Development and design of a local computing network for an organization with two office and warehouse. Informatics Programming: Coursework: Designing a local computing network Design of a distributed local computing network
Today there is a gradual increase in the number of Internet users, which will certainly require the correct organization of local networks. Through the use of modern technologies, data transmission between individual computers can be easily ensured, which are established within the framework of a separate enterprise, a commercial organization. It is worth noting that on each of the possible stages of creating this line of communication, a full design is necessarily performed. It is important to note the fact that such computing networks can be born, both through a wired and wireless method, each of which has some individual features and characteristic features.
Stages of design work
What stages highlight the design of the local computer network? In this case, it is necessary to allocate the following:
- Primary study of features and procedures for conditions provided for for various computing networks. It is worth noting, at this stage the possibilities and prerequisites for creating a specific network indoors, an office, a separate structural unit are analyzed;
- Development of a technical task, which is performed by the head of the organization, commercial structure. It is worth noting, at this stage you can use specific recommendations of specialists, this will be the best result;
- Preparation of equipment, as part of this stage, actual operational abilities are required, various functionality. Preparation checks not only practical performance, but also a number of features and opportunities to use aggregates;
- Specialists are carried out by high-quality and operational installation of the appropriate LAN, which is carried out exclusively on the design technology. Certain conditions are created for the subsequent operation of the network, when the equipment used is installed, the wizard will configure it;
- Finally, a warranty is provided (and in some cases post-warranty service). This is done by preliminary agreement with the potential customer of the service, but experts will be able to solve this issue without any problems, providing the customer with everything necessary.

Properties of local networks, to pay attention to
By designing a local computing network of the organization, it will be necessary to pay attention to the following properties of the communication line, which will allow to maximally solve the issue of employee interaction:
- The possibility of scalability, which is one of the most important properties relevant with subsequent design. Directly at the initial stage of creating an organization, the system must necessarily meet all the necessary tasks, goals set before the Communication by the heads of the structural unit. It is necessary to take to attention the fact that the possibility of subsequent network expansion is taken into account so that in the future you can easily connect numerous additional equipment into the scheme;
- Flexibility, the network should respond quickly enough to possible requirements, be sure to adapt to various types of network cables. What is noteworthy, in the general concept of "flexibility" also includes special support for numerous technologies, for example, from the same Ethernet, Fast Ethernet, Gigabit Ethernet, which allows you to use all possible lines of communications without any problems and must ensure the creation of all the necessary terms of full-fledged work;
- High resistance to failures, problems with playback and data transfer. This is a characteristic advantage that can only be provided in the design process. There is a similar condition only subject to the use of numerous backup lines, which are used directly in situations where the main elements may fail. There is an option when the server can connect to concentrators, among whose advantages is also noted for spare ways. If the network has one concentrator failure, you can always try to switch to another. This can be done exclusively in automatic mode, while the communication session is not interrupted, which will become an excellent solution for the full organization of the work of the enterprise, a commercial structure, a separate object;
- Reliability, this parameter must be taken to attention the design of the local café branches, carried out in order to control the work of structural units. In this aspect, you need to look for options that will allow a long period of time to operate the network, without the need to fulfill its maintenance, additional settings. It is important to understand that the long-lasting ease of the network is expelled quite expensive, it is for this reason that it is necessary to look for the optimal option, numerous tools that can significantly increase the overall reliability of the system;
- Protection criteria, which today is given significant attention. In kind, it is security that can be a prerequisite for the subsequent guarantee, the most efficient work of a particular organization, a company, its department. With proper design of a particular network, the system is required to ensure the security of the system, it is reduced to a minimum of the probability of refusal, but the main thing is unauthorized access to the operation of the equipment. It is accepted for the fact that such access can be carried out from the inside of the organization, as well as outside when the cracker is at a distance from the company. It should be noted that the presence in the ordinary password system will not provide it as a reliable guarantee and protection, for this reason, for the subsequent increase in the equipment reliability indicator, the creation of optimal conditions for its operation, a certain level of the hub is assigned, using a switched connection, router. Remote access servers are actively used, by means of which the maximum system security is ensured from penetration. In the same way, the maximum level of control over the operation of the network is also provided, it is possible to verify even the most remote computers;
- The latter, but no less important parameter, which should ensure the design of the locally computing office network, is the handling of this communication line. For example, it is being worked out the possibility of creating enough powerful modern monitoring tools, which is typical for the operational diagnosis, eliminate possible problems in the system. Thus, the downtime of the system and equipment is eliminated in the work, which were mentioned somewhat higher.
It will not cause problems when experts are called to fulfill the task. The cost of such an operation is established individually.
Large companies have in circulation a large amount of different data:
- text files;
- graphic;
- images;
- tables;
- schemes.
For manual, it is important that all the information has a convenient format, easily converted and passed on any carrier in the necessary hands. But paper documents have long begun to be changed digitized, as the computer may contain a variety of data with which it is more convenient to work with the help of automation of processes. It also contributes to the movement of information, reports and treaties to partners or verifier companies without long movements.
So there was a need for the ubiquitous supply of departments by firms with electronic computing devices. At the same time, the question arose about connecting these devices into a single complex to protect, preservation and ease of movement of files.
In this article we will tell you how to facilitate the design of a local computing (computer) network in the enterprise.
What is LAN, its functions
This is a binder connection of a number of computers in one closed space. Often this method is used in large companies, in production. You can also independently create a small connection of 2 - 3 devices even at home. The more inclusions in the structure, it becomes more difficult.
Types of compilation of networks
There are two types of connectivity, they differ in complexity and availability of steering, central links:
- Equal.
- Multi-level.
Equimcons, they are peer, characterized by similarity in technical characteristics. On them there is the same distribution of functions - each user can gain access to all common documents, make the same operations. Such a scheme is easier in management, it does not require multiple efforts to create it. The minus is its limitations - no more than 10 members can enter into this circle, otherwise the overall efficiency of work is disturbed, speed.
The server design of the company's local network is more time-consuming, however, in such a system above the level of information security, as well as a clear distribution of responsibilities inside the web. The best technical characteristics (powerful, reliable, with greater RAM) computer is assigned by the server. This is the center of the entire LAN, it is stored here all the data, from the same point you can open or stop accessing documents to other users.
Computer network functions
The main properties that need to be taken into account in the preparation of the project:
- Ability to connect additional devices. Initially, several machines may be in the grid, with the extension of the company, you may need additional inclusion. When calculating power, it is worth paying attention to, otherwise you will need to redecessing and buy new consumables of increased strength.
- Adaptation for different technologies. It is necessary to ensure the flexibility of the system and its adaptability to different network cables and different software.
- Availability of backup lines. First, this refers to the points of the ordinary computers. If you fail, you should be able to connect another cord. Secondly, it is necessary to ensure the uninterrupted operation of the server with a multi-level connection. This can be done by providing an automatic transition to the second hub.
- Reliability. Equipment uninterrupted, autonomous energy reserves to minimize the possibility of interruption of communication.
- Protection against extraneous influences and hacking. The stored data can be protected not just a password, but a whole bundle of fixtures: a hub, switch, router and remote access server.
- Automated and manual control. It is important to establish a program that will analyze the state of the grid at each time and notify the faults to quickly eliminate them. An example of such software - RMON. This can use personal monitoring through Internet servers.
Drafting technical requirements for the design and calculation of the local network (LAN) in the enterprise
From properties, the conditions that need to be taken into account in the preparation of the project are out. The entire design process begins with the preparation of the technical task (TK). It contains:
- Norms on the safety of information.
- Providing all connected computers access to information.
- Performance Parameters: reaction time from user request before opening the desired page, bandwidth, that is, the amount of data in the operation and transmission delay.
- Terms of reliability, that is, the readiness of a long, even constant work without interruptions.
- Replacement components - extension of the grid, additional inclusions or installation of equipment of other power.
- Support for different types of traffic: text, graphics, multimedia content.
- Ensuring centralized and remote control.
- Integration of various systems and software packages.
When the TK is drawn up in compliance with the needs of users, the type of inclusion of all points into one network is selected.
Main topology LAN
These are methods of physical connection of devices. The most frequency are three figures:
- tire;
- ring;
- star.
Tire (linear)
When assembly, one drive cable is used, the wires to user computers are already departed. The main cord is directly connected to the server that stores information. It also occurs selection and data filtering, providing or restricting access.

