Consider some search algorithms in peerging networks, limiting the basic methods of search by keywords. What is P2R video surveillance technology peer to
Peer to Peer is one of the most common methods of high-speed network interaction, built over a junior computer network. The main principle of work Peer to Peer (P2R) - Absolute equality between all users. As a rule, in a peerging (peer-to-peer) network, any distinction between the main server and the client computer is excluded, and each network node is dealt with both server and user tasks.
Piropan networks have become in demand relatively recently. Ten years ago, networks with the client-server architecture were absolutely popular. Peer to Peer (P2R) managed to displace their predecessor, due to the presence of a number of benefits:
- anonymity - user data involved in the network is stored without attracting third parties;
- stability - the network continues to work even if most nodes simultaneously turn off;
- scalability - bandwidth The network has a permanent amount and excludes the creation of the so-called "narrow neck" in separately taken points, since the exchange of data can occur directly between the extreme nodes.
Where PEER TO PEER is used (P2R)
The classic area of \u200b\u200buse of peer-to-peer peer-to-peer is decentralized file sharing, for example, the well-known BitTorrent protocol. For supporting stable work The resource, as well as to ensure maximum speed, the developers use a peer-to-peer R2P network, which offers the best scalability, which is extremely important when exchanging large files.
Modern resources famous high levels Anonymity and user security, as a rule, use peer-to-peer networks. However, services similar to the same "Torah" are most often caused concern, as they are an ideal platform for committing illegal transactions, sales of prohibited substances, weapons, etc. To date, more than two million people use this browser, and specialists Call his Black Ethernet (black Internet).
Peer-free R2P networks use cryptocurrency platforms, including Bitcoin. It was his developer who is Satoshi Doboto, managed to solve the main task - the elimination of the possibility of reuseing the same means. For this, a unique blockchain architecture operating on the principle of proof-of-work (proof of work performed) was created. Despite the fact that today there is a colossal number of forks, Bitcoin remains the most popular cryptomet.
Disadvantages of Peer to Peer (P2R)
 In order to place your platform in the Piroga Network of P2R, it is necessary to have a colossal luggage of knowledge, as it is necessary to independently think out security methods. In the "crude" peering network (not having centralized services), any user is a potential intruder. In this case, it is impossible to trust anyone. For each developer who has chosen a peer-to-peer network of P2P, security is a difficult task, because problems begin at the first stage - creating ideal authentication conditions.
In order to place your platform in the Piroga Network of P2R, it is necessary to have a colossal luggage of knowledge, as it is necessary to independently think out security methods. In the "crude" peering network (not having centralized services), any user is a potential intruder. In this case, it is impossible to trust anyone. For each developer who has chosen a peer-to-peer network of P2P, security is a difficult task, because problems begin at the first stage - creating ideal authentication conditions.
Theoretically is impossible, since the strict peer-to-peer network of P2P is in no way associated with the Global Certification Center. And without the involvement of third parties with an extensive database, and offering the possibility of concluding preliminary contracts, to implement a reliable intrastable authentication - is unrealistic.
Another, extremely serious problem associated with the safety of Piroga Networks P2R, is a vulnerability in front of a hacker attack, which is called sybil. It is carried out by implementing the network of foreign nodes with a unique identifier. The attack itself does not carry any threat to a peer-to-peer network, but is an auxiliary tool for the implementation of a number of actions that put the safety platform operating with P2R.
Relevance of Peer to Peer (P2R)
According to official statistics based on Internet providers, the peer-to-peer network accounts for about 75% of world traffic. However, despite the enormous trust of developers, peering networks cannot be considered perfect. In addition to the above-mentioned safety problems, P2R is also subject to the so-called timing attacks based on correlation. Despite the fact that the holding of such hacker attacks requires the attraction of huge capacities, their implementation is quite real, for example, for representatives of the special services.
Stay aware of all important events United Traders - subscribe to our
One of the first peerging networks was created in 2000. It still functions, although due to the serious shortcomings of the algorithm users currently prefer the GNUTELLA2 network.
When connected, the client receives from the node, with which he managed to connect, a list of five active nodes; They refer to the search for a resource for a keyword. The nodes are looking for the corresponding resources for the query and, if you do not find them, send the request to the active nodes up on the "wood" (the network topology has the structure of a tree type graph) until there is a resource or the maximum number of steps will not be exceeded. Such a search is called query reproduction (Query Flooding).
It is clear that such a realization leads to the exponential increase in the number of requests and, accordingly, at the upper levels of "wood" can lead to a refusal of maintenance, which was observed repeatedly in practice. The developers have improved the algorithm, entered the rules, in accordance with which requests can send up the "wood" only certain nodes - the so-called dedicated (Ultrapeers), the remaining nodes (Leaves) can only request the latter. The system of caching nodes is also introduced.
In this form, the network operates now, although the flaws of the algorithm and the weak possibilities of expandability lead to a decrease in its popularity.
The shortcomings of the GNUTELLA protocol initiated the development of fundamentally new algorithms for the search for routes and resources and led to the creation of a DHT protocol group - in particular, the Kademlia protocol, which is now widely used in the largest networks.
