Syn Flood attacks. Protection Linux Server from Syn Flood: Basics and Methods. If nothing helps
Spooofed Syn is an attack at which packet headers are forged in such a way that the place of the real sender takes an arbitrary or non-existent IP address.
Since essentially syn is a frequent tool " intensive competitive struggle"And at the same time, most of the DDOS Mitigation solutions show an impressive efficiency in this form of attacks, then we will start with Syn-Flood, considering the spooofed type of attack as the most formidable of them.
Disclaimers
Disclaimer number 1.
All described in this and subsequent topics - in fact, is not Know-How. All techniques are open, and at anyway (some - from 2003) were published in open sources. I took the work only to reduce them into one and describe " global strategy»Protection-oriented protection system administratorsserving small projects located on highlighted servers (the described strategy can be applied in shared projects, but the implementation will be so exhaust terrible that there is no desire to write about it)Disclaimer number 2.
In the topic not considered Hardware defense solutions - firstly, they are perfectly considered in numerous articles of manufacturers of these very solutions, secondly, projects that have one server cannot often afford them (roughly speaking, the price for working solutions starts from 20 thousand euros), third - The author does not have sufficient data and experience in working with such specialized iron, to make global conclusions about the methods and effectiveness of such protection - it is hardly interesting to someone an overview of decisions from two vendors from a dozen, not supported by serious working statistics of their use. But it is worth noting that both hardware solutions that I had to use are usually very effective on SYN attacks. when performing a number of conditions.Disclaimer number 3.
In the topic not considered Proteaders of protection against DDOS attacks - service engineers of these organizations will be able to describe their work methods better and more. It would probably be worthwhile to make a review of the providers themselves as such - from the client's point of view (at different times, projects in which I participated were clients of Dragonara, Blacklotus, Gigenet, VistNet (currently), ProLEXIC (currently) and A number of sellers of the services of the above companies), but it is knocked out from the Topic Framework, let's try to talk about it later. Again, it is worth noting that all providers of the protection that the author's projects work or worked should cope with the problem of SYN attacks, showing good efficiency.Some mechanics and wikipedia
I would not like to turn the topic into the RFC semblance and quote and so all the well-known truths, therefore, we will confine themselves to the fact that the TCP is interesting from the point of view of the SYN attack and run in the top.First, TCP is one of the most used transport protocols, on top of which most applied protocols are located. Secondly, it has a number of special features (clearly confirmed start and completion of the connection, flow control, etc.) - which make it a relatively complex and resource-intensive.
In the context of the article it is interesting to consider the TCP connection mechanism - a tripartite handshake. In the first approximation at the "Client-Server" level, it looks like this: the client sends the SYN-pack server to which Syn + Ack. Clyient sends an ACK in response to an SYN server and the connection goes into the state of the installed.
SYN attack - sending to an open port of the SYN packet mass, which will not lead to the installation of a real connection for one or another reasons, which entails the creation of "half-open connections" that overflow the connection queue, forcing the server to refuse to maintain to regular customers. Plus, TCP RFC obliges the server to respond to each incoming SYN, which additionally beats both through the server resources and through the data channel. In other words, if you have already come across - in essence - by any DDOS attackers - Described above you know without me. Go to specific recommendations.
One in the field
Use what is at hand, and do not look for another thing - what can be done, being alone with an attack? Honestly, not much, but it happens that there is enough that. This describes what to do with FreeBSD, as in our projects in 90% of cases this system is used. However, the difference will be small from the OS to the OS - the principles are the same.First - It is necessary to access the server (yes, this may also be difficult, especially if the attack is large-scale and / or long-time - the server simply chose all buffers or has a 100% CPU load). Usually, it is enough to close the attacked service of the firewall or simply it - the service is to pay off (however, when an attack is detected, it must be done anyway, at least in order to be able to do something else on the server).
Second - Get the first information about the attack. If you have already been made to monitor incoming traffic - excellent, if not, open the firewall / raise the service and use old-good TCPDUMP and NETSTAT, to find out what attacked and what is the size of the attack in packages per second. Along the way, you can quickly view the networks from which mass requests go - whether they are in a typical audience for your service. All this is useful in the future.
