Official information However, centralized file sharing. Piring file sharing network. Read more about GUID
One of the first peerging networks was created in 2000. It still functions, although due to the serious shortcomings of the algorithm users currently prefer the GNUTELLA2 network.
When connected, the client receives from the node, with which he managed to connect, a list of five active nodes; They refer to the search for a resource for a keyword. The nodes are looking for the corresponding resources for the query and, if you do not find them, send the request to the active nodes up on the "wood" (the network topology has the structure of a tree type graph) until there is a resource or the maximum number of steps will not be exceeded. Such a search is called query reproduction (Query Flooding).
It is clear that such a realization leads to the exponential increase in the number of requests and, accordingly, at the upper levels of "wood" can lead to a refusal of maintenance, which was observed repeatedly in practice. The developers have improved the algorithm, entered the rules, in accordance with which requests can send up the "wood" only certain nodes - the so-called dedicated (Ultrapeers), the remaining nodes (Leaves) can only request the latter. The system of caching nodes is also introduced.
In this form, the network operates now, although the flaws of the algorithm and the weak possibilities of expandability lead to a decrease in its popularity.
The shortcomings of the GNUTELLA protocol initiated the development of fundamentally new algorithms for the search for routes and resources and led to the creation of a DHT protocol group - in particular, the Kademlia protocol, which is now widely used in the largest networks.
Requests in the Gnutella network are sent via TCP or UDP, file copying is carried out via the HTTP protocol. IN lately There appeared extensions for client programsallowing you to copy files by UDP, making XML requests for meta-information about files.
In 2003, a fundamentally new GnuTella2 protocol was created and the first customers supporting it, which were reverse with Gnutella clients. In accordance with it, some nodes become concentrators, the others are conventional nodes (Leaves). Each ordinary node has a connection with one or two concentrators. A hub is associated with hundreds of ordinary components and dozens of other hubs. Each node periodically forwards the audio list of identifiers keywordsFor which resources published by this node can be found. Identifiers are saved in the overall table on the hub. When the node "wants" to find a resource, it sends a request to a keyword to its concentrator, the latter either finds the resource in its table and returns the ID of the node that has a resource, or returns a list of other hubs, which the node reappears in turns randomly. Such a search is called a search using the Random Walk.
The noteworthy feature of the GNUTELLA2 network is the ability to reproduce information about the file in the network without copying the file itself, which is very useful in terms of tracking viruses. For transmitted packets, the network has developed its own format similar to XML, flexibly implementing the possibility of increasing the functionality of the network by adding additional service information. Queries and lists ID keywords are sent to UDP concentrators.
Here is the list of the most common client programs for Gnutella and Gnutella2: Shareaza, Kiwi, Alpha, Morpheus, GnuCleus, Adagio Pocket G2 (Windows Pocket PC), Filescope, Imesh, Mldonkey
The work of such networks is based on the equality of participants, that is, there are no dedicated servers in them, and each computer can be both the server and the client. What is the advantage of such an organization? In the fact that the operation of the network does not break, if some node (computer) fails, and you can safely continue to use the network. Moreover, it is completely optional during the day and night to torment the computer with continuous operation, because any network user P2P. May come and leave when he wants.
P2P. Networks are divided by centralized decentralized and hybrid.
The first view is a network in which the service information (still needs an infrastructure to combine scattered clients with each other) store indexing servers. Advantages is a small amount of service information transmitted to the server and simplicity of programming such networks. But the lack still serious - when the indexing servers fails, the network stops working.
IN decentralized Networks There are no such servers, but the amount of service information transmitted is greater. However, there are no ways to force this network to stop functioning.
Well, finally hybrid Networks, which combine the advantages of the first two. They exist indexing servers used to coordinate work, but they do not depend on each other and synchronize the information among themselves. Thanks to this, such networks combine high reliability decentralized Networks and speed centralized.