Benefits:
- Turning off or problem with one element does not violate the actions of the rest of the mesh.
- The design of the local network organization is pretty simple.
- The relatively low cost of installation and consumables.
Disadvantages:
- Failure or damage to the carrier cable stops the operation of the entire system.
- A small plot can be connected in this way.
- Speed \u200b\u200bmay suffer from this, especially if the connection passes between more than 10 devices.
"Ring" (ring)
All custom computers are connected sequentially - from one device to another. So often do in the case of peer-to-peer LAN. In general, this technology is applied less and less.

Benefits:
- No hub costs, router and other network equipment.
- Several users can immediately transmit information.
Disadvantages:
- The transfer rate in the entire grid depends on the power of the slower processor itself.
- In case of failures in the cable or in the absence of connecting any element, a common work is terminated.
- Customize such a system is quite difficult.
- When connecting an additional workplace, it is necessary to interrupt the overall activity.
"Star"
This is a parallel inclusion of devices to the network to a common source - server. Like the cent is most often used hub or hub. All data is transmitted through it. In this way, not only computers, but also printers, faxes and other equipment can be carried out. In modern enterprises, this is the most frequency applied method of organizing activities.

Benefits:
- Easy to connect another place.
- Performance does not depend on the speed of individual elements, so it remains at a stable high level.
- Just find breakdown.
Disadvantages:
- Malfunction of the central instrument stops the activities of all users.
- The number of connections is due to the number of the ports of the server device.
- A lot of cable is spent on the grid.
- Highness equipment.
Stages of software design LAN
This is a multi-stage process that requires the competent participation of many specialists, as it should be pre-calculated the necessary bandwidth of the cables, take into account the configuration of the premises, install and configure the technique.
Planning the premises of the organization
Capabilities of workers and bosses should be positioned in accordance with the selected topology. If the shape of the star is suitable for you, then you should put the main technique in that room, which is main and is located in the center. This may be the office of the leadership. In the case of bus distribution, the service may be located in the indoor remote area.
Building a local network scheme

The drawing can be made in specialized automated design programs. The products of the company "ZvSoft" are ideal - they contain all the basic elements that will be required when constructing.
The grid must consider:
- maximum voltage;
- sequence of occurrences;
- possible interruptions;
- installation efficiency;
- convenient electricity supply.
The characteristics of the LAN must select according to the plan of the organization's premises and the equipment used.
Parameters of computers and network devices
When choosing and buying mesh elements, it is important to take into account the following factors:
- Compatibility with different programs and new technologies.
- Data transfer and speed of devices.
- The amount and quality of cables depends on the selected topology.
- Method of network exchange method.
- Protection against interference and failure of wire winding.
- Cost and power of network adapters, transceivers, repeaters, hubs, switches.
LAN design principles using computer programs
When drawing up a project, it is important to consider a large number of nuances. This will help the software from ZWSoft. The company is developing and selling multifunctional software to automate the work of engineers-designers. Basic CAD is an analogue of the popular, but expensive Autodesk - AutoCAD Covenant, but surpasses it in ease and convenience of licensing, as well as on a more loyal pricing policy.

Advantages of the program:
- An intuitive, convenient interface in black color.
- Wide tool selection.
- Work in two-dimensional and three-dimensional space.
- 3D visualization.
- Integration with the files of most popular extensions.
- Organization of LAN elements in the form of blocks.
- Count lengths of cable lines.
- Visual location of elements and nodes.
- Simultaneous work with graphics and text data.
- The ability to install additional applications.
For ZWCAD - a module that expands the functions of the basic scope in the design of multimedia schemes. All drawings are performed with an automated calculation of the cables of the local computing network and their marking.
Benefits:
- automation of the selection of switching systems;
- wide library of elements;
- parallel filling of the cable log;
- automatic creation of specifications;
- adding equipment to the library;
- simultaneous operation of several users with a database;
- schematic markers for the location of devices and furniture items.
It will help to make a project in bulk form, create it in 3D. Intelligent tools allow you to quickly parse the LAN tracks to the connection points, clearly present the locations of the cables, organize the crossing of the lines, perform the cuts of the connected equipment and technological furniture (including in dynamic mode). Using the component editor, you can create a library as cabinets, switching apparatuses, cables, clamps, etc., as well as assign them the characteristics based on which in the future you can create specifications and calculation. Thus, the functions of this software will help complete the General Plan of the Organization's premises with the trace of all LVS lines.
Create a project of a local computing network in your enterprise, together with Zvsoft programs.
Federal State Budgetary Educational Institution
Higher professional education
Ural State University of Communications
Department of "IT and Zi"
Course project
On the topic: "Designing LAN enterprises"
Performed Parshin K.A.
Checked: Ph.D. Associate Professor Art. c. IT-311.
Akhmetgareyev K.Yu.
Yekaterinburg, 2013.
Introduction
Local computing network
Channel level of the OSI model
Computer location scheme
Calculation of the total cable length
Ethernet frame formats
SIP protocol
Switters
Routing
Multiservice. IP - Telephony, SIP, H.323
Distribution of IP addresses for LAN.
Software and hardware
Calculation of the estimated cost
Conclusion
Bibliography
Introduction
The local computing network is a set of switching nodes and communication lines providing network user data transfer. Therefore, requirements can be divided into two parts:
requirements for switching nodes
requirements in communication lines
The purpose of any design is the choice of the option most fully satisfying the requirements of the customer.
Designing the local computing network (LAN) of the enterprise for information support for the interaction of departments on the floor of the production building (Appendix 1) taking into account the source data:
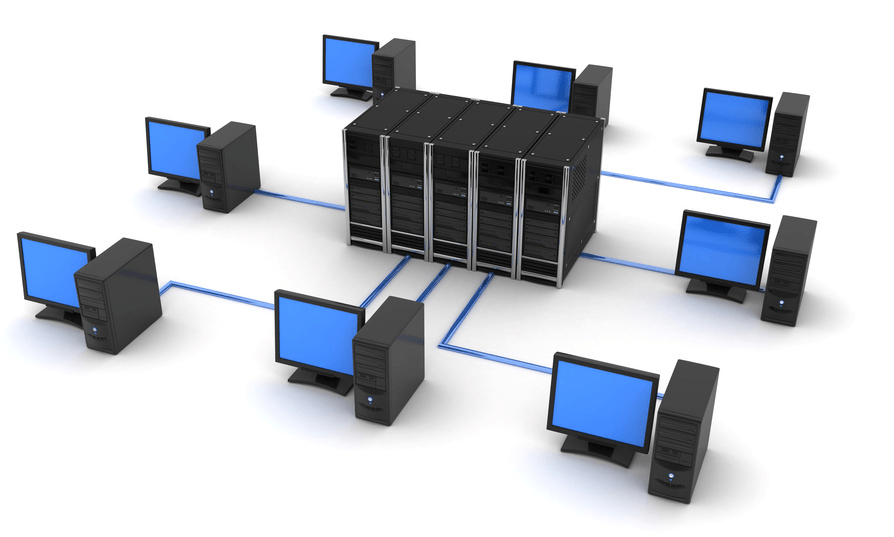
1. Local computing network
Local computing network (LAN, local network; English. Local Area Network, LAN) - a computer network that covers usually relatively small territory or a small group of buildings (house, office, firm, institute). There are also local networks, the nodes of which are geographically separated at a distance of more than 12,500 km (space stations and orbital centers). Despite such distances, similar networks are still referred to as local.
Computers can be connected with each other using various access media: copper conductors (twisted pair), optical conductors (optical cables) and through radio channels (wireless technology). Wired, optical connections are installed via Ethernet, wireless - via Wi-Fi, Bluetooth, GPRS and other means. A separate local computing network may communicate with other local networks through gateways, as well as be part of a global computer network (for example, Internet) or have a connection to it.
Most often, local networks are built on Ethernet or Wi-Fi technologies. To build a simple local network, routers, switches, wireless access points, wireless routers, modems and network adapters are used.
Local network technology implements, as a rule, the functions of only the two lower levels of the OSI model - physical and channel. The functionality of these levels is enough to deliver frames within standard topologies that support LAN: Star, total tire, ring and wood. However, it does not follow from this that computers associated with the local network do not support the protocols of the levels above the channel. These protocols are also installed and operate on the nodes of the local network, but the functions performed by them do not relate to the LAN technology.
LAN protocols.