Third - On the interface where the attacked IP address is located only one one should remain. Each alias will reduce system performance. It is expressed in different numbers for different systemsBut these numbers are serious, each Alias \u200b\u200bcan cost additional 2-3 thousand packages per second.
Fourth - If you are using any firewall for incoming traffic on an attacked address - all rules except blocking must be disabled - for example, with Spooofed Syn-Attack the likelihood that SYN-Proxy from PF will help to zero, and CPU It will take very seriously.
Fifth - Configure the system. Miracles here will not be, for them you need a piano in the bushes in the form of prepared drivers and specially purchased network cards, and the only two general recommendations that are seriously reflected in the possibility of receiving SYN attacks have long been known to everyone:
- madify the processing of interrupts on server processors;
- Enable SYN-Cookies and disable SYN-Cache.
The rest of the tuning system will help to squeeze additional 5-10 thousand packages, which in the conditions of the attack is unlikely to be determining. In case, if he is useful to someone - this is the maximum common config (without inclusion of options that require rebeling core or specialized drivers):
Net.isr.direct \u003d 1 kern.ipc.nmbclusters \u003d 400000 net.inet.tcp.nolocaltimewait \u003d 1 net.inet.tcp.recvspace \u003d 16384 net.inet.tcp.sendspace \u003d 32768 net.inet.tcp.msl \u003d 5000 net.inet.tcp.blackhole \u003d 1 net.inet.ip.intr_queueue_maxlen \u003d 3000 net.inet.tcp.blackhole \u003d 2 net.inet.udp.blackhole \u003d 1 net.inet.icmp.log_redirect \u003d 1 Net.inet.IP .redirect \u003d 0 net.inet.icmp.maskrepl \u003d 1 net.inet.tcp.syncookies_only \u003d 1 net.route.netisr_maxqlen \u003d 4096 kern.ipc.maxsockbuf \u003d 83886080 net.inet.ip.intr_queue_maxlen \u003d 10240
The system of the desktop computer configured in accordance with these recommendations:
First # netstat -w1 -h -d input (Total) Output Packets Errs Idrops Bytes Packets Errs Bytes Colls Drops 260k 0 0 15m 230K 0 13m 0 0
The IBM System X3630 M3 level system configured in accordance with these recommendations:
Second # netstat -w1 -h -d input (Total) Output Packets Errs Idrops Bytes Packets Errs Bytes Colls Drops 477K 0 0 36M 457K 0 25M 0 0
Detailed configurations of OS and machines, and, in fact, as we came exactly to them - I will try to tell in the next topic.
One thing is done
What to do in addition to tuning the system in principle, there is something to do.It is worth making a little digression - most hosting companies will help in the fight against attack extremely reluctant, if they are helpful, and in this it is difficult to blame them. But at least they will provide data on the attack - if you have to work with protection providers, this, coupled with the information collected by you during the attack, will greatly facilitate life.
If the hoster caught understanding (what really frequency) - we work according to the following algorithm - Parallel and blocked, block and parallel:
If we have several network cards (if not, we ask to put) - turn them into the LACP mode (for this you have to include similar options on the hoster switch) - this will actually consider the performance increase (separate subtleties of the process we will look later - to argue immense within The topic does not work in any way) we go out to such productivity:
Second # netstat -w1 -h -d input (Total) Output Packets Errs Idrops Bytes Packets Errs Bytes Colls Drops 1.2m 16K 0 65m 1.1m 0 59m 0 0
Please block all unused ports and protocols - the SYN attack may easily change the UDP attack.
Actually any Hosnith company is capable of these actions. But if you were lucky enough to work with a serious company - ask you to block traffic from the region, where most of the audience of your project (for example, China) does not live - usually this means the blexolon announcement for your network for the main providers of a certain region. As a rule, SYN attack is made from Asia, due to the cheapness and mass, and, therefore, such an announcement can seriously help in the fight against the attack or even exclude its possibility.
In addition to the measures described above, you can advise to use Geodns-Like service - under certain conditions (the attack is carried out on a domain, for example) it will work similarly to the announcement of blexol for certain networks.
