The remote computer requires network-level authentication which it does not support. An authentication error has occurred. The specified function is not supported. Disable NLA for RDP on Windows
After installing update KB4103718 on my Windows 7 computer, I cannot remotely connect to a server running Windows Server 2012 R2 via RDP Remote Desktop. After I specify the address of the RDP server in the mstsc.exe client window and click "Connect", an error appears:
Remote Desktop Connection
An authentication error has occurred.
The specified function is not supported.
Remote computer: computername
After I uninstalled the KB4103718 update and rebooted my computer, the RDP connection started working fine. If I understand correctly, this is only a temporary workaround, will a new cumulative update package arrive next month and the error will return? Any advice?
Answer
You are absolutely right that it is pointless to solve the problem, because you thereby expose your computer to the risk of exploiting various vulnerabilities that are closed by the patches in this update.
You are not alone in your problem. This error can appear on any Windows or Windows Server operating system (not only Windows 7). For users of the English version of Windows 10, when trying to connect to the RDP / RDS server, a similar error looks like this:
An authentication error has occurred.
The function requested is not supported.
Remote computer: computername

The RDP error “An authentication error has occurred” may also appear when trying to launch RemoteApp applications.
Why is this happening? The fact is that your computer has the latest security updates (released after May 2018), which fix a serious vulnerability in the CredSSP (Credential Security Support Provider) protocol, which is used for authentication on RDP servers (CVE-2018-0886) (I recommend read the article). At the same time, on the side of the RDP / RDS server to which you connect from your computer, these updates are not installed and the NLA protocol (Network Level Authentication) is enabled for RDP access. NLA uses CredSSP mechanisms to pre-authenticate users over TLS / SSL or Kerberos. Your computer, due to the new security settings that the update you installed, simply blocks the connection to the remote computer that uses the vulnerable version of CredSSP.
What can be done to fix this error and connect to your RDP server?
- Most correct the way to solve the problem is to install the latest Windows security updates on the computer / server to which you connect via RDP;
- Temporary method 1 ... You can disable Network Level Authentication (NLA) on the RDP server side (described below);
- Temporary method 2
... You can, on the client side, allow connections to RDP servers with an insecure version of CredSSP, as described in the article at the link above. To do this, you need to change the registry key AllowEncryptionOracle(REG ADD command
HKLM \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Policies \ System \ CredSSP \ Parameters / v AllowEncryptionOracle / t REG_DWORD / d 2) or change local policy settings Encryption Oracle Remediation/ Fix encryption oracle vulnerability) by setting its value = Vulnerable / Leave vulnerability).This is the only way to access a remote server via RDP if you do not have the ability to log into the server locally (via the ILO console, virtual machine, cloud interface, etc.). In this mode, you will be able to connect to a remote server and install security updates, so you will go to the recommended 1 method. After updating the server, do not forget to disable the policy or return the key value AllowEncryptionOracle = 0: REG ADD HKLM \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Policies \ System \ CredSSP \ Parameters / v AllowEncryptionOracle / t REG_DWORD / d 0
Disable NLA for RDP on Windows
If NLA is enabled on the side of the RDP server you are connecting to, this means that CredSPP is used to pre-authenticate the RDP user. You can disable Network Level Authentication in the system properties on the tab Remote access(Remote) by unchecking the box "Allow connections only from computers running Remote Desktop with Network Level Authentication (recommended)" (Windows 10 / Windows 8).

Windows 7 has a different name for this option. In the tab Remote access you need to select the option " Allow connections from computers with any version of Remote Desktop (dangerous)/ Allow connections from computers running any version of Remote Desktop (less secure) ".
It is also possible to disable Network Level Authentication (NLA) using the Local Group Policy Editor - gpedit.msc(in Windows 10 Home, the gpedit.msc policy editor can be launched) or using the Domain Policy Management Console - GPMC.msc. To do this, go to the section Computer Configuration -> Administrative Templates -> ComponentsWindows-> Remote Desktop Services - Remote Desktop Session Host -> Security(Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services - Remote Desktop Session Host -> Security), disconnect policy (Require user authentication for remote connections by using Network Level Authentication).