Requests in the Gnutella network are sent via TCP or UDP, file copying is carried out via the HTTP protocol. IN lately There appeared extensions for client programsallowing you to copy files by UDP, making XML requests for meta-information about files.
In 2003, a fundamentally new GnuTella2 protocol was created and the first customers supporting it, which were reverse with Gnutella clients. In accordance with it, some nodes become concentrators, the others are conventional nodes (Leaves). Each ordinary node has a connection with one or two concentrators. A hub is associated with hundreds of ordinary components and dozens of other hubs. Each node periodically forwards the hub of the keyword identifiers by which you can find resources published by this node. Identifiers are saved in the overall table on the hub. When the node "wants" to find a resource, it sends a request to a keyword to its concentrator, the latter either finds the resource in its table and returns the ID of the node that has a resource, or returns a list of other hubs, which the node reappears in turns randomly. Such a search is called a search using the Random Walk.
The noteworthy feature of the GNUTELLA2 network is the ability to reproduce information about the file in the network without copying the file itself, which is very useful in terms of tracking viruses. For the transmitted packets, the network has developed its own format similar to XML, flexibly implementing the possibility of increasing the functionality of the network by adding additional service Information. Queries and lists ID keywords are sent to UDP concentrators.
Here is the list of the most common client programs for Gnutella and Gnutella2: Shareaza, Kiwi, Alpha, Morpheus, GnuCleus, Adagio Pocket G2 (Windows Pocket PC), Filescope, Imesh, Mldonkey
Peer-to-peer technology
Performed:
female student 1 courses FMF magistra
Kulachenko Nadezhda Sergeevna
Checked:
Chernyshenko Sergey Viktorovich
Moscow 2011.
Introduction
As the Internet has been developing, more and more interest in users cause file sharing technologies. More affordable than before, the network and the availability of wide access channels allow you to significantly easily find and pump the necessary files. Not the last role in this process play modern technologies and the principles of constructing communities that allow us to build systems, very effective from the point of view of both organizers and users of file sharing networks. Thus, this topic is currently relevant, because Constantly appear new networks, and the old either stop working, or modifier and improved. According to some reports, currently on the Internet more than half of the entire traffic accounts for the traffic of file sharing networks. The size of the largest of them exceeded the mark in a million simultaneously working nodes. The total number of registered participants of such file sharing networks around the world is about 100 million.
Peer-to-peer (English equal to equal) is an ancient principle of Japanese samurai and utopian socialists. He gained real popularity at the end of the twentieth century. Now this principle uses millions of Internet users, talking to friends from distant countries, downloading files from users with whom have never been familiar.
PEER-TO-PEER (P2P) technology is one of the most popular topics to date. The popularity achieved using such programs as Skype, BitTorrent, DirectConnect and a list of such programs can continue and continue, confirms the potential of peer-to-peer systems.
In this paper, I will consider the specific principles of the operation of the resources of this topic, the principles of functioning of popular peerging networks that are actively used to exchange files, as well as the problems of their use.
1. Napster and Gnutella - the first peer's networks
Napster's first pyring network appeared in 1999 and immediately became known to the entire online community. The author of the client was eighteen-year-old Sean Fenning. Napster connected thousands of computers with open resources. Initially, Napster users exchanged mp3 files.
Napster made it possible to create an interactive multiplayer environment for some specific interaction. Napster provides all users connected to it. The ability to exchange music files in MP3 format almost directly: Napster's central servers provide the ability to search on computers all users connected to them, and the exchange occurs through the central servers, according to the user-to-user. A considerable part of records circulating in the NAPSTER environment has been protected by copyright law, but it applies to free. Napster calmly existed for five months, becoming a very popular service.
On December 7, the Association of Recommegement Industry of America (RIAA) was submitted to Napster to Court for the "Direct and Indirect Copyright Violation".
In the end, Napster first sold some European firm, and then it was closed at all.
Gnutella - was created in 2000 by Nullsoft programmers as a succession of Napster. It still functions, although due to serious flaws of the algorithm, users currently prefer the GNUTELLA2 network. This network works without a server (complete decentralization).
When connected, the client receives from the node, with which he managed to connect, a list of five active nodes; They refer to the search for a resource for a keyword. The nodes are looking for the corresponding resources for the query and, if you do not find them, send the request to the active nodes up on the "wood" (the network topology has the structure of a tree type graph) until there is a resource or the maximum number of steps will not be exceeded. Such a search is called query reproduction (Query Flooding).
It is clear that such a realization leads to the exponential increase in the number of requests and, accordingly, at the upper levels of "wood" can lead to a refusal of maintenance, which was observed repeatedly in practice. The developers have improved the algorithm, entered the rules, in accordance with which requests can send up the "wood" only certain nodes - the so-called dedicated (Ultrapeers), the remaining nodes (Leaves) can only request the latter. The system of caching nodes is also introduced.
In this form, the network operates now, although the flaws of the algorithm and the weak possibilities of expandability lead to a decrease in its popularity.
The shortcomings of the GNUTELLA protocol initiated the development of fundamentally new algorithms for the search for routes and resources and led to the creation of a DHT protocol group - in particular, the Kademlia protocol, which is now widely used in the largest networks.