In LAN, it is not required to provide most of the functions, so the functions performed are divided between the physical and channel levels, and the channel level is split into two subcoels: control of access to the environment (MAC) and logical channel control (LLC).
In the LAN, twisted pair, coaxial cable and fiber optic cable are used as cable transmitters.
The main characteristics of the LAN:
The territorial length of the network (the length of the total communication channel);
Maximum data transfer rate;
The maximum number of the network on the network;
The maximum possible distance between the workstations on the network;
Network topology;
View of the physical data environment;
Maximum number of data channels;
The subscriber access method into the network;
Network software structure;
The possibility of transmitting speech and video signals;
Conditions of reliable networking;
The possibility of communication LANs with each other and with a higher level network;
The ability to use prioritization procedures while connecting subscribers to a shared channel.
Channel level of the OSI model
The channel level ensures reliable data transmission on the physical network channel. Different channel layer specifications define various network characteristics and protocols, including physical addressing, network topology, error diagnostics, frame alternation and flow control. Physical addressing determines how devices are addressed on the channel level. The network topology consists of channel-level specification, which determine the physical connection of devices, such topologies, like a tire or ring. Error diagnoses informs the highest level protocols that the transmission error occurred, and the alternation of the data frames extends the frames that were transmitted to the sequence violation of the IEEE 802.3 protocol. Finally, the flow control manages the data transfer in such a way that the receiving device will not be overloaded with large traffic than it can be processed per unit of time.
The channel level is divided into two sublevels: a logical link control system (LOGICAL Link Control - LLC) and a sublayer access control system (Media Access Control - Mac). A logical connection control system (LLC) controller controls the exchange of data between devices on one channel channel. The LLC sublayer is defined in the IEEE 802.2 specification and supports both services operating without confirmation of connections and services oriented services used by top-level protocols. The IEEE 802.2 specification defines the number of channel layer frames that allow the separation by several top-level protocols of one physical data channel.
The sublayer of access control to the transmitting medium (Mac) of the channel level controls the access of protocols to the physical network environment. The IEEE specification defines the MAC addresses and allows you to identify each other a uniquely multiple devices on a channel level.
3. 100Base-TX
The standard of this physical interface involves the use of unshielded twisted pair of category not lower than 5. It is fully identical to the FDDI UTP PMD standard, which is also discussed in detail in chapter 6. Physical port RJ-45 as in the 10Base-T standard can be of two types: MDI (Network Maps, workstations) and MDI-X (repeater Fast Ethernet, switches). The MDI port in single quantity can be available on the Fast Ethernet repeater. For transmission over the copper cable, pairs of 1 and 3. Couples 2 and 4 are used - free. The RJ-45 port on the network card and on the switch can support to a row with a 100Base-TX mode and 10Base-T mode or a speed auto definition function. Most modern network cards and switches support this feature by RJ-45 ports and besides this can work in duplex mode.
BASE-TX uses for data transmission to one pair of twisted (twisted) wires in each direction, providing up to 100 Mbps with bandwidth in each direction.
Twisted steam is a low-current cable for transmitting data using an electrical signal over copper or aluminum copper veins. In the modern world, the UTP 5e cable is deeply used in SCS (structured cable systems). Among the varieties of UTP differing characteristics and quantities, they most often found UTP 5E 4 pairs and UTP 2 pairs for inner laying and external, in the latter case, there is a cable in the cable design. UTP with a cable conveniently lay down the street between buildings, and the price of this product is significantly lower than the analogues. Usually, the outer twisted pair UTP is made in a black sheath of polyvinyl chloride, including the screen in the form of a metal braid in bays with different lengths, the common option is 305 meters of the bay. For laying in rooms, the color of the shell is gray. Mostly UTP is used to connect subscribers to the Internet or building a local computing network, in which case, only two twisted pairs 5e are used, with a gigabit connection - all 4. Its second name "twisted pair" received at the expense of a twist He lived pairwise, the UTP - Unshieded Twisted Pair is decrypted. Thanks to its balance, the cable has all the necessary characteristics for the SCS, among the global manufacturers of UTP cable are the most famous brands such as: Hyperline, Neomax, IO-SCS, Maxys, Silverlan. As a rule, wholesale prices for UTP 5e are much lower among similar cable products, in our assortment, the entire "twisted pair" is certified and complies with world quality standards.
Computer location scheme
In order to draw a plan for our premises to use the Compass program. 1: 100 drawing scale. Immediately place on the plan of 27 jobs according to the task, two switches, and we define the cable laying track, whatever she satisfy all our conditions.
Calculation of the total cable length
Using the resulting drawing, we calculate the required length of the cable L, for the laying of our network. To calculate, we use the formula (1). Also, when calculating, we take into account all the raises, descents, turns, etc. After finding, the length of the cable L will verify it for compliance with the condition (2).
where: i is the distance from the I-wow workplace to the switch K1; J - the distance from the jth workstation to the switch K2; - distance from Switch to K1 to the router M; - distance from Switch K2 to the router M;
8 * 300B ≤ L ≤ 300B (2)
where: - an integer cable bay.
Table. 1 Cable lengths
|
|
|
||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|
|
This cable length satisfies our condition.
Ethernet frame formats
The data transmitted in the Ethernet network is divided into frames. Network data is not transmitted in pure form. As a rule, the title "is attached" to the data unit. In some network technologies, the end is also added. The header and ending are credited and consist of certain fields.
Since there are several types of frames, in order to understand each other, the sender and the recipient must use the same type of personnel. Frames can be four different formats, somewhat different from each other. Basic frame formats (RAW FORMATS) exists only two - Ethernet II and Ethernet 802.3. These formats are distinguished by the purpose of just one field.
For the successful delivery of information, the recipient each frame should except the data contain service information: the length of the data field, the physical address of the sender and the recipient, the type of network protocol, etc.
In order for the workstations to have the ability to interact with the server in one network segment, they must support a single frame format. There are four main varieties of Ethernet frames: Type II802.3802.2SNAP (Subnetwork Access Protocol).
The minimum permissible length of all four types of Ethernet frames is 64 bytes, and the maximum is 1518 bytes. Since 18 bytes is given to the service information in the frame, the "data" field may have a length of 46 to 1500 bytes. If the data transmitted over the network is less than permissible minimum length, the frame will automatically be complemented to 46 bytes. Such rigid restrictions on the minimum frame length are entered to ensure normal operation of the conversion mechanism.
In order for the Ethernet network, consisting of segments of various physical nature, it worked correctly, it is necessary that three main conditions are performed:
) The number of stations in the network does not exceed 1024 (taking into account restrictions for coaxial segments).
) Double signal propagation delay (PDV) between the two networks remote from each other does not exceed 575 bite intervals.
) Interpacca Gap Shrinkage (Interpacket Gap Shrinkage) When passing a frame sequence through all repeaters, no more than 49 bit intervals (we will remind that when sending frames, the station provides an initial intercase distance in 96 bitted intervals).
Compliance with these requirements ensures the correctness of the network, even in cases where simple configuration rules are violated, which determine the maximum number of repeaters and the maximum length of the segments of each type.
The physical meaning of the restriction of the delay in the distribution of the signal over the network has already been illustrated - compliance with this requirement provides timely detection of collisions.
The requirement for the minimum intercade distance is due to the fact that when the frame passing through the repeater, this distance decreases. Each package taken by the repeater, resynchronized to eliminate the shake of signals accumulated during the passage of the pulse sequence over the cable and through the interface circuits. The process of resynchronization usually increases the length of the preamble, which reduces the intercadron interval. When passing frames through several repeaters, the intercadron interval may decrease so much that the network adapters in the last segment will not have enough time to process the previous frame, with the result that the frame will be simply lost. Therefore, a total decrease in the intercontramic interval is not allowed to more than 49 bitted intervals.
Calculation PDV-temporal delay. The first term describes the delay in all cable segments. The second term describes a temporary delay in switching nodes. The third term is a delay in network adapters.
If the speed of 10 Mbps À PDV should be no more than 576 bits per interval.
If the speed is 100 Mbps Àpdv no more than 512 bits per interval. (Bit on the 6T interval).
When counting PDV, you must find the 2 most remote computers on the network. It is also necessary to determine the delays in the concentrators.
Increasing PDV more than the maximum value to a significant number of collisions, due to the fact that the minimum length 64b frame does not have time to bypass the network 2 times and the Collisium Detected mechanism does not record the conflict.