Finally
I hope the article will help you cope with the problem of SYN-Flud, not exceeding the annual budget of any African country. Of course, only the most general recommendations are given here, but believe me - in 90% of cases, they are quite enough. And most importantly - don "T Panic!UPD. The continuation is in the stages of writing, and will soon be laid out here. Stay with us!
11.11.2012
Near Floom.it is understood by a huge flow of data in the form of messages, which is sent to accommodate on all sorts of forums and chats. If you look at the technical point of view, flood. - This is one of the most common. species of computer attack, and his goal is to send such a number of requests that the server equipment will be forced to perform failure to service user services. If a attack on computing equipment It is carried out with a large number of computers, then you are dealing with.
There are several types of DDoS attacks with floods, the main of them are listed below:
- SYN-ACK-FLUD
- Http-flood
- ICMP-flood
- UDP-flood
SYN-ACK-FLUD
SYN-ACK-FLUD - one of the types network attackswhich is based on sending a huge number of SYN queries per unit of time. The result will be the failure of the service whose work was based on the TCP protocol. At first, the client will exchange a package containing the SYN flag, the presence of which indicates the desire to establish a connection. The server, in turn, sends a package. In addition, except the SYN flag, there is an ACK flag that pays the client's attention to the fact that the request is accepted and confirmed confirmation of the establishment of a client's connection. He responds with a package with ACK flag about a successful connection. All requests for "Connect" from customers Server stores in line of a certain size. Requests are stored in the queue before returning from the ACK Flag client. The SYN attack is based on sending a packet server from a non-existent source, the amount exceeds the size of the queue. The server simply will not be able to respond to the package on the fictional address. The queue will not decrease and the service will stop functioning.
Http-flood.
Http-flood. - applies in case of service with database. Attack is aimed either on web server.Or on the script working with the base. Heading off great amount GET requests to 80 ports, so that the Web server was unable to pay due attention to the requests of another type. Log files increase, and working with the database becomes impossible.
ICMP-flood
ICMP-flood - simple way reducing throughput and increased loads On the stack by means of sending the same type of ICMP Ping requests. Dangerous in case of small pay attention network screensSince the server responding to Echo infinite requests is doomed. So in the case of the same number of incoming and outgoing traffic, simply register the rules in iPTABLES..
UDP-flood
UDP-flood - Another way claim bandwidthbased on working with a protocol that does not require synchronization before sending data. The attack comes down to the usual premise package on the UDP server port. After receiving the package, the server begins to process it hard. The client sends the UDP packets of incorrect content one by one. As a result, the ports will no longer function and the system will fail.
In principle, to determine type DDoS attack Often it is not necessary to spend a lot of time. It is enough to know several signs. If significant the size of the Log File has increased - You deal with Http-flood. If a limited access to the service As a result of exceeding the number of permissible connections - this SYN-ACK-FLUD. If outgoing and incoming traffic is approximately equal - You deal with ICMP-Flud.. The main thing is not to forget to maintain safety of its server From DDOS and give her due attention. The best is to take care of
A Syn Flood Is a Form of Denial-of-Service Attack in Which An Attacker Sends A Progression of Syn Requests to An Objective's Framework Trying to Consume Enough Server Assets to make the Framework Inthentic Activity.
TCP Three-Way Handshake
TYPICALLY, WHEN A CUSTOMER BEGINS A TCP CONNECTION WITH A SERVER, THE CUSTOMER AND SERVER TRADE A PROGRESSION OF MESSAZ WHICH REGULARLY RUNS THIS WAY:
1) The Customer Asks for a Connection by Sending A Syn (Synchronize) Message to the Server.
2) The Server Recognizes This Request by Sending Syn-Ack Back to The Customer.
3) The Customer Reacts with An Ack, And The Connection Is Built Up.
This Is Known As The TCP Three-Way Handshake, and Is The Establishment for Each Connection Set Up Utilizing The TCP Protocol.
Working of Syn Flood Attack
A SYN Flood Attack Works by Not Reacting to The Server with the Normal Ack Code. The Pernicious Customer Can Either Basically Not Send The Normal Ack, Or by Satirizing The Source IP Address in the Synic, Bringing Abyde The Server to Send The Syn-Ack to A Distorted IP Address - Which Won't Send An Ack On The Grounds That IT "KNOWS" THAT IT NEVER SENT A SYN.