Requests in the Gnutella network are sent via TCP or UDP, file copying is carried out via the HTTP protocol. Recently, extensions have appeared for client programs that allow you to copy files by UDP, making XML query meta-information about files.
In 2003, a fundamentally new GnuTella2 protocol was created and the first customers supporting it, which were reverse with Gnutella clients. In accordance with it, some nodes become concentrators, the others are conventional nodes (Leaves). Each ordinary node has a connection with one or two concentrators. A hub is associated with hundreds of ordinary components and dozens of other hubs. Each node periodically forwards the hub of the keyword identifiers by which you can find resources published by this node. Identifiers are saved in the overall table on the hub. When the node "wants" to find a resource, it sends a request to a keyword to its concentrator, the latter either finds the resource in its table and returns the ID of the node that has a resource, or returns a list of other hubs, which the node reappears in turns randomly. Such a search is called a search using the Random Walk.
The noteworthy feature of the GNUTELLA2 network is the ability to reproduce information about the file in the network without copying the file itself, which is very useful in terms of tracking viruses. For transmitted packets, the network has developed its own format similar to XML, flexibly implementing the possibility of increasing the functionality of the network by adding additional service information. Queries and lists ID keywords are sent to UDP concentrators.
2. P2P technologies. Principle "Client-Client"
Single, decentralized or pyring (from the English. Peer-to-peer, P2P - equal to equal) Network is an overlay computer network based on participants' equality. There are no dedicated servers in such a network, and each node (PEER) is both a client and server. Unlike the client-server architecture, such an organization allows you to maintain network performance in any number and any combination of available nodes. We network participants are peers.
For the first time, the term peer-to-peer was used in 1984 by IBM when developing a network architecture for dynamic traffic routing through computer networks ADVANCED PEER TO PEER NETWORKING. The basis of the technology is the principle of decentralization: all nodes in the P2P network are equal, i.e. Each node can simultaneously perform both as a client role (information recipient) and the role of the server (information provider). "This ensures such advantages of P2P technology in front of a client-server approach, such as fault tolerance when losing communication with multiple network nodes, an increase in the speed of obtaining data by copying simultaneously from several sources, the ability to share resources without" binding "to specific IP addresses, huge power Networks in general, etc. "[2]
Each of the equal nodes interacts directly only with some subset of network nodes. If you need to transfer files between non-optating network nodes, file transfer is carried out either through intermediary nodes, or according to the temporarily installed direct connection (it is specifically set for the transmission period). In its work, file sharing networks use their own set of protocols and software, which is incompatible with FTP and HTTP protocols and has important improvements and differences. First, each client of such a network, downloading data, allows you to connect to it to other customers. Secondly, P2P servers (unlike HTTP and FTP) do not store files for exchanging, and their functions are based mainly to coordinating the collaboration of users in this network. To do this, they lead a kind of database in which the following information is stored:
Which IP address has one or another network user;
What files are posted from what client;
What fragments of which files where are located;
Statistics of the one who has downloaded and gave to download others.
Work in a typical file sharing network is built as follows:
The client requests the required file on the network (it is possible to search for the desired file as stored on the servers).
If a the desired file. there is also found, the server gives the client an IP address of other customers who have this file was found.
The client requested the file sets the "direct" connection to the client or clients who have the desired file, and starts downloading it (if the client is not disconnected at this time from the network or not overloaded). At the same time, in most P2P networks it is possible to download a single file from several sources at once.
Clients inform the server about all clients that are connected to them, and files that are requested.
The server enters into its database who downloaded that (even if the files are not entirely downloaded).
Networks created on the basis of PEER-TO-PEER technology are also called peerging, peer-to-peer or decentralized. And although they are used now mainly for the separation of files, there are still many other areas where this technology is also successfully applied. These are television and audio reports, parallel programming, distributed resource caching for unloading servers, mailing notifications and articles, support for the domain name system, indexing distributed resources and their search, backup and create sustainable distributed data warehouses, messaging, the creation of systems resistant to attacks Type "Failure to maintain", distribution of software modules.
3. Basic Vulnerable P2P Parties
To cope with the problem described, clients must use reliable hash functions ("trees" of hash functions if the file is copied in parts), such as SHA-1, Whirlpool, Tiger, and only to solve in unomatural tasks - CRC control sums. To reduce the volumes of sent data and facilitate their encryption, you can apply compression. To protect against viruses, you need to be able to store identifying meta-information about the "worms", as, in particular, is done on the GNUTELL2 network.
Another problem is the ability to counter servers and nodes. In the absence of a mechanism for authentication of forwarded service messages, such as certificates, it is possible to falsify the server or node (many nodes). Since the nodes exchange information, fake some of them will result in compromising the entire network or part of it. Closed by clients and servers is not a solution to the problem, since it is possible for reengineering protocols and programs (ReverseEngineering).
Part of the clients only copy other people's files, but do not offer anything to copy others (Leechers).
In Moscow houses on several activists who are available more than 100 GB of information, accounts for about a hundred, laid out less than 1 GB. To combat it is used miscellaneous methods. The emule uses the loan method: copied the file - the loan decreased, allowed you to copy my file - the loan increased (xmule is a credit system with promoting the spread of rare files). In the EDONKEY network is stimulated by sources, the BitTorrent is implemented "how many file blocks received, so much gave", etc.