What should be done to become a member of the file sharing network? First, you need to establish the appropriate type of network file sharing program which is created specifically for downloading files over the network. Then, after connecting to the network, take the file - it can be a program, a music file, a picture, and the like. - And "shake" him, that is, to give it to other users of the network. As a rule, the volume of such files must be several gigabytes, but the size is not limited. Although you do not need to fully share your hDD, especially system folders. Open for general access Directory Other users will not be able to change and delete, they have the ability to download them. Millions of people are "shaking" their files, so everything that has yet to do is to use the search, which is present in the file sharing program and is looking for resources laid out similarly on other network computers. The number of users of file sharing hugely, due to this, the search file will certainly be found. So, it remains only to download found resources, and for free.
It would seem that everything is fine - put the program, look for and download, but there are our pitfalls here. One of them is available for intercepting part of the information about IP addresses and resources of participants, as it is stored and it is sent in unencrypted form. Another problem is the distribution of "worms" and falsification of ID resources for their fake. These issues are solved by various means, but about full security It is too early to talk.
Now let's talk about one of the bright representatives of the decentralized file sharing network type P2P. - Direct Connect. or DCWhat is decoded as a "connection directly". This is one of the most popular networks. P2P. In the world, in many ways because:
- there is a developed multiplayer chat in it.
- the server (hub) can be devoted to a specific subject, for example, a specific film genre, which makes it easier to search for users with the necessary files.
- depending on the client, you can download entire directories, establish restrictions on the minimum volume of shared material, get a list of user files in the form of a tree structure, etc.
In a special program - client for the network DC It is indicated which folders will be available for download, then it connects to a common server in local network And with it, it allows you to see others connected to the server, computers.
Consider the most popular file sharing clients for DC, namely DC ++., APEXDC ++. and FlyLinkDC ++.. All of them are Open Source programs, i.e. open source.
By default, ApexDC ++ supports the English interface. In order to Russify it, you need to download a special Russification file.
Among the features of Apexdc ++ there are such as blocking IP addresses, updating IP addresses at startup, the function of saving the list of unwanted users, chat.
The version is based on StrongDC 2.22which is a modification DC ++., with numerous improvements.
An intuitive interface allows you to set up a program for your taste, it is possible to change the subject of the program design.
Conclusion
Among the considered file sharing clients for networks Direct Connect. It is impossible to allocate some one, all of them are relative, and the differences can be seen by setting any of them on their own computer and looking at what you like, and what you are not.
So, if you want to join the file sharing community, download any of the clients and release more places on the hard disk - now it is exactly useful for you!
What is the file sharing network? This is a collective designation of programs that are necessary for sharing files. The principle of their work is to find and download the necessary resources in free access, which laid out another user.
general information
The file sharing network is a peer-to-one. It is used to exchange files between the participants, which are simultaneously the server and the client. Networks exist by the type of organizations: centralized, decentralized, hybrid. What is the difference?

What is needed for?
The file sharing network is necessary for sharing information via the Internet. With it, you can download music, software, movies, games, and more. File sharing works on the following principle:
- The user downloads the program.
- Opens access to some part of your own resources.
- The downloaded program has a search string that allows you to search for files on resources of other users. They must be designed for free use. Found resources can be downloaded for free.
Torrents are considered a bright example of file sharing. Translated from English means "bitstream". The network is a piring protocol for sharing files between participants. Downloading information occurs in parts. For file sharing exist special programs and BitTorrent networks. They will be described in more detail just below.

Guide to use
How to use I2P network and other file sharing? One of the most popular today is programming programs for the BitTorrent protocol. Distribution may consist of one or more files. Each transmission creates metadata with the extension of the torrent. They contain information about the URL tracker, full information About the file (name, volume) and other parameters. In addition, the amount of the file segments, the user's key, sources that do not work via the protocol are specified. The peculiarity of the torrent is that the load during the distribution is minimal.
In order to download the selected file, you must join the Tarrow at the specified address, report your address and the amount of the file. Next, the user receives addresses of other clients that download the same resource. He needs from time to time to inform the progress of the process to receive updated customer addresses. As a result, there is a constant process of exchanging information of segments. In order for the torrent to work faster, a large number of customers are needed. The exchange of information also depends on the number and size of the segments.