(UTP-5) \u003d 1,112 BT / M - Cable Delays Cable Category TX
(2TX / FX) \u003d 100 bt - delays in 2 adapters category TX
(TX / FX) \u003d 92 BT - delays in switches and routers 2y category \u003d (17.34 + 16,91 + 51,61 + 20.35) * 1,112 + 3 * 92 + 100 \u003d 505.9 BT
Mbps \u003d\u003e PDV< 512 bt
bT - Marine interwacing interval
For high-quality operation, it is necessary that PDV satisfies the following condition: PDV ≤ 512 BT.
In our case, this condition is performed. Since all of our conditions are executed, you can finally draw the cable laying track (Appendix 1).
SIP protocol
Session Initiation Protocol - Session Initiation Protocol (SIP) is an application-level protocol and is intended for organizing, modifying and completing communication sessions: multimedia conferences, telephone connections and multimedia information distribution. Users can take part in existing communication sessions, invite other users and be invited to a new communication session. Invitations can be addressed to a specific user, a group of users or all users.
The protocol is based on the following principles:
Personal user mobility. Users can navigate without restrictions within the network, so communication services should be provided to them anywhere in this network. The user is assigned a unique identifier, and the network provides him with communication services, regardless of where it is located. For this, the user using a special message - Register - informs the location server about its movements.
Scalability of the network. It is characterized primarily, the possibility of increasing the number of network elements in its expansion. The server structure of the network built on the SIP protocol database fully meets this requirement.
Extensibility of the protocol. It is characterized by the possibility of adding the protocol with new features when introducing new services and adapting it to work with various applications.
Interaction with other signaling protocols. The SIP protocol can be used in conjunction with the N.323 protocol. The interaction of the SIP protocol with the TFOP signaling systems is DSS1 and OX7. To simplify such interaction, the SIP protocol signal messages can transfer not only a specific SIP, address, but also a phone number. In addition, the SIP protocol, along with H.323 and ISUP / IP protocols, can be used to synchronize the loading devices of the gateways.
10. Switches
Objectives:
increasing the capacity of LAN
creating a parallel processing of internal network packet streams - Intranet and external - Internet
solving network security issues
optimization of network architecture
Classification:
First-level switches:
Optical switches - based on prisms and works on the principle of optics physics (signal splitting). They commute optical signals.
Second-level switches:
switching (Cross Bar) with buffering at the entrance
camera Route (SELF ROUTE) with shared memory
high Speed \u200b\u200bBus (High Speed \u200b\u200bBus) Bar - Switching with buffering at the entrance based on the switching matrix.Road - Managed Multiple Memory
Comparative analysis of switching technologies.
Cross Bar technology provides the highest switch and bandwidth in the absence of internal memory.
Switches made on this technology make minimal time delays in the data network. Such switches are called slave switches. Group 1 class. These switches are simple device and a small cost. Depicted in the form of a monoblock with a limited number of ports.
Lack of technology:
film frames that have errors
minimum administration capabilities
possible internal locking matrixroad.
Since the frame in this technology is fully placed in the internal memory of the switch, then the control sum of the frame is checked on a row with the MAC address of the recipient, and if there is a mismatch, this frame is removed.
Advantages:
no blocking
the presence of filtering of minor frames
the number of ports can be much more than in Crossbar
more administration opportunities, in particular, on frame filtering.
Disadvantages:
significant temporary delay when processing frame
such switches to the 1st class working group.
self-Road value more than Crossbar
Level 3 switches.
It is customary to call switches with the routing function. Works on the 3 levels of the OSI model. In addition to the network switching framework, the network can be routed online application packages.
There is no difference that the MAC address or IP protocol is used. It has a MAC compliance table and IP addresses.
Level 4 switches.
Switching technology at level 4 includes the possibility of controlling the performance and traffic of level 2 and 3 switches, complementing them with new features, including server management capabilities and applications. New switches use information that is contained in packet headers and refers to the level 3 and 4 protocol stacks, such as the source and receiver IP addresses, the SYN / FIN bits that mark the beginning and end of application sessions, as well as TCP / UDP port numbers for identification Traffic accessories to various applications. Based on this information, level 4 switches may make decisions on redirecting traffic to a session.
Routing
Routing goal: Accumulation of information for the router TCP / IP stack protocols by drawing up and adjusting the routing table.
Routing is performed on the OSI network level.
The network level provides solutions to the following tasks:
Consistent data transfer principles
Solves the problem of protocols. WAN works with LAN
Disquires data format
Dissens data environment.
It is all possible thanks to a large number of protocols.
Main Protocol on the network layer model OSI IP Protocol. His task is to transfer packets from the sender to the recipient, where the sender and the recipient are computers. Each host on the global network is assigned its IP address. 4 grade is used:
In the class, the first byte goes to the structure of a network of 3 bytes to the host address.
In class 2 byte - network address, 2 bytes - host address
In class with 3 bytes - address, 1 byte host.
The total length of the package IP can reach 64 bytes. IP options apply to routing methods.
Routing in global networks is as follows: A request is created, suppose Ping request, the message of the IP sender and IP of the recipient is available. This query goes to the router, and then forwarded to all routers, they watch the message and determine if they have information about IP recipient in the table. If yes, the response information contains the MAC address of the recipient. Data is written in the ARP table. Thus, the connection is established. ARP request is one of the huge number of protocols that operate on the network level of the OSI model. Also on the network level, I operate such protocols as ICMP, IPSec, RIP, DGP.
Protocol characteristics:
reliability
stability
simplicity
convergence
optimality
Protocol classification by control method:
static (routing table buildings are performed in manual, routes do not change over time)
dynamic (the construction of the table is automatically performed as it changes in the data network)
To implement all these protocols, it is used, as already mentioned a little earlier, the router. This is a network device that is intended for connecting local networks into a single structured network with managed traffic and high protection capabilities.
Multiservice. IP - Telephony, SIP, H.323
local computing network
In order to transmit voice, video and data in global networks, new generation networks NGN were created. Thanks to NGN, it became possible to arrange IP telephony, audio (video) conference. It became possible using Softswitch. - Software switch that controls VoIP sessions. It implements several approaches to building IP telephony: H.323, SIP, MGCP..323 ITU-T Recommendation, set of standards for transmitting multimedia data on networks with packet transmission.
Alarm - Generates a connection and manages its status, describes the type of data transmitted
Multimedia Stream Management (Video and Voice) - Data Transfer Through Real Time Transport Protocols (RTP)
Data transfer applications.
Communication interfaces are the interaction of devices on the physical, channel, network levels. Wession Initiation Protocol - a data transmission session protocol that describes how to establish and terminate a custom Internet session, including the exchange of multimedia content.
The protocol was based on the following principles:
Easy: Includes only six methods (functions)
Personal user mobility. Users can navigate within the network without restrictions. At the same time, the set of services provided remains unchanged.
Scalability of the network. The network structure based on the SIP protocol allows you to easily expand it and increase the number of items.
Extensibility of the protocol. The protocol is characterized by the ability to supplement it with new functions when new services appear.
Integration into the stack of existing Internet protocols. The SIP protocol is part of the global multimedia architecture developed by the IETF committee. In addition to SIP, this architecture includes RSVP, RTP, RTSP, SDP protocols.
Interaction with other signaling protocols. The SIP protocol can be used in conjunction with other IP telephony protocols, TFE protocols, and for communication with intelligent networks.
Thus, SoftSwitch will allow multiservice to organize. Using the data network, users can use VoIP phones, IP television, and many other features. - Power Over Ethernet, this is a system that allows you to convert an alternating voltage of 220 V per 48 V permanent (from 36 to 52 V). This technology is used in switches to power Web cameras, or IP phones.
The main advantage of PoE technology is the lack of need to pull into network devices a separate electrical wiring for power supply to the power where it is not. Wireless access points, video surveillance cameras, access control systems that are powered by PoE technology can be installed wherever it is necessary. The installation of the installer in hard-to-reach places is facilitated.