The user Will Sit Tight for the Afirmation for Quite A While, As Straightforward System CLOG COULD LIKEWISE BE THE REASON FOR THE MISSING ACK. In Any Case, in An Attack, The Half-Open Connections Made By The Pernicious Customer Tie Resources on The Server And May In The Long Run Surpass The Resources Accessible on the Server. By then, The Server Can't Be Access by Any Customers.
Security AGAINST SYN Flood Attacks
There Are Various Surely Understood Countermeasures Including:
1) Filtering
2) Increasing Backlog.
3) TCP Half-Open:The Term Half-Open Alludes to TCP Associations Whose State Is Out of Synchronization Between The Two Potentially Because of An Accident On One Side. A Connection Which Is Being Set Up Is Otherwise Called a Embryonic Connection. The Absence of Synchronization Could Be Because of Malignant Purpose. A TCP Connection IS Allounded to As Half-Open When The Host Toward One Side of That Tcp Association Has Slammed, Or Has Generally Evacuated The Attachment Without Informing The Flip Side. In The Event That The Association May Stay in The Half-Open State for Unbounded Time Frames. These Days, The Term Half-Open Association IS Regularly Used to Portray An Embryonic Connection, I.E. A TCP Connection Which is Being Set Up.
The TCP Convention Has a Three State Framework for Opening a Connection. To Begin With, The Beginning Endpoint (A) Sends a Syn Bundle to the Destination (B). A IS Currently In An Embryonic State (Particularly, Syn_Sent), And AntiCipating A Reaction. B NOW REDESIGNS Its Portion Data to Demonstrate The Approaching Connection From A, and Conveys a Request to Open a Channel Back (The Syn / Ack Bundle). Now, B is Additionally in An Embryonic State (Particularly, Syn_RCVD). Note That B Was Put Into This State by Another Machine, Outside of B's \u200b\u200bControl.
Under Typical Conditions (See ForesWearing Of-Administration Attack for Conscious Disappoint Cases), a Will Get The Syn / Ack from B, Overhaul Its Tables (Which Now Have Enough Data for A to Both Send and Get) and Send A Last Ack Back To B. WHEN B GETS THIS LAST ACK, IT ADDITIONALLY HAS ADEQUATE DATA FOR TWO-WAY CORRESPONDENCE, AND THE CONNECTION IS COMPLETELY OPEN. Both Endpoints Are Currently in An Established State.
4) Firewalls and Proxies
5) Reducing Syn-Received Timer
6) SYN CACHE
7) Recycling the Oldest Half-Open TCP
8) Hybrid Approaches
9) Syn Cookies:Syn Cookie IS A Strategy Used to Oppose Syn Surge Assaults. Daniel J. Bernstein, The Procedure's Essential Creator, Characterizes Syn Treats AS "Specific Decisions of Beginning TCP Arrangement Numbers by Tcp Servers." The Utilization of Syn Treats Permits a Server to Abstain from Dropping Associations When The Syn Line Tops Off. Rather, The Server Carries On As Though The Syn Line Had Been Amplified. The Server Sends Back The Suitable Syn + Ack Reaction to the Customer Yet Disposes of the Syn Line Section. In The Event That The Server Then Gets a Resulting Ack Reaction From The Customer, The Server Can Reproduce The Syn Line Section Utilizing Data Encoded As A Part of the TCP Succession Number.
If You Need Any Further Assistance Please Contact Our Support Department.
Do you really think you know everything about DOS? Then read!
DENIAL-OF-SERVICE (DOS), attacks of refusal, have become more dangerous and easier. DOS is a variety
Network attacks (from worms to SYN Flooding), the purpose of which to make the server is not available to users. 'DISTRIBUTED REFLECTION' This is a new kind of DOS attacks using SYN Flood "a. Its feature is that millions of SYN packets are not sent to the attacked server, they are sent to the router" s or server and the answer comes to the target server. BUT
Routers There are millions!
To understand how it all works and why it is so important
Let's remember something ... Confirmation TCP connections occurs by sharing three packages between two
Computers, so-called handshake. Here is an approximate scheme:
- SYN client (Web browser, fTP client, etc.) enters communication with the server, sending him an SYN package.
