursday in Soviet canteens
Menu of Soviet tables What was the name of Thursday in Soviet canteens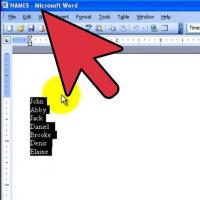 How to make in the "Word" list alphabetically: useful tips
How to make in the "Word" list alphabetically: useful tips How to see classmates who retired from friends?
How to see classmates who retired from friends?