Pros and cons
File sharing network "Fridom" has advantages and disadvantages. The advantages should be able to find any program, software, another resource and download it completely free. Taking into account the fact that users in such systems there are quite a lot, finding even the most exclusive file will not be difficult. When downloading, an SSL protocol is created.
The minuses of file sharing systems include penalties for the use of torrents in some countries. Also for download large number software will need a huge amount random access memory. Many users have difficulty receiving information due to the lack of a "gold" account. In order to purchase full access For file sharing resources, you need to pay a certain amount. In addition, the downloaded files are packed in the archives, so time required for their extraction.

Network
One of the most popular file sharing includes the following programs: Emule, DC ++, LimeWire, Frostwire. Also do not forget about various torrents, among which Azureus, Bitcome, UTorrent. Separate attention deserve private file sharing networks. For example, the I2P network belongs to anonymous. She independently organizes his work. Its feature is that I2P stores hash, encrypted network addresses. Transmitted traffic is encrypted, all messages are protected.
The common features of networks, regardless of their popularity, include the lack of queues for downloading files. All information is distributed by parts, and the exchange of segments is made from one user to another. During the process, the client controls the integrity of the fragments. The user has the ability to simultaneously receive and distribute files. Already downloaded fragments can be handed out again.
The ED2K network is a centralized type of exchanger. Search on it available files help specialized servers that are connected with each other. An independent exchange of information between clients occurs through the MFTP protocol.
File sharing network
Another file transfer method has become more popular - P2P systems such as Kazaa, Edonkey, Gnutella, Direct Connect, etc. In such networks, regular network users exchange files directly connected to each other. The premium of these systems is that the files do not have to be on the same server. At the same time, however, it is impossible to track the contents of these files. That is why these networks got a huge distribution among music lovers, films and especially Warez. The problem of these networks became popular data to which the greatest number of people are drawn. Since the new files literally "lined up", then the download speed decreased in proportion to the number of requests for this file. In addition, in most P2P systems, the number of connections between users are limited, and often users who appealing for any file simply received failure. An incompletely downloaded files were also a problem for users. Acknowledged in advance to determine the "whole" whether the requested file is or not impossible. The result of these problems was the fall in the popularity of many networks and the introduction of prohibitive rules for users participating in them.
File sharing network - the collective name of peer-to-connect computer networks to share files based on equality involved in sharing files, that is, each participant is both the client and the server.
One of the applications of peer-to-peer network technology is file sharing.
Users of the file sharing network lay out any files in T.N. "Shared" (English Share - share) directory, the contents of which are available for download to other users. Some one Another network user sends a search requestany file. The program is looking for network customers files that match the query and shows the result. After that, the user can download files from found sources. In modern file sharing networks, information is loaded immediately from several sources. Its integrity is checked according to the control sums.
Types of File sharing network
Centralized networks
Despite the fact that each partial network participant is both the client and the server, an infrastructure is needed to combine fragmented clients among themselves to a certain community. In centralized file sharing networks, service information store indexing servers.
The advantage of such a network is the relative simplicity of programming such network and a small amount of service information transmitted to servers. Closing Napster and WinMX networks showed unreliability of centralized file sharing networks. Indexing servers can be disabled by different reasons (technical failure, ruin of owning a company, judicial decision). In this case, the network ceases to function. Direct Connect refers to central networks.
Decentralized networks
Decentralized file sharing networks function without indexing servers. Although the volume of the transmitted service information in them is more, their reliability is much higher. So far there is no way to force the functioning of such a network. Decentralized networks include Gnutella, Overnet, Kad.
Partially decentralized (hybrid) network
Combining the speed of centralized networks and reliability of decentralized, hybrid schemes are used in which independent indexing servers are used, constantly synchronizing information between themselves. Thus, when one of them fails, the network continues to function. Partially decentralized file sharing networks include EDONKEY2000, OpenNap.
