Auto-guessing passwords. How to crack a password: an overview of the most common methods. The best password brute-force programs
We recently published an article on the strength of passwords, as well as passwords that are used by many users. Most people use weak passwords. But how can you make sure your password is strong? Cracking passwords is an integral part of digital forensics and information security testing.
In this article, we have compiled the best password cracking software that can be used by system administrators to check the strength of their passwords. All utilities use different algorithms and are applicable to different situations. Let's first look at some basic information that will help you understand what we will be dealing with.
In the field of cybersecurity and cryptography, password cracking plays a very important role. It is the process of recovering a password in order to compromise or restore the security of a computer or system. So why do you need to learn password brute-force programs? For peaceful purposes, password cracking can be used to recover forgotten passwords from online accounts; it is also used by system administrators for prevention on a regular basis.
To crack passwords, brute force is used in most cases. The software generates various options for passwords and reports if the correct one was found. In some cases, the personal computer is capable of producing millions of variations per second. A program for cracking a password on a pc checks all the options and finds a real password.
The time it takes to crack a password is proportional to the length and complexity of that password. Therefore, it is recommended to use complex passwords that are difficult to guess or guess. Also, the search speed depends on the cryptographic function that is used to generate password hashes. Therefore, it is better to use Bcrypt to encrypt the password over MD5 or SHA.
Here are the main brute force methods used by cybercriminals:
- Dictionary attack- the attack uses a file that contains a list of words. The program checks each of the words to find a result;
- Bruteforce attack- it is possible not to use a dictionary, but to iterate over all combinations of the given symbols;
- Attack with rainbow tables- the attack uses pre-computed hashes, so it is faster.
There are other socially engineered password cracking methods, but for today we will focus only on unattended attacks. To protect against such attacks, you only need to use complex passwords. Now let's take a look at the best password cracking tools 2017. This list is published for informational purposes only and we in no way call for hacking other people's personal data.
The best password brute-force programs
1. John the Ripper
John the Ripper is one of the most popular password cracking tools available to absolutely everyone. It is open source and written in the C programming language. Various methods of brute-forcing passwords are collected here.
The program is able to sort passwords by the stored hash, and supports various hashing algorithms, including automatic algorithm detection. John the Ripper refers to Rapid7's suite of security testing tools. In addition to Linux, Windows and MacOS are supported.
2. Aircrack-ng

Aircrack-ng is a suite of programs for cracking and intercepting passwords from wifi networks. The program is one of the best used by hackers. It has everything you need to crack WEP and WPA encryption, from hijacking a hash to getting a ready-made password.
WEP encryption is especially easy to crack; to overcome the protection, there are PMS and PTW attacks, with which you can crack this protocol in a matter of minutes if there is enough traffic through the network. Therefore, always use WPA2 to be safe. All three platforms are also supported: Linux, Windows, MacOS.
3. RainbowCrack

As the name suggests, RainbowCrack uses rainbow tables to crack password hashes. With the help of ready-made tables, the utility greatly reduces the time of cracking. In addition, there is both a graphical interface and command line utilities.
After completing the pre-computation step, this tool runs hundreds of times faster than regular iteration. You don't need to create tables yourself, the developers have already created them for LM, NTLM, MD5 and SHA1. Everything is available for free.
Another important point is GPU acceleration. By using a video card, you can reduce the password computation time by several orders of magnitude. Windows and Linux platforms are supported.
4. THC Hydra

Unlike the programs listed above, Hydra works differently. It does not compute hashes. Instead, the program performs brute-force attacks on various network protocols. Astrisk, FTP, HTTP, MySQL, XMPP, Telnet, SHH and many more are supported here. The main purpose of the utility is brute-force attacks on the password entry form.
This tool helps security researchers know how easy it is to access a remote system. Modules can be added to expand functionality, Linux, Windows, Solaris, FreeBSD and MacOS are supported.
5. HashCat