4. Some Pirot Networks
4.1 DirectConnect.
peernet Torrent peernet network
Direct Connect is a partially centralized file sharing (P2P) network, which is based on a special protocol developed by Neomodus.
Neomodus was founded by Jonathan Hess in November 1990 as a company that earned on the ADWARE program "Direct Connect". The first third-party client was "DCLITE", which has never fully supported the protocol. The new version of the Direct Connect has already required a simple encryption key to initialize the connection, it hoped to block third-party clients. The key was hacked and the author DCLite released new version your program compatible with the new software from Neomodus. Soon, the DCLite code was rewritten, and the program was renamed Open Direct Connect. Among other things, her user interface He became multi-document (MDI), and the ability to use plugins for file sharing protocols (as in MLDOnKey). Open Direct Connect also did not have complete protocol support, but appeared under Java. Low later, other clients began to appear: DCC (Direct Connect Text Client), DC ++, etc.
The network works as follows. Clients are connected to one or more servers, the so-called habams for searching for files that are usually not interconnected (some types of hubs can be partially or fully associated with the network using specialized scripts or Hub-Link program) and serve to search for files and sources for their downloads. As a hub, Ptokax, Verlihub, Ynhub, Aquila, DB Hub, Rushub are most often used. To communicate with other hubs, so-called are used. DCHUB links:
dCHUB: // [username] @ [IP or Domain Hub]: [Huba port] / [File path] / [File Name]
Differences from other P2P systems:
1. Conditioned network structure
· Developed multiplayer chat
· Network server (hub) can be devoted to a certain topic (for example, the music of a particular direction), which makes it easy to find users with the required files
· Presence of privileged users - operators with an enhanced set of hub management capabilities, in particular, following the compliance with the users of the Chat and File sharing rules
2. Customer-dependent
· Ability to download entire directory
· Search results not only by file names, but also by directories
· Restrictions on the minimum amount of shared material (by volume)
· Support scripts with potentially limitless capabilities both on the client side and on the side of the hub (right not for all sorts of hubs and customers)
The DC ++ client authors have developed a fundamentally new protocol for solving specific problems, called Advanced Direct Connect (ADC), whose goal is to improve the reliability, efficiency and safety of the file sharing network. On December 2, 2007, the final version of the ADC 1.0 protocol was published. The protocol continues to develop and supplemented.
4.2 BitTorrent
BitTorrent (letters. English. "Big Stream") - Piring (P2P) network Protocol For cooperative file sharing via the Internet.
Files are transmitted by parts, each Torrent client, receiving (downloading) these parts, at the same time gives (downloads) to their other customers, which reduces the load and dependence on each source client and provides data redundancy. The protocol was created by Bram Koen, who wrote the first Torrent Client "BitTorrent" in Python on April 4, 2001. The launch of the first version took place on July 2, 2001.
For each distribution, the metadata file is created with the extension .Torrent, which contains the following information:
TRACKER URL;
General information about files (name, length, etc.) in this distribution;
Checksums (more precisely, hash-sum Sha1) segments of the filed files;
Passkey user if registered on this tracker. The key length is set by the tracker.
Not necessary:
Hash-sum files fully;
Alternative sources that do not work on the BitTorrent protocol. The most common support for the so-called WEB-SID (HTTP protocol), but are also valid are FTP, ED2K, Magnet URI.
Metadata file is a dictionary in the Bencode format. Metadata files can be distributed via any communication channels: they (or links to them) can be postponed on web servers, placed on home network users, send by email, publish in blogs or RSS news feeds. It is also possible to obtain Info part of the public metadata file directly from other distribution participants thanks to the Extension For Peers to Send Metadata Files protocol. This allows you to do with the publication of only the magnet link. After receiving a file with metadata in any way, the client can start downloading.
Before you start downloading, the client is connected to the Trointer at the address specified in the torrent file, tells him his address and hash sum of the torrent file, to which the client receives the addresses of other clients downloading or distributing the same file. Further, the client periodically inform the tracker about the progress of the process and receives an updated list of addresses. This process is called an ad (eng. Announce).
Customers are connected to each other and exchange file segments without direct participation of the tracker, which only stores information obtained from customer exchanges connected to the customer exchange list and other statistical information. For efficient work BitTorrent networks need to be able to receive incoming connections as much clients. Incorrect setting NAT or firewall can interfere.
When connected, customers immediately exchange information about their segments. The client who wants to download the segment (Litter) sends a request and, if the second client is ready to give, receives this segment. After that, the client checks the checksum of the segment. If it coincided with the one that is recorded in the torrent file, the segment is considered successfully downloaded, and the client notifies all the attached peters about the presence of this segment. If the checksums differ, the segment begins to jump again. Some clients are banging those peers that are too often incorrect segments.
Thus, the amount of service information (torrent file size and message size with the segment list) directly depends on the quantity, and hence the size of the segments. Therefore, when choosing a segment, you must follow the balance: on the one hand, with a large size of the segment, the amount of service information will be less, but in the case of an error checking the checksum will have to download again more information. On the other hand, with a small error size is not as critical, since it is necessary to re-download a smaller volume, but the size of the torrent file and messages about the available segments becomes greater.