- SYN / ACK: When a connection request (SYN package) is obtained on open Porta Servers, he confirms the connection by sending the SYN / ACK client to the package.
- ACK: When the client receives a confirmation of the SYN / ACK server package for expected communication, then responds by ACK package.
What's happening?
Traditional "SYN Flooding DOS" Attacks work on two principles:
- "One-on-one" One machine refers sufficient SYN packages to block access to the server.
- "Many-On-One" many zombie programs,
Installed on different servers, attack the target machine SYN packages.
Using "REFLECTION SYN Flooding" packages are sent,
But with the source IP address indicating the target machine. TCP connection using these three packages requires any TCP service that receives a SYN package replied by SYN / ACK package. Server or Router that gets these fake SYN packages send SYN / ACK answers to the machine specified by SYN packages with the source address
IP. Primary Internet and Infrastructure Protocol
Networks are used themselves against themselves!
In details
Any TCP Communication with a general purpose server can be used to "reflect" SYN packets. Here
Short list of the most popular TCP ports:
22 (Secure Shell), 23 (Telnet), 53 (DNS) and 80 (HTTP / WEB). And actually Router "on the whole Internet will be confirmed by TCP communication on
179 port. Let's estimate the potential of this attack:
- It uses the fundamental Internet communications protocol;
- Machines that use this protocol, there are millions;
- extremely easy to organize an attack 'Syn Packet
Reflectors'.
It can be quite easy to build a list,
in which rauters will be listed and
Servers that respond to SYN packages. Having
Large list of SYN "reflectors", each
Hacker can distribute fake syn
Packages evenly through the whole set
routers / servers in the list. None of the innocent "reflectors" will not experience
substantial network load. Routers do not save reports on packages with requests for
pre-connection, it does
The attack tracking is extremely difficult.
"Reflectors" (routers and servers) will be sent at three or four times large quantity SYN / ACK packages than the number of SYN packets that they
get. TCP connection that receives the command
SYN, awaits ACK response from the car to which he sent
SYN / ACK Package, so the computer is sent to another SYN / ACK responses in a few minutes. This feature of the TCP protocol is essentially multiplies by the number of malicious SYN / ACK packets sent to the target machine to three or four. It also means that Flood Syn / Ack
Packages will continue to attack the target server for a minute or
Two even after the attacker recalled the attack.
Syn Flood Attack Is a Form of Denial-of-Service Attack in Which An Attacker Sends a Large Number of Syn Requests to a Target System's Services That Use TCP Protocol. This Consumes The System Resources to make the System UnreSponsive to Even Legitimate Traffic. This Attack Can Occur on Any Services That Use TCP Protocol But Mainly On Web Service. In This Tutorial, We Will Go Through The Basics of Syn Flood Attacks and The MiTigation Steps in Detail.
The Syn Flood Attack Exploits An Implementation Characteristic Of The Transmission Control Protocol (TCP), Which is Called 3-Way Handshake. Following Are The Steps That Occur in a Normal 3-Way Handshake:
1. The Client Requests a Connection by Sending a Syn (Synchronize) Message To the Server.
2. The Server Acknowledges This Request by Sending Syn-Ack Back to the Client.
3. The Client Responds with An Ack, and the connection is easyblished.
A Syn Flood Attack Works by Not Responding to The Server with the Expected Ack Code. By These Half-Open Connections, The Target Machines TCP Backlog Will Get Filled Up and Hence All New Connections May Get Ignored. This Will Cause The Legitimate Users to Also Get Ignored.
This Attack Can Take Place in Two Ways:
1. Direct Attack
In this Kind of Attack, Attackers Rapidly Send Syn Segments with off Spoofing Their IP Source Address. When Detected, This Type of Attack Is Very Easy to Defend, Because We Can Add a Simple Firewall Rule to Block Packets with the attacker "S Source IP Address Which Will The Attack.
2. Using IP Address Spoofing
This is a more Complex Form of Attack the Direct Attack. In This Method, The Malicious Machine Will Send Syn Request Floods to the Target Machine From Spoofed IP Addresses, Causing The Server to Send the Syn-Ack to A Falsified IP Address - Which Will Not Send An Ack Because It "Knows" That It Never Sent a Syn.