I chose Cisco Systems CP-7906G phone, as it meets our requirements: IP phone on 1 line with 1 Fast Ethernet port and POE support
Distribution of IP addresses for LAN
There is one IP address that defined the provider (set):
10.0.5 - IP address
255.255.192 / 26 network mask
10.0.5 / 26 - Network ID
10.0.63 - broadcasting 197.10.0.0/28
10.0.1/28 197.10.0.5/28
10.0.2/28 197.10.0.6/28
10.0.3/28 197.10.0.7/28
10.0.4/28 197.10.0.8/28
10.0.9 / 28 - IP - Phone
10.0.15 Broadcast Addressing 197.10.0.16/28
10.0.17/28 197.10.0.21/28
10.0.18/28 197.10.0.22/28
10.0.19/28 197.10.0.23/28
10.0.20/28 197.10.0.24/28
10.0.31 Broadcast Addressing 197.10.0.32/28
10.0.33/28 197.10.0.35/28
10.0.34/28 197.10.0.36/28
10.0.47 Broadcast Addressing 197.10.0.48/28
10.0.49/28 197.10.0.53/28
10.0.50/28 197.10.0.54/28
10.0.51/28 197.10.0.55/28
10.0.63 broadcast address
Software and hardware
In our course project chosen industry construction. This branch is engaged in the creation of architectural projects of buildings, urban structures and other things. This is a powerful CAD platform that combines a familiar set of basic functions with an improved 2D set of tools and intelligent 3D modeling for Windows and Linux at an acceptable price. Fees and records data in DWG format and It offers very high compatibility with AutoCAD®. In addition to this, Bricscad offers direct 3D modeling in DWG format. Bricscad is much more than just an alternative.
Due to the complete set of compatible APIs, third-party applications can work on Bricscad without modifying the source code.
DNS EXTREME system unit
Intel Core i5 Processor Type
I5 3340 processor code
Number of processor cores 4
Processor frequency 3100 MHz
RAM size 8192 MB
Hard disk volume 1000 GB
Optical drive DVD ± RW
Chipset graphic controller NVIDIA GeForce GTX 650
Video memory size 1024 MB
Cisco UCS C240 \u200b\u200bM3 Server
Intel Xeon Processor Type
Intel® C600 chipset
Intel® Xeon® E5 2620 processor
Processor frequency 2.0 GHz
CPU 1 is established
Power 2 x 650 W
Switch Cisco WS-C3560V2-24PS-S
Number of ports of the switch 24 x Ethernet 10/100 Mbps
Cisco 857-K9 Router
RAM number 64 MB
Number of switch ports 4 x Ethernet 10/100 Mbps Cisco 7906G
Network Interfaces 1 x RJ-45 10 / 100Base-TX
with Fast Ethernet port and POE support
Twisted pair UTP 5e
(frequency band 125 MHz) 4-paired cable, improved category 5. Data transmission speed up to 100 Mbps when using 2 pairs and up to 1000 Mbps when using 4 pairs. Cable Category 5e is the most common and used to build computer networks. Restriction on the length of the cable between devices (computer-switch, switch-computer, sweat switch) - 100 m.
Calculation of the estimated cost
|
Equipment / program |
Name |
number |
Price, rub / pcs |
Price, rub |
|
|
System block, with Windows 7 Home Premium 64-bit |
|||||
|
Keyboard |
Gigabyte GK-K6150 Multimedia USB Black |
||||
|
DNS Office WRD-039BS Black USB |
|||||
|
Operating system |
Microsoft Windows Server 2008 R2 STANDART EDITION SP1 (64-BIT) |
||||
|
Antivirus |
Kaspersky Internet Security |
3990 per 5 pc 1790 per 2 pc |
|||
|
IP phone |
Cisco Systems CP-7906G |
||||
|
UTP 4 Couple Cat.5E |
305 m (bay) |
||||
|
Plug RJ45 5E 8P8C |
|||||
|
Wall socket |
Plug RJ45 cat.5. |
||||
|
Cable Channel |
|||||
|
Corner internal |
|||||
|
Switch |
Cisco WS-C3560V2-24PS-S |
||||
|
Router |
|||||
|
Cisco UCS C240 \u200b\u200bM3 |
|||||
|
Server cabinet |
|||||
|
Design and Installation Work |
|
|
TOTAL: 2 279 806 rubles
Conclusion
In the course of the work done, the LAN enterprise was designed, the cable gasket route was determined, the necessary equipment and software was selected. It was also counted the estimate for the implementation of the LAN. The final characteristics of the network turned out as follows:
Number of jobs - 27, pcs;
Topology - Star;
Transmission rate - 100, Mbit / s;
Service life - 10 years;
Estimated cost LAN - 2 200 833 rub.
Bibliography
1) lectures on the subject of "Infocommunication Systems" - teacher of Parshin K.A.
) DNS Online Shop -www.dns.ru
Green Effect Company is designing, construction (gasket) and LAN service.Laying LAN Provides a guaranteed presentation of information resources and services with the required levels of availability, reliability, scalability, safety and manageability. LAN (local computing network) This is a set of software and hardware, which includes many components and nodes. The network subsystem LAN Customer is designed to meet the needs of subscribers in providing information interaction and exchange of data aimed at fulfilling the business processes of the Customer.
Most often, the LAN is organized on Ethernet and / or Wi-Fi technologies. For construction and laying, LANs are used switches, routers, wireless access points (Wi-Fi), modems, optical (volc) and copper communication lines, etc.
To remotely connect to the LAN, the VPN connection is most often used. VPN - technology allowing from home, remote office or business trips to organize one or more network connections over another network (Internet).

Choice and rationale for the construction of LAN
The choice of technology, architecture and equipment for the construction of the LAN is determined by the following factors:To achieve the best results on productivity, reliability, manageability, LAN scalability requires a modular and hierarchical approach to the data transmission system design. This approach allows you to increase the LAN optimal by adding new blocks without affecting the remaining components of the network structure, provides an extremely high degree of certainty in the behavior of the LAN, which facilitates troubleshooting.
LAN provides its subscribers the following information services:
The LAN consists of the following subsystems:
We work with the entire spectrum of optical fiber products (VOLS), copper pairs, server cabinets, patch panels, wireless network equipment (Wi-Fi), sockets, etc. Our company has modern equipment and software for construction (gasket) LAN. When surrendering LAN, a complete report on the testing of all laid lines of communication is attached. The construction of the LAN is carried out using network active and passive equipment from leading manufacturers, such as Cisco, Hewlett-Packard, 3Com, etc. Green Effect construction and gasket LAN for office, production, public and residential buildings.
Design LAN
Green Project Department Effect provides a full range of LAN design services (local computing network).At the first stage of the design of LANs, an inspection of the object is made, negotiations with the customer, identifying the tasks and the requirements of the LAN.
According to the results of research and analysis of the source data, the optimal project for building a local computing network is developed, which includes all the wishes and customer requirements. The LAN project includes: detailed plans for the location of the elements of the system; Principal and structural connection schemes, cable laying tracks, cable log. It is also composed of the specification of equipment and materials, estimated on the Moting LAN and the statement of the work performed.


Design LAN It is carried out in accordance with the Decree of the Government of the Russian Federation of February 16, 2008 No. 87 "On the composition of the sections of the project documentation and the requirements for their content", regional construction regulations and requirements of the technical specifications.
When designing a LAN, the requirements of existing legislation and regulatory documents on ecology, labor protection and fire safety are taken into account.
Pre-project examination
The purpose of the pre-project survey is to determine the set of measures and the development of technical proposals, taking into account the formed typical solutions. According to the results of the survey, our designer engineers will help the customer to develop a competent technical task (TK) on the design of the LAN.Technical task (TK) LAN
Customer requirements form the basis technical task (TK) LAN And the primary document from which work begins to create a local computing network. In addition to technical requirements, in the first stages of work on the design of LANs, data obtained in the process of pre-project survey are used as source information. Any design begins with a properly written technical task approved by the customer. From competently written TK, the design periods and the choice of the necessary equipment for the construction of the LAN, described in the TK.The composition of the design documentation of the LAN is regulated by the Decree of the Government of the Russian Federation "On the composition of the sections of project documentation and requirements for their content" of February 16, 2008 No. 87.
Design documentation LAN (Stage "P")
The competently designed concept of the LAN and the technical task gives grounds for creating a sketch plan of the LAN - a single complex of solutions intended to ensure a given mode of operation of the LAN. The sketch project defines the optimal structure of the LAN and the cable posting layout route, the location and composition of the elements of the telecommunications infrastructure, an idea of \u200b\u200bthe project budget, as well as a number of other parameters that will make it easier to choose specific solutions.The design documentation of the LAN is text and graphic materials that determine the volume-planning, design and technical solutions for the construction or reconstruction (modernization) of the LAN.