When downloading is almost completed, the client enters special regimecalled End Game. In this mode, it requests all the remaining segments from all connected peters, which avoids a slowdown or complete "hanging" of almost complete injection due to several slow customers.
The protocol specification does not determine when the client must enter the END GAME mode, however, there is a set of generally accepted practices. Some clients are included in this mode when there are no unsubstantiated blocks, others - as long as the number of remaining blocks is less than the number of transmitted and not more than 20. There is a chemless opinion that it is better to maintain the number of expected blocks of low (1 or 2) to minimize redundancy, and that when Casual requesting a smaller chance to get duplicates of the same block.
Disadvantages and restrictions
· Inaccessibility of distribution - if there are no distributing users (sids);
· No anonymity:
Users of unprotected systems and customers with known vulnerabilities can be attacked.
It is possible to find out the addresses of users who exchange counterfeit content and submit to the court.
· The problem of Lyumbers - customers who distribute much less than download. This leads to a drop in performance.
· The problem of cheaters - users modifying information on the number of downloaded \\ transmitted data.
Personalization - Protocol does not support nicks, chat, viewing a list of user files.
Conclusion
Modern peerbital networks have undergone complex evolution and became in many ways perfect software products. They guarantee reliable and high-speed transmission of large amounts of data. They have a distributed structure, and cannot be destroyed when several nodes are damaged.
Technologies tested in peer-to-peer networks are now used in many programs from other areas:
For high-speed distributions of distributions of open source programs (with open source);
For distributed data networks such as Skype and Jot.
However, data exchange systems are often used in the unlawful sphere: copyright law, censorship, etc. violate. You can say the following: The developers of peer-to-peer networks understood perfectly for which those will be used, and took care of the convenience of their use, the anonymity of customers and the invulnerability of the system as a whole. Programs and data exchange systems often refer to the "gray" area of \u200b\u200bthe Internet - a zone in which the legislation is violated, but to prove the guilt of persons involved in violation or difficult, or impossible.
Programs and network exchange networks are somewhere on the "outskirts" of the Internet. They do not enjoy the support of large companies, sometimes nobody contributes to them; Their creators are usually hackers who do not like Internet standards. Data exchange programs do not like manufacturers of firewalls, routers and similar equipment, as well as Internet providers (ISP) - "hacker" networks are selected from them a significant part of precious resources. Therefore, providers are trying to displace and prohibit data exchange systems or limit their activities. However, in response to this, the creators of the data exchange systems begin to seek countering, and often achieve excellent results.
The implementation and use of distributed systems have not only advantages, but also cons associated with safety features. Get control of such an extensive and large structure, which is the P2P network, or use gaps in the implementation of protocols for your own needs - the desired target for hackers. In addition, the distributed structure is more complicated than a centralized server.
Such a huge amount of resources that are available in P2P networks is hard to encrypt / decrypt, so most of the information about IP addresses and resources of participants is stored and sent in unencrypted form, which makes it available for interception. When intercepting an attacker not only receives information itself, but also learns about the nodes on which it is stored, which is also dangerous.
Only recently in the majority of large networks, this problem has become solved by encrypting packet headers and identification information. Customers appear with SSL technology support, special means of protecting information about the location of resources, etc. are being implemented.
A serious problem is the distribution of "worms" and counterfeit resources for their falsification. For example, the KAZAA client uses the Uuhash hash function, which allows you to quickly find ID for large files even on weak computersBut the opportunity remains for fake files and record a spoiled file having the same ID.
Currently, selected servers and nodes are periodically exchanged by verifying information and, if necessary, add fake servers / nodes into a black list of access blocking.
Work is also underway to create projects, unifying networks and protocols (for example, JXTA - Developer Bill Joy).
Bibliography
1. Yu. N. Gurkin, Yu. A. Semenov. "File sharing networks P2P: basic principles, protocols, security" // "Networks and communication systems", №11 2006
06/02/2011 17:23 http://www.ccc.ru/magazine/Depot/06_11/read.html?0302.htm.
2. A. Rodzunova Napster: History Internet Magazine, Number 22 06/02/2011 15:30 http://www.gagin.ru/internet/22/7.html
3. Modern computer networks Essay 06/02/2011 15:49 http://5ballov.qip.ru/referats/preview/106448
4. 28/01/2011 16:56 http://ru.wikipedia.org/wiki/peer-to-peer
5. http://style-hitech.ru/peer-to-peer_i_tjekhnologii_fajlooobmjena.
PEER-TO-PEER (P2P) technology is undoubtedly one of the most popular topics today. The popularity achieved using such systems as NAPSTER, GNUTELLA, EDONKEY, EMULE, KAZAA and a list of such programs can continue and continue, confirms the potential of peer-to-peer systems. In this review, we will tell us about the R2P technology as a whole, about systems (or correctly speaking) programs involved popularity through this technology. After all, if it is good to look at everything, it can be understood that the R2P technology can serve as an introduction for all new supporters, developers, and just amateurs wishing to develop P2P applications.
What is P2P?
To date, the most common model is CLIENT / SERVER.