According to the developers, it is the fastest password brute-force tool. It is distributed as free software and supports the following algorithms: md4, md5, LM, SHA, MySQL, Cisco PIX and Unix Crypt.
There are versions of the tool for brute-force attacks on the CPU, as well as GPU-based hacking - oclHashcat and cudaHashcat. In addition to the standard Bruteforce attack, dictionary attacks, hybrid attacks against most, against tables, Prince, and so on are supported. The supported platforms are Windows, Linux and MacOS.
6. Crowbar
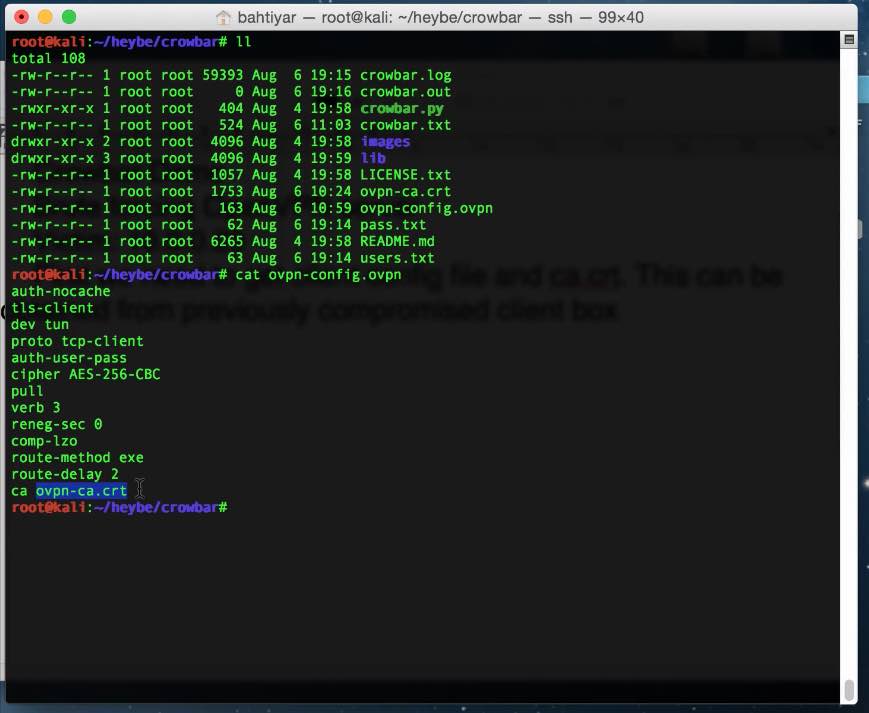
Crowbar is a popular password security testing tool. Other brute-forcing programs use usernames and passwords, but crowbar allows brute-forcing SSH keys.
This open source tool is designed to work with protocols that are rarely supported by other programs. VNC, OpenVPN, SSP, NLA are now supported. The program can run on Linux, Windows and MacOS.
7.coWPAtty