The basis for the development of the LAN project is the architectural and construction, technological and engineering parts of the building project. The LAN project is focused on using the most efficient and well-proven equipment and component materials. Competent design is a high speed of construction work and LAN maintenance. Unmistakable project calculation - minimizing equipment costs.
Working documentation LAN (Stage "P")
At the next stage, the LAN working documentation is being developed, which is used in the construction phase. It is at this stage that the resource-intensity of the process is determined, the volume of construction and installation work, the number of necessary equipment and materials, and therefore the final budget of the LAN project.LAN working documentation is developed after approval of the preceding design stage. The purpose of the work at the "P" stage is to prepare accurate drawings, schemes and tables that installers will be guided during the work on the creation of a LAN. Working documentation provides detailed binding of components of all systems to the object. Working documentation LAN contains drawings, tables of connections and connections, plans for the location of equipment and wiring and other documents.
Estimated Documentation LAN ("SD")
The development of estimated documentation is the final stage of the design of the local computing network and determines the full cost of equipment, construction and commissioning and commissioning work.Construction (installation) LAN
In accordance with the LAN project approved by the Customer and the procurement of the necessary equipment, it is produced:Experts of Green Effect provide a full range of services for the installation of LAN.
The accumulated, in the art, experience allows you to install and connect the LAN as soon as possible, in strict accordance with the project and the appropriate quality of work.


Setting up LAN
Upon completion of the installation, the LAN is subjected to comprehensive testing and configuration in order to verify the performance of the system and detecting defects. The results of testing and configuration with the explanations of parameter values \u200b\u200band the quality analysis of the local computing network are provided to the customer (an example of testing report in the figure). After completing all the works and the transfer of documentation, the Customer, representatives of the artist and the Customer, are inspected by the object. If you fulfill all the necessary requirements and tasks, as well as compliance with the technical task, the object is commissioned.

Service LAN.
Maintenance of the LAN (local computing network) It is carried out in order to ensure the smooth operation of the Unified IT system of the company's equipment and the permanent access of personnel to various information services.The LAN maintenance is implemented by diagnosing the state of all areas of the LAN, measurements in cross cabinets, detecting and eliminating damage to the LAN elements.
LAN maintenance includes:
LAN maintenance works are dependent on the operating conditions and equipment composition.
Preventive maintenance work LAN:
The diagnostics of the LAN ports is to measure the parameters of the LAN ports to comply with category parameters using the corresponding certified instrumentation with the issuance of reports on all measured parameters throughout the frequency range. Non-compliance of LAN ports The category requirements is determined by the results of the port diagnostics.
Recovery maintenance work LAN:
The faults identified as a result of preventive work are eliminated by the Contractor as part of the maintenance of the LAN. Depending on the nature of the malfunction, a decision is made on the output of faulty equipment from the use and inclusion of it into the current repair plan of the LAN, or the elimination of the defect in place. Faults to eliminate additional work and material resources, eliminate after the preparation of a defective statement. The identified disorders of the operating conditions of the LAN are reported to customer representatives.
The schedule of work, the LAN is developed and approved by the Customer. According to the results of the work, the Contractor provides a report in which:
Send your good work in the knowledge base is simple. Use the form below
Students, graduate students, young scientists who use the knowledge base in their studies and work will be very grateful to you.
Posted by http://www.allbest.ru/
Federal Agency for Education of the Russian Federation
Omsk State Institute of Service
Faculty of absentee (tourism and applied informatics)
Department Applied Informatics and Mathematics
Controlwork
By discipline: Computing systems, networks and telecommunications
Subject: "Designing a local computing network organization"
Performed: Student 121-PZ c.
Ivashchenko Natalia Alexandrovna
Checked:
Shabalin Andrey Mikhailovich
Introduction
1. Theoretical Basics of Local Network Design
1.1 General characteristics of the object under study
1.2 General characteristics of network technologies used
2. Local Network Design
2.1 Topology Network and Network Equipment
2.2 Computer computers of local network
2.3 Ensuring the LAN Connection with the Internet Network
2.4 Economic calculation
Conclusion
Bibliographic list
Introduction
At the moment, no enterprise or organization costs without computing machines. This is due to the transition to electronic document flow, with machine calculations and storage of huge arrays of information in electronic form. The use of computers brings great benefits and the more operations can be converted to an electronic computing form, the more effective the management becomes. But one increase in the number of computers in the organization cannot be limited to, it is necessary to combine them optimally. This is the purpose of local computing networks.
Computer network - Computer and / or computer equipment communication system (servers, routers and other equipment). To transfer information within which various physical phenomena can be used, as a rule - various types of electrical signals or electromagnetic radiation.
The local computing network (LAN, LAN) is a computer network covering usually a relatively small territory or a small group of buildings.
This test is devoted to the design of the local computing network in the conditions of the organization OJSC "Furniture World"
The purpose of work is to consolidate knowledge of computer networks and network equipment, receiving the design skills of the local network of the organization in accordance with its needs.
During operation, Internet resources were widely used.
1. Theoretical foundationslocal network design
If in one room, building or complex of nearby buildings there are several computers whose users must jointly solve some tasks, exchange data or use general data, then these computers are advisable to merge into the local network.
The local network is a group of several computers connected by cables (sometimes also telephone lines or radio channels) used to transmit information between computers. To connect computers to the local network, network equipment and software are needed.
Assigning all computer networks can be expressed in two words: sharing (or sharing). First of all, it means sharing data. People working on one project have to constantly use the data created by colleagues. Thanks to the local network, different people can work on one project not in turn, but at the same time.
The local network provides the possibility of sharing the equipment. Often it is often cheaper to create a local network and set one printer to an all division than to acquire the printer for each workplace. The network file server allows you to provide joint access to programs.
Equipment, programs and data are combined with one term: resources. We can assume that the main purpose of the local network is access to resources.
To communicate with external (peripheral) devices, the computer has ports through which it is capable of transmitting and accepting information. It is easy to guess that if you connect two or more computers through these ports, they will be able to exchange information among themselves. In this case, they form a computer network. If computers are close to each other, use a shared set of network equipment and manage one software package, then such a computer network is called local. The simplest local networks are used to maintain working groups. The Working Group is a group of persons working on one project (for example, over the release of one journal or on the development of one aircraft) or simply employees of one unit.
1.1 General characteristics of the object under study
OJSC "Furniture Mir" is an open joint-stock company for the production of high-quality furniture. The company is famous for the introduction of more advanced technologies in the production of furniture and the use of new materials. A significant number of furniture is produced by a universal national team, built-in, transformed for the situation of a small area of \u200b\u200brooms. In recent years, the furniture industry began to produce artistic furniture. Along with the products, easy-to-form products, furniture furniture and aesthetics are produced using improved facial fittings for artistic decoding elements. Along with the growth of furniture, special attention is paid to its convenience, hygienic, design, decoration. Particular attention is paid to optimizing the range of furniture based on the real need for the market, the production of products of various styles and options, which allows you to set and update the furniture every 4 to 5 years.
The structure of the organization Figure 1
Posted by http://www.allbest.ru/
1.2 General characteristics of network technologies used
Technology Fast Ethernet - This is an integral part of the IEEE 802.3 standard, which appeared in 1995. It is a faster version of the standard Ethernet network that uses the same CSMA / CD access method, but a significantly higher transmission rate is 100 Mbps. The Fast Ethernet saves the same frame format that is accepted in the classic version of Ethernet. In order to preserve compatibility with earlier versions of Ethernet, the standard defines a special mechanism for the FAST Ethernet to automatically determine the transmission speed in mode AUTO-NEGOTIATION (Auto detection), which allows Fast Ethernet network adapters to automatically switch from a speed of 10 Mbps to the speed of 100 Mb / s and vice versa.
The higher bandwidth of the transmission medium in Fast Ethernet allows you to drastically reduce the load on the network compared with the classical Ethernet technology (with the same amount of information transmitted) and reduce the likelihood of collisions. The main topology of the Fast Ethernet network is a passive star. It brings it closer with the 10Base-T and 10Base-F specifications. The standard defines the following FAST Ethernet specification: 100Base-T4. (Transmission is carried out at a rate of 100 Mbps in the main frequency band on the four twisted pairs of electrical wires), 100Base-TX. (Transmission is carried out at a speed of 100 Mbps in the main frequency band on two twisted pairs of electrical wires), 100Base-FX. (Transmission is carried out at a rate of 100 Mbps in the main frequency band in two fiber optic cables).