In Client / Server architecture, customers poll server, and the server returns the necessary data and produces the necessary operations on them. Today exist different servers In the inet: Web Servers, Mail Server, FTP, etc. The Client / Server architecture is an example of a centralized architecture, where the entire network depends on the central nodes called servers intended to provide the necessary services. Without servers, such an architecture does not make any sense. Regardless of the availability of clients, the network will exist solely with the existence of servers.
Like the Client / Server, P2P architecture is also a distributed model, but there is a very important distinctive feature. In the P2P architecture there is no client or server concept. Each object on the network, call it peer (eng. Equal, the same), has the same status, this means that this object can perform both the client functions (send requests) and the server (receive answers).
And although all Peers have the same status, it does not mean that they must have the same physical capabilities. P2P network may consist of peers with different features, ranging from mobile devices and finishing Mainframes. Some Mobile Peer may not support all server features, due to limiting their resources (weak processor / small memory), but the network does not limit them.
Both network models have their advantages and disadvantages. Visually, you can see that the growth of the Client / Server system (which the more customers are added to it) leads to an increase in the load on the server. With each new client, the central node is weakening. Thus, the network can become overloaded.
P2P network works on another scenario. Each object on the network (Peer) is active on the network, PEER provides some network resources, such as data storage space and additional CPUs. The more peer on the network, the more productivity of the network itself. Consequently, as the network grows, it becomes more powerful.
Additional differences
Also, P2P differs from the Client / Server model in that the P2P system is considered a worker if there is at least one active PEER. The system will be considered inactive if no PEER is active.
Disadvantages of P2P technology
However, there are deficiencies in P2P systems. First, the management of such a network is much more complicated than the CLIENT / Server control with systems where administration requires only the central node - Server. Thus, you need to spend much more efforts to support Security, Backup, and the like.
Secondly, P2P protocol is much more "talkative" - \u200b\u200bPeer can join the network or get out of it at any time, and it can adversely affect performance.
For example:
As a rule, the network consists of equal nodes, and each of them interacts only with some subset of the network nodes, since the establishment of communication "each with each" is impossible due to limited resources (both computing and bandwidth). At the same time, the transfer of information between nodes not related to this moment Immediately, it can be carried out both on a peculiar relay - from the node to the node and by establishing a temporary direct connection. All questions of routing and authorization of messages transmitted by the relay are not on a single server, but on all these individual nodes. Such a definition is also known as PURE P2P. I hope all accumulated questions about what PEER-TO-PEER (P2P) is exhausted. Now we will be brought to your attention on the top 5 programs used by the notorious PEER-TO-PEER technology (P2P).
A bit of history
Many Internet users remember the Napster phenomenon "A, the first worldwide file sharing network between users (by the way, used P2P technol). Napster survived a couple of fate pins, several noisy judicial processes as a result What was soft and fluffy. But "Jean Freebie" already flew out of the bottle ...
Speaking about the "first network of exchange", I, of course, did not mean that before that, people were not exchanged by files over the network. Anyone could send and get a file by mail or lay it out on FTP. But, nevertheless, never before the network shocked such a "wave" of data exchange between users - this wave questioned the foundations of modern show business themselves.
What was a breakthrough in the new technology?
Probably the creation of a giant distributed database containing information "What have anyone." Files were classified by category, so it was possible to produce a more meaningful search. So the system understood - even files with different names can be the same file. At the same time, the system itself sees, who and how much is injected, and connects only to those users that they have parts that you lack you.
The process itself is called peer to peer (P2P), that is, the connection of two users without using the server. Of course, not so "without a server" - in fact, the servers are used in this scheme three times.
The first time is to receive remote users. When connected to the server, you give it a list of files that were identified by you as "common", and in return to get: a) a list of other available (selected) servers; b) List of users who can perform the role of servers.
Another use of servers is the actual search operation. In the original scheme, for example, EDONKEY, the server has a common database of common files for all users. When searching for searching for the server, he determines who from users has the desired file. This scheme has recently comes out of fashion - servers are increasingly containing the search base.
Some servers can limit the number of weak customers or prohibit their connection. For example, in the Overnet system, ID no longer depends on the properties of the client - instead, customers are clearly divided into open and those "for firewall".
What remains from napster "and?
The first thing that rushes into the eyes when you go to www.napster.com, is the installation of the new Napster "A, which is now reminded by the installation of the porn console or another Trojan. I, as it were, I understand that the exe load is no better - But still somehow strange it all looks. The next installation of a funny moment is that Napster works only in the USA. And for American - please register and enter the name and password (as you can see, in America there is a media census. Pirates "). In short - do not go there, there is nothing to do there.
Epidemic KAZAA.
One of the hot pies "one time was Kaazaa. The program and really drank a lot of things useful and her name even became nominative - however, recently the program has become less efficient. In addition, the number of banners and other garbage around this program grows with terrifying speed, so now Kaazaa causes me an association with the words "spam", "pop-up console", "Internet accelerator" ... - and with appropriate cases with emotions.
So, the best programs for today are those that work in the E-donkey2000 and Overnet network. These include their own E-Donkey itself and his cub - overnet (although such jellyfish may occur from the donkey?), As well as the mass of clones. And now, our best five.