It is an implementation of a WPA / WPA2 PSK password brute-force utility based on a dictionary or rainbow tables. Using rainbow tables greatly speeds up the utility. The PSK standard is used very often now. The only good news is that it is very difficult to sort out the password if it was initially chosen correctly.
This article provides a list that includes the best password cracking software that works on various types of operating systems. Described, among others, are programs such as Aircrack, John the Ripper and THC Hydra - all of them use different algorithms and protocols that are theoretically capable of cracking passwords of varying complexity in Linux, Windows and OS X. The description is limited to a simple listing for an introductory excursion ... The list includes only those that work on Windows and Linux platforms.
What should a layperson (to which the author of the article counts himself) need to know about the hacking process? Some things you need to understand before proceeding with the procedure for "recovering forgotten" or removing passwords from intercepted packets:
Question "How long does it take to crack a password?" in this form reveals an amateur in you. It is tantamount to asking how long will it take to get from Moscow to Vladivostok? On foot? By plane? Through China? Although the answer is: from 1 second to 100,000 years. If you take the decryption through the "handshake", it works aircrack-ng gave me the combination only once:
- after a week of work ...
- on a dual-core laptop with an integrated GPU and 4 GB of RAM ...
- despite the fact that the password included 8 ONLY numeric characters
John the ripper running on the same machine failed in 5 days. Old man desktop with 4
-my Intel 2,8
GHz cores on board, 6
GB of RAM and Nvidia 660Ti I figured out the handshake for ..., in general, I didn't even get up from the table when I saw the password. You can work faster and work with much larger volumes, but give more than half of the income forGTX 980 does not pin at all ...
And the reason is not the program. So, having at hand weak hardware assembly, do not expect a serious result.
Cracking passwords. What techniques are there?
Getting to the goal is possible in several ways. Among them:
- dictionary attack (the hacker uses a special file with a ready-made list of symbolic combinations, which the program selects)
- brute force attack (password combinations are generated by the program)
- rainbow table attack (cracking hashes of valid user-entered passwords)
The programs presented here use various attack options and are ranked in an arbitrary order chosen by the author. The description of working with the programs will appear in the corresponding links in the corresponding paragraphs.
Password cracking software: John the Ripper
John the ripper- perhaps the most popular of its kind. The preferred programming language is C. The program is free (in a stripped-down version) and includes several approaches to the hacking process. The ability to automatically detect the types of password hashes puts it at the forefront of ethical hacking tools. Just like another hacking tool Metasploit, belongs to the family of security tools family Raspid7.
Supported platforms: Linux, Windows, Android, DOS and OS X
Password cracking software: OphCrack
The program is most often used among lovers of password cracking for a Windows account. Just like RainbowCrack, OphCrack works with rainbow tables to extract treasured combinations from password hashes. It is thanks to the ability to extract passwords of various formats from various sources of the system that the OphCrack program is known for its ability to crack Windows password in a matter of moments. When physically accessing a victim's computer, it leaves no traces in the form of a Live DVD. It comes in two versions, an extended version and a free version (the capabilities of Windows rainbow tables have been cut down).
From the manufacturer's website
Hacking software passwords: L0phtCrack
Like the previous one, L0phtCrack is known for the fact that it can quickly figure out the Windows password. Uses a wide range of attacks (hybrid, dictionary, brute force, rainbow tables), but can also be used for sniffing. Essentially analogous to the previous program. At the moment, there is only a 15-day trial version.
Supported platforms: Windows
Download L0phtCrack from the manufacturer's website
It is not uncommon for you to come up with a rather complex and unique password using different case, numbers and letters, but it takes a lot of time to create such complex passwords, especially if you need to create a large number of them.
Typically, such situations are faced by all sorts of administrators who need to create and monitor a user base or those who are engaged in security on the Internet and not only, it is possible to list the areas of application of such complex passwords for quite a long time.
To simplify and speed up this process of coming up with passwords and logins, you can use online services or programs that can be installed and run on a local computer. It is these services that will be discussed in our article.
The list of programs will include the most popular and functional services for creating complex and simple passwords with logins. These services will be presented in two forms, for online use and as a program on a computer.
The article will present the most functional and easy-to-use password and login generators, which are completely free.
Online password generators
Password generators for installation on a computer
Login generator
LastPass….
An online service that allows you to generate a password of any length with a choice of using the case of letters and the presence of symbols. The password is generated directly on your computer using Javascript. All passwords created using this service are not transferred anywhere and are displayed only on your computer.
This service is available not only online, it can also be downloaded and installed on a computer in order to use it locally without the need for an Internet connection.
Password creation options:
- Password length in characters
- Create a password in the form of a word for simplified pronunciation in voice.
- Number of digital characters in the password
- Selecting the type of characters to use (case letters, numbers and special characters)
Conclusion
This article presented the most functional and easy-to-use password and login generators. You can familiarize yourself with the general information for each generator and decide on the functionality you need.
Brute force (derived from the English phrase: brute force) is a type of hacker attack - a method of hacking accounts in computer systems, payment / banking services and on websites through the automated selection of password and login combinations.