Work principles
The basic principles of the file sharing are as follows: the user downloads the program to the computer;
Through the Internet, you can easily find people with similar interests and hobbies. If the circle of online communication is limited to several people, then communicate with them is quite simple. This can be done by mail, and through services instant messages. But what if you need to constantly keep a connection with dozens, and then the hundreds of people close to you in the spirit? How to tell them to all that you have photos from the last concert of Richie Blackmore, a list of tickets for the exam or latest version Free tweaker? Not to ask the same question to everyone and wait for you when you answer. Most the best way Solutions to this problem are peer-to-peer networks (Peer-to-Peer Networks, or "Networks with Equal Participants"). A group of people in such a network receives equal access rights to the information available in it, that is, each computer can be both a client and a server. Each of the participants of such a network opens access to specific files on its hard disk, after which they are recorded in the database and become available for download by all users of the network. File sharing is carried out through a program called a peerbear client. There are many peer-to-peer networks, and customers to work even more, because for one network there may be several programs.
The name of this client is decrypted as Direct Connect, that is, a direct connection from one user to another passing server. The DC ++ connection process () is simplified as much as possible: You need to enter your nickname, the mailing address (can be non-existent) and specify the speed of the Internet connection. In the Description field, you can specify any information about yourself: interests, geographical position - in a word, all that you feel necessary.
Habs are usually broken down by topics: music, movies, comics, games, etc. Each hub has its own administrator, which establishes the rules for its use and the minimum amount of open resources, having which can be logged in. In many hubs, they look not only on how many files you share, but also on whether they correspond to the topic of the hub. If you went to a hub dedicated to games, and opened access to windows foldermay and throw away from the system. The use of hubs has its advantages: network members living in one region can be combined into such communities. Many providers charge a much less traffic within a region or country than foreign, and in some packages internal incoming traffic and free. Thus, it is possible to save great, loading everything required files Users who live in your area.
SOULSEEK.
This program is oriented primarily on music files. This does not mean that it does not allow you to download and share files of other types. However, you are interested in the audio file you will find here with a greater probability than, say, game or photo. To share its resources in Soulseek is not necessarily, but, as in all programs of this plan, it is desirable. The fact is that when you start downloading a file from someone from users, he sees who and what he shakes. And it is possible that he will want to see, and what an interesting thing you have. Without finding a single open resource, he can be offended and put you in Ban List, i.e. In the list of users who will never be able to download anything else. The program is very conveniently implemented by the connection settings. You can control the boot speed directly in the file transfer / reception window. Immediately you can determine maximum amount Network participants who can simultaneously transmit the file as well as the number of extra users. The latter are those from the system participants who do not need to stand in a common line to get a cherished file from you. You can make users to an extra-list only you yourself. This is how it turns out that all users are equal, but some "equally" others.
SOULSEEK allows you to exchange not only by files, but also messages. For this there is a chat in which there are many rooms for musical interests. There are rooms for Russian-speaking users - for example, RUSSIA. Russian language is supported. One of the most interesting features of SOULSEEK is an opportunity to put search queries In Wish List. This option works like this: if you did not find anything on a given query, you can put it in this list of wishes. After certain intervals, SOULSEEK itself will search among the files appearing in the network. If a file suddenly finds, the program will immediately inform you about it.
This client is an improved version of the EDONKEY version, which, in turn, is the original client of the eponymous peerge network. For several years of its existence, the EDONKEY network has become incredibly popular worldwide. The EDONKEY client was not designed for such a number of participants, which was the reason for the deterioration of its work - slow download files, errors appear, etc.
 Cellular - what it is on the iPad and what's the difference
Cellular - what it is on the iPad and what's the difference Go to digital television: What to do and how to prepare?
Go to digital television: What to do and how to prepare? Social polls work on the Internet
Social polls work on the Internet Savin recorded a video message to the Tyuments
Savin recorded a video message to the Tyuments Menu of Soviet tables What was the name of Thursday in Soviet canteens
Menu of Soviet tables What was the name of Thursday in Soviet canteens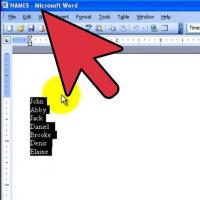 How to make in the "Word" list alphabetically: useful tips
How to make in the "Word" list alphabetically: useful tips How to see classmates who retired from friends?
How to see classmates who retired from friends?