1.- The first position was divided by Overnet "Ohm and E-donkey
The difference between Overnet "Ohm and E-donkey - in where file search is selected. If the oldest" donkey "produced a search on a centralized server or, more precisely, in a distributed database on multiple servers (and this is a narrow place - as in the sense of traffic, So in the sense of Interpol) - then the more advanced Overnet is looking only on client machines, although the servers are used for proxy services. On the specified reason for the crowded ED servers, it is recommended to use Overnet, and not e-donkey - although the first, by virtue of its nature, may Load your traffic on the full program. On the other hand, the number of found (accurately rare) files in Overnet strikes. Bad, that it has not been without advertising, but it is solved we know-how.
disadvantages
Disadvantage and EDONKEY and Overnet: The composition of their installation includes several advertising softwareSo, if you do not care this moment and do not cancel the installation of the latter, you will get a handful of garbage to your screw.
2.- At the second position of Emule and other "outstanding"
Among the popular Ed- "Suction" - Emule and OneEmx. They are similar that even a strange feeling is created, as if it is generally the same program. That, in general, it is: the first - Open Source, the second - "type free". The only difference is in the list of default servers. And if Emule, in the end, found a "path to happiness,", then ONEMX could not get out at all - so my knowledge about his work is very modest. Then we will discuss, mainly about Emule, to get which can be (and necessary) on www.emule-project.net. Emule supports two types of network - automatic ED2K and Kademlia Bootstrap. Do not be afraid, this is not a curse, but a distributed hash system - DHT, Distributed Hash Table. The system is working as follows: All users receive identifiers, and files receive identifiers, and portions of files receive identifiers. First you are connected to the pair of "friends" and as if you ask, "and how to go to the library." Since your "Korean" is already aware of the libraries and other institutions, they reset the addresses of new servers where the desired files can be located - and so on, to the victorious end. The promotion process itself is called bootstrap, and the identification system and the search system is only in the light of hash-values \u200b\u200b- Kademlia. In what the chip is that Emule offers you to independently enter the first host address with an emule installed or another Kademila server installed So you can move from it to the next hosts - and gradually get to the required files. It can be said that Emule works and as edonkey, requesting data from servers, and as overnet, through Kademila, - that is, it applies both ways to search. Another question is where you will take this address? That's it. Another "strain" of this technology is that it is necessary to specify a server with a real IP address to "raise", and this is not the connection method too common now, and it will not work for NAT-firewall. But, nevertheless, thanks for the opportunity. Pleasant Emule feature - it stores unchanging files separately, so you do not see the "garbage" at the destination point (as, for example, WinMX). Therefore, the destination point can be specified quite a decent place, for example, "My Documents". Another friend is the opportunity to see the comments to Falu. Unfortunately, they often are stupid, but sometimes contain and important information, for example, "this is a film in Chinese" :-). Among other things, Emule contains the built-in IRC client for live communication with remote "comrades in misfortune" - shorter, full minced meat with butt.
disadvantages
Excessively shipping the system, and not very high download speed.
3.- In the third position WinMX
The tool became very popular recently. His main difference is a complete lack of even a hint of advertising and other nonsense. You can download this mark on www.winmx-download-winmx.com (the injection itself comes from the Morpheus-Download site, which suggests; however, I did not find other information on WinMX and Morpheus - probably people prefer to encrypt).
WinMX - Reduction from "Windows Media Exchange". There is a port on Mac, no ports are not detected for other port systems.
Unlike other P2P clients, WinMX does not show either the list of servers nor the connection process itself. In fact, the average user is extremely rarely extracted from this data some useful information for itself or somehow constructively affect the connection of the connection.
The search bookmark is dedicated to what - everything is clear here: enter words and are looking. After the sources are found, you can postpone them for "Interesting" - although you never guess who will "fuck the file", so discrimination here is inappropriate. It is reasonably clicking the download throughout the group, and not only one source - unnecessary will fall themselves as autumn foliage.
Several incomprehensible cuts you will find on the TRANSFERS tab, namely AFS and AEQ. These are very good parameters. The first means AUTO FIND SOURCES and shows the period (in minutes), what an attempt to find new sources for your files will be performed. Thus, it is possible to "drive" the search engine, and you can, on the contrary, "to climb." It makes no sense to constantly check new sources, they appear not too often - the main thing, never install this parameter in NEVER.
The second parameter is decrypted as AUTO Enqueue - that is, when you find the file and you are offered to be in the queue, in which case agree? For rare files, this parameter can be put in maximum value - 100.
You can configure AFS and AEQ by default on the Configuration tab ... for some reason, search, but not the essence. In other clients there are no such settings (or did I not find it?).
There is a small "pen" in the default settings - you are configured to discard "Inactive DL SOURCES" every 10 minutes. This leads to the fact that at one point you can throw away all sources - and the download will fly away from the list. The file will remain in place, and you, of course, can always "return" downloading by clicking Load Incomplete - but you can only do it with your hands ... in the morning on Monday, whereas you could download all the weekends.
disadvantages
Multifunctionality and a huge number of settings complicates the development of the program by an ordinary user.
4.- At the fourth position of ShareAza or G2.