Also needed in politics “ Require a specific security level for remote RDP connections»(Require use of specific security layer for remote (RDP) connections) select the Security Layer - RDP.
To apply the new RDP settings, you need to update the policies (gpupdate / force) or restart the computer. After that, you should successfully connect to the server's remote desktop.
We open the registry editor.
Branch HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Control \ Lsa
Open the Security Packages parameter and look for the word tspkg there. If it is not there, add it to the existing parameters.
HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Control \ SecurityProviders branch
Open the SecurityProviders parameter and add credssp.dll to the existing providers, if there is none.
Close the registry editor.
Now you need to reboot. If this is not done, then the computer will ask us for a username and password, but instead of the remote desktop it will answer the following:
That's all, actually.
Server administrators based on Windows 2008 may have to face the following problem:
Connection via rdp protocol to your favorite server from a Windows XP SP3 station fails with the following error:
Remote desktop is disabled.
The remote computer requires network-level authentication that this computer does not support. Contact your system administrator or technical support for assistance.
And although the promising Win7 threatens to eventually replace its grandmother WinXP, the problem will remain urgent for another year or two.
Here's what you need to do to enable the network layer authentication mechanism:
We open the registry editor.
Branch HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Control \ Lsa
Opening the parameter Security Packages and looking for a word there tspkg... If it is not there, add it to the existing parameters.
Branch HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Control \ SecurityProviders
Opening the parameter SecurityProviders and add to existing providers credssp.dll if there is none.
Close the registry editor.
Now you need to reboot. If this is not done, then when trying to connect, the computer will ask us for a username and password, but instead of the remote desktop it will answer the following:
Remote Desktop Connection
Authentication error (code 0x507)
That's all, actually.
There have always been problems with the security and speed of servers, and every year their relevance only grows. Consequently, Microsoft has moved from the original server-side authentication model to network-level authentication.
What is the difference between these models?
Previously, when connecting to Terminal Services, the user created a session with the server, through which the latter loaded the credential entry screen for the user. This method consumes server resources even before the user has confirmed his legality, which allows an illegal user to completely load the server resources with multiple login requests. A server that is unable to process these requests refuses to process requests to legitimate users (DoS attack).

Network-Level Authentication (NLA) forces the user to enter credentials in a client-side dialog box. By default, if there is no network-level authentication on the client side, then the server will not allow the connection and it will not happen. NLA asks the client computer to provide its authentication credentials, even before creating a session with the server. This process is also called frontal authentication.

NLA was introduced back in RDP 6.0 and was supported natively by Windows Vista. From RDP 6.1 - supported by servers running Windows Server 2008 and above, and client support is provided for Windows XP SP3 (you need to allow a new security provider in the registry) and above. The method uses the Credential Security Support Provider (CredSSP) security provider. If you are using a remote desktop client for another operating system - you need to inquire about its NLA support.
Benefits of NLA:
- Doesn't require significant server resources.
- An additional layer to protect against DoS attacks.
- Speeds up the mediation process between client and server.
- Allows you to extend NT "single login" technology to work with a terminal server.
- Other security providers are not supported.
- Not supported by client versions lower than Windows XP SP3 and server versions lower than Windows Server 2008.
- It is necessary to manually configure the registry on every Windows XP SP3 client.
- Like any "single login" scheme, it is vulnerable to theft of "keys to the entire fortress".
- It is not possible to use the "Require password change at next login" function.
If you are using Windows XP when connecting to the server, then you may get an error: "The remote computer requires authentication at the network level, which this computer does not support."
This error occurs due to the fact that initially in Windows XP, authentication at the network level was not implemented; the developers implemented this feature in subsequent operating systems. An update file was also released later. KB951608 which fixed this bug and allowed Windows XP to implement network-level authentication.
In order for you to be able to connect to the server's remote desktop from your computer running Windows XP, you need to install Service Pack 3 (SP3), and then do the following:
On the official Microsoft website on the Russian-language page https://support.microsoft.com/ru-ru/kb/951608 download the automatic fix file. Scroll down the page and click the "Download" button in the "Help in solving the problem" section.
An English-language page is also available to you https://support.microsoft.com/en-us/kb/951608 where you can download this file by clicking the "Download" button in the "How to turn on CredSSP" section
After downloading the file, run it for execution. After starting this file, you will see the program window. In it, at the first step, check the "I Accept" box. In the second step, click the "Next" button

Upon completion of the installation, you will see the following window with the notification "This Microsoft Fix it has been processed" You just have to click "Close".

After you clicked the "Close" button, the program will tell you that the changes take effect, you need to restart the computer, click "Yes" to restart.


Solve the problem yourself without downloading the file
If you have administrative skills, then you can make changes to the registry of your computer manually, without having to download the patch file.
1. Click the button Start, select item Run, enter the command regedit and press the key Enter
 Skype free download Russian version Install Skype application
Skype free download Russian version Install Skype application How to recover a photo on Android after deleting it?
How to recover a photo on Android after deleting it? Original hosts for Windows operating systems What should be in a Windows 7 host
Original hosts for Windows operating systems What should be in a Windows 7 host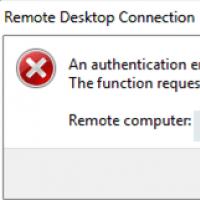 An authentication error has occurred
An authentication error has occurred Open the following ports at the client's workstation
Open the following ports at the client's workstation How to hide all VKontakte friends in the new version?
How to hide all VKontakte friends in the new version? Hide friends on VKontakte
Hide friends on VKontakte