Brute force is based on the mathematical method of the same name (brute force), in which the correct solution - a finite number or a symbolic combination - is found by enumerating different options. In fact, each value from a given set of potential answers (solutions) is checked for correctness.
How brute force works
A hacker writes a special program to guess passwords or uses a ready-made solution of his colleagues. It can be targeted at a specific mail service, website, social network (i.e., designed to hack a specific resource). Next, preparations are made for hacking. It consists of the following steps:
- Drawing up a proxy list
In order to hide the true IP address of the computer from which the attack will be carried out, and to prevent blocking by the site, where it is necessary to hack the account, the Internet connection is configured through a proxy server.
Proxy addresses / ports are searched for in Proxy Grabber. This utility independently extracts all data for connecting to intermediary servers from sites that provide proxies (they are specified in the list). In other words, the proxy is being collected.
The resulting base is saved to a separate text file. And then all server addresses in it are checked for operability in a proxy checker. Quite often, programs designed for automated extraction of proxies combine the functions of both a grabber and a checker.
As a result, a ready-made proxy list is obtained in the form of a list of IP / port, saved in a txt file. (You will need it when configuring the brute force program).
- Search for bases for brutus
It is necessary to connect a dictionary to brute force - a certain set of combinations of passwords and logins - which it will substitute in the login form. It, like a proxy list, has the form of a list in a plain text file (.txt). Dictionaries, they are also databases, are distributed through hacker forums, sites and file hosting. More experienced "craftsmen" create them on their own and provide them to everyone for a fee. The larger the base (the number of combinations, logins, accounts), the better (for a hacker) - the more likely the hacking will be successful.
- Configuring brute force
The proxy list is loaded; the brute-force program will automatically change the proxy so that the web server does not detect the attack and, accordingly, the source (host) of the attack.
A dictionary of password / login combinations is connected. The number of threads is set - how many combinations brute force will check at the same time. A powerful computer with high internet speed can confidently handle 120-200 streams (this is the optimal value). The speed of the brute directly depends on this setting. For example, if you set only 10 threads, the selection will be very slow.
- Launching brute force
The program records successful hacking attempts: saves the credentials (password / login) to a file. The duration of the selection procedure ranges from several hours to several days. At the same time, it does not always turn out to be effective - due to the high crypto-resistance of the data for entering or the implementation of other protective measures on the part of the attacked.
Types of brute force
Personal hacking
Hunting for a specific account - on social networks, on the postal service, etc. Through or in the process of virtual communication, the attacker elicits a username from the victim to access any site. Then he cracks the password using the brute-force method: he points to the brute-force address of the web resource and the obtained login, connects the dictionary.
The chances of such a hack are small, for example, compared to the same XSS attack. It can be successful if the account owner used a 6-7 character password with an unpretentious symbolic combination. Otherwise, it will take years - tens and hundreds of years to “guess” more stable variants of 12, 15, 20 letters, numbers and special symbols, based on the calculations of the mathematical search formula.
Brut / check
A database with logins / passwords from mailboxes of the same mail service (for example, mail.ru) or different ones is connected to brute force. And a proxy list - for masking a host (since web e-mail services quickly detect an attack on multiple requests from one IP address).
The brutus options contain a list of keywords (as a rule, the names of sites) - the landmarks by which it will look for login information on the hacked mailboxes in letters (for example: steampowered, worldoftanks, 4game, VK). Or a specific Internet resource.
The user, when registering in an online game, social network or forum, as expected, indicates his mail (mailbox). The web service sends a message to the specified address with login information and a link to confirm registration. It is these letters that brute-force is looking for to extract logins and passwords from them.
Press "START" and the cracker starts to brute force. It operates according to the following algorithm:
- Loads the login / password to the mail from the database.
- Checks access, or "checks", (automatically logs in): if you manage to log into your account, add one in the good (good) column (it means that another working email has been found) and starts viewing it (see the following points); if there is no access, it puts it in bad (bad).
- In all "buzzes" (open mails), brute-force scans letters at the request given by the hacker - that is, it searches for logins / passwords for the specified sites and payment systems.
- When the required data is found, it copies it and stores it in a separate file.
Thus, there is a massive "hijacking" of accounts - from tens to hundreds. The attacker disposes of the trophies obtained at his own discretion - selling, exchanging, collecting data, stealing money.
Remote computer hacking
Brute force, in conjunction with other hacker utilities, is used to gain remote access to the victim's password-protected PC via an Internet channel.
This type of attack consists of the following stages:
- It searches for IP networks in which an attack on users' computers will be carried out. Ranges of addresses are taken from special databases or by means of special programs, for example, such as IP Geo. In it, you can select IP networks for a specific county, region and even city.
- The selected IP ranges and selection dictionaries are set in the Lamescan brute-force settings (or its analogue), intended for remote brute-force login / password entry into the system. Once launched, Lamescan does the following:
- performs a connection to each IP from the specified range;
- after establishing a connection, it tries to connect to the host (PC) through port 4899 (but there may be other options);
- if the port is open: tries to access the system, brute-force when prompted for a password; if successful, saves the host (computer) IP address and login information in its database.