Computer combining circuit in the Fast Ethernet network is almost no different from the 10Base-T specification scheme. The cable length also cannot exceed 100 meters, but the cable must be better (not lower than Category 5). It should be noted that if in the case of 10Base-T, the limit cable length of 100 m is limited only by the quality of the cable (more precisely, losses in it) and can be increased (for example, up to 150 m) when using a better cable, then in the case of 100Base -Tx Limit length (100 m) is limited to the specified temporal exchange ratios (double-time restriction) and cannot be increased under any circumstances. Moreover, the standard recommends limited to the length of the segment of 90 m, so that there is a stock of 10%.
The main difference between the 10Base-T4 equipment of 100Base-TX is that unshielded cables containing four twisted pairs are used as connecting cables. Data exchange is on one transmitted twisted pair, one receiving twisted pair and two bidirectional pairs using differential signals. In this case, the cable may be less high-quality than in the case of 100Base-TX (for example, Category 3). The signal transmission system received in 100BASE-T4 provides the same speed of 100 Mbps on any of these cables, although the standard recommends using all the same Category 5 cable.
The use of fiber-optic cable and in this case makes it possible to significantly increase the length of the network, as well as get rid of electrical filing and increase the secrecy of the transmitted information. The maximum cable length between the computer and the hub can be up to 400 meters, and this restriction is determined not by the quality of the cable, but by temporal ratios. According to the standard, in this case it is necessary to use a multimode fiber optic cable.
2. Local Network Design
The object of the design is the local system of the organization. This network should ensure the transportation of information within the Organization and to ensure the possibility of interacting with the global network of the Internet. The organization for which the local network is designed is an enterprise, the main activity of which is the production of high-quality furniture.
2.1 Network Topology and Network Equipment
Topology network
When building a LAN organization, we will use the tree structure based on the star topology. This is one of the most common topologies, since it is easy to maintain.
Advantages of topology:
· The failure of one workstation is not reflected in the work of the entire network as a whole;
· Good network scalability;
· Light troubleshooting and cliffs on the network;
· High network performance (subject to proper design);
· Flexible administration capabilities.
Disadvantages of topology:
· The failure of the central concentrator will be wanted by the inoperability of the network (or network segment) as a whole;
· For network laying, more often requires more cable than for most other topologies;
· The final number of workstations in the network (or network segment) is limited by the number of ports in the central hub.
This topology is chosen due to the fact that is the most fast-acting. From the point of view of reliability, it is not the best solution, since their output of the central node leads to a stop of the entire network, but at the same time it is easier to find a malfunction.
Subscribers of each network segment will be connected to the corresponding switch (Switch). And these segments will be connected to a single network - the control switch is the central network element.
Next Network Equipment:
1. Network switches or switches (Switch) - 8 PC.- A device intended to connect multiple computer network nodes within one segment.
2. Servers (Server) - 1 PC. - hardware, dedicated and / or specialized to perform service software without direct human participation.
3. Printers (including multifunctional devices)(Printer) - 5 PC. - A device for printing digital information on a solid carrier, usually on paper. Refers to the terminal devices of the computer.
4. DVBPC. map1 PC.- this is a computer board that is designed to receive a signal from the satellite, and then decipher it.
5. Satellite antenna- 1 PC. - This is the most important component of satellite Internet and satellite TV, the stability of the Internet compound will depend on it, and the quality and number of satellite TV channels.
6. Converter -1 PC.- A program using which you can convert files from one format to another.
Transmission environment:
The transmission medium is a physical environment for which the distribution of information signals in the form of electrical, light, and the like can be distributed. pulses.
To combine PCs in a single LAN, you will need a UTP5E cable "Twisted Pair), is one of the most common types of cable at present. It consists of several pairs of copper wires covered with plastic shell. The wires that make up each pair are twisted around each other, which ensures protection against mutual filing. The cables of this type are divided into two classes - "shielded twisted pair" and "unshielded twisted pair" ("unshielded twisted pair"). The difference between these classes is that the shielded twisted pair is more protected from external electromagnetic interference, due to the presence of an additional screen from the copper grid and / or aluminum foil surrounding the cable wire. Networks based on the "twisted pair" depending on the category of cable provide transmission at a rate of 10 Mbps - 1 Gbit / s. The length of the cable segment cannot exceed 100 m (up to 100 Mbps).
Table 1. Number of equipment online
|
Equipment |
number |
|
|
Switters |
||
|
Switch D-Link |
||
|
Switch D-Link (SWICH1,2,3,4,5,6,7) |
||
|
PC (2 configuration) |
||
|
Satellite DVB Card TEVII S 470 PCI-E (DVB-S2) |
||
|
Satellite antenna |
||
|
Converter Multico.< EC-202C20-BB> |
Calculation of the cable system:
To calculate the cost of cables, we will take that the average distance between computers in the department and the corresponding switch is 10 meters, then you will need about 850 m UTP 5e cable.
To cover the distance from switches to the central managed switch (+ Connect the Manager) 350 m UTP 5E cable. Network Local Cable Internet
I will increase the cost of the UTP 5e cable by 10% (for waste and marriage when installing) and get about 1350 m.
Most 100 segments of twisted pair, for which 200 RJ-45 connector will be required. Taking into account marriage - 220.
2.2 Computer computers of local network
Table 2. Description of computers (K)
|
Complete set (K) |
Characteristic |
number |
Price, rub) |
|
|
CPU case |
Miditower Vento. |
|||
|
CPU |
CPU AMD ATHLON II X4 641 (AD641XW) 2.8 GHz / 4Core / 4 MB / 100 W / 5 GT / With Socket FM1 |
|||
|
Motherboard |
Gigabyte GA-A75-D3H Rev1.0 (RTL) SocketFM1 |
|||
|
RAM |
Corsair Vengeance. |
|||
|
HDD 1 TB SATA 6GB / S Seagate Barracuda 7200.12 |
||||
|
DVD RAM & DVD ± R / RW & CDRW LG GH24NS90 |
||||
|
Cooller processor |
AMD Cooler (754-AM2 / AM3 / FM1, CU + Al + Heat Tubes) |
|||
|
Couller housing |
||||
|
Keyboard |
TOTAL: 16347.
This equipment is designed to work with office documents. Installed cheap and simple components.
Chairman of the Board:
Cabinet №1 General Director (K1)
Cabinet №2 Secretary (K2)
Cabinet # 3 Board of Directors (K3, K4, K5, K6, K7, K8, K9, K10, K11, K12, K13, K14, K15)
Security Service:
Cabinet №4 Protection Department (K16, K17, K18, K19, K20)
Cabinet №5 Economic Security Department (K21, K22, K23, K24, K25, K26)
Quality service:
Cabinet №6 Department Special Technologies (K27, K28, K29, K30, K31, K32, K33)
Cabinet №7 Department of specials. Equipment (K34, K35, K36, K37, K38, K39, K40)
Personnel Department:
Cabinet number 8 Economic department (K41, K42, K43, K44, K45, K46)
Cabinet №9 Personnel Department (K47, K48, K49, K50, K51)
Cabinet №10 Personnel Director (K52)
Executive Department:
Cabinet №11 Technical Department (K53, K54, K55, K56, K57)
Cabinet №12 Production Department (K58, K59, K60, K61, K62)
Cabinet №13 Executive Director (K63)
Table 3. Description of computers (P)
|
Equipment (P.) |
Characteristic |
number |
Price, rub) |
|
|
CPU case |
Miditower Inwin BS652. |
|||
|
CPU |
CPU AMD FX-8150 (FD8150F) 3.6 GHz / 8Core / 8 + 8MB / 125 W / 5200 MHz Socket AM3 + |
|||
|
Motherboard |
Gigabyte GA-990FXA-D3 Rev1.0 / 1 (RTL) Socketam3 + |
|||
|
RAM |
Crucial Ballistix Elite. |
|||
|
Video Map. |
3GB. |
|||
|
HDD 1 TB SATA 6GB / S Seagate Barracuda |
||||
|
Cooller processor |
Arctic Cooling Freezer 13 Pro Co (1366/1155/775/754-AM2 / AM3, 300-1350 + 700-2700 rpm, Al + heat pipes) |
|||
|
Couller housing |
ARCTIC COOLING ARCTIC F12 PWM CO (4pin, 120x120x25mm, 24.4db, 400-1350OB / min) |
|||
|
21.5 "Monitor LG E2242C-BN (LCD, WIDE, 1920x1080, D-Sub) |
||||
|
Keyboard |
Genius Slimstar i8150 (KL-RA, USB, FM + Mouse, 3kn, Roll, Optical, USB, FM) |
TOTAL: 37866.