Detecting Syn Flood Attack
The Generic Symptom of Syn Flood Attack to a Web Site Visitor Is That A Site Takes A Long Time to Load, OR Loads Some Elements of a Page But Not Others. If you suspect a syn flood attack on a web Server, You can Use to Check the Web Server Connection Requests That Are in "Syn_Received" State.
netstat -tuna | Grep: 80 | grep syn_recv
If IT SHOWS NUMEROUS Connections with this state, The Server Could Be under Syn Flood Attack. If The Attack Is Direct With Large Number of Syn_Recv Packets From A Single IP Address, You Can Stop This Attack by Adding That IP Address in the Firewall. If You Have APF OR Firewall Installed On Your Server, You Can Accomplish this by Executing The Following Command:
aPF -D iPaddress
csf -d ipaddress
Defending Syn Flood Attack
Using Syn Cookies
This Is The Most Effective Method of Defending From Syn Flood Attack. The Use of Syn Cookies Allow A Server to Avoid Dropping Connections When The Syn Queue Fills Up. Instead, The Server Behaves AS If The Syn Queue Has Been Enlarged. The Server Sends Back The AppropriTe Syn + Ack Response to the Client But Discards The Syn Queue Entry. If The Server Then Receives A Subsequent Ack Response from the Client, It is Abynd to Reconstruct The Syn Queue Entry using Encoded in the TCP Sequence Number.
Syn Cookies CAN BE Enabled by Adding the followinging to /etc/sysctl.conf
net.ipv4.tcp_syncookies \u003d 1.
After Modifying The Sysctl Configuration File, You Need to Execute The Following Command to Load SysTl Settings from the file /etc/sysctl.conf
Increasing The Syn Backlog Queue
An Optional Defending Technique Is To Increase The Sys Backlog Queue Size. The Default Size IS 1024. This Can Be Done by Adding The Following To /etc/sysctl.conf
net.ipv4.tcp_max_syn_backlog \u003d 2048.
Reducing Syn_ack Retries.
Tweaking The Kernel Parameter TCP_SYNACK_RETRIES CAUSES The Kernel To Close The Syn_Recv State Connections Earlier. Default Value IS 5.
net.ipv4.tcp_synack_reTries \u003d 3.
Setting Syn_Recv Timeout.
Lowering The Timeout Value for Syn_Recv Will Help in Reducing The Syn Flood Attack. The Default Value IS 60 and WE Can Reduce IT to 40 OR 45. This Can Be Done by Adding The Following Line to Sysctl.conf.
net.ipv4.netfilter.ip_conntrack_tcp_timeout_syn_recv \u003d 45.
Preventing IP Spoofing
The Following SYSTL PARAMETER WILL HELP TO PROTECT AGAINST IP Spoofing Which Issed for Syn Flood Attacks.
net.ipv4.conf.all.rp_filter \u003d 1.
Many Hosting Companies Provide Protection Against Syn Attack by Deploying Firewalls That Employ Syn Flood Defense Such As Netscreen or Appsafe.
 How to pay a domain name
How to pay a domain name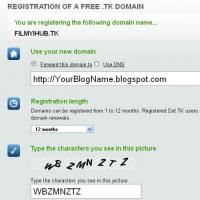 Domain zone of tokelau islands
Domain zone of tokelau islands What is domain what problems may be
What is domain what problems may be Yandex Wordstat: detailed instructions for using the service and grouping operators and a complicated request
Yandex Wordstat: detailed instructions for using the service and grouping operators and a complicated request Editing DBF files
Editing DBF files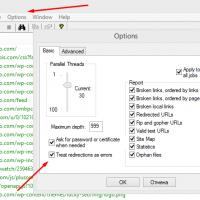 Xenu Link Sleuth - What is this program how to use the Xenu program
Xenu Link Sleuth - What is this program how to use the Xenu program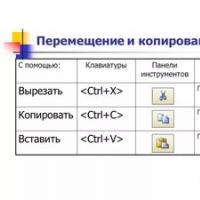 Methods Copy and insert text from keyboard without using mouse
Methods Copy and insert text from keyboard without using mouse