Shareaza (or, popular, W (s) Araza) is a client created by the authors and fans of the Gnutella network for their own needs :-). Shareaza supports its own Gnutella2 protocol (Mike "S Protocol, MP), the protocol of the old network GNUTELLA 1, ED2K and BITTORRENT. Since MP and BitTorrent have not yet received a special distribution (although, everything can change). Another client supports G2 - MLDONKEY, Others could not be found. What is good - G2 has a formal description, a clear system of requirements and even its own standard, which can make this network sufficiently sustainable for competition with overnet. Side effect ShareAza - Since this client serves requests at once many networks, the outgoing (even When you do not download anything) Traffic can easily "start" up to 25 kb / s! Watch this if you roll out under control. You can limit the download in config-Internet-uploads (default: 7 kb / s for Core, 12 CB / s for partially downloaded and 2 kb for each size of files, large, medium and small - total outgoing outgoing traffic - 25 KB / s).
5.- And finally on the fifth position Gnutella and Bittorrent
The most common and popular exchange network (if not consider ED2K) is called Gnutella. By the way, after the appearance of Gnutella2, it is often called Gnutella 1 or "Old (Legacy) Gnutella". G1 is based on a slightly different query dissemination mechanism - but in principle, all without any special changes. The main difference between Gnutella - it does not use Kademlia mechanisms, that is, the search in this network is carried out "blindly", by random routes. The best criticism G1 is given on the site of the Gnutella 2.D. - there, for example, it is mentioned that in the worst case, one user can "put on the ears" 80% of the entire G1 network.
Official programs for this network - BEARSHARE (also supports ED2K?), Gnucleus, Morpheus (version: Originally was on the Kaazaa - FastTrack engine, but after the "sessions" with the court of Los Angeles passed under the banners Gnutell "s), Xolox Ultra, LimeWare , PEX. Some of them are written in Java, and some even under .Net. Each of these clients exalts itself as "himself": Bearshare - "The Best", Gnucleus - "most honest", and so on.
A typical modern client for the Gnutella - LimeWire network. The entire LimeWare site has been fucked by inscriptions "faster than Kaazaa!" - Hmm, well, it would be known. The main distinguishing feature of this client is a Java program. With all the consequences resulting from this: beautiful and slow.
The program listed above, especially Lime, is often simply oversaturated with advertising, spy-ware and other things, so I mention them only for the completeness of the presentation - you can put these programs in order to familiarize yourself, so as not to say later, you did not have a choice.
In addition, in the GNUTELLA network, I did not find the files you need, so the acquaintance with it ended, and without starting. The only thing that pleased is this website www.gnutella.com (on the Zope + Plone engine?) - Although there all downloads occur through an advertising unit.
BitTorrent This is the technology of distributed file injection files, which is also called Swarming, - that is, the file is going to one piece, just as bees collect honey in the hive. Actually, the BT itself is a server part for download here is this way.
All you need to customize is described here. As you will understand, it is rather a technology than a custom tool - at least programs do not replete with documentation and rich interface.
Guide to action
You know what you need, and are ready to get it in any way. Additional condition - you have a huge channel and you do not pay for traffic. Your actions - you can install in parallel three utilities - WinMX, Emule and Shareaza - they will be swing, as experience shows, from different sources. Of course, you will duplicate the files several times, but your chances of getting them in life will increase significantly. Not threefold, of course (people and servers in all networks often are the same) - but nevertheless.
If you have a paid connection and resources exactly so much to have enough for a "modest luxury" - but the desire is great and at the price you do not stand. Still, once again go through the layouts - what if you find on the disk? Since the specific value of the megabyte will be impressive. Choose Emule, this is the most universal "outstanding" P2P. And precisely, I received the most rare files. If you like a circus and blinking light bulbs - download emule in the "Plus" version.
Other customers, such as WinMX, are also capable of much (it is not scary, advertising consoles are there).
If you really do not have any traffic problems, you can actively use overnet - but be prepared for the fact that the entire network will publish on your node the corresponding fragments on your ID. And this, I tell you, not a joke - at least, be sure to put traffic limiters!
But what do I do not advise anything - it is to put "free" benutless softyns (if, of course, you don't want to remove all your life from the cockroaches's screw). The Gnutella grid itself is not to blame, but the soft packers surprise their arrogance and the desire to make a profit from the open code. Well, and everything is probably writing, knock, and believe that on our sites I have on "promonews", and "SuperQ" you will always get answers to so necessary and important questions. Our motto sounds like this: "Find yourself among friends!" Good luck :)
 Cellular - what it is on the iPad and what's the difference
Cellular - what it is on the iPad and what's the difference Go to digital television: What to do and how to prepare?
Go to digital television: What to do and how to prepare? Social polls work on the Internet
Social polls work on the Internet Savin recorded a video message to the Tyuments
Savin recorded a video message to the Tyuments Menu of Soviet tables What was the name of Thursday in Soviet canteens
Menu of Soviet tables What was the name of Thursday in Soviet canteens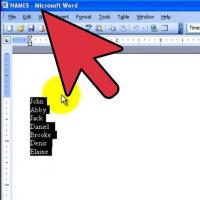 How to make in the "Word" list alphabetically: useful tips
How to make in the "Word" list alphabetically: useful tips How to see classmates who retired from friends?
How to see classmates who retired from friends?