- The hacker launches the Radmin utility designed to control remote PCs. Sets the victim's network coordinates (IP, login and password) and gains full control over the system - the desktop (displayed visually on the intruder's computer display), file directories, settings.
Brutus programs
HASHCAT
For 2020, one of the most powerful programs for brute. Uses over 200 brute force algorithms. It is widely used to brute force WPA / WPA2 passwords, as well as passwords for MS Office documents, PDF, 7-Zip, RAR, TrueCrypt.

Classic brute force, one of the very first. Nevertheless, it does not lose its relevance and competes with new solutions. Has a smart brute-force algorithm and supports all major Internet protocols - TCP / IP, POP3, HTTP, etc. It knows how to fake cookies. Brutalizes the dictionary and generates passwords on its own.

Powerful brute-checker. Equipped with an extended arsenal of functions for working with databases (checking, sorting by domains). Supports various types of proxies, checks their performance. Scans messages in mailboxes according to settings such as date, keyword, address, unread messages. It can download letters from Mail.ru and Yandex.

There are many ways to crack a password. Of course, we provide information on how to crack a password for reference, so that you have an idea of how hackers work, why simple passwords are dangerous and how to protect yourself from being hacked.
How can you crack a password by guessing it?
Most people use simple passwords, and this is what hackers rely on in the first place. They start guessing the password using some initial data - the user's last name, date of birth, and their combinations. Here you do not need to rack your brains for a long time over how to find out the password. If the code word is so simple, then it will be determined in a couple of minutes.
The so-called "spider" method can be attributed to the same method. It consists in using knowledge about what the user is doing, who will be hacked. Very often in their passwords, people use words that are related to their professional activities, the name of the company. Using the Internet and specialized literature, they manage to reduce the scope of the search for the desired word and not rack their brains over how to crack the password.
How to protect yourself: do not use dictionary words, surnames, first names, dates of birth in your passwords. An automatically generated password using our website negates any attempts at a logical choice of a word.
Brute-force password guessing
Another common type of password that can be easily cracked is a dictionary word. Slightly more complex - with the addition of a number. Easily hacked with programs that use dictionaries from different languages. It is highly probable that in a couple of hours the code word will be in the hands of a hacker. Moreover, many sites offer such password selection online for free.
A variation of this method is cracking passwords from a table of hashed passwords. Simply put, a hash is the encrypted value of passwords. For example, password hashes of Windows users are stored in a special registry. If a hacker is skilled and competent enough to determine the password hashes, then in the database he will be able to find the password that matches this hash. There are also pre-prepared tables that help to guess the password by the hash even faster.
How to protect yourself: again - don't use dictionary words. It is possible to protect against brute-force passwords by hash, but it is quite difficult, and this will require a whole article. This is a task already for programmers who are working on creating a website.
Find out the password using brute force
How to crack any password? By brute force, or a brute-force search of combinations of symbols. Unlike dictionary search, the maximum possible number of combinations is used here, and the question of time to crack is only in the length and complexity of the password. For example, if a brute-force program generates 100,000 passwords per second, then it will take 9 days to select a combination of 7 characters, from 8 to 11 months, from 9 to 32 years, and so on.
How to protect yourself: do not use passwords less than 8 characters long, a password of any complexity and size can be generated.
Malware and phishing sites
While wandering around the Internet, downloading something, it is not difficult to pick up a virus program (they are often called Trojan horses) or get on a phishing site. Depending on the type of malware, it can steal passwords directly from the browser or record keystrokes on the keyboard. This data is then sent to the attacker.
A phishing site is a fake site that copies the design of a popular site. For example, vkkkk.com. The user buys for the design and enters his data, which is instantly received by the attacker.
How to protect yourself: do not download software from dubious resources, software without information about the developer (operating systems tell you about such software), check the authenticity of the site, do not follow the links that come to you from unfamiliar email addresses, do not trust tempting offers in the mail and do not trust your technology strangers.
Password guessing online directly
How can I find out the password yet? The most cunning attackers may not be afraid to break into a company's office disguised as an employee. They can simply wipe the dust, water the flowers, but carefully record who is doing what and where which passwords are entered.
Criminals can also work on the phone, posing as technicians and offering to provide him with information so that he can gain access to any system.
How to protect yourself: It is quite difficult to be confident in all employees, but it is important to train employees in basic security methods - do not enter passwords in front of strangers, do not attach stickers with passwords to tables and computer monitors.
These are not all the possibilities in the arsenal of hackers, however, knowledge of these basic techniques will significantly reduce the risk of theft of confidential information.
 Analysis of legacy code when the source code is lost: do or not?
Analysis of legacy code when the source code is lost: do or not? Windows does not load after installing updates Laptop does not turn on after updating windows 10
Windows does not load after installing updates Laptop does not turn on after updating windows 10 How to crack a password: an overview of the most common methods
How to crack a password: an overview of the most common methods Disable encryption on the tablet
Disable encryption on the tablet Creation of a light bulb. Edison's light bulb. Who Invented the First Light Bulb? Why did Edison get all the glory? Incandescent lamp device change history
Creation of a light bulb. Edison's light bulb. Who Invented the First Light Bulb? Why did Edison get all the glory? Incandescent lamp device change history How to quickly find your phone on google, wherever it is
How to quickly find your phone on google, wherever it is The electric incandescent lamp was invented in russia
The electric incandescent lamp was invented in russia