This high-performance equipment provides maximum speed ensures that you work with any type of documents.
This package will feature the following jobs:
Financial department:
Cabinet №4 Financial Director (P1)
Accounting Cabinet (P2, P3, P4, P5, P6)
Cabinet №6 Labor and wages (P7, P8, P9, P10, P11)
Sales department:
Cabinet №7 Commercial Director (P12)
Cabinet number 25 sales (P13, p14, p15, p16, p17)
Cabinet №9 Marketing Department (P18, P19, P20, P21, P22)
Table 4. Description of additional equipment.
|
Equipment |
number |
Price for 1pc (rub) |
|
|
Switch (SWICH 8) D-Link |
|||
|
Switch (SWICH 1,2,3,4,5,6,7) D-Link |
|||
|
SS7000B / PRO2U server (SX20H2MI): Xeon E5-2650 / 16 GB / 2 x 1 TB SATA RAID |
|||
|
Epson AcuLaser M2400DN (A4, 35 ppm, 1200dpi, USB2.0 / LPT, Network, Bilateral Printing) |
|||
|
Satellite DVB Card TEVII S 470 PCI-E (DVB-S2) |
|||
|
Satellite antenna |
|||
|
Converter Multico.< EC-202C20-BB> 10 / 100Base-TX to 100Base-FX Converter (1utp, 1sc) |
2.3 Providing a local network connection with the Internet network
Theoretical certificatenetwork technology:
The transition from analog television broadcast to the digital practically predetermined the appearance of the technology of satellite Internet access. But the real revolution in this area is associated with the European standard MPEG-2 / DVB, which organically combined the transmission of digital video and audio information and data. Another important factor should be to apply the IP protocol as a network data transfer standard. Today it is already possible to say that the world has identified both the sustainable standards of digital satellite television broadcasting and the frequency range used and the signal encoding and the necessary functions of the receiving equipment.
How satellite internet works:
In order to use the Internet from the satellite, except for the parabolic antenna you will need a receiver (PCI or USB device).
Through the Internet provider, we transmit query packages to the server, after which the files are sent to us through a special proxy server or VPN connection, but no longer on the ground channel, but through the satellite. To do this, the request sent by us first comes to a special operating center where the desired file is downloaded.
After that, the file is transmitted to the satellite. From the satellite file "lands" on your plate and enters the computer. The transmission rate from the satellite on your plate can be calculated by hundreds of kilobytes per second, depending on the workload of the operating center, and the delay between sending your request and the start of sending the file to you may be the same or smaller than your provider.
Equipment:
1.Pustovaya DVB Card
TEVII S 470 PCI-E (DVB-S2)
2.Putman antenna
LANS-7.5 Mesh Antenna Right Focus Parabolic with azimutyl Fixed Suspension AZ / EL 2.30M F / D \u003d 0.375
3. Converter
Multico.< EC-202C20-BB> 10 / 100Base-TX to 100Base-FX Converter (1utp, 1sc)
Provider:
"Rainbow"
Rate:
Wholesale 4000 MB / month.
Subscription fee: 2300 p / Mesz.
Additional traffic: 0.50 p / mb.
The speed of the incoming channel: 6144 kbps.
Outgoing channel speed: 2048 kbps.
2.4 Economic calculation
|
Name |
number |
Unit price |
||
|
Computer equipment (K) |
||||
|
Computer equipment (P) |
||||
|
SS7000B / PRO2U server (SX20H2MI): Xeon E5-2650 / 16 GB / 2 x 1 TB SATA RAID |
||||
|
D-Link |
||||
|
D-Link |
||||
|
Satellite DVB Card TEVII S 470 PCI-E (DVB-S2) |
||||
|
Satellite antenna LANS-7.5 Mesh-stra-focused parabolic antenna with azimutyl fixed suspension AZ / EL 2.30M F / D \u003d 0.375 |
||||
|
Multico.< EC-202C20-BB> 10 / 100Base-TX to 100Base-FX Converter (1utp, 1sc) |
||||
|
Epson AcuLaser M2400DN (A4, 35 ppm, 1200dpi, USB2.0 / LPT, Network, Bilateral Printing) |
||||
|
Defender ES Network Filter<5м> (5 sockets)<99483> |
||||
|
UTP 4 Cable Cat.5E<бухта 305м> Strategic Telecom Ultra. |
||||
|
RJ-45 Connector Cat.5E |
||||
|
Cable Channel 32x16 White, EFAPEL 10040 (10100)< < 2м > > |
||||
|
Total for network equipment and connecting cables will need |
Conclusion
When performing test work, a local computing network for the work of OJSC "Furniture Peace" was designed. The structure of the organization has been developed, the floor plan, cabinets and departments are designed, a computers and selection of network equipment are made, a cable system is calculated. Calculated the cost of the project.
Bibliographic list
1. Computing systems, networks and telecommunications: Tutorial / S. F. Horpsky. - Omsk: Omsk State Institute of Service, 2005. - 372 c. Electronic variant.
2. Olifer V.G., Olifer N.A. Computer networks. Principles, technologies, protocols: Textbook for universities. 3rd ed. - SPb.: Peter, 2006
Posted on Allbest.ru.
...Similar documents
Features of the local computing network and information security of the organization. Protection methods, selecting the implementation of the policy of using the use and control system of email content. Designing a secure local network.
thesis, added 01.07.2011
Appointment of the designed local computing network (LAN). The number of subscribers of the Designed LAN in the areas involved. List of equipment associated with cable gasket. The length of the connecting lines and segments for connecting subscribers.
abstract, added 16.09.2010
Theoretical substantiation of building a computing local network. Analysis of various network topologies. Streparation of prerequisites and conditions for creating a computer network. Selection of cable and technology. Analysis of the specifications of the physical environment FAST Ethernet.
coursework, added 12/22/2014
General characteristics and organizational structure of the enterprise. The advantages and disadvantages of the network built using 100VG-AnyLAN technology. Select the type of cable, stages and rules of its gasket. Requirements for the reliability of the local network and the calculation of its main parameters.
course work, added 04/25/2015
Development of a locally computing network of a computer club. Requirements for the LAN, system of security television (rel). Characteristics of used communication channels used equipment. Visual location schemes for the LAN and NET network, automation of processes.
coursework, added 03/06/2016
Information about the current state of the organization's computing network, the definition of the requirements for the organization to the local network. Selection of technical support: active switching equipment, hardware of servers and workstations.
course work, added 01/06/2013
The concept of computer networks, their types and purpose. Development of a local computing network of Gigabit Ethernet technology, building a block diagram of its configuration. Selection and justification of the type of cable system and network equipment, description of the exchange protocols.
course work, added 15.07.2012
Designing a local computing network intended for interaction between bank employees and information exchange. Consideration of its technical parameters and indicators, software. Used switching equipment.
course work, added 01/30/2011
The main features of local computing networks. Internet needs. Analysis of existing LAN technologies. Logical design LAN. Selection of equipment and network software. Calculation of the cost of network creation. Network health and safety.
course work, added 01.03.2011
The concept of a local network, its essence, species, purpose, purpose of use, determining its size, structure and cost. Basic principles for selecting network equipment and its software. Ensuring information security on the network.
 Lighting devices based on alternating current LEDs find their niche and may come out beyond its limits.
Lighting devices based on alternating current LEDs find their niche and may come out beyond its limits. Requirements and rates for cable laying in Earth Scope of application, Definitions
Requirements and rates for cable laying in Earth Scope of application, Definitions Automobile stroboscope from laser pointer
Automobile stroboscope from laser pointer Order 20 UAH to the account. How to Borrow on MTS. Additional information on the service
Order 20 UAH to the account. How to Borrow on MTS. Additional information on the service How to check the account replenishment
How to check the account replenishment How to get a loan on tele2?
How to get a loan on tele2? Responsiveness SSD on a miniature board What SSD Drive Buy
Responsiveness SSD on a miniature board What SSD